2024-7-30 23:42:5 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
Table of Contents
In the second quarter of 2024, we observed a large increase in attacks that appeared to have unaffiliated branding attribution. Branding attribution includes aspects of the attack that bind the attacker to a specific brand of ransomware (e.g., Lockbit, Black Basta). The attributes are typically obvious indicators of compromise (IOCs) such as the type of encryption malware (which is brand-specific most of the time), the accompanying ransom note (which identifies the brand of ransomware), or a branded TOR site used for victims/threat actor communications. Over 10% of the incidents handled by Coveware in Q2 were unaffiliated; this is attributed to attackers that were deliberately operating independently of a specific brand and what we typically term ‘lone wolves’. We have seen small jumps in unaffiliated ransomware attacks before, but never to such magnitude, so it’s worth discussing why and how this happens.
Threat actors are compelled to deliberately rotate ransomware brands or go ‘unaffiliated’ for a variety of reasons, but all reasons lead back to efforts to obfuscate their identity. Here are some examples:
-
In the current cyber extortion climate, and certainly in the heyday of the Ransomware-as-a-Service (RaaS) model, a ransomware affiliate will use one specific brand regularly for most of their attacks. At times, they may have a unique opportunity to attack a more sensitive or publicly impactful victim, such as a hospital, a bank or a very large, well-known company. While victims in this category carry a certain allure, such as the perceived ability and inclination to pay substantial sums, there is also a consequence – increased publicity and scrutiny into the “brand” responsible for the attack. A brief spin through the historical ransomware archives tells us all we need to know about ransomware groups who “make a name” for themselves by attacking high profile entities; they don’t last long. Most established threat actors in the ransomware space are attuned to this trend. So how do they balance the aversion to this risk with the desire to pursue a potentially substantial extortion fee? Rather than put their preferred “brand” at risk for reputational damage and increased law enforcement/regulatory attention, they rotate towards a different brand that arguably has “less to lose” than their primary group affiliation. Then, if things take a turn for the worse, the affiliate can quietly revert back to their usual place of business while the brand name they “borrowed” suffers the long term consequences. Coveware has been tracking the increase in threat actor fluidity since Q2-2022, and the rampant deceptions and in-fighting exposed in the aftermath of the recent BlackCat/ALPHV and Lockbit collapses of Q1-2024 seem to have only deepened the distrust affiliates hold for the traditional model.
-
Sometimes an entire ransomware brand gets dismantled, either directly by law enforcement, or indirectly by the brand’s own administrators who are increasingly concerned about an imminent law enforcement disruption. This past quarter, we saw major disruptions to both BlackCat/ALPHV and Lockbit ransomware groups and within a few short weeks of these platforms being compromised/eliminated, we observed statistically significant increases in the number of attacks from groups like BlackSuit, RansomHub, Medusa and others. . Aside from the sheer number of attacks that increased from these groups, we also correlated tactics, techniques, and procedures (TTPs) used in these attacks to TTPs that were previously unique to one of the now-defunct brands, indicating some displaced affiliates were being onboarded to new platforms and bringing their playbooks and toolkits with them.
-
Sometimes there are actors or groups of actors that prefer to remain unaffiliated with any established brand name, but invariably end up needing the infrastructure of a brand to complete a certain aspect of the attack life cycle. The most common example of this is a lone wolf actor who lacks the infrastructure to host their own “name and shame” data leak site, so they pay to use the site of an existing group and threaten to post the victim there if they don’t comply. Another long standing example of this approach is a lone wolf actor/actor group that either can’t or won’t expend the resources to develop encryptors from scratch and resorts to “borrowing” the encryption mechanisms built by others. This was observed in Q2 with various members of the Scattered Spider group utilizing an encryptor from the Qilin group when they had previously relied on the encryptor used by BlackCat/ALPHV.
The ability for threat actors to move so fluidly between different ransomware brands or to carry out attacks as an unaffiliated actor demonstrates why it’s critical for enterprises to focus more on the prevalent Tactics Techniques and Procedures (TTPs) that are being used and less on the specifics of one ransomware brand or another. The security product marketing industry and the media do a very good job of focusing readers on “brands”, as it helps them personify the threat actors and write more compelling stories. The downside of this approach is that it draws the reader’s attention towards the name, and away from what is important, which are the underlying attack techniques that are often very repetitive between these groups.
Ransom Payment Amounts in Q2 2024
Average Ransom Payment
$391,015
+2.4% from Q1 2024
Median Ransom Payment
$170,000
-32% from Q1 2024
In Q2 2024, the average ransom payment amount increased very slightly to $391,015 (2.4% increase from Q1 2024), while the median ransom payment fell to $170,000 (32% decrease from Q1 2024).

