2024-7-4 00:14:44 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
The cybersecurity industry is experiencing significant shifts in 2024. LogRhythm’s State of the Security Team global research reveals a whopping 95% of organizations have adjusted their security strategy this year. These changes are primarily driven by artificial intelligence (AI), regulatory shifts, customer expectations regarding data protection and privacy, and evolving cyberthreats.
As organizations progress through 2024 and beyond, alignment with executive leadership, alongside the development of adaptive and forward-thinking security strategies, is essential for fostering a resilient digital environment — one that supports ongoing business success and protects against cyberthreats.
In this blog, LogRhythm’s CISO Andrew Hollister and Deputy CISO Kevin Kirkwood, dive into both insights from the research report and cybersecurity trends in 2024.
The Evolving Security Landscape & Its Impact on Security Strategies
The 2024 cybersecurity environment is dynamic. Between changing regulations, new attack types, budget changes, and recent breaches, most companies have had to shift their security strategy in the last year. The most substantial driver of these changes is the use of artificial intelligence in cybersecurity. Below are examples of several cybersecurity trends in 2024 and how this impacts CISOs and security strategies.
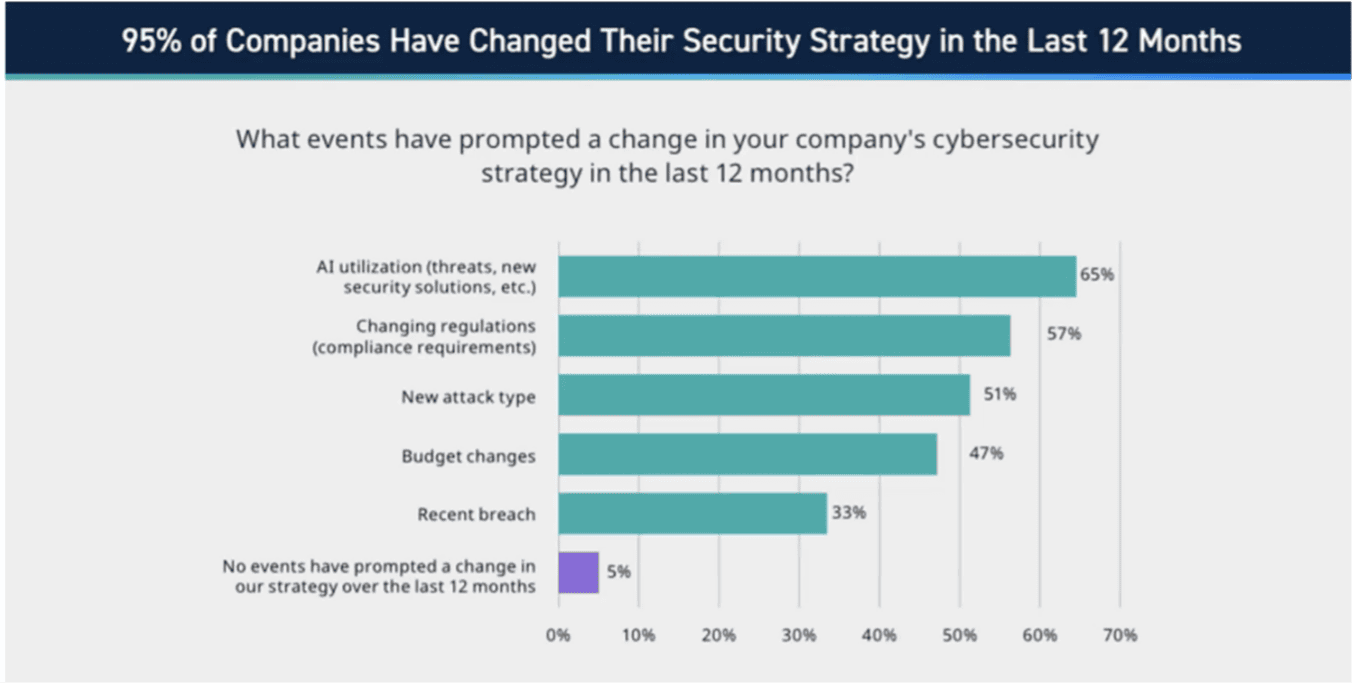
Figure 1: Statistics on evolving security strategies, State of the Security Team Research.
