Our X-Labs team’s research seems to have discovered and identified basic ransomwar 2024-7-12 20:11:33 Author: www.forcepoint.com(查看原文) 阅读量:7 收藏
Our X-Labs team’s research seems to have discovered and identified basic ransomware targeting Turkish businesses. The attack vector initiates through a PDF attachment disseminated via suspicious emails originating from the "internet[.]ru" domain. The embedded links within the PDF facilitate the download of a subsequent stage exe payload upon user interaction. It encrypts files with “.shadowroot” extension. Currently, ransomware is actively targeting numerous businesses worldwide, including those in the healthcare and online shopping sectors.
Initial Access:
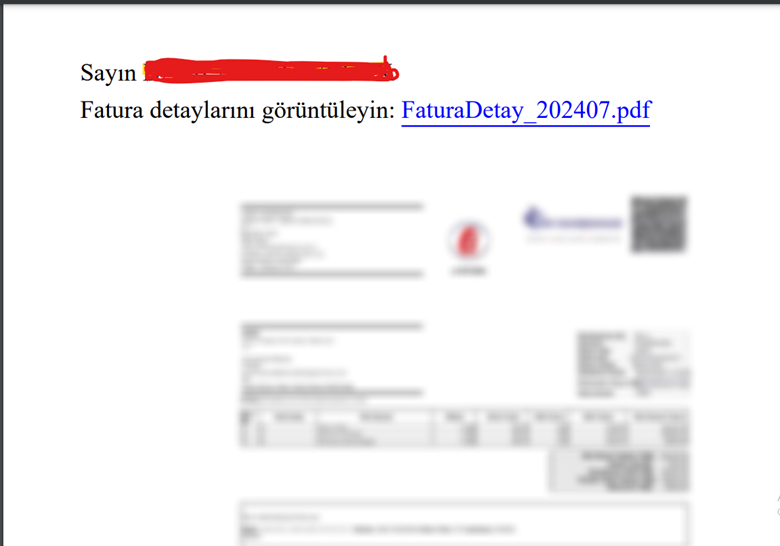
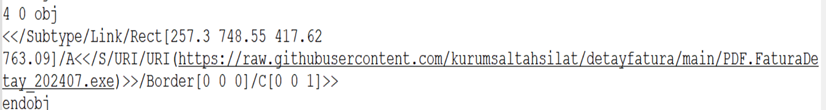
This pdf contains a URL link, which downloads further exe payload from a compromised GitHub account.
hxxps://raw[.]githubusercontent[.]com/kurumsaltahsilat/detayfatura/main/PDF.FaturaDetay_202407.exe
Execution of stage payloads:
The download file is a 32 bit Borland Delphi 4.0 compiled binary. While analyzing exe, it is observed that it drops further payload in “C:\TheDream\RootDesign.exe”, “C:\TheDream\Uninstall.exe” and “C:\TheDream\Uninstall.ini”.
Dropped second stage rootdesign.exe is protected with dotnet confuser core ver 1.6.
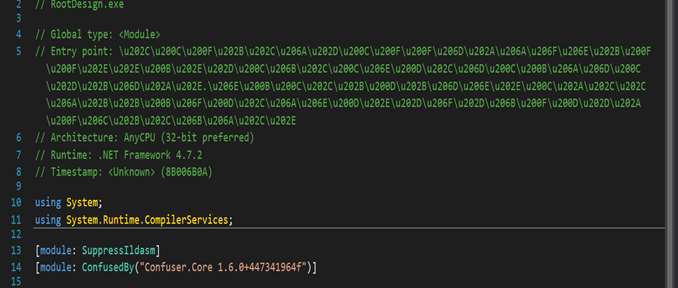
We can see classes with random names having special characters and all function names are obfuscated. It is mostly preferred by malware authors to bypass traditional detection techniques of security applications and it is an open-source protector for .NET applications.
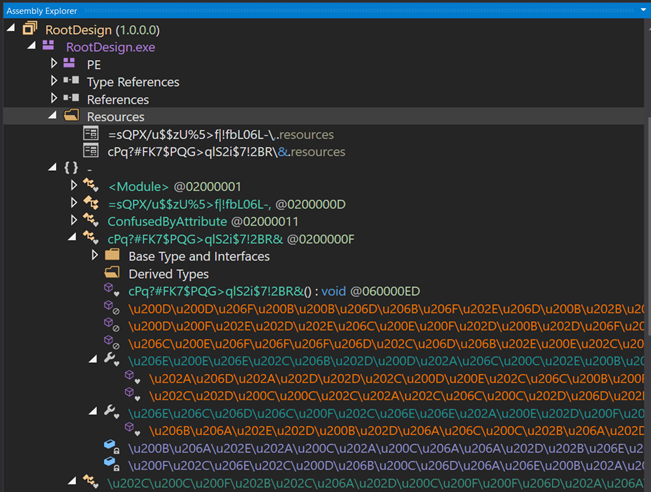
PDF.FaturaDetay_202407.exe after dropping payload it initiates PowerShell to run another hidden PowerShell command to execute RootDesign.exe in hidden mode.
Command:
“”C:\Windows\System32\cmd.exe" /c PowerShell.exe -windowstyle hidden powershell -c C:\TheDream\RootDesign.exe”
Created mutants/mutex:
Local\ZonesCacheCounterMutex
Local\ZonesLockedCacheCounterMutex
_SHuassist.mtx
This dropped file then creates its recursive threads of itself in memory with new PIDs and starts performing encryption.
It logs its every thread activity on root “C:\TheDream\log.txt” by adding a new line comment “ApproveExit.dot”. Its recursive threads also increase memory consumption.