Most Common Ransomware Variants in Q2 2023
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q1 2024 |
|---|---|---|---|
| 1 | Akira | 11% | – |
| 2 | (Independent) Lone Wolves | 10% | New in Top Variants |
| 3 | Black Basta | 8% | -1 |
| 3 | BlackSuit | 8% | +1 |
| 4 | Lockbit 3.0 | 7% | -2 |
| 4 | Medusa | 7% | -1 |
| 5 | BianLian | 5% | New in Top Variants |
| 5 | Inc Ransom | 5% | -1 |
| 6 | Phobos | 4% | -2 |
Market Share of the Ransomware attacks
With the elimination of BlackCat/ALPHV and the rapid dissolution of Lockbit 3.0 following Q1 and Q2 law enforcement actions against them, we observed a sharp rise in the frequency of lone wolf “unaffiliated” extortion attacks (some data theft only, some with new encryption), as well as a rise in groups whose TTPs abruptly shifted to mirror those of the recently-dissolved brand names. Other groups such as Akira and Black Basta continued to hold comparable market share that they’ve held in prior quarters, but without a noticeable shift in techniques and behaviors, suggesting not all ransomware brands have opened their doors to receive displaced affiliates. It’s also unlikely that the “lone wolf” contingent is composed of brand new actors just stepping into the cyber extortion economy. It’s much more likely that these are existing threat actors that were directly displaced from disrupted groups, or actors that made the decision to operate independently due to the increasing threat of exposure, interruption, and profit loss associated with “toxic” ransomware brands.
Ransomware Payment Trends in Q2 2024

In the second quarter of 2024, 36% of clients chose to pay their Ransom versus 28% in Q1. This is a marked increase but well within the bands of historical month-to-month volatility.
Data Exfiltration Only Payment Trends in Q2 2024

In matters that only involved data exfiltration (DXF i.e. the victim of the attack did not sustain file encryption, just data theft), the percentage of companies that resolved to pay versus not pay a ransom in Q2 jumped from 23% in Q1 to 43% in Q2, reversing a 2 quarter downward trend, but still remaining in the bounds of historical month to month numbers.
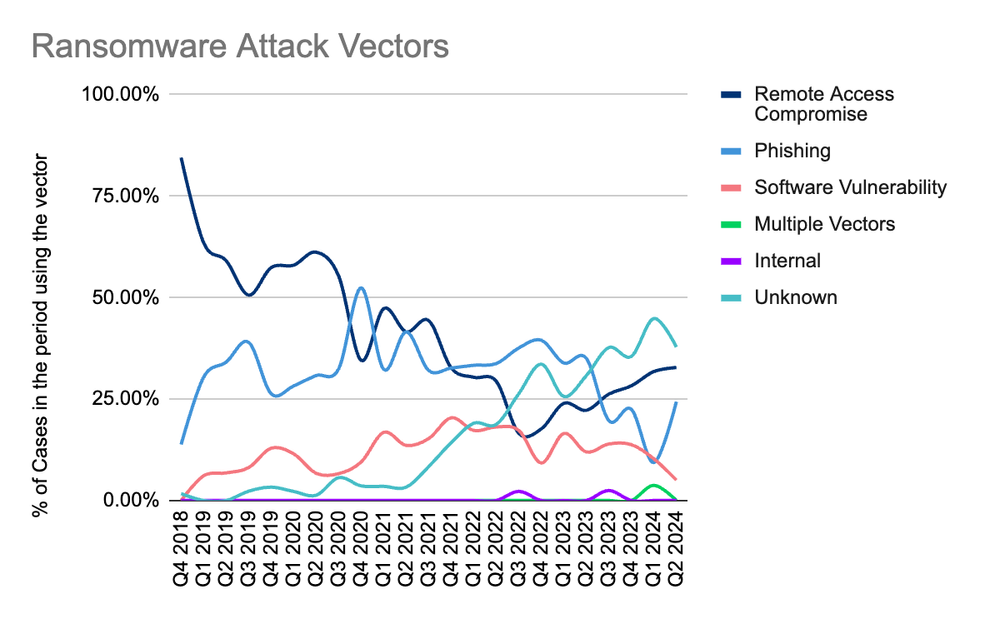
Most Common Attack Vectors in Q2 2024

