2024-7-9 15:31:24 Author: cyble.com(查看原文) 阅读量:11 收藏
Key Takeaways
- Cyble Research & Intelligence Labs has observed a recent surge in phishing campaigns targeting banking users in India.
- Cybercriminals have shifted their focus from SMS to WhatsApp for distributing phishing messages, expanding themes from credit card rewards and KYC updates to utility bills and government schemes.
- The admin panel hosted on the Command and Control server mentioned the APK support via WhatsApp, suggesting the use of Malware-as-a-Service(MaaS).
- Recent malware strains lack launcher activities, making them stealthier as the app icon does not appear on the app drawer.
- In this analysis, we’re investigating a new campaign impersonating the Regional Transport Office (RTO). This campaign uses fake APKs to lure victims into installing malware and focuses on collecting and sending SMS messages and contact information.
- The malware collects device and contact data, sending it to a Telegram bot and using Firebase to get phone numbers and text messages, facilitating unauthorized SMS verification.
Overview
Since 2021, India has faced an ongoing cyber threat involving Android malware specifically targeting bank customers. Threat actors initially distributed this malware through SMS messages containing phishing links, which directed users to download malicious Android applications. Themes such as credit card reward points and KYC updates were used initially to entice victims.
In 2021, Cyble Research and Intelligence Labs (CRIL) highlighted this campaign, which specifically targeted users of major Indian banks using an Android infostealer. Recently, we have observed a rise in this phishing campaign. Threat actors have expanded their tactics beyond the reward points, and KYC update themes to include themes related to utility bill payments and government schemes. Notably, there has been a shift from sending phishing messages via SMS to using WhatsApp messages in this campaign.

Figure 1 – Phishing messages impersonating Indian banks distributed via WhatsApp

Figure 2 – Fake government scheme APKs being distributed via WhatsApp

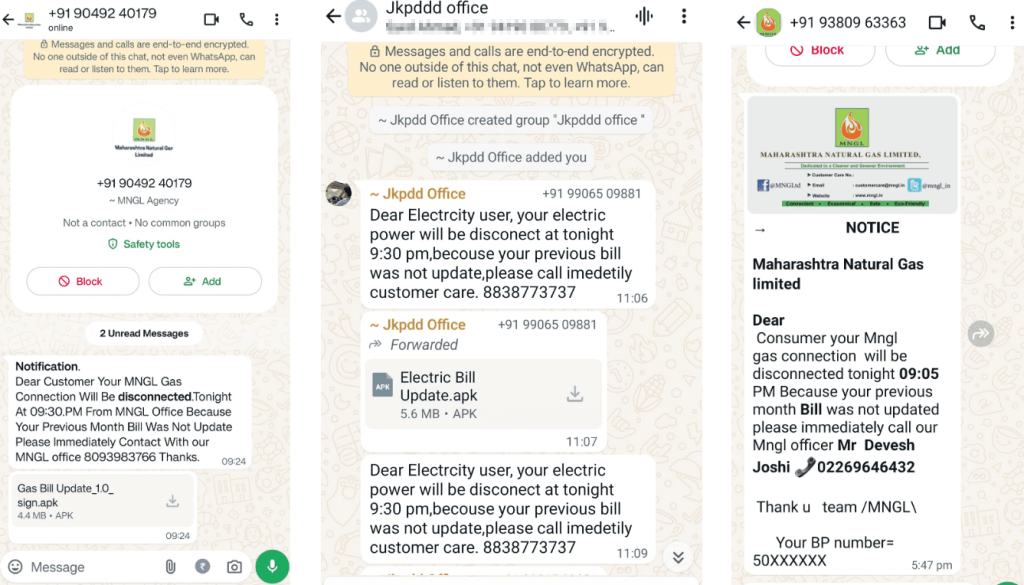
Figure 3 – Gas and electricity bill phishing messages
During our analysis of the applications associated with this campaign, we discovered a Command and Control (C&C) server, “hxxps://sallu[.]info”, which hosts an admin panel. On this admin panel, we found a WhatsApp number, “9238022687”, listed for support related to links, APKs, and UPI panel assistance. We suspect that the threat actor may be utilizing a Malware-as-a-Service (MaaS) model offered by certain cybercriminals.