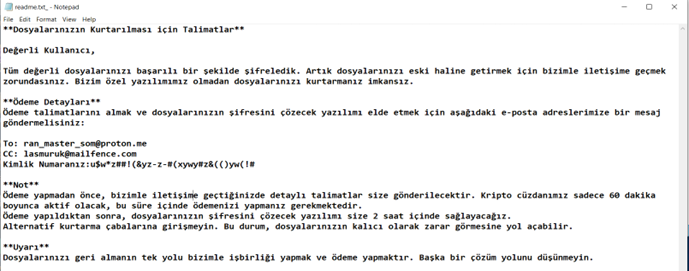
After this it will start performing, encrypting various system-critical non-pe and office files and renaming those files with “.ShadowRoot” extension, dropping readme.txt.

Readme.txt shows ransom notes in Turkish and encrypted files are dropped on desktop.
There is no direct crypto wallet ID info mentioned, but it is asking victims via readme to contact via the provided email address for further payment processing via crypto wallet and decryption tools.
We have observed recursive self-process creation by RootDesign.exe, which causes the files to get encrypted multiple times, resulting in higher memory consumption. It also drops many copies of encrypted files on the root. As highlighted in the screenshot the file extensions are also appended multiple times.
Standard AESCryptoServiceProvider .Net class is observed in the code.
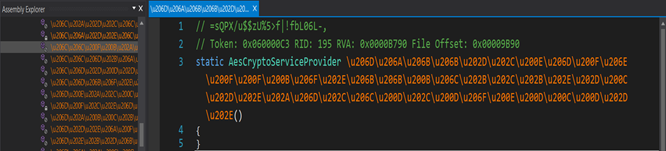
It is the most commonly used class in .net compiled binary and in powershell scripts.
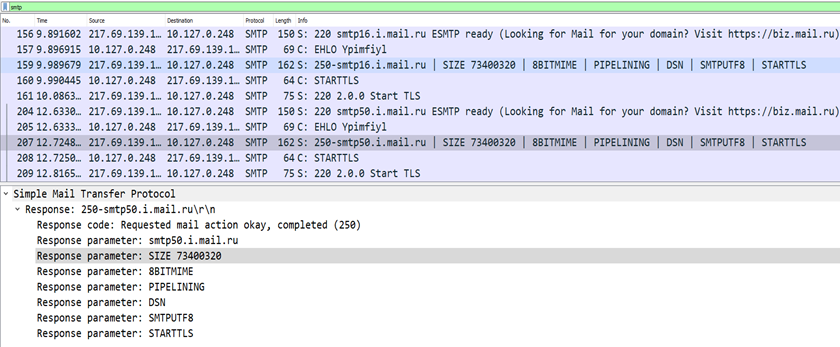
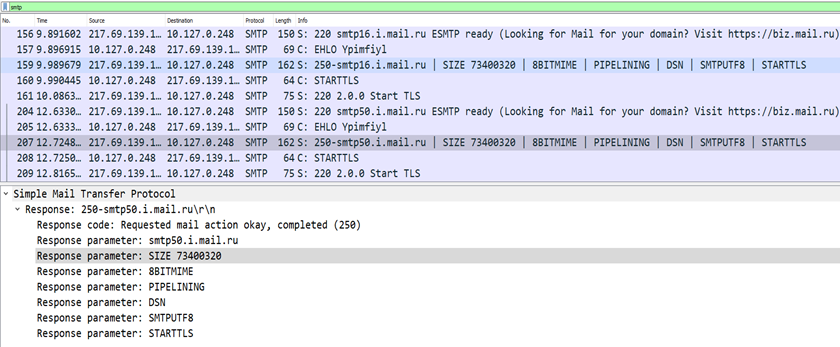
It performs SMTP C2 connection on smtp[.]mail[.]ru on port 587. Then it sends details via email service to suspicious accounts username: kurumsal[.]tasilat @internet[.]ru, which is also used as a sender domain.
Conclusion:
This ransomware seems to be targeting Turkish businesses by sending suspicious fake PDF invoices and urging users to click on malicious links. It downloads suspicious Delphi payload and then drops dotnet confuser protected binary for further activity. It encrypts files with “.ShadowRoot” extension and connects to a Russian SMTP mail server. This ransomware appears to a relatively rudimentary, likely the work of an inexperienced developer, exhibiting some basic functionality.
Protection statement:
Forcepoint customers are protected against this threat at the following stages of attack:
- Stage 2 (Lure) – Malicious PDF attachments associated with these attacks are identified and blocked.
- Stage 5 (Dr.opper File) - The dropper files are added to Forcepoint malicious database and are blocked.
- Stage 6 (Call Home) - Blocked C2 credentials
IOCs
Payload HASH:
- CD8FBF0DCDD429C06C80B124CAF574334504E99A
- 1C9629AEB0E6DBE48F9965D87C64A7B8750BBF93
Download URL:
- hxxps://raw[.]githubusercontent[.]com/kurumsaltahsilat/detayfatura/main/PDF.FaturaDetay_202407.exe
Email addresses to block:
- Kurumsal[.]tasilat[@]internet[.]ru
- ran_master_som[@]proton[.]me
- lasmuruk[@]mailfence[.]com

Mayur Sewani
Mayur serves as a Senior Security Researcher as part of the Forcepoint X-Labs Research Team. He focuses on APT malwares, information stealers, phishing attacks, and also works to stay on top of the latest threats. He is passionate about advancing the field of defensive adversary...
Forcepoint is the leading user and data protection cybersecurity company, entrusted to safeguard organizations while driving digital transformation and growth. Our solutions adapt in real-time to how people interact with data, providing secure access while enabling employees to create value.
如有侵权请联系:admin#unsafe.sh