Artificial Intelligence in Cybersecurity
The use of artificial intelligence in cybersecurity is prompting changes in 65% of organizations’ security strategies. Within the industry, AI is commonly being used in three ways:
1. To Attack – “Security from AI”
Companies are noting an uptick in sophisticated cyberthreats arising from the malicious use of AI, including increased quality of phishing emails and social engineering. For example, threat actors can use AI to build high-quality webpages or impersonate employees remarkably well.
2. To Defend – “Security by AI”
Security operations center (SOC) teams often find themselves reacting to evolving threat tactics, but surprisingly, when it comes to AI, defenders have outpaced attackers. This is attributed to how swiftly AI tools have been adopted around the globe, prompting organizations to quickly leap into policy enforcement to avoid PII or IP leaks and to educate employees on how to use AI technology safely. From threat detection to predictive analytics, AI is enhancing the way the industry responds to cyberthreats.
3. To Develop – “Security of AI”
In an increasingly AI-driven world, prioritizing ethical standards and the security of AI is essential for companies. This approach helps them to remain proactive, resilient, and trustworthy while responding to current threats and anticipating future challenges.
If CISOs can incorporate AI into their security strategy effectively, there is much potential to enhance and scale defenses against cyberattacks; however, CISOs need to proceed with caution. At the foundation of all AI tools is the output of data and the quality and integrity of your data will reflect the success of your AI program. For tips to ensure your data is ready for an AI-driven SOC, read this blog.
Changing Regulations
Navigating the landscape of data privacy and regulations while operating business efficiently requires a delicate balancing act. Each day, multiple compliance changes occur worldwide, leaving both governments and their industry bodies grappling with establishing a baseline of compliance standards. Large organizations, or those in dynamic industries like healthcare or financial services, are finding it particularly difficult to adapt to this new pace of change.
The introduction of the General Data Protection Regulation (GDPR) in the EU, followed by the California Consumer Privacy Act (CCPA) in the US, reflects a larger trend towards stricter data protection laws globally. The private sector has also played a part in shaping these data protection frameworks. Many businesses have advocated for regulations that strike a balance between protecting individual privacy while still allowing for innovation and operational efficiency.
Breach Responsibility: Who is Accountable?
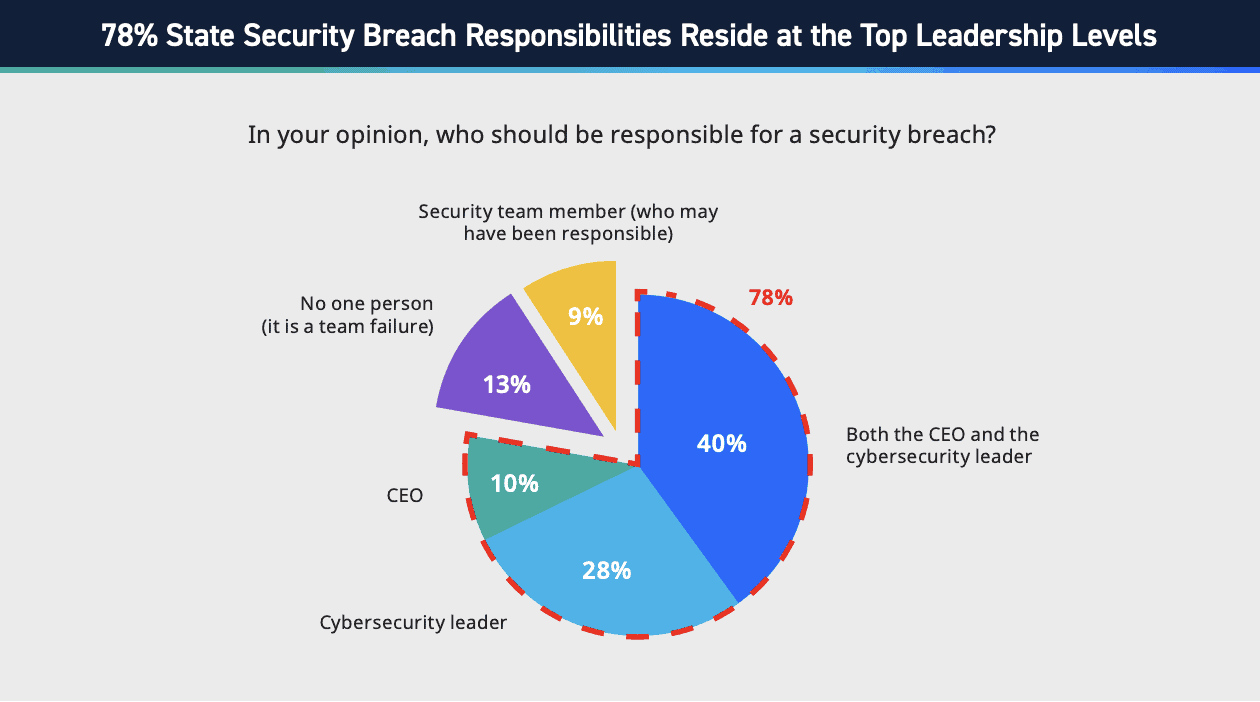
Figure 2: Statistics on breach responsibilities, LogRhythm’s State of the Security Team Research.