Figure 4 – Admin panel displaying WhatsApp number for support
We discovered other similar admin panels associated with this campaign displaying the same message. In March 2024, McAfee also noted that this campaign was using Malware-as-a-Service(MaaS) provided by ELVIA INFOTECH.

Figure 5 – More C&C server hosting admin panel
Absence of Launcher Activity in Recent Malware Strains
Threat actors have been observed deploying new malware strains that do not utilize launcher activities. Examination of the manifest file reveals the absence of a launcher activity, which prevents the app icon from appearing on the app drawer. This makes it difficult for the victim to identify and uninstall the malware.

Figure 6 – Launcher activity missing
After the user installs the application, they are given the option to open it. Upon opening, the malware prompts the user to grant permission to send and receive SMS messages. Once the victim grants these permissions, the malware displays a phishing screen displaying a fake login page of major Indian Banks.

Figure 7 – Malware prompting permissions and loading fake login screen
A New Phishing Campaign Impersonating Regional Transport Office
Since the beginning of 2024, Indian citizens have been receiving phishing messages on WhatsApp that impersonate the Regional Transport Office (RTO), a governmental organization in India responsible for vehicle registration, driver licensing, and other transport-related matters.

Figure 8 – Phishing messages impersonating the RTO
The phishing messages, sent via WhatsApp, masqueraded as official notices from regional RTOs, alleging violations of traffic rules against the users’ vehicles. They included an APK file named “VAHAN PARIVAHAN.apk,” purportedly for viewing the “challan”, which is a regional term that refers to an official document or receipt. These messages featured regional RTO logos in their profile pictures, enticing victims to download the malicious application.
The malware from this campaign also lacks a launcher activity. Unlike previous malware, it does not use a phishing screen mimicking any Indian banks. Instead, this application runs in the background to send SMS messages from the infected device and collect SMS messages and contact lists.
Technical Details
Once the user installs and opens the application, the malware prompts the victim to grant permissions for SMS and contact access.

Figure 9 – Permissions prompted by the VAHAN PARIVAHAN app
In the main activity, the malware loads a blank screen into the WebView and prompts the user to designate the “VAHAN PARIVAHAN” application as the default SMS application. Concurrently, the malware sends device information, including the model number, version number, battery status, carrier name, and other relevant details, along with the contact list from the infected device, to a Telegram bot URL: hxxps://api[.]telegram.org/bot7487929666: AAHotf1RHqgk6W0WbFjXywI458I9r9CmxiM/sendDocument.

Figure 10 – Collecting device information

Figure 11 – Collecting contacts and sending stolen information to the Telegram Bot
After gathering data and obtaining necessary permissions, the malware initiates a background service that connects to the Firebase URL “hxxps://numnumfour-default-rtdb.firebaseio[.]com/-1002221216537/.json”.
The service retrieves data from the Firebase URL, including lists of phone numbers and text messages. Subsequently, the malware uses the received text to send SMS messages from the infected device to the phone numbers obtained from the Firebase server.

Figure 12 – Sending messages from the infected device
When we accessed the Firebase URL, we observed the JSON response, which included Indian phone numbers and random text, as depicted in the figure below.

Figure 13 – Firebase URL JSON response
However, a similar URL, “hxxps://hookuptolookup-default-rtdb[.]firebaseio.com/-1002118750305/.json” was identified. This URL also manages data containing phone numbers and text. Other applications within the same campaign utilize this URL. The figure below illustrates the data present in the JSON file fetched from Firebase.

