2024-7-23 00:0:11 Author: securityboulevard.com(查看原文) 阅读量:13 收藏

After bringing together the French security community at an in-person event, GitGuardian hosted CodeSecDays, its annual worldwide gathering for the software security community. This global event brought together leading experts from Snyk, Docker, CyberArk, Chainguard, and CircleCI, for a full-day immersion in software supply chain security. It featured informative presentations and discussions on cybersecurity challenges and best practices in the industry. If you couldn't attend, here are some highlights from the conversations and roundtables!
Roundtable 1: How to augment DevSecOps with AI?
CodeSec Days 2024 began with a discussion of integrating AI into DevSecOps, featuring Mackenzie Jackson from GitGuardian, Antonio Maio from Protiviti, Sonya Moisset from Snyk, and Christian Dupuis from Docker. The conversation highlighted the dichotomy between the excitement around AI's potential and the fears related to its risks and new attack surfaces.
The panelists collectively acknowledged AI as an inevitable part of today's and future computing environments, describing the urgency for businesses to appropriately integrate AI while mitigating the associated risks. The early adopters of AI come from all ends of the enterprise spectrum, with notable enthusiasm from top management down to everyday coders. However, many within the industry remain ambivalent due to concerns over new vulnerabilities, with a segment still lagging in innovation adoption.
Sonya Moisset emphasized the need for awareness and vigilance when using generative AI tools, highlighting vulnerabilities like the introduction of security flaws into codebases. Mackenzie Jackson elaborated on this by discussing the infeasibility of using vanilla large language models (LLMs) for all tasks, pointing out their computational expense and the necessity for specialized tools that enrich data with context. Antonio Maio echoed these sentiments, stressing on the importance of updating policies around AI usage and monitoring shadow AI where employees might bypass approved tools.
A deep dive into AI's implications on the supply chain revealed that AI increases the attack surface and complexity. Sonya provided examples of how AI chatbots could be compromised through prompt injections, while Mackenzie underlined AI hallucinations as another flawed aspect. These potential threats necessitate a thorough rethinking of security protocols and the introduction of regulatory measures to ensure accountability, as mentioned by Sonya.
Key Takeaways
- Multifaceted Impact of AI: AI adoption in organizations is being driven from both top management and grassroots levels, with varying degrees of enthusiasm across different sectors.
- Security Risks of AI: The deployment of generative AI tools must be met with strong security guardrails to prevent vulnerabilities such as prompt injections and AI hallucinations.
- Supply Chain Vulnerabilities: AI tools introduce significant supply chain risks, requiring companies to enhance their security postures and monitor third- and fourth-party tool usage.
- Need for Specialized AI: Out-of-the-box LLMs are often inadequate. Training specialized models and integrating contextual understanding can bridge the gap in cybersecurity-related AI applications.
- Promising Future: The panelists remain optimistic about AI's potential to democratize technology access, enhance productivity, and unlock unprecedented innovation, provided that robust security and regulatory frameworks are established.
Three Tips To Use AI Securely at Work
How can developers use AI securely in their tooling and processes, software, and in general? Is AI a friend or foe? Read on to find out.
 GitGuardian Blog – Code Security for the DevOps generationGreg Bulmash
GitGuardian Blog – Code Security for the DevOps generationGreg Bulmash

