
Since 2022, our security research team has been keeping a close eye on API-related data breaches, 2024-7-22 21:52:41 Author: securityboulevard.com(查看原文) 阅读量:11 收藏

Since 2022, our security research team has been keeping a close eye on API-related data breaches, especially as we were ramping up to finalize our first product version. Our goal has been to identify the vulnerabilities that attackers commonly exploit so we can enhance Escape's scanner to better detect these issues.
API-related breaches made headlines this year (like Twilio's Authy Breach or Life360). So, it's never been so crucial for organizations to stay updated on what's happening in their industry and learn from others' mistakes.
Thus, given that open-source projects are an essential part of our DNA, we’ve decided to make our API data breach database publicly accessible!
We hope this will help others strengthen their own security measures and avoid similar pitfalls. By sharing our findings, we hope to foster a collaborative environment where knowledge is openly exchanged, and everyone in security community can benefit from improved protection against API-related threats.
If you have any questions or need further insights, feel free to reach out!
What is The API Threat Landscape?
The API Threat Landscape is a curated public instance of Escape Security Research’s team database, summarizing information about publicly disclosed API security data breaches.
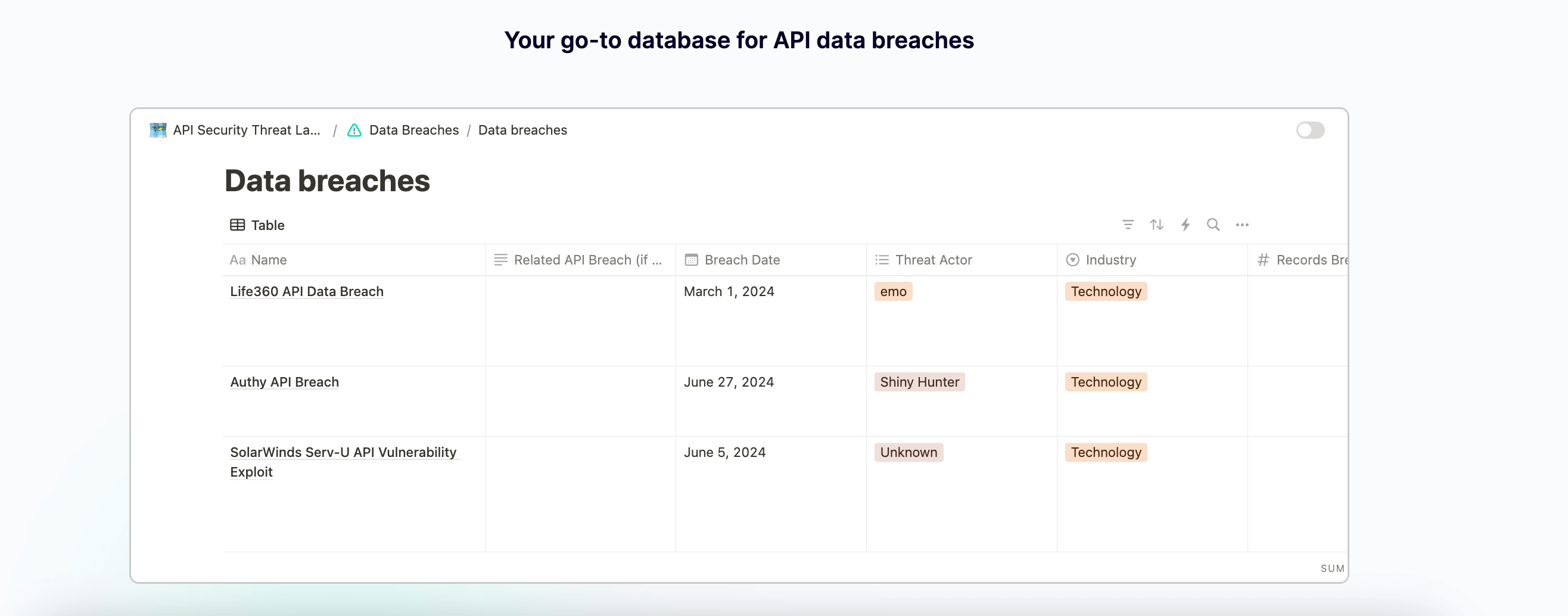
The database lists:
Security incidents: A historical collection of past API security incidents and campaigns, offering insights into targeting patterns, exploitation methods and effective impact.