Figure 14 – Text and number data present in .json
As indicated in Figure 13 under ID 11357, the text message begins with “SIMPL,” suggesting it is related to the verification process of the Simpl app. Simpl is a Buy Now, Pay Later (BNPL) app in India that allows the user to make online purchases. When a user attempts to register for the Simpl application using their mobile number, the app sends an SMS containing a verification code that starts with “SIMPL.”

Figure 15 – Simpl app’s number verification message
In December 2022, CRIL identified several techniques used by threat actors to commit financial fraud using UPI. One such technique involved sending verification messages from the victim’s device, enabling the threat actors to successfully verify the UPI app on their own device. We suspect that the threat actors in this campaign are attempting to employ the same tactic.
Conclusion
Since 2021, India has faced persistent cyber threats targeting bank customers through advanced Android malware campaigns. Initially spread via SMS with themes like credit card rewards and KYC updates, these attacks now include utility bill payments and government schemes distributed through WhatsApp. Using Malware-as-a-Service (MaaS) and hiding launcher activities have made detection difficult.
This new phishing campaign impersonates the Regional Transport Office (RTO), using a malicious APK to send SMSs from victims’ devices. This enables threat actors to verify payment applications via SMS. This ongoing threat underscores the need for increased vigilance, user awareness, and robust cybersecurity measures to defend against these sophisticated attacks.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Download and install software only from official app stores like Google Play Store or the iOS App Store.
- Use a reputed anti-virus and internet security software package on your connected devices, such as PCs, laptops, and mobile devices.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Enable biometric security features such as fingerprint or facial recognition for unlocking the mobile device where possible.
- Be wary of opening any links received via SMS or emails delivered to your phone.
- Ensure that Google Play Protect is enabled on Android devices.
- Be careful while enabling any permissions.
- Keep your devices, operating systems, and applications updated.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Defense Evasion (TA0030) | Masquerading: Match Legitimate Name or Location (T1655.001) | Malware pretending to be Indian banking applications or government entity |
| Persistence (TA0028) | Event-Triggered Execution: Broadcast Receivers (T1624.001) | Malware has implemented an SMS broadcast receiver to fetch incoming SMS |
| Discovery (TA0032) | System Information Discovery (T1426) | The malware collects basic device information. |
| Defense evasion (TA0030) | Hide Artifacts: Suppress Application Icon (T1628.001) | Malware does not have launcher activity enabling it to hide icon |
| Collection (TA0035) | Protected User Data: Contact List (T1636.003) | The malware collects contacts from the infected device |
| Collection (TA0035) | Protected User Data: SMS Messages (T1636.004) |
Steals SMSs from the infected device |
| Command and Control (TA0037) | Application Layer Protocol (T1437) | Application using Firebase URL |
| Exfiltration (TA0036) | Exfiltration Over C2 Channel (T1646) | Sending exfiltrated data over C&C server |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 31e92f014c1e64fad475fb3eade116c19464a6978159de55c59e3189a67eb979 e0190113fc10e743b1f0862d498ab5c41d5bd242 961ede4f131f3a7322863ef99cc446b5 |
SHA256 SHA1 MD5 |
VAHAN PARIVAHAN malicious application |
| hxxps://numnumfour-default-rtdb[.]firebaseio.com/ | URL | Firebase URL to get mobile number and text message |
| hxxps://api[.]telegram.org/bot7487929666:AAHotf1RHqgk6W0WbFjXywI458I9r9CmxiM | URL | Telegram bot URL used to send data |
| 3d2e8bd0b83a48c89e44c6e9dea76f803460484517d193bfc114f20170e4baba 634ff3c0a3346935b1ec4d0fe32fedd7fa0c4b5e 41450833c1eb6512843b2beb27e121c1 |
SHA256 SHA1 MD5 |
Reward campaign file with no launcher activity |
| api[.]warnert.online sallu[.]info |
Domain | C&C server |
如有侵权请联系:admin#unsafe.sh