Session: Address Security Issues Before They Hit Production
Through a live demonstration, Christian Dupuis, Senior Principal Engineer at Docker, showcased Docker Scout's practical applications for identifying and mitigating security vulnerabilities before they reach production.
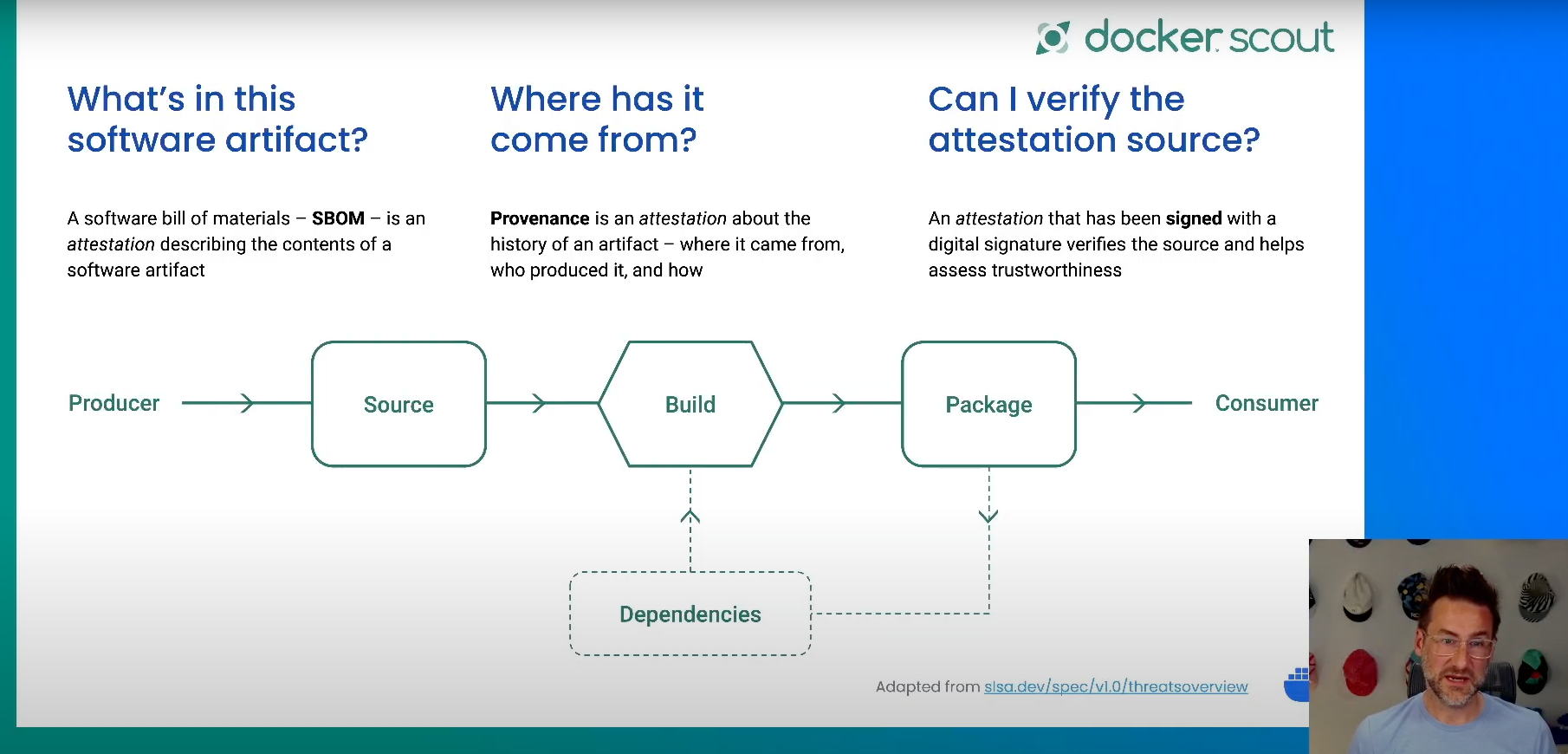
Docker Scout tackles supply chain security comprehensively by focusing on the dependency layer, build environment, and policy enforcement. The journey from source code to a deployable artifact involves numerous dependencies, each potentially carrying security vulnerabilities. Docker Scout integrates deeply with the Docker ecosystem, leveraging Docker’s extensive repository of official and verified images to provide trusted base layers for developers. This aids in preventing the deployment of compromised code from untrusted sources.
Attestations play a crucial role by providing metadata about software artifacts, such as Software Bill of Materials (SBOM), provenance, and vulnerability exploitability exchange (VEX). These attestations need to be signed to ensure authenticity. Docker Scout efficiently stores, manages, and applies policies across all stages of the software lifecycle, from a developer’s local environment to CI pipelines and production environments. This empowers developers to continuously verify the trustworthiness of the components they utilize. With Docker Scout, developers can quickly identify vulnerabilities, outdated dependencies, and configuration issues. Appropriately configured policies ensure that only compliant and up-to-date images proceed through the CI pipeline, drastically reducing the security risk before the software is deployed to production.
Key Takeaways
- Comprehensive Security Coverage: Docker Scout ensures security across all stages of the software lifecycle, from development to production.
- Trusted Base Images: Utilizes Docker's vast repository of official and verified images to guarantee the integrity of base layers.
- Policy Enforcement: Real-time policy evaluations prevent the use of outdated, untrusted, or vulnerable images.
- Attestation Utilization: Employs SBOM, provenance, and VEX attestations to convey and verify essential metadata about software.
- Integrated Tools: Features an intuitive Web dashboard and CLI integration for immediate feedback and remediation guidance.
Why you need an SBOM (Software Bill Of Materials)
SBOMs are security analysis artifacts becoming required by more companies due to internal policies and government regulation. If you sell or buy software, you should know the what, why, and how of the SBOM.
 GitGuardian Blog – Code Security for the DevOps generationGreg Bulmash
GitGuardian Blog – Code Security for the DevOps generationGreg Bulmash
Conversation: Fortifying the Software Delivery Pipeline
Dwayne from GitGuardian hosted a detailed discussion with Blake Kizer, a seasoned information security engineer from Tenable, on the intricacies of securing the modern software delivery pipeline. Over the course of the dialogue, they explored the evolving landscape of software pipelines, emphasizing the shift from simple build-and-run processes to highly sophisticated, secure, and automated pipelines.