While the unknown vector continues as the top vector, we note it declined in Q2. More clients are able to isolate the initial “patient zero” and point of initial access early on with good security incident and event management (SIEM) logging and alerting. This increased visibility may also be attributed to shorter dwell times leading to more available forensic artifacts and better log retention covering the timeframe of compromise. Two of our top 3 adversaries this quarter have average dwell times of 24 hours, which is much shorter than prior quarters.
Remote compromise remains the highest confirmed vector, as forensics increasingly isolates the organization’s VPN as the source of compromise. It remains challenging to pinpoint if it was a stolen credential, brute force access combined with single factor authentication, exploitation of a CVE, or all of the above. The dark web market for valid credentials seems to be rich at the moment, with infostealers being the likely culprit for how credentials are initially scraped weeks, or months in advance of their use. This highlights the importance of enforcing multifactor authentication and strong password hygiene.
Phishing remains a mixed vector and we’ve seen variations of call techniques exploited in Q2. Social engineering efforts targeting help desk employees at large enterprises remain popular, particularly with data-theft-only groups. Variations of callback phishing also persist, wherein the threat actor directly calls an employee, or prompts the employee to call them to resolve a feigned IT issue with the goal of coercing the victim to download a remote access client such as ZohoAssist or QuickAssist. If successful, the threat actor then exfiltrates as much information as possible from that single endpoint, or they may attempt lateral movement to pull from additional network resources.
Most Common TTPs in Q2 2024