In our research, an overwhelming majority (78%) believe the responsibility for breaches lies at top leadership levels. In the past, breach responsibility was often blamed on IT departments, or on inexperienced members of staff, such as interns. As cybersecurity has more widely become recognized as a critical business risk, accountability has shifted to the appropriate leadership.
Over the next few years, we anticipate an increase in the percentage of people who find the CEO and the cybersecurity leader jointly responsible for breaches. Cybersecurity is a collective team effort — a successful cybersecurity program requires sponsorship from the CEO downwards, across the entire organization.
How Often Should Security Teams Meet?
A robust cybersecurity program can only be built from a secure foundation, one that includes security awareness, effective patching, and proper prioritization. Security should ideally be a standing item on the weekly or bi-weekly agenda of senior leadership.
Check out episode 1 of our State of Security Team webinar series for more on this topic.
How Modern Security Teams Are Finding Success in 2024
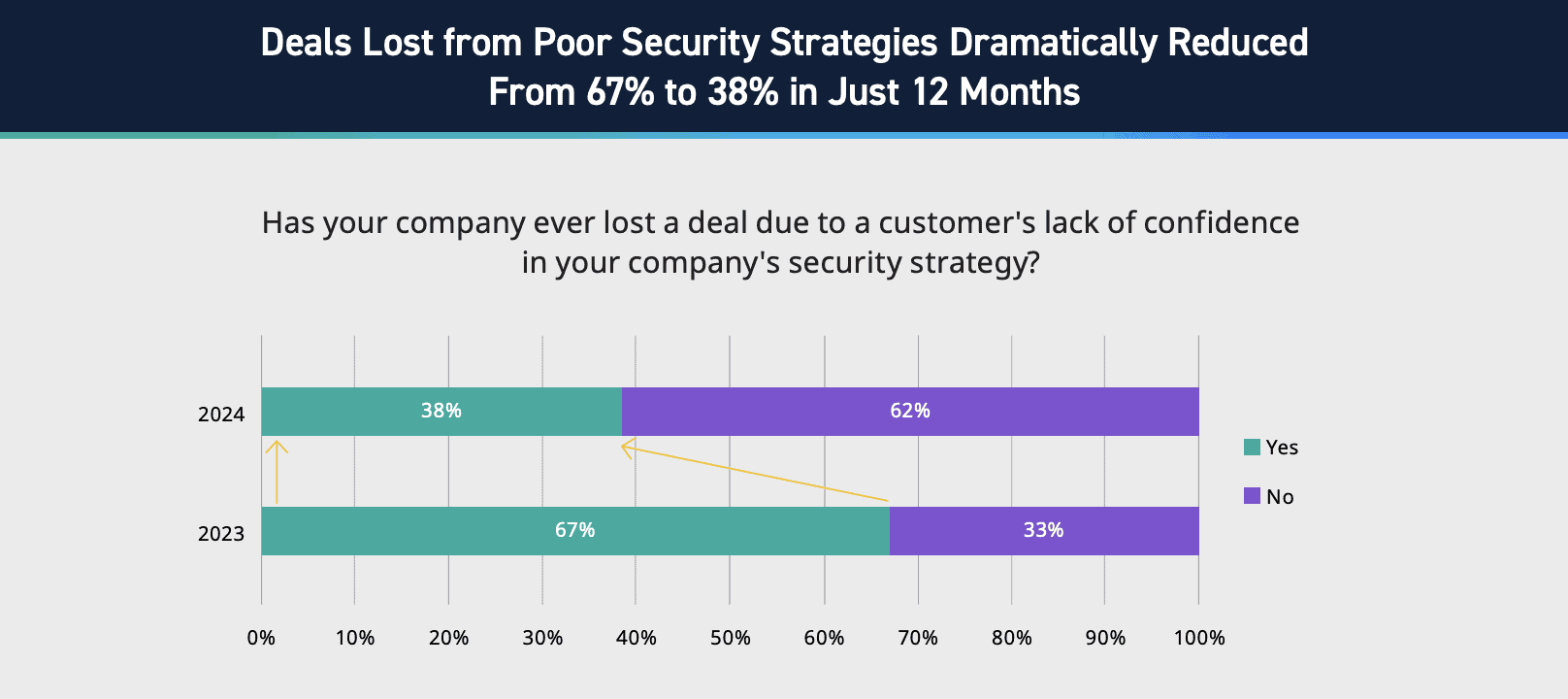
In 2023, 67% of organizations reported having lost a deal due to a customer’s lack of confidence in their security strategy. In 2024, however, only 38% of organizations have experienced the same issue. This improvement is proof of organizations’ increased commitment to integrating security directly into business processes and development activities. For instance, we’ve seen a rise in adoption of DevSecOps practices and incorporating security into CI/CD pipelines; this trajectory is expected to continue into the coming years.
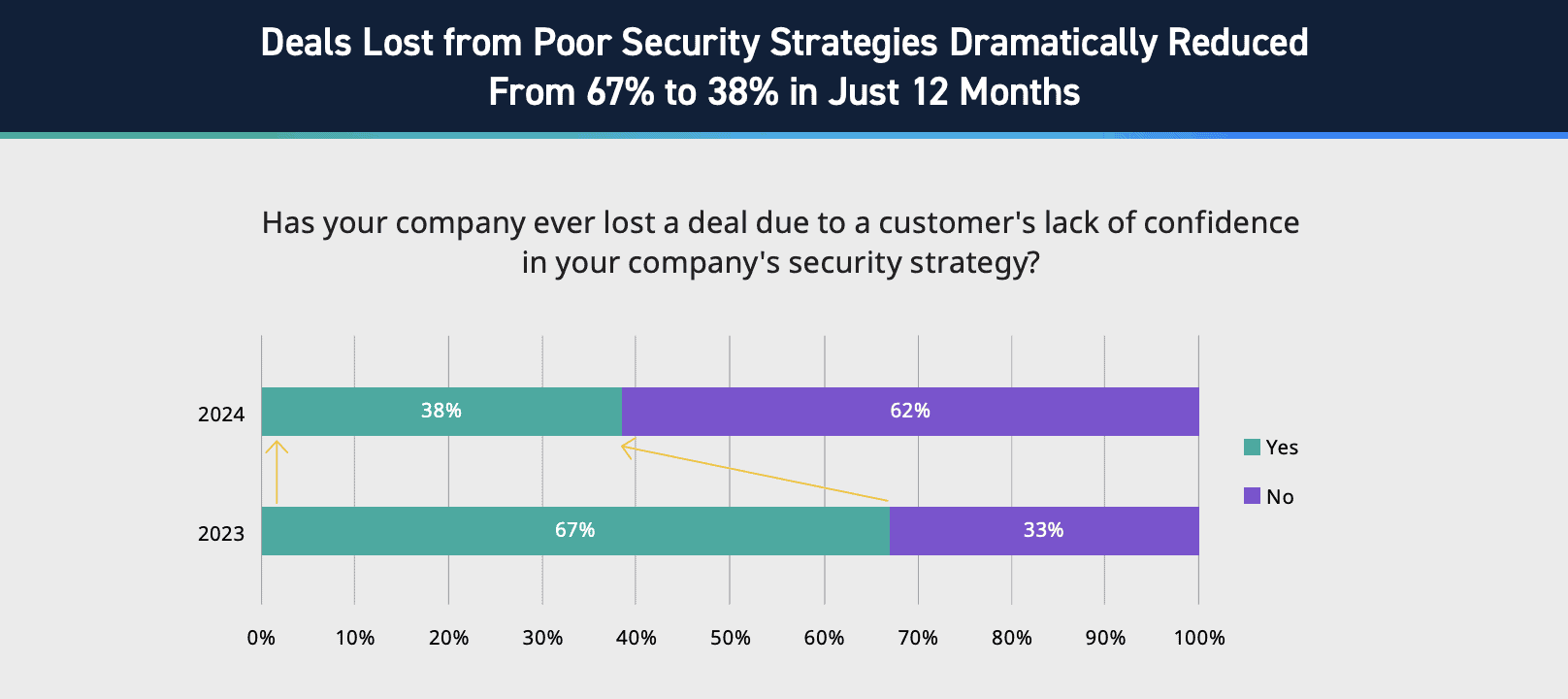
Figure 3: Statistics on deals lost from poor security strategies, LogRhythm’s State of the Security Team Research.
