2024-7-9 20:38:2 Author: securityboulevard.com(查看原文) 阅读量:15 收藏
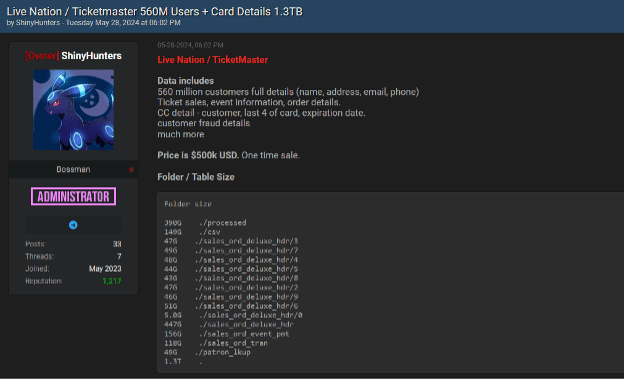
As commented in our previous blog, The Resurgence of Major Data Breaches?, in May 2024, a potential data breach involving Ticketmaster surfaced on deep and dark web forums, and we want to analyze it as a sample data breach. The original breach, as shown in the accompanying image below, was posted by the user named ShinyHunters on May 28, 2024. This breach includes data of 560 million customers and 1.3TB of detailed information, including full names, addresses, emails, phone numbers, ticket sales, event information, order details, credit card details, customer fraud details, and more. The data was offered for sale at a price of $500,000 USD.
Understanding the Breach
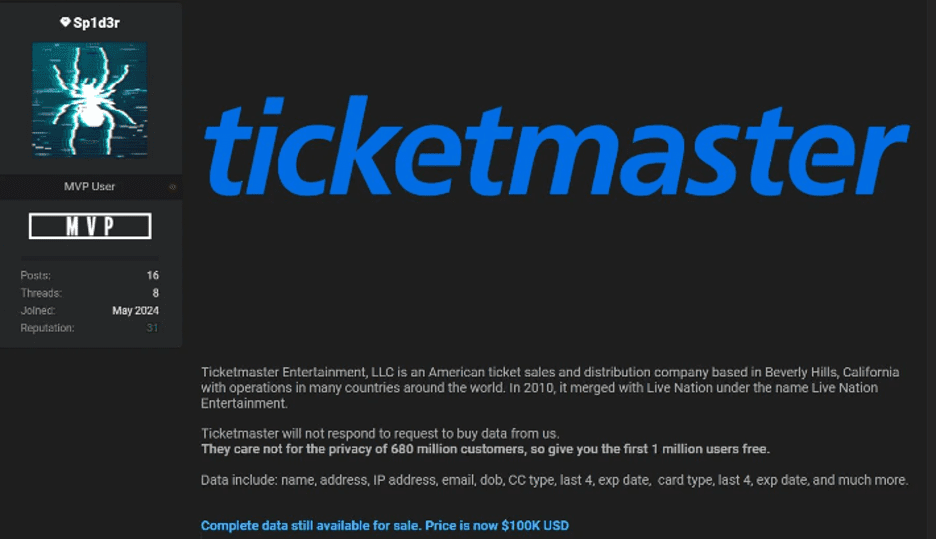
Recently, another user named Sp1d3r seems to have taken more prominence on the forum, possibly due to the ShinyHunters user having fallen back to a somewhat more secondary role. Sp1d3r advertised the data on the forum, indicating that the potential data breach affected 680 million customers, with data available for $100,000 USD. In addition to selling the entire 680M data set, it has offered a sample of the first million records to all users.
Constella Intelligence obtained the 1 million records sample offered in the forum and analyzed it, providing a glimpse into the scale and severity of the incident. The sample dataset includes:
- Personal Information: Names, email addresses, phone numbers, physical addresses.
- Financial Data: Credit card details, payment methods, and transaction information.
- Web Sessions and Cookies: Session details, IP addresses, browser identifiers.
- Transaction Details: Purchase history, patron IDs, party lookup IDs.
Key Statistics from the Sample
Analyzing the sample dataset provides several important statistics that illustrate the scope and impact of the potential breach. These statistics offer a quantitative perspective on the breach, helping to understand the extent of the data exposure and identify trends that could inform future protective measures.
- Total Records: 999,998 entries
- Total Fields: 53 fields encompassing various data types
- Email Statistics: 999,985 total email addresses, 761,041 unique email addresses
- Top Email Domains: Gmail.com (620,985), Yahoo.com (57,796), Hotmail.com (45,490)
- Geographical Distribution: USA (800,414 records), Mexico (99,910), Canada (64,011)
- Payment Methods: VISA (429,279 records), MasterCard (304,484), American Express (64,369), PayPal (59,747)
AI-Driven Scams: What You Need to Know

The exposure of such detailed and sensitive information in the potential data breach poses several significant risks to the affected individuals. At Constella, in our experience, we are seeing many spear phishing attacks that use credit card data or payment methods as inputs for AI models trained to generate realistic, targeted phishing attacks.
