
On July 14th 2024, a malware analyst @0x6rss discovered and shared on X a security issue in Wha 2024-7-23 20:16:58 Author: www.mobile-hacker.com(查看原文) 阅读量:56 收藏
![]()
On July 14th 2024, a malware analyst @0x6rss discovered and shared on X a security issue in WhatsApp Messenger for Android. This issue allows an attacker to disguise malicious Android app as PDF file shared in chat. The bug cannot be misused to share malicious app as attachment directly through the regular use of the WhatsApp Messenger. Instead, to take advantage of this issue, an attacker would have to send a special request through WhatsApp’s programming interface.
On June 25th 2024, @0x6rss reported this extension manipulation bug to Facebook security team, that manages WhatsApp bug bounty. However, the team did not consider it a security vulnerability but rather as a type of deception known as social engineering, which doesn’t fall under the category of in-scope security vulnerabilities. Despite not being officially recognized as a vulnerability, I think it’s crucial for users to know about this simple but effective trick. Using this method, people who are not very familiar with technology can be tricked into downloading and installing a harmful application. Similar issue was recently discovered and fixed by Telegram, where malicious Android apps could be disguised as videos shared in chat in Telegram for Android application.
I reached the @0x6rss to learn more about his discovery. He shared with me the details and I was able to replicate it. Prove of concept is not publicly available.
You can watch a demo of how this issue appears to users in a video below.
WhatsApp trick: Android malware can impersonate PDF filehttps://t.co/K9Pafn0CCF pic.twitter.com/nGGgsdFiPN
— Mobile Hacker (@androidmalware2) July 23, 2024
This bug can be misused only using WhatsApp API, and not directly by sending a crafted payload within the app. This simple trick is to change the file extension of displayed document; however, WhatsApp still shows correct file extension, see Figure 1. For tech savvy users it most likely would be a red flag, however, everyday user might not know what APK does mean or what file extension Android app’s use when file name states it’s a PDF format.