Targeted API secrets: Analysis of frequently targeted API secret types found in exposed environments
Threat actors: Profiles of threat actors involved in API security incidents, shedding light on their potential motivations.
CVE: A list of CVEs associated with each incident.
and provides OWASP Top 10 classification.
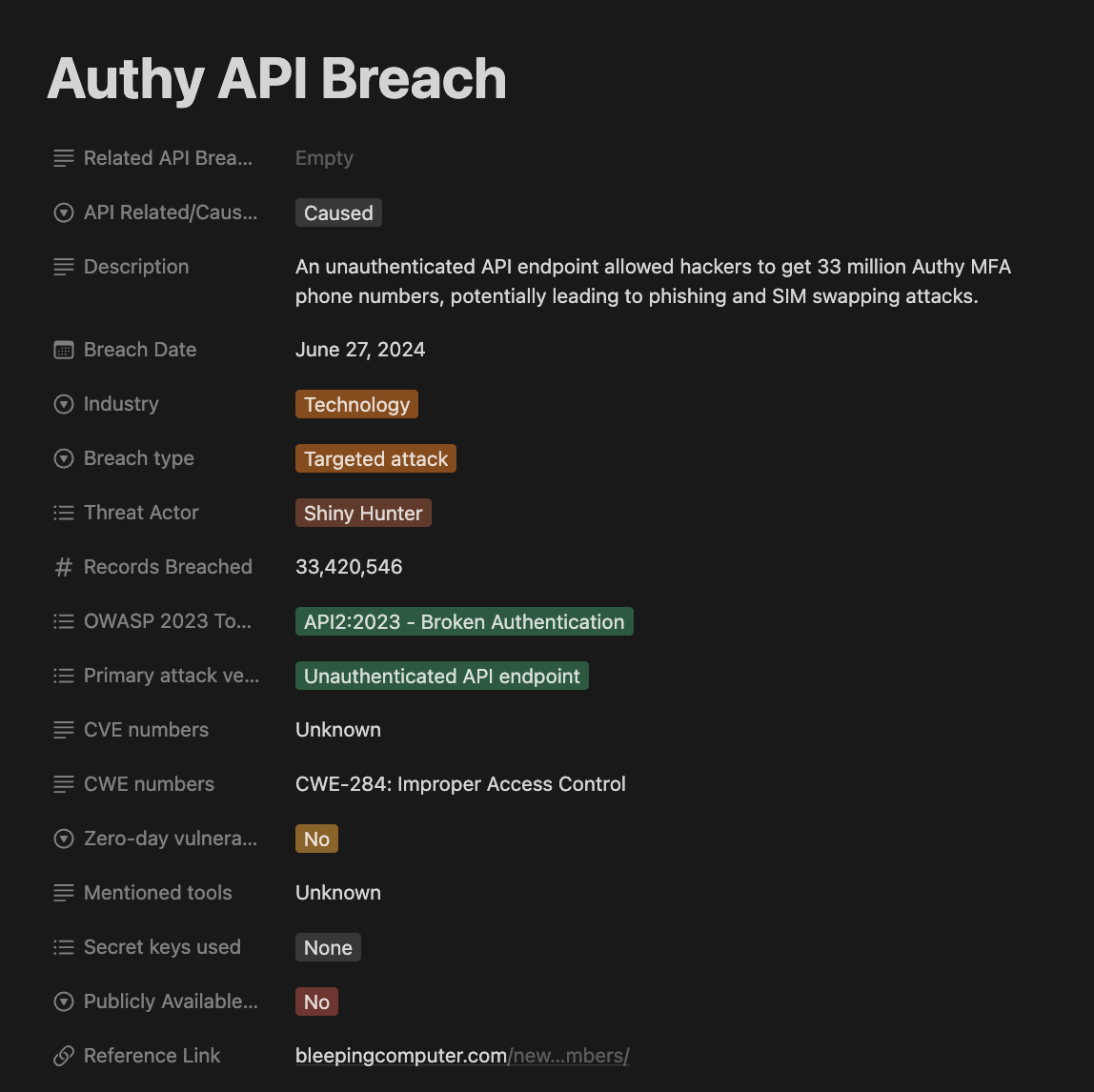
Every entry in the API Threat Landscape is backed by references to well-known external sources of information.