Aligning Cybersecurity Strategies with Business Objectives
When it comes to aligning cybersecurity strategies with business objectives, here are three best practices to keep in mind:
- Ensure you understand your business – CISOs and security leaders must understand what their business aims to achieve, customer priorities, and the industry they’re operating in. They should have a voice in larger business discussions to help integrate security considerations into strategic planning. Networking with other leaders within the company is also vital; by building relationships across departments, security leaders can identify critical assets needing protection and understand what drives value for stakeholders.
- Keep the business perspective at the center of everything – Ensure your cybersecurity strategy or program aligns with how you do business — daily workflows, processes, culture, and other core business operations. Keeping the business perspective at the forefront of your strategy will ensure both protection of the company, and growth and innovation.
- Employee training and education – Invest time in educating employees on potential risks and best-practices that make sense for the threat landscape you’re dealing with. Regular training sessions will foster a security-aware culture and contribute positively to the overall security posture of your company.
Using the Right Resources to Defend Against Cyberattacks
In Figure 3, we shared how deals lost from a customer’s lack of confidence in a company’s security strategy dramatically decreased year-over-year. In alignment with that finding, we also found that 78% of organizations feel confident that they have the right resources to secure their company from cyberattacks (Figure 4). This statistic illuminates a newfound confidence within and of cybersecurity teams. Resources are more effectively being allocated, and these decisions are paying off in the form of increased customer confidence.
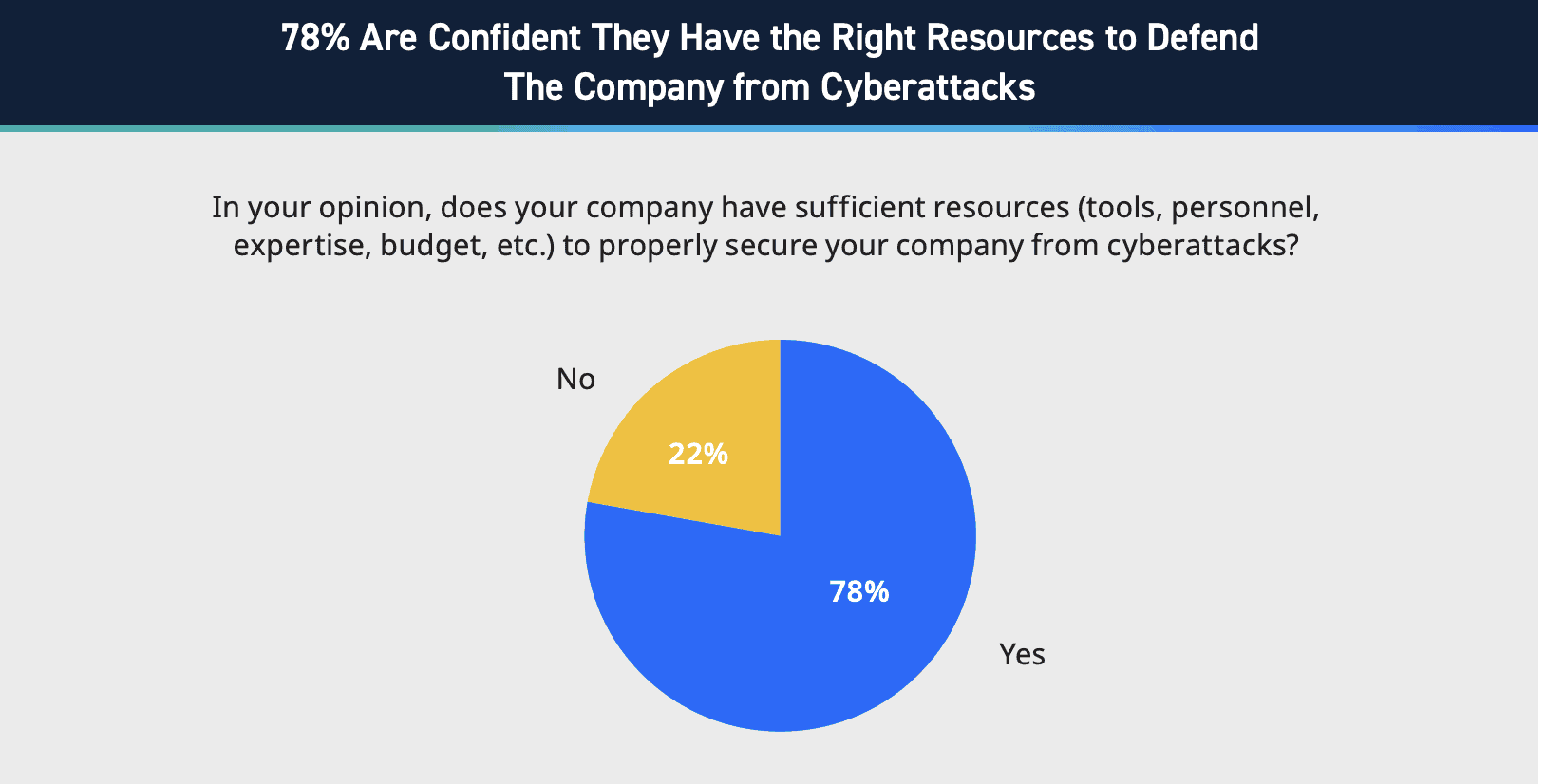
Figure 4: Statistics on confidence in sufficient resources, LogRhythm’s State of the Security Team Research.