Spear phishing is a targeted attack aimed at stealing sensitive information from a specific individual by posing as a trusted entity. Unlike mass phishing, it is highly personalized and tailored using detailed information from breaches.
With access to names, email addresses, financial information, payment methods, web session cookies and transaction histories, threat actors can create highly convincing emails that appear legitimate using actual AI tools (using LLM models like WormGPT, HackerGPT or DarkBERT, or even prompt jailbreaking into corporate LLM modes).
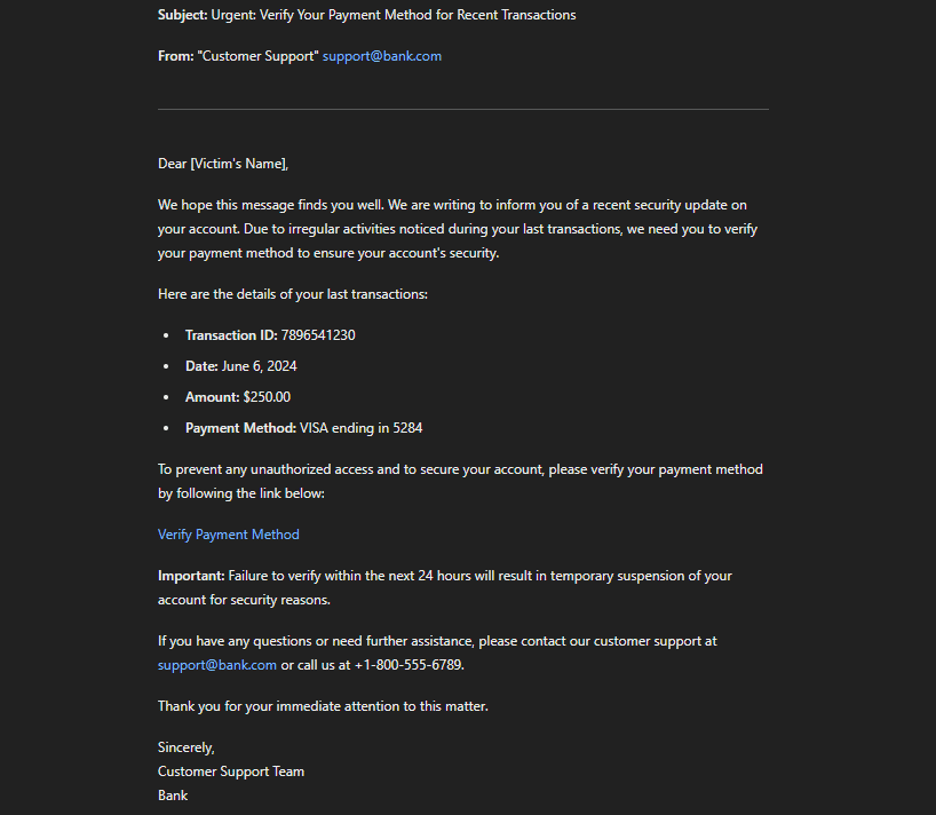
As the previous example, an email might reference recent user purchases or use personal financial information to make the message more believable. The use of AI can enhance the realism and effectiveness of these scams, making it harder for individuals to distinguish fraudulent emails from legitimate ones.
Protecting Exposed Data
If the information published by “Sp1d3r” is accurate, Constella recommends taking the following actions:
- Clear cookies and close any active sessions: Regularly clearing your browser cookies and cache and closing any active sessions can help protect your web session data.
- Reset the password associated with your account and any other accounts using the same password: Although Ticketmaster claims that no passwords were compromised and the banking data is encrypted, it is wise to reset the password for your Ticketmaster account and any other accounts using the same password. Use strong, unique passwords for each account, and consider using a password manager to generate and store these securely.
- Stay alert for possible spear-phishing campaigns, as mentioned earlier: Be vigilant with emails, especially those that seem related to Ticketmaster or recent transactions. Avoid clicking on links or downloading attachments from unknown senders, and verify the authenticity of any requests for personal information.
By following these specific recommendations, individuals can better protect their personal information and mitigate the impact of data breaches like the one potentially experienced by Ticketmaster.
*** This is a Security Bloggers Network syndicated blog from Constella Intelligence authored by Alberto Casares. Read the original post at: https://constella.ai/analyzing-ticketmaster-sample-data-breach-key-insights-and-implications/
如有侵权请联系:admin#unsafe.sh