
![]()
If you successfully installed NetHunter as described in previous blogs, we can start use its tools. In this blog, I will focus on Duck Hunter provided by NetHunter.
Using DuckHunter allows our TicWatch Pro smartwatches to behave as Rubber Ducky, also known as Bad USB, to perform human interface device (HID) attack. This means that once this attack will be triggered, our watches will behave as keyboard that inject predefined keys on devices we are connected to. You can see a quick demonstration in the video below.
In this blog you will learn how to use Duck Hunter, where from download each Rubber Ducky scripts, upload them on your TicWatch Pro and execute various scenarios that will help you understand how this could be misused by attacker with physical access to your computer.
In the section below, I will use rickroll ducky script payloads available at Hak5 GitHub.
As a first we need to change file permissions for hidg devices so then, NetHunter can control them and send keyboard signals. This must be done after every reboot of watches. Don’t worry if you forget about it, NetHunter will let you know with toast notification that your missed it after launching attack.
- Connect your TicWatch Pro to computer and enable ADB debugging.
- Copy your preferred script to watches. For this test purpose we will use rickroll payload and store it locally on our computer as
rickroll. Scripts needs to be copied to exact location in our watches, soDuckHuntercan see them. Use command:adb push rickroll /sdcard/nh_files/duckyscripts/ - Set world-writable permissions on
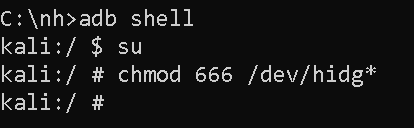
hidg*devices. Invoke sudo shell from computer and change permissions onhidg*devices:chmod 666 /dev/hidg*(see Figure 1.) Alternatively, if on the go, you can use NetHunter Terminal app, see Figure 2. - Open NetHunter app, go to
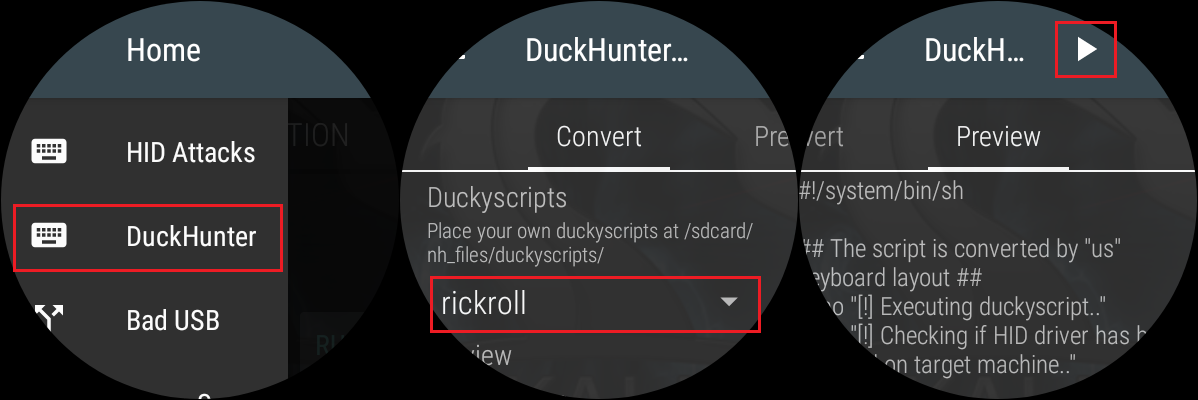
Settings, pickDuckHunter. FromConverttab, scroll down, and choose therickrollscript that we copied earlier. Either slide to left side or manually pickPreviewtab. This action converts the supplied Rubber Ducky scripts likerickroll, into HID format. Press play icon to launch the script. Visible in Figure 3.

If you forget to change the permissions after reboot, you will be informed when launching attack with warning visible in Figure 4. When this happens, repeat point 3.

Besides not granting world-writable permissions on HID interface, I haven’t experienced any other problem during my tests of DuckHunter.
Detecting an HID attack can pose challenges because such a device masquerades as a legitimate keyboard to the host device, and the injected keystrokes may remain invisible to the user. However, several steps can aid in detecting and preventing HID attacks:
- Monitor for unusual activity: Be vigilant about unexpected pop-ups, system messages, or the execution of unfamiliar programs on your device.
- Utilize device control software: Control which devices can connect to your system and block unauthorized ones.
- Safeguard physical access: Rubber Ducky attacks often involve physically inserting the device into a USB port. Securing physical access helps prevent such attacks.
Don’t allow unauthorized people to charge their devices using your laptop.