Gone are the days of the “no vendor left behind” policy, a blanket approach of using a wide array of security tools without strategic consideration. Today, organizations prioritize having and using security tools that specifically fit their environment and needs, and training personnel to gain business and security expertise with those tools.
There’s also now a widespread recognition that every organization with a public internet presence, whether it’s a multinational corporation or an SME, will encounter some level of cyber risk. Given this reality, cybersecurity is understood as an essential part of overall business spending.
Measuring and Maturing the Sufficiency of Security Programs
How can you truly measure the effectiveness of your security program and your resources? Metrics is always a fraught subject in the cybersecurity space, but it ultimately comes down to gathering “actionable intelligence” to protect your organization.
MITRE’s 11 Strategies of a World-Class Cybersecurity Operations Center speaks to the importance of measurement and the difference between internal and external SOC metrics:
Internal metrics are all about reporting back to the SOC how it’s doing. The specific metrics here include data feeds health, time consumed doing routine activities, and detection accuracy.
External metrics refer to the metrics you report to stakeholders, including dwell time, response time, and overall SOC readiness.
The final piece on metrics that’s important to note is that only providing raw statistics to your stakeholders won’t foster a mutual understanding of the technical data. You must also craft a narrative around the numbers to provide context and insight into gaps and successes, and align your team around developing a plan to drill down into those gaps.
Check out episode 2 of our State of Security Team webinar series for more on this topic.
Bridging the Communication Gap in Cybersecurity
We’ve never had as much access to communication as we do today, whether it’s through email, messaging services, dashboards, and other platforms. Despite these extensive communication channels and opportunities, the question remains: does all this communication result in a shared understanding of the subject?
“The single biggest problem in communication is the illusion that it has taken place.”
