Two protocols stand out in the realm of identity and access management: OpenID Connect (OIDC) and Security Assertion Markup Language (SAML). Both serve similar purposes but differ in their approach, implementation, and use cases. This article provides a deep technical dive into OIDC and SAML, comparing their architectures, examining their differences, and exploring their integration with authentication and authorization systems.
OpenID Connect (OIDC)
OpenID Connect is an identity layer built on top of the OAuth 2.0 protocol. It allows clients to verify end-users identities based on the authentication performed by an authorization server and to obtain basic profile information about the end-user in an interoperable and REST-like manner.
Key Components
- Identity Provider (IdP): Authenticates users and issues ID tokens.
- Relying Party (RP): The application relies on the IdP for authentication.
- ID Token: A JWT (JSON Web Token) containing claims about the authentication event and user.
- UserInfo Endpoint: An API that returns claims about the authenticated user.
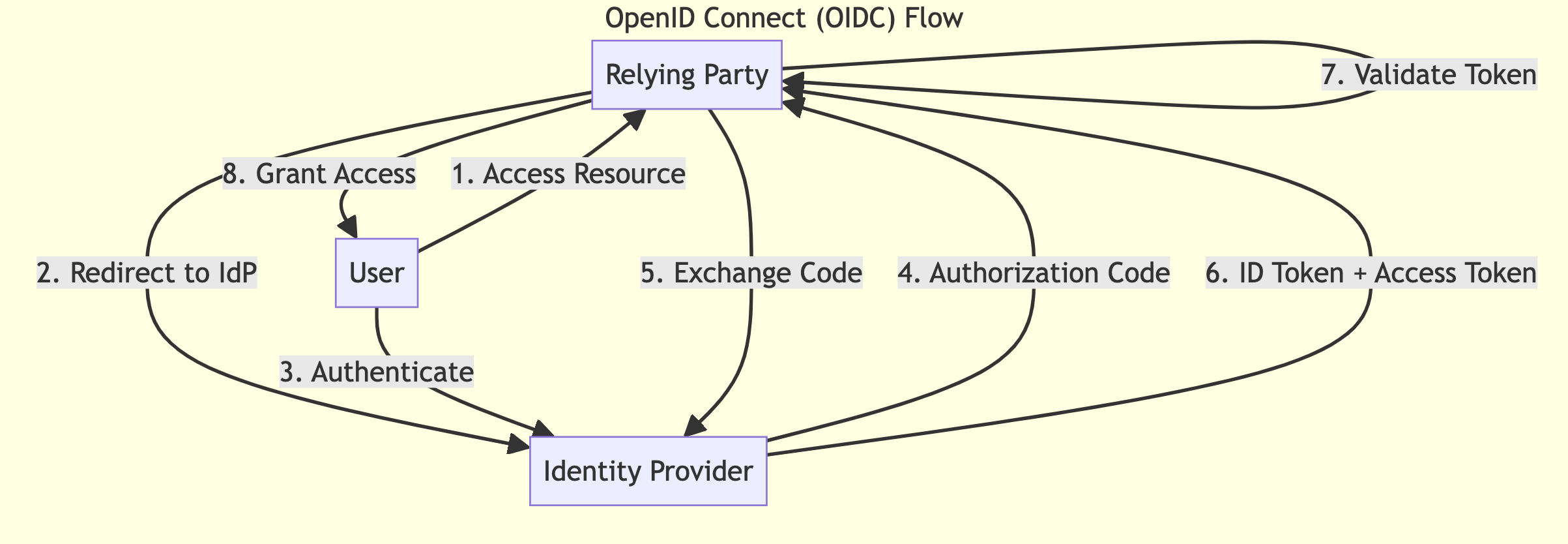
Flow
- The user attempts to access a protected resource on the RP.
- The RP redirects the user to the IdP for authentication.
- The user authenticates with the IdP.
- The IdP issues an authorization code to the RP.
- The RP exchanges the code for an ID token and, optionally, an access token.
- The RP validates the ID token and extracts user information.
- (Optional) The RP uses the access token to request additional user information from the UserInfo endpoint.
Security Assertion Markup Language (SAML)
SAML is an XML-based open standard for exchanging authentication and authorization data between parties, specifically between an Identity Provider and a Service Provider.