When user clicks on the file, the second red flag appears, which is a warning from WhatsApp that This document might contain unsafe content. Make sure you trust the sender before you open it. See Figure 2.
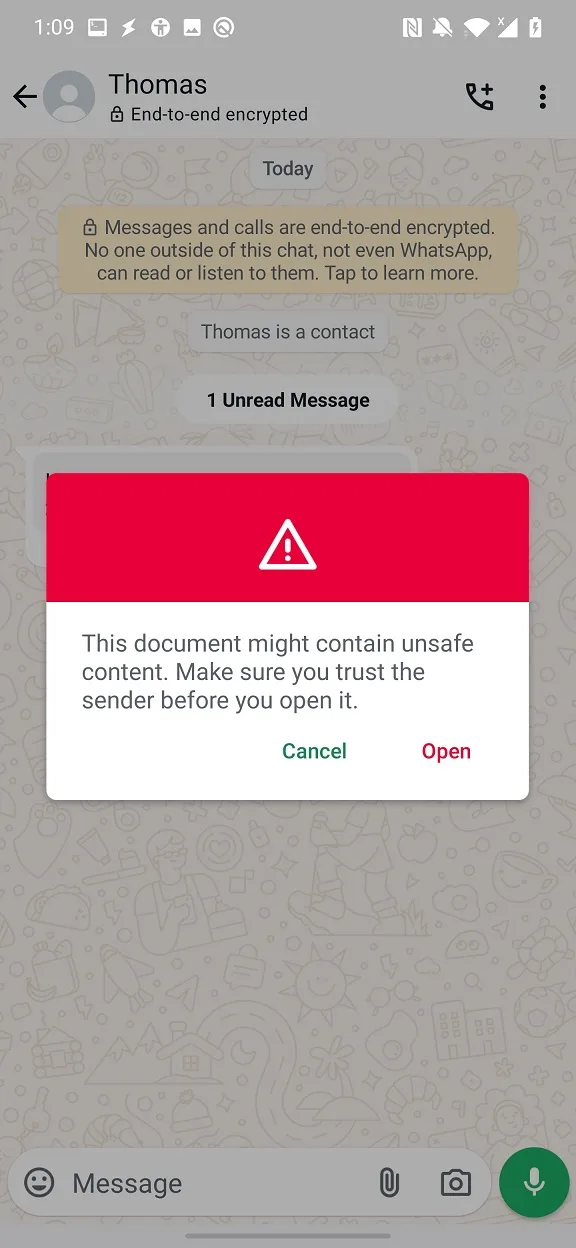
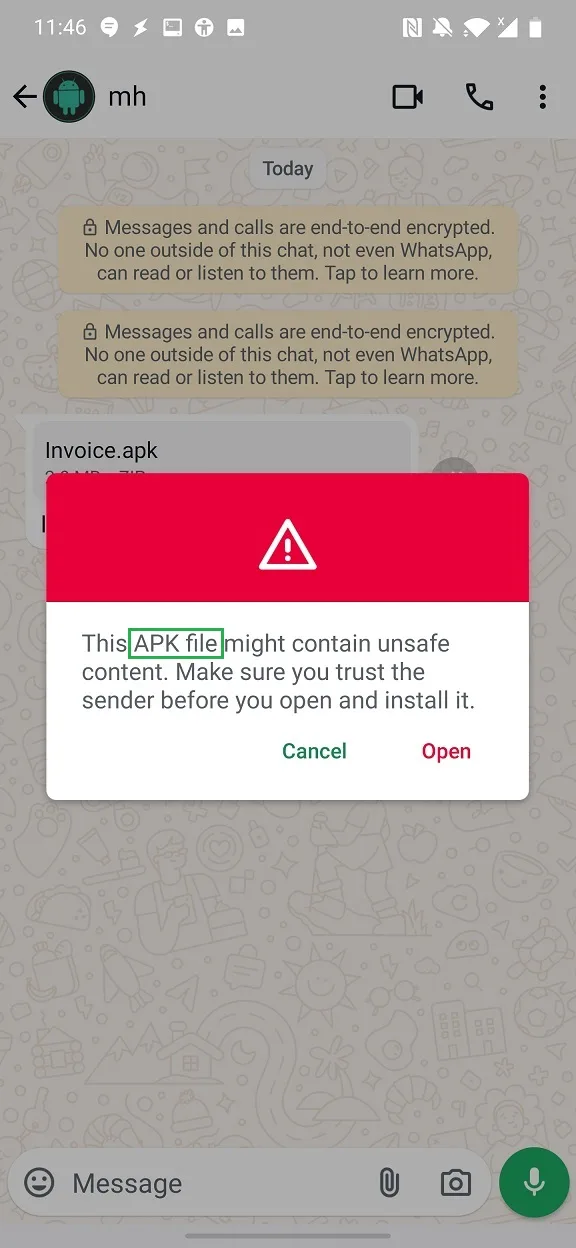
This warning is reasonable; however, it explicitly says a document, not an application. There is a small text difference between sharing APK file with manipulated extension (Figure 2) and regular method of sharing APK file in the WhatsApp Messenger app, see Figure 3. In the second case is file recognized as APK, not as document.
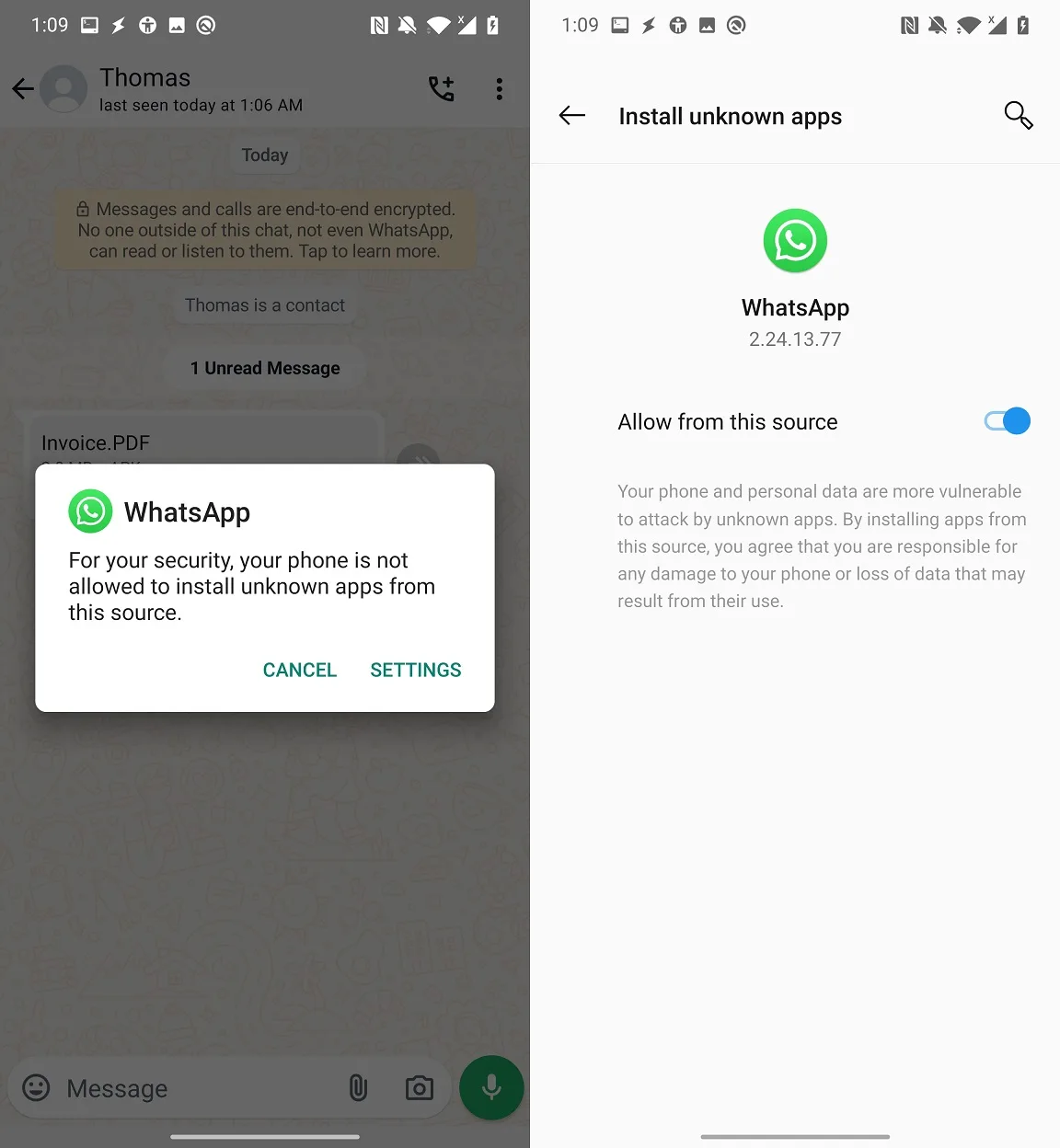
When clicked on Open, WhatsApp requests user to allow WhatsApp Messenger to install apps from unknown sources, see Figure 4. If this is already allowed, then this step is skipped.
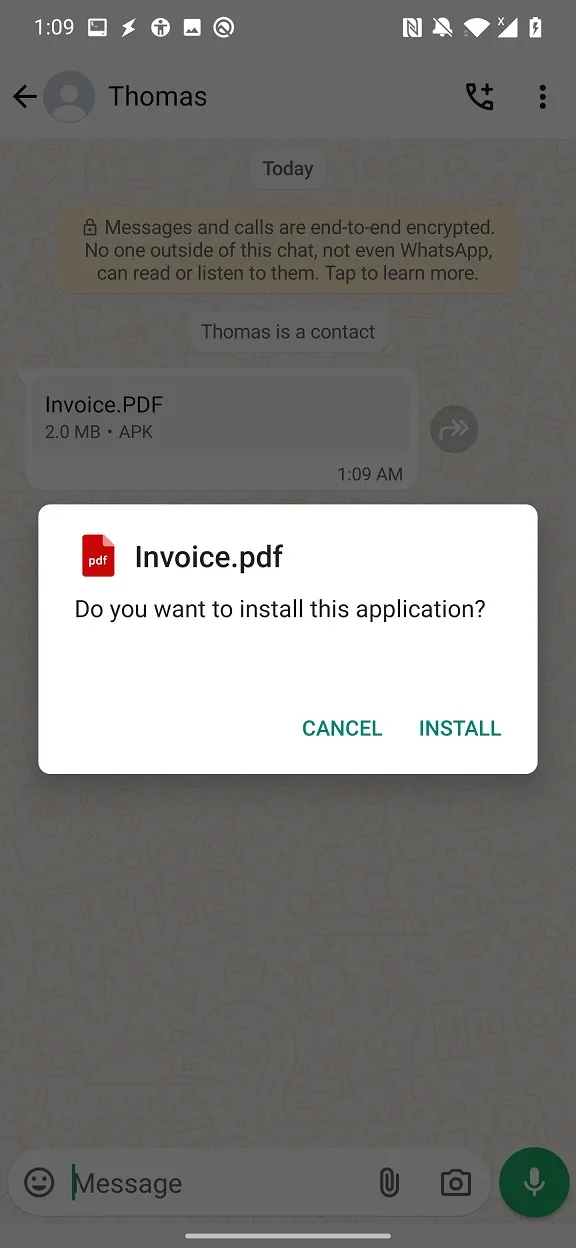
User is then asked to install an app from attachment, see Figure 5.
