2024-7-24 21:26:50 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Threat actors continually leverage and create a plethora of tactics to bypass Secure Email Gateways (SEGs). These include encoding malicious URLs with other SEG protection tools, obfuscating file contents, and abusing SEG treatment of “legitimate” files.
Recently, threat actors appear to be abusing how SEGs scan the contents of archive type file attachments. The threat actors utilized a .zip archive attachment and when the SEG scanned the file contents, the archive was detected as containing a .Mpeg video file and was not blocked or filtered. When this attachment was opened with common/popular archive extraction tools such as 7zip or Power ISO, it also appeared to contain a .Mpeg video file, but it would not play. However, when the archive was opened in an Outlook client or via the Windows Explorer archive manager, the .Mpeg file is (correctly) detected as being a .html and victims were able to open the .html and eventually execute the embedded FormBook malware.
Emails
The specific emails that Cofense Intelligence has identified were targeting Spanish speaking employees at an international financial firm and claimed to deliver an attached invoice. The emails are fully featured, including a full email body and a signature, a step beyond most common phishing emails. The emails were sent with the “Roundcube Webmail/1.4.8” User-Agent and bypassed Cisco IronPort but based on this analysis it is strongly likely they would also bypassed other SEGs.
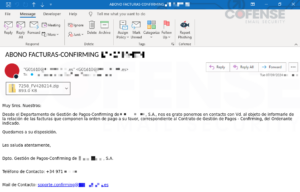
Figure 1: Email with attached archive containing obfuscated contents.
SEG Bypass
Based on this analysis and related testing, it appears that the malicious attachments were able to bypass detection due to how SEGs parsed the file inside of the archive files. If the SEG had received and scanned an email with the identified malicious HTML attached, it would have blocked the email. Even if it was a .zip archive attachment with clearly malicious content, most SEGs would have scanned the archive contents and detected their malicious nature.
Here in Figure 2 is an example of how Cisco IronPort typically views the contents of a .zip file. This indicates that an attached .zip archive had its contents extracted and contained a gif and an HTML file.
![]()
Figure 2: Sample of Cisco IronPort scan of typical .zip archive attachment.
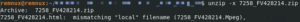
In Figure 3 below, we see the Cisco IronPort header for the email in Figure 1 containing an HTML file disguised with the .Mpeg file extension inside of an attached .zip archive.
![]()
Figure 3: Cisco IronPort scan of obfuscated .zip archive.
Illustrated in Figure 3, Cisco IronPort determined that the file inside of the archive was an .Mpeg and not an HTML. Although other SEGs are not as verbose in the email headers when it comes to their scanning of file attachments, it is highly likely that they would return similar results when scanning this .zip archive. In fact, as will be seen in the next section, many common archive extraction tools also view the contained file as a .Mpeg despite indicators to the contrary.
Attachments
The .zip archive attached to this email appears innocuous to both SEGs and a cursory investigation by an analyst using standard static analysis tools. The .zip archive contents would appear to be an .Mpeg to many common tools utilized by security analysts and researchers, such as Power ISO and 7zip.

Figure 4: Archive file contents viewed in multiple programs.
- In the top window depicts the archive file opened in Windows explorer directly, initiated from the Outlook desktop client. This clearly shows the archive contents as being an .html file.
- The middle window is the archive file opened using the common archive extractor Power ISO.
- The bottom window is the archive file viewed with the highly popular 7zip application.
As can be seen in the bottom and middle window, even common and widely used archive extractors incorrectly identify the enclosed file as a .Mpeg. Using the “test” option of 7zip on Windows we are also able to see a general warning about the archive’s headers in Figure 5. However, the rather succinct warning does not provide enough information to draw any conclusions.

Figure 5: 7zip test of obfuscated archive.
When the unzip tool in Ubuntu is used on the archive it provides the most relevant information available yet, as can be identified in Figure 6.
![]()
Figure 6: Ubuntu unzip tool analysis of archive.
Starting with the hint that there is a “local” file name mismatch we are able to look at the .zip archive in a text editor as seen in Figures 7 and 8. The start, or “header”, of the file shown in Figure 7 shows us that the threat actor has customized the .zip archive so that the file header calls its contents a .Mpeg.

Figure 7: Header of .zip archive.
The end of the file, or the “footer”, shown in Figure 8 shows us that the file contained in the .zip archive should actually be treated as a .html.
![]()
Figure 8: Footer of .zip archive.
This demonstrates that many common archive extractors and SEGs read the file header information for the archive and ignore the file footer that may contain more accurate information.
Infection
When properly recognized as a .html file and opened, the HTML file delivered another .zip archive, appearing to provide the file as a download from an external source when it is in fact a decoded file embedded in the original HTML file.
This second .zip archive contained a .cmd file which was in fact a .cab archive. Inside of this .cab archive was the malicious executable. The executable was a sample of DBat Loader. When run, the executable downloaded a payload, decrypted its contents, and ran FormBook in memory. This version of FormBook contacted several different C2s with different paths, unlike the standard FormBook which contacts 16 different domains with the same path.
FormBook is an Information Stealer and is consistently in the top 10 most commonly seen malware by Cofense. It is capable of keylogging, file management, clipboard management, taking screenshots, network traffic logging, and password, cookie, and form recovery from browsers. It is able to download and execute additional malware putting infected users at risk of other kinds of malware including Ransomware.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained herein regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® names and logos, as well as any other Cofense product or service names or logos displayed herein are registered trademarks or trademarks of Cofense Inc.
The post Malware Exploit Bypasses SEGs Leaving Organizations at Risk appeared first on Cofense.
*** This is a Security Bloggers Network syndicated blog from Cofense authored by Cofense. Read the original post at: https://cofense.com/blog/malware-exploit-bypasses-segs-leaving-organizations-at-risk/
如有侵权请联系:admin#unsafe.sh