Key Components
- Identity Provider (IdP): Authenticates users and issues SAML assertions.
- Service Provider (SP): The application relies on the IdP for authentication.
- SAML Assertion: An XML document containing claims about the authentication event and user.
- Metadata: XML documents describing the configuration of SAML entities.
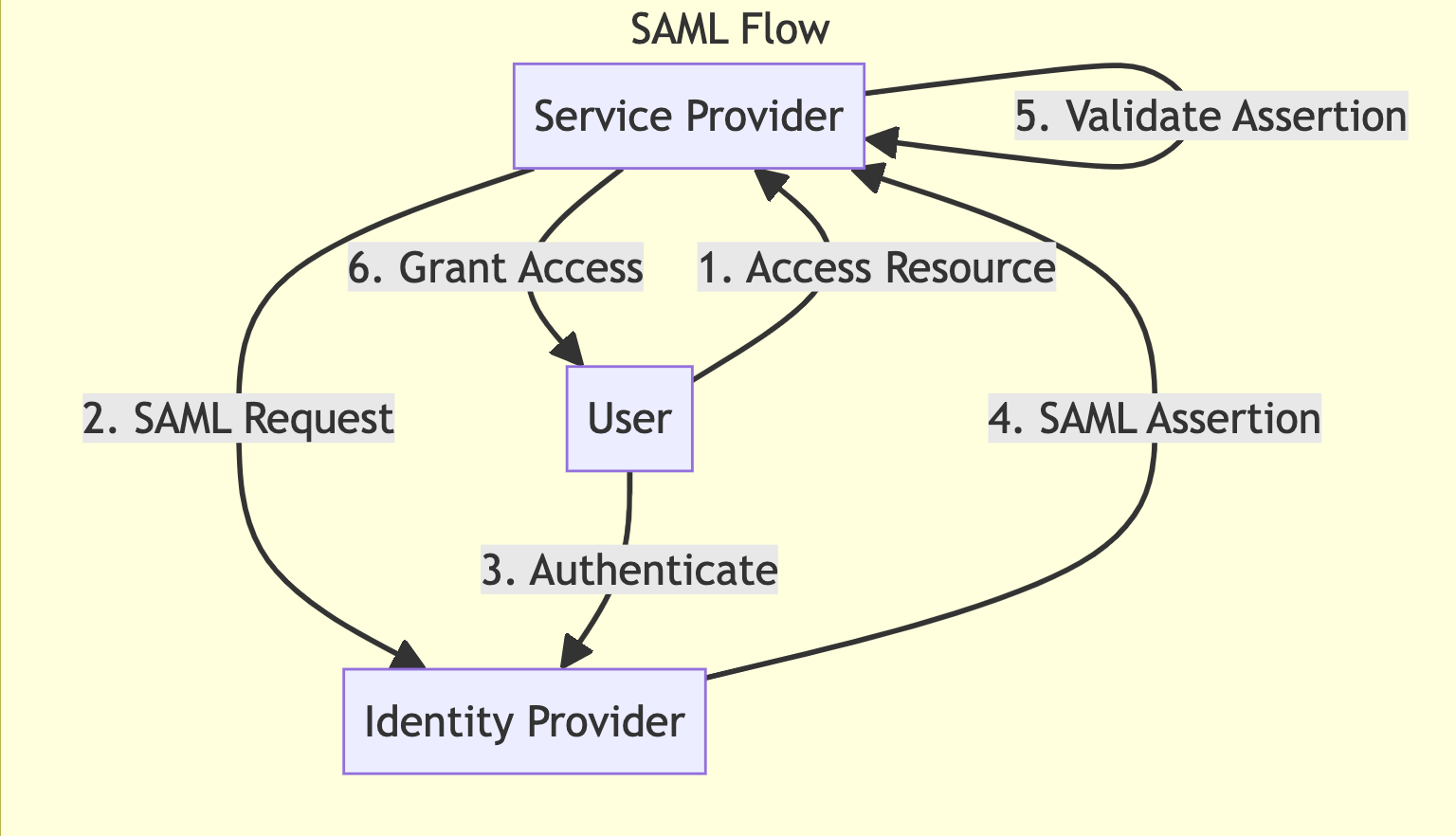
Flow
- The user attempts to access a protected resource on the SP.
