Found in Environments Protected By: Microsoft
By Andrew Mann, Cofense Phishing Defense Center
Everyone today has some form of social media, whether it is Instagram, X, YouTube or Facebook. It is an amazing way to communicate and stay connected with family and friends, but at the same time, it can be scary when your social media falls victim to a cyber-attack.
These types of campaigns illustrate how secure email gateways (SEGs), or any type of automated system, may fail to catch things that only the trained eye can. Threat analysts here at the Cofense Phishing Defense Center (PDC) are properly trained and equipped to catch these phishing campaigns that have shown up in environments utilizing SEGs.
Here at the PDC, we have seen numerous social media phishing websites, ranging from X, Instagram, Telegram, Snapchat and Facebook. These attacks can aim to collect your username and password by sending an email saying that “your password needs to be updated” or “your account is going to be deleted. Click here to avoid termination!”
These phish can already be very probable and tempting to the untrained eye, and even with that, the threat actor did a commendable job at tailoring this phish to look like a legit Facebook/Meta account termination email. They were able to do this partially because they used Meta’s Business Manager service which helped make the email seem more real. Receiving emails like these can be scary when you don’t know if your account is under fire. It is always best practice to keep a calm mind and not rush to click anything in the email if you are unsure.
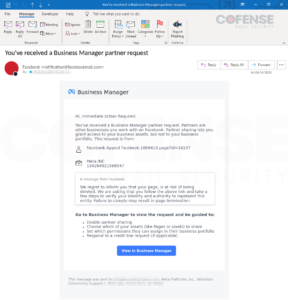
Figure 1: Email Body
In the above image you can see format of the body is well done, the grammar is correct and professional, and they included a unique case number for this specific account requisition. They also included some informative assistance to help guide the user to the request made.
One indicator of suspicious activity, is they started out the email as “Hi, Immediate Action Required.” The threat actor used a simple scare/urgency tactic to make the user think if they do not follow these steps right away, their account will be deleted. A very popular tactic to use amongst these types of social media phishing emails.
Customarily, the big blue button would take us to the phishing website if clicked on. However, in this case, it does not, which is one the reasons this a unique phishing email. Instead, they provided the phishing URL above in the portion of the email listing who made the Business Manager request.
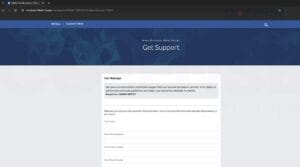
Figure 2: Phishing Page
After going to the above link, the threat actor put in their tailored email, it redirects to the phishing site. It is a very standard Facebook/Meta phishing webpage, and they even put a note at the top saying “your account has been in violation of our terms of service and community guidelines.”
A final threatening reminder to convince the user to provide their username and password. A naïve perspective could miss the obvious implications that this website is fake. Some common pointers are that if it was Facebook, the URL address would be a real Meta/Facebook domain such as facebook[.]com and not facebook[.]1006615[.]page. The threat actor tried to make a good attempt by at least including the name Facebook in the subdomain.
Always be wary of the threats cyber-criminals can pose. They are after anything and everything that can be held against a user. Ranging from credit-card information, Social Security numbers, or your login credentials, they’ll use what they can to not just access your social media account but to any online account you may have.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
The post A “Meta” Facebook Phish appeared first on Cofense.
*** This is a Security Bloggers Network syndicated blog from Cofense authored by Hillary Long. Read the original post at: https://cofense.com/blog/a-meta-facebook-phish/
如有侵权请联系:admin#unsafe.sh