– George Bernard Shaw
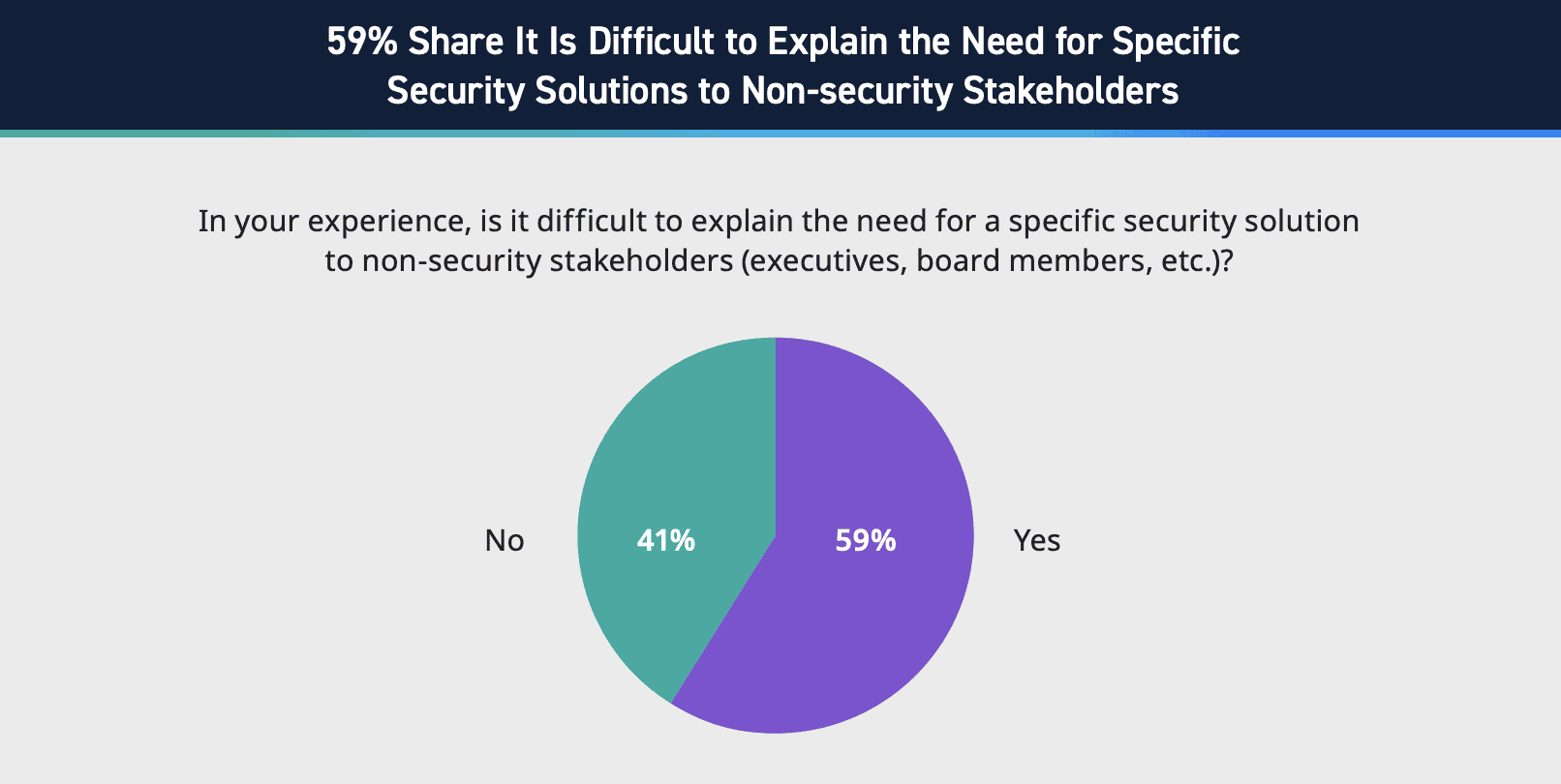
Figure 5: Statistics on communicating to non-security stakeholders, LogRhythm’s State of the Security Team Research.
59% of organizations still have difficulty communicating the need for specific security solutions to non-security stakeholders. We predict that if we flipped this question around and asked non-security executives if they ever have difficulty understanding their CISO or security leaders, an even larger percentage would respond “yes.”