Besides WhatsApp Messenger for Android, I also tested WhatsApp Web and Desktop for Windows.
Good news for those who use WhatsApp on their computers, because it doesn’t affect WhatsApp Web or the Desktop app. This means that even if someone tries to trick you by changing a file’s name, it won’t make you download or run any harmful software. I’ve tested this with both APK and EXE files. WhatsApp didn’t recognize the right file type, however, downloaded file wasn’t executable. Interestingly, WhatsApp showed a preview image of the file based on its fake name, not based on file header. So, while the bug is sneaky, it’s less of a worry if you’re using WhatsApp on your computer. See Figure 6 and Figure 7.
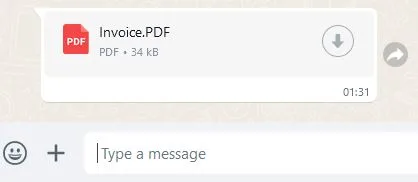
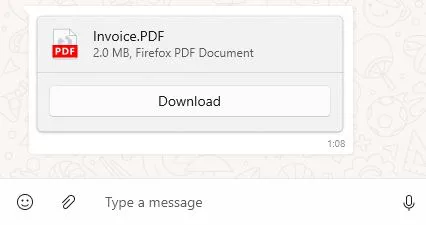
Think twice before opening similar attachments, in the Figure 8 you can see a comparison of specially crafted Android app with manipulated extension and legitimate PDF file shared in the WhatsApp chat. As a difference, WhatsApp recognized file extension, number of pages and displays the preview.
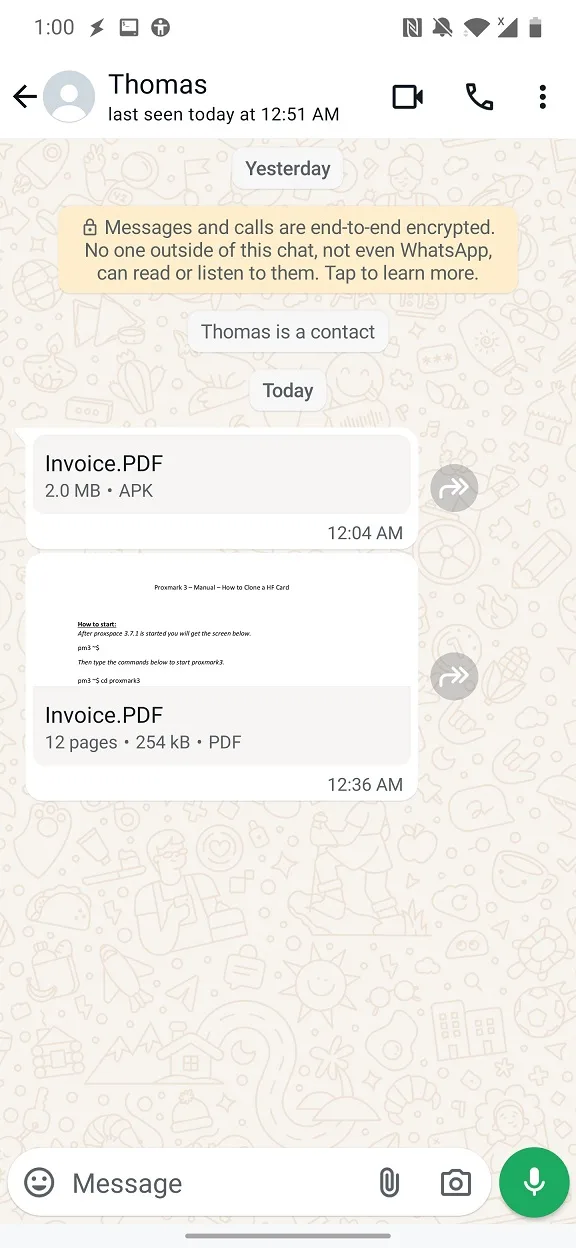
Additionally, use security software that can help to identify and remove downloaded or installed malicious apps that had manipulated extension.
Exploiting this trick can easily mislead non-tech-savvy users into installing a malicious app that impersonates a PDF document. The trick lies in manipulating the file extension within the WhatsApp Messenger using API interface.
There are already cases when Android malware was spread via WhatsApp as regularly shared app that needs to be manually installed. This technique could add an extra layer to mislead a potential victim into installing a harmful app.
如有侵权请联系:admin#unsafe.sh