- The SP generates a SAML authentication request and redirects the user to the IdP.
- The user authenticates with the IdP.
- The IdP generates a SAML assertion and returns it to the SP via the user's browser.
- The SP validates the SAML assertion and extracts user information.
- The SP grants access to the protected resource.
Key Differences
Protocol and Format
- OIDC: Built on OAuth 2.0, uses JSON/JWT for tokens and claims.
- SAML: Standalone protocol, uses XML for assertions and metadata.
Complexity
- OIDC: Generally simpler to implement and understand, especially for developers familiar with OAuth 2.0.
- SAML: More complex, with a steeper learning curve due to its XML-based nature and more extensive specification.
Token Format
- OIDC: Uses compact, URL-safe JWTs which can be easily parsed and validated.
- SAML: Uses XML-based assertions which are more verbose but potentially more expressive.
Discovery and Metadata
- OIDC: Provides dynamic discovery of IdP metadata via well-known URIs.
- SAML: Typically requires manual exchange of metadata XML files.
Mobile and Native App Support
- OIDC: Better suited for mobile and native applications due to its JSON-based nature.
- SAML: Primarily designed for web applications, can be challenging to implement in mobile environments.
Key Use Cases
OIDC Use Cases
- Single Sign-On for Consumer Applications: Ideal for consumer-facing apps that need to integrate with social login providers.
- Mobile and Native Applications: Better suited for mobile environments due to its lightweight nature.
- API Authentication: Can be used to secure APIs in conjunction with OAuth 2.0.
- Microservices Architecture: Well-suited for service-to-service authentication in microservices environments.
SAML Use Cases
- Enterprise Single Sign-On: Widely adopted in enterprise environments for web-based SSO.
- Federated Identity Management: Excellent for scenarios where organizations need to share identity information across trust boundaries.
- Government and Healthcare Sectors: Often preferred in highly regulated industries due to its maturity and extensive security features.
- Education Sector: Commonly used in academic environments for federated access to research resources.
Integration with Authentication and Authorization Systems
Both OIDC and SAML can be integrated with various authentication and authorization systems. Here's how:
OIDC Integration
- Authentication Systems:
- Implement the OIDC IdP role in your existing authentication system.
- Expose the necessary OIDC endpoints (authorization, token, userinfo, etc.).
- Generate and sign JWTs for ID tokens.
- Authorization Systems:
- Use the OAuth 2.0 scopes mechanism to define and enforce access controls.
- Implement token introspection for validating access tokens.
- Use JWT claims for fine-grained authorization decisions.
SAML Integration
- Authentication Systems:
- Implement the SAML IdP role in your existing authentication system.
- Generate SAML assertions with the necessary attributes and claims.
- Implement SAML endpoints for receiving authentication requests and sending responses.
- Authorization Systems:
- Use SAML attributes in the assertion for making authorization decisions.
- Implement XACML (eXtensible Access Control Markup Language) for more complex authorization scenarios.
- Use SAML attribute queries for fetching additional user attributes for authorization.
Common Integration Patterns
- Bridging: Implement both OIDC and SAML support in your system to cater to different client requirements.
- Token Translation: Convert between SAML assertions and OIDC tokens to support legacy systems.
- Federation: Use either protocol to establish trust relationships between different organizations or domains.
- Multi-Factor Authentication: Extend both protocols to support additional authentication factors.
Conclusion
Both OIDC and SAML are robust protocols for identity federation and single sign-on. OIDC, with its simplicity and mobile-friendliness, is often preferred for modern, consumer-facing applications. SAML, with its maturity and extensive feature set, remains a strong choice for enterprise environments and sectors with stringent security requirements.
The choice between OIDC and SAML often depends on specific use cases, existing infrastructure, and client requirements. Many organizations choose to support both protocols to maximize flexibility and interoperability. Regardless of the chosen protocol, proper implementation and security best practices are crucial for maintaining a robust identity and access management system.
*** This is a Security Bloggers Network syndicated blog from Meet the Tech Entrepreneur, Cybersecurity Author, and Researcher authored by Deepak Gupta - Tech Entrepreneur, Cybersecurity Author. Read the original post at: https://guptadeepak.com/oidc-vs-saml-a-comprehensive-technical-comparison/
