2024-7-24 11:36:2 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
Overview
Leveraging our global threat hunting system, NSFOCUS Security Research Labs discovered spear-phishing email attacks by the APT group TransparentTribe targeting Indian government departments on February 2, 2024. The timing of these attacks coincides with the presidential election in India, scheduled for April-May of this year, and the bait documents are related to the “President’s Award,” suggesting a possible connection with the election.
In this incident, the TransparentTribe group utilized a phishing document named “Recommendation for the award of President’s.docm.” The malicious file was concealed within this document and, upon execution, would run the embedded VBA script to extract and execute the malicious program within the file. The ultimate payload used in this attack was the CrimsonRAT remote control program, a common Trojan used by the TransparentTribe attack group. This RAT is capable of collecting system information, downloading and running files, and stealing sensitive information, posing a significant threat.
Introduction of TransparentTribe
TransparentTribe, also known as ProjectM or APT 36, is an APT attack group originating from Pakistan. It primarily targets India, Kazakhstan, and Afghanistan. The group’s main objectives are defense, military, embassies, and governments. Their activities date back to as early as 2012. Recently, they have been using phishing emails to deliver malicious docm and xlam documents, utilizing VBA scripts in the documents to release malicious programs, with the aim of stealing user information.
Bait Information
In this incident, the bait document used by TransparentTribe was named “Recommendation for the award of President’s.docm.” The document’s content pertains to a document sent by the “Government of India Ministry of Home Affairs, Police-I Division” to various Indian government departments. The document impersonates an official document issued by the Indian government on October 17, 2023, mainly discussing recommendations for the award of the President’s Distinguished Service Medal and the Meritorious Service Medal on Republic Day 2024. This confirms that the target of this attack is Indian government departments.
In November 2023, a historical phishing email appeared, also using a bait document containing malicious VBA scripts. The document was named “Monthly Report MAP.xlam.” Upon execution, it prompts to enable macros, and if the user clicks to enable, the VBA script will execute, leading to subsequent malicious operations; it also pops up a normal Excel file to cover up the malicious operations.
It can be seen that this APT group has recently favored impersonating official documents issued by government departments when constructing bait content, using highly targeted content such as government documents and forms. This narrows the scope of the attack, targeting specific targets.
Technical Analysis
Different from the group’s previous method of using a downloader to execute remote links to obtain subsequent programs, we have observed that the group’s recent activities prefer to hide the ultimate payload within the bait document.
The phishing file in this instance is named “Recommendation for the award of President’s.docm.”
The attack process executed after opening this phishing file is as follows:
1. Execute the malicious VBA script;
2. The script will decompress the current file and store the file in the download directory;
3. The script decompresses the document, extracting the word\media\image1.png file;
4. The script changes the extension of image1.png to .zip, decompresses it, and extracts the image1.exe file;
5. The script renames image1.exe to itmvroidovs.scr and runs it, which is the ultimate payload CrimsonRAT;
6. The script changes the extension of word\media\image2.png to .docx and runs it, using it as a decoy to confuse the attacked user.

CrimsonRAT Analysis
CrimsonRAT is the main Trojan program used by TransparentTribe, with primary functions such as obtaining system information, capturing screenshots, collecting victim host processes, and driver information. It also supports downloading, running files, and stealing sensitive information.
Combining the bait creation time with the official report release time, the timestamp is likely to be genuine, indicating that this incident is a recent attack launched by TransparentTribe.
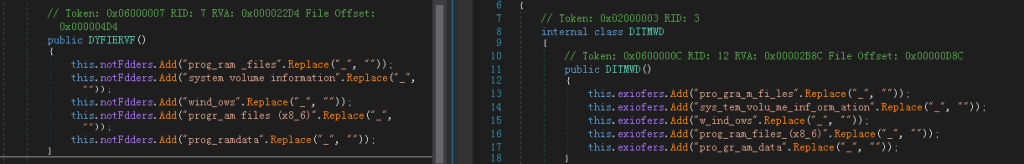
In this attack incident, the CrimsonRAT Trojan program used has a timestamp of December 16, 2023, which is not much different from the version on October 12, 2023. The main change is the modification of the obfuscation character “_” in the string to evade detection.
TransparentTribe used a version of CrimsonRAT with the version number “S.F.0.3” in November 2023, but in this activity, the CrimsonRAT has increased the version number obfuscation, confusing the version number into “A._E.0._6”, using this method to evade detection:
The version found on October 12 is somewhat different from the previously found versions, adding obfuscation strings “_” to a large number of key strings, and all the versions found recently have been done through this string obfuscation method:
Attribution of Attackers
NSFOCUS Security Research Labs found the following attribution items in this APT incident:
- The malicious sample used by the attacker is CrimsonRAT, which is one of the Trojans commonly used by TransparentTribe;
- The attack process and VBA script used by the attacker in this incident are consistent with the attack chain characteristics and coding habits of TransparentTribe in recent attacks;
- The phishing document captured in this incident was uploaded from India, which is consistent with the common attack targets of TransparentTribe;
Therefore, NSFOCUS Security Research Labs attributes the attackers of this attack incident to the TransparentTribe group.
IOC
| IOC | Note |
| c2b37effe3195665ec5597afa329f | Recommendation for the award of President’s.docm |
| f5380e7a6e15a0ef27e6f31fcc29ed4d | itmvroidovs.exe |
| 41d801d96c9e27c5ca6c4678ffa2d7e2 | Monthly Report MAP.xlam |
| mus09.duckdns.org | C2 |
| 64.188.21.202:6826 | C2 |
| 64.188.21.202:18828 | C2 |
| 64.188.21.202:22821 | C2 |
| 64.188.21.202:28120 | C2 |
| 164.68.122.64:11128 | C2 |
| 164.68.122.64:18187 | C2 |
| 164.68.122.64:19986 | C2 |
| 164.68.122.64:27684 | C2 |
| 164.68.122.64:25123 | C2 |
Related blog post:
Indian Government Agencies Targeted in Phishing Attacks by APT Group SideCopy
About NSFOCUS Security Research Labs
NSFOCUS Security Research Labs is an internationally recognized cybersecurity research and threat response center at the front of vulnerability assessment, threat hunting and mitigation research.
The post TransparentTribe’s Spear-Phishing Targeting Indian Government Departments appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks..
*** This is a Security Bloggers Network syndicated blog from NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks. authored by NSFOCUS. Read the original post at: https://nsfocusglobal.com/transparenttribes-spear-phishing-targeting-indian-government-departments/
如有侵权请联系:admin#unsafe.sh








