2024-7-23 23:46:51 Author: isc.sans.edu(查看原文) 阅读量:7 收藏
In April, an OS command injection vulnerability in various D-Link NAS devices was made public [1]. The vulnerability, CVE-2024-3273 was exploited soon after it became public. Many of the affected devices are no longer supported.
We have seen different exploits following similar patterns:
/cgi-bin/nas_sharing.cgi?user=messagebus&passwd=&cmd=15&system=[base 64 encoded payload]
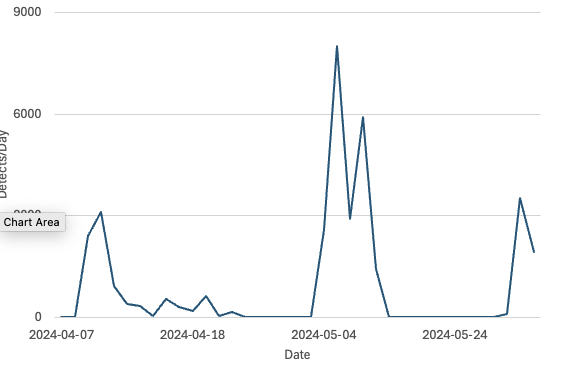
After the initial scans, we had two more "spikes" in scans for this vulnerability. The second one just started two days ago.
The latest set of scans uses this payload:
ZWNobwktZQlcXHg2NVxceDYzXFx4NjhcXHg2ZlxceDIwXFx4MjdcXHg3OFxceDc4XFx4NzhcXHg3OFxceDc4XFx4NjNcXHg2M1xceDYzXFx4NjNcXHg2M1xceDI3fHNo
This payload decodes to
echo -e \\x65\\x63\\x68\\x6f\\x20\\x27\\x78\\x78\\x78\\x78\\x78\\x63\\x63\\x63\\x63\\x63\\x27|sh
Encoding strings as hexadecimal with "echo -e" has been popular for a while and took off after Mirai started using it. In this case, the command to be executed is:
echo 'xxxxxccccc'|sh
The goal of this exploit is to find vulnerable machines. The "double obfuscation" is likely supposed to bypass some filters and better discriminate against honeypots. I have seen "non functional" exploits used to detect honeypots by attempting to fingerprint the error message returned. Maybe a pattern to add to our honeypots after lunch.
The single source (192.227.190.158) scanning for this particular version of the exploit on July 19th has now switched to related scans for nas_sharing.cgi
[1] https://nvd.nist.gov/vuln/detail/CVE-2024-3273
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
如有侵权请联系:admin#unsafe.sh