We deployed a web crawler as a baseline to find the most significant breaches—those most likely to be reported by well-known cybersecurity media.
The data underwent a three-step filtering process:
- Initial Filtering: We used certain keywords, with 'API' and 'Data Breach' as primary filters.
- Advanced Filtering: We used a LLM as classifier on top of language embedding models to further refine the data, retaining only information regarding data breaches specifically caused by API vulnerabilities or exploits.
- Manual Screening: The final round of screening was conducted manually to cross-verify the data and check multiple sources for the accuracy of the information. This step also helped identify any breaches that may have been initially overlooked.
What is considered an "API threat"?
Our primary focus has been on malicious activities that have exposed sensitive data transmitted through an API to unauthorized systems. These include any breach where the API was utilized as the main attack vector. We looked at scenarios which resulted in unauthorized access, data theft, or unauthorized modification of sensitive information.
We have defined a data breach as an incident where sensitive, protected, or confidential data has been accessed, stolen, or manipulated by an unauthorized party through the misuse or exploitation of an API.
These breaches are often the result of:
- Vulnerabilities in API implementation: Flaws that can be exploited.
- Inadequate security measures: Lack of proper security controls like authentication.
- Malicious exploitation of API endpoints: Deliberate attacks by threat actors.
Initially, we excluded cases where security research revealed API vulnerabilities or bugs that did not lead to the exposure of sensitive data. Our aim was to focus on incidents that had a tangible impact on data security and privacy.
As our research evolved, we recognized the value of including instances of security research. These cases, while not resulting in actual data breaches, provide insights into vulnerabilities and the weaknesses that could be exploited. They help us better understand the landscape of API security threats.
💡
The MOVEit API data breach has significantly impacted over 2,620 organizations. We've decided to include organizations that were the most affected by the breach.
Over the past few years, API-related breaches have evolved significantly, with both the frequency and severity of incidents on the rise. Our in-depth analysis of the database reveals that more than 37 million records have been compromised across 12 major incidents, causing considerable damage to the financials and reputations of the affected organizations.
Over 40% of the breaches analyzed involved vulnerabilities that attackers were aware of, but the organizations' developers were not. Consequently, there was no official fix or patch available, leaving the systems exposed and at risk.
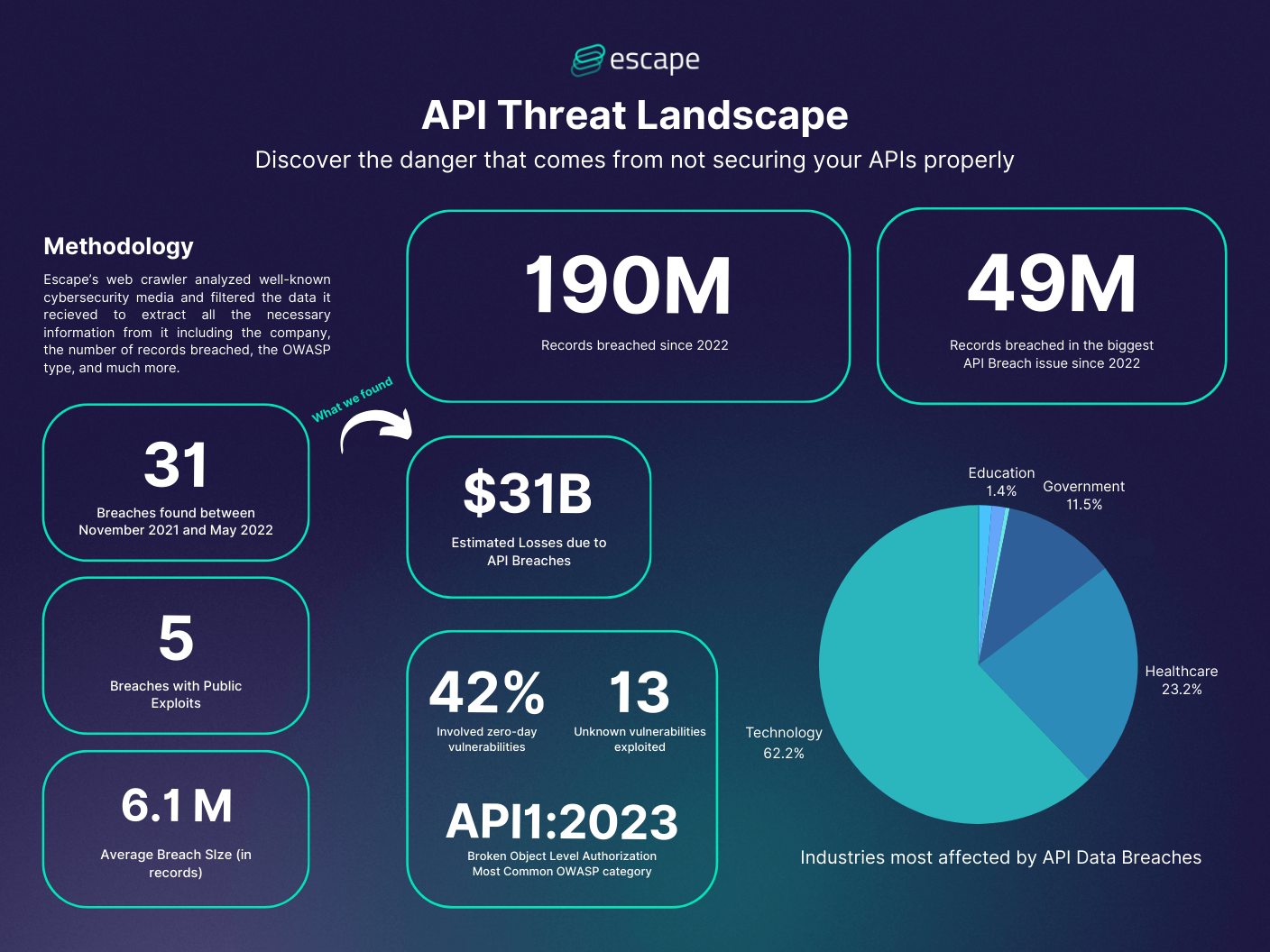
Different industries face varied levels of risk, with technology, healthcare, and government sectors being particularly vulnerable due to the sensitivity of their data and the money attackers believe they can get from the affected organizations. These breaches often lead to severe compliance violations and significant financial repercussions of API breaches, with an estimated $23 billion in potential losses. This underscores the economic ramifications of inadequate API security practices.
The most common vulnerabilities exploited in API breaches included Broken Object Level Authorization and Broken Authentication, as highlighted in the OWASP Top 10 for 2023.
If you want to explore the API threat trends from 2022 to 2024 in-depth, feel free to download our detailed report.
Work in progress
We hope this database proves useful for threat intelligence analysts or securing researchers looking into API security data breaches, incident responders investigating compromised APIs, and the API security community at large.
We are committed to updating our report bi-weekly as part of our ongoing work. Please remember that, as humans, we may make mistakes. If you notice any inconsistencies or wish to contact the Escape Security Research team about this project, please fill out this form.
💡 Want to learn more? Discover the following security research reports:
- Methodology: How we discovered over 18,000 API secret tokens
- The State of GraphQL Security 2024
- The State of Public APIs 2023
*** This is a Security Bloggers Network syndicated blog from Escape - The API Security Blog authored by Alexandra Charikova. Read the original post at: https://escape.tech/blog/introducing-the-api-threat-landscape/
如有侵权请联系:admin#unsafe.sh