Exfiltration [TA0010]: For the second consecutive quarter, Exfiltration remains in the top spot with 77% of our cases in line with 78% in Q1 and 77% in Q4. This consistency has been maintained both by a continued focus on exfiltration as either a precursor to an encryption attack or as the sole tactic, but also by a significant increase in “lone wolf” attacks focused solely on DXF. In Q2, exfiltration attempts included leveraging weakly secured Snowflake instances. This wave of attacks demonstrates how third party cloud applications can easily become targets for threat actors looking to score cheap exfiltration opportunities.
Threat actors more commonly leverage internally staged data that is then packaged and compressed before exfiltrating it from the network. Techniques for getting data out of a target network typically include transferring stolen data over threat actor command and control channels, but most commonly use file transfer and synchronization tools combined with exploiting outbound server access (e.g., 443/HTTPS) to the Internet. Common third party exfiltration tools used in these instances include Megasync, Rclone, Filezilla, and Windows Secure Copy (WinSCP) with some actors having clear tool favorites.
Lateral Movement [TA0008]: Lateral Movement, in the second spot at 71% is consistent with the prior quarter at 68%. Lateral Movement by threat actors consists of techniques used to enter and control remote systems on a network. Successful ransomware attacks require exploring the network to find key assets such as domain controllers, file share servers, databases, and continuity assets that are not properly segmented. Reaching these assets often involves pivoting through multiple systems and accounts to gain access. Adversaries often use legitimate credentials or those created by the threat actor along with native network and operating system tools, which may be stealthier and harder to track.
The usage of internal Remote Desktop Protocol (RDP) remains one of the fastest and most efficient methods for lateral movement if a threat actor has the proper credentials. Other favored tactics involve the exploitation of SMB/Windows Admin Shares, remote controls tools like VNC, and using SSH (e.g., Putty) for lateral movement. SSH is a common protocol used to access VMWare ESXi for execution of scripts and malware during encryption attacks against those environments.
Impact [TA0040]: Impact consists of techniques used by adversaries to disrupt the availability or compromise the integrity of the business and operational processes. Techniques used for impact can include destroying or tampering with data along with encryption. Forensically, Impact has fallen further down the rankings now residing in the third spot, a 20% decline from Q1 at 68% down to 48%. This continues to be a bit of a red herring as the number of Coveware cases with data encryption was actually 89%.
Much of the observed encryption in Q2 was VMware ESXi encryption, which has been a favored target of many groups due to the “jackpot” nature of disrupting a virtualized host or cluster of hosts, impacting multiple applications and databases. Security challenges with proper configuration and hardening of these environments and lack of security tools capable of running on ESXi contribute to the attraction by threat actors. Due to the latter, it often remains difficult to capture the actual tactic and technique from the forensic inspection of the impacted ESXi host. This is further complicated by threat actors tampering with credentials to deny access, which leads to a huge margin of our clients being locked out of the ESXi hosts, which necessitates the need to reinstall to get to the datastores for eventual recovery. The reinstallation wipes forensic artifacts from the host which is an unfortunate consequence, but necessary for optimal recovery outcomes.
Command and Control [TA0011]: Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Threat actors commonly attempt to mimic normal, expected traffic to avoid detection. While instances of what would be considered “traditional” C2 tooling are still observed (e.g., Cobalt Strike, Impacket, Metasploit), TA preferences continue towards the use of legitimate remote management and monitoring (RMM) software, leveraging trusted domains and signed executables, to maintain an interactive session on victim systems. These tools may already be installed in the environment and conscripted by the threat actor, but often are downloaded into the environment after initial access has been achieved.
Common tools in use include AnyDesk, ScreenConnect, TeamViewer, LogMeIn and TightVNC. Some of these tools have unique feature functions such as ‘stealth modes’ attractive to a TA, such as Atera and ScreenConnect’s ‘backstage mode’ feature. As many of these RMM tools are cloud based, it’s important to consider layered approaches to mitigation that focus not only on the installation of the applications but the external network destinations to which they attempt to connect.
Credential Access [TA0006]: Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals. The most popular tool used by threat actors, regardless of what group they’re in, is Mimikatz, along with tools like Lazagne. This also includes web browser harvesting tools such as WebBrowserPassView and PasswordFox. Any credential stored on a system could be a target of opportunity, with threat actors introducing new techniques or tooling on a regular basis to harvest from the operating system, specific applications, or the browser with some less mature threat actors dumping a chest of tools into an environment as part of toolkits and packs.
Ransomware Victimology: Industries impacted Q2 2024

In Q2 2024 we saw a standard distribution of industries impacted by ransomware attacks. The Snowflake data exfiltration campaign demonstrated how cyber extortion continues to be a crime of opportunity. Individual companies are rarely targeted directly, as the majority of ransomware actors pursue targets based on opportunity and the path of least resistance, which is significantly more economical than expending the resources to try and compromise a target of interest. It is also rare to find individual sectors/industries intentionally targeted.
The share of extortion attacks that a given industry absorbs is typically a function of one of two things. First, the overall percentage of companies in the population that fall into that industry, or second, a specific cost-effective vulnerability that is more prevalent in one industry versus another. For instance, if a specific application or type of software has a cost-effective vulnerability that makes it easy for ransomware actors to exploit and extort those companies, then you typically see a larger concentration of attacks impacting those industries versus others. In a normal month, though, we typically see the distribution of attacks more closely correlated to the overall percentage of companies that fall into that industry as a whole.
Ransomware Victimology: Victims size Q2 2024


While much of the media attention tends to focus on large companies that create major waves of secondary disruption when they get impacted, ransomware still remains a small to mid-market business problem by the numbers. The average victim size in any given quarter will also be influenced by which threat actor group is holding market share. Groups that previously demonstrated a keen interest in targeting the large enterprise market have since collapsed, and the groups that comprise the current top of the “food chain” in terms of sheer volume of attacks tend to skew towards the SME side of the market.
*** This is a Security Bloggers Network syndicated blog from Blog | Latest Ransomware News and Trends | Coveware authored by Bill Siegel. Read the original post at: https://www.coveware.com/blog/2024/7/29/ransomware-actors-pivot-away-from-major-brands-in-q2-2024
如有侵权请联系:admin#unsafe.sh