Extending beyond SBOMs, which are critical for transparency and managing software components, the SLSA (Supply Chain Levels for Software Artifacts) framework encourages the capture of detailed build provenance, verifying every build step and ensuring artifacts are untampered and secure. This detailed documentation and validation process enhances trust in the build integrity, which is crucial for effective incident response and supply chain security.
Yet implementing such security frameworks is arduous and often requires custom solutions and third-party validation, as evidenced by Tenable's extensive eight-month journey to adopt SLSA for their Nessus product. This process involves tight collaboration between development and security teams to ensure thorough dependency checks and build validations. The cultural shift towards integrated security practices within development workflows is paramount for successful implementation.
Dwayne and Blake also discussed Application Security Posture Management (ASPM) tools, which are designed to manage and prioritize the myriad of security alerts generated by various pipeline tools. Effective ASPM tools aggregate these data streams and prioritize risks while maintaining up-to-date application inventories. The ultimate goal is to streamline the decision-making process and enhance the overall security posture, though it remains a challenging task to keep all data sources clean, accurate, and synchronized.
Key Takeaways:
- Integration of Security in Pipelines: Modern pipelines integrate comprehensive security checks directly with automated build systems, moving beyond traditional build-test-run models.
- SBOMs and SLSA Provenance: SBOMs provide crucial insights into software components, but frameworks like SLSA add depth, capturing and verifying build processes to enhance trust and security.
- Collaboration and Culture Shift: Successful security implementation requires close collaboration between development and security teams and a shift towards a security-first culture throughout the development lifecycle.
- Challenges of Implementation: Implementing frameworks like SLSA in the real world can be complex and resource-intensive, often necessitating custom solutions and external validation.
- Effective Use of ASPM Tools: Efficient ASPM tools are critical for managing security alerts, prioritizing risks, and ensuring application inventories are current and accurate to maintain a strong security posture.
Supply Chain Security: What is SLSA? (Part I)
Attacks on software supply chains have been around for some time, but recently they have evolved into much more dangerous threats. Let’s dive into the SLSA framework to understand where supply chain security is headed.
 GitGuardian Blog – Code Security for the DevOps generationGuest Expert
GitGuardian Blog – Code Security for the DevOps generationGuest Expert

Roundtable 2: How to build a better security and developer relationship?
In this second roundtable, Rachel Stephens, Sonya Moisset, and Christian Dupuis were joined by Eric Fourrier, CEO and co-founder of GitGuardian, Kaylin Trychon, Olaf Molenveld, technology advisor at CircleCI, and Kaylin Trychon, VP of marketing at ChainGuard.
Open source security is a dynamic and increasingly critical aspect of the software supply chain. The recent XZ attack has intensified the conversation, highlighting divergent views among proponents and skeptics of open source. The incident ultimately underscores the need for collective action to secure the software ecosystem. High-profile cases like XZ and Log4j have spurred governmental and foundational initiatives, with notable contributions from bodies such as the OpenSSF and projects like Sigstore. These efforts aim to build more robust security frameworks, stressing the importance of both technical and human aspects of security.
The Open-Source Backdoor That Almost Compromised SSH
The open-source world narrowly escaped a sophisticated supply-chain attack that could have compromised countless systems. A stark reminder of the necessity of vigilant monitoring and rigorous vetting within the open-source ecosystem to maintain trust and security.
 GitGuardian Blog – Code Security for the DevOps generationThomas Segura
GitGuardian Blog – Code Security for the DevOps generationThomas Segura

The response to security incidents reveals broader truths about the open-source community: while it is vulnerable to sophisticated attacks, it is also highly resilient and collaborative. Security breaches often stem from complex human factors, such as social engineering and maintainer burnout, which can compromise even the most well-maintained projects. This dual reality highlights the necessity for holistic solutions that include technological defenses and strong community support systems, ensuring maintainers are well-supported and educated about potential threats.
Supply chain security involves more than just technology; it requires comprehensive strategies that incorporate developer education, effective tooling, and streamlined processes. Staying up to date with dependencies and tools, verifying software provenance, and employing effective security information and event management (SIEM) systems are foundational practices. Organizations must develop these capabilities alongside fostering a security-first culture, which includes clear communication and close collaboration between security teams and developers.
The focus must be on making security practices as seamless and unintuitive as possible for developers. This involves integrating security tools directly into development workflows, automatic signing and verification, and ensuring observable and actionable security data. Future progress lies in creating environments where the secure path is also the path of least resistance, combining developer-friendly tools with robust educational initiatives to form a resilient security culture.
Key Takeaways
- Holistic Security: Effective security encompasses both technical measures and the human element, supporting maintainers to reduce burnout and susceptibility to social engineering.
- Education and Awareness: Continuous education and awareness programs are essential to make developers understand and participate actively in securing the software supply chain.
- Effective Tooling: Integrating user-friendly security tools into developers' existing workflows is critical in ensuring adherence to security practices without hindering productivity.
- Up-to-date Practices: Keeping tools and dependencies consistently updated, verifying software provenance, and automating as many processes as possible are vital steps in securing the supply chain.
- Community and Collaboration: Strong community support and clear communication between security and development teams are crucial in building a secure software ecosystem.
Secrets management takes more than just tools
Can you just purchase a tool to give you good security posture? Discover how People, Processes, and Tools elevate code security to protect against data breaches.
 GitGuardian Blog – Code Security for the DevOps generationDwayne McDaniel
GitGuardian Blog – Code Security for the DevOps generationDwayne McDaniel
Session 5: Unlock Use Cases for Successful Secrets Security
In this session, Dwayne McDaniel from GitGuardian was joined by Uzi Ailon and Evan Litwack from CyberArk to discuss how developers play a crucial role in cybersecurity, particularly in machine identities, secrets management, and preventing "vault sprawl."
Uzi and Evan emphasized that in today's tech landscape, developers are integral to security; writing secure code, avoiding vulnerabilities, and preventing hard-coded credentials are crucial steps they should incorporate daily. Both human and machine identities operate similarly—relying on credentials for resource access. However, machine identities face unique challenges due to their lack of secure storage systems, making secret management essential.
Machine identity needs authentication methods based on 'what the application is' rather than 'what it knows' to avoid the recursive issue of needing credentials to access credentials. They extend the discussion to workload identities, explaining the growing complexity in modern applications where multiple services might require individual credentials for different tasks.
Securing your machine identities means better secrets management
Machine identities make up the majority of the over 12.8 million secrets GitGuardian discovered in public in 2024. Let’s look at how we got here and how we fix this.
 GitGuardian Blog – Code Security for the DevOps generationDwayne McDaniel
GitGuardian Blog – Code Security for the DevOps generationDwayne McDaniel

Vault sprawl, a significant problem caused by developers using various vaults (like AWS Secrets Manager, Azure KeyVault, etc.), leads to scattered credentials across multiple platforms, complicating governance and security. The panelists advocated for centralized vault management, which can systematically control and audit these dispersed credentials. This centralization is vital for ensuring that all secrets are continuously and efficiently managed.
Integrating vault management deeply into CI/CD processes and leveraging automation wherever possible helps ensure both secure and efficient code development. Continuous monitoring tools like GitGuardian help capture accidental secret exposure before it escalates.
Key Takeaways:
- Developer Responsibility: Developers must integrate security into their daily work, ensuring secure coding practices and avoiding the pitfalls of hard-coded credentials.
- Machine vs. Human Identity Management: Reinforce machine identity authentication based on inherent application properties to prevent recursive credential dependencies.
- Vault Sprawl Challenges: Centralize vault management to handle credentials scattered across various environments and applications efficiently.
- Ease of Integration: Security tools and vaults should integrate seamlessly into developers' workflows, ensuring minimal disruption and promoting widespread adoption.
- Continuous Monitoring and Automation: Use automation and continuous monitoring to manage new and existing credentials, maintaining high standards of security and compliance.
End-to-end secrets security with CyberArk and GitGuardian
In this guide, we’ll walk you through integrating CyberArk Conjur with GitGuardian, step by step.
 GitGuardian Blog – Code Security for the DevOps generationFerdinand Boas
GitGuardian Blog – Code Security for the DevOps generationFerdinand Boas

Wrapping Up
As we conclude CodeSecDays, it's clear that the landscape of software security is evolving rapidly, presenting both challenges and opportunities. Throughout our sessions, we've explored the transformative impact of AI in DevSecOps, the critical importance of securing software supply chains, and the need for stronger collaboration between security teams and developers.
As we look to the future, it's exciting to see the innovative solutions and collaborative efforts emerging to address these challenges. By working together, sharing knowledge, and continuously improving our practices, we can build a more secure digital world for everyone.
Thank you to all our speakers, panelists, and attendees for making CodeSecDays a success. Let's carry this momentum forward, applying these insights to create more robust, secure, and resilient software ecosystems. Here's to a safer digital future!
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Code Security for the DevOps generation authored by Thomas Segura. Read the original post at: https://blog.gitguardian.com/codesecdays-2024/
如有侵权请联系:admin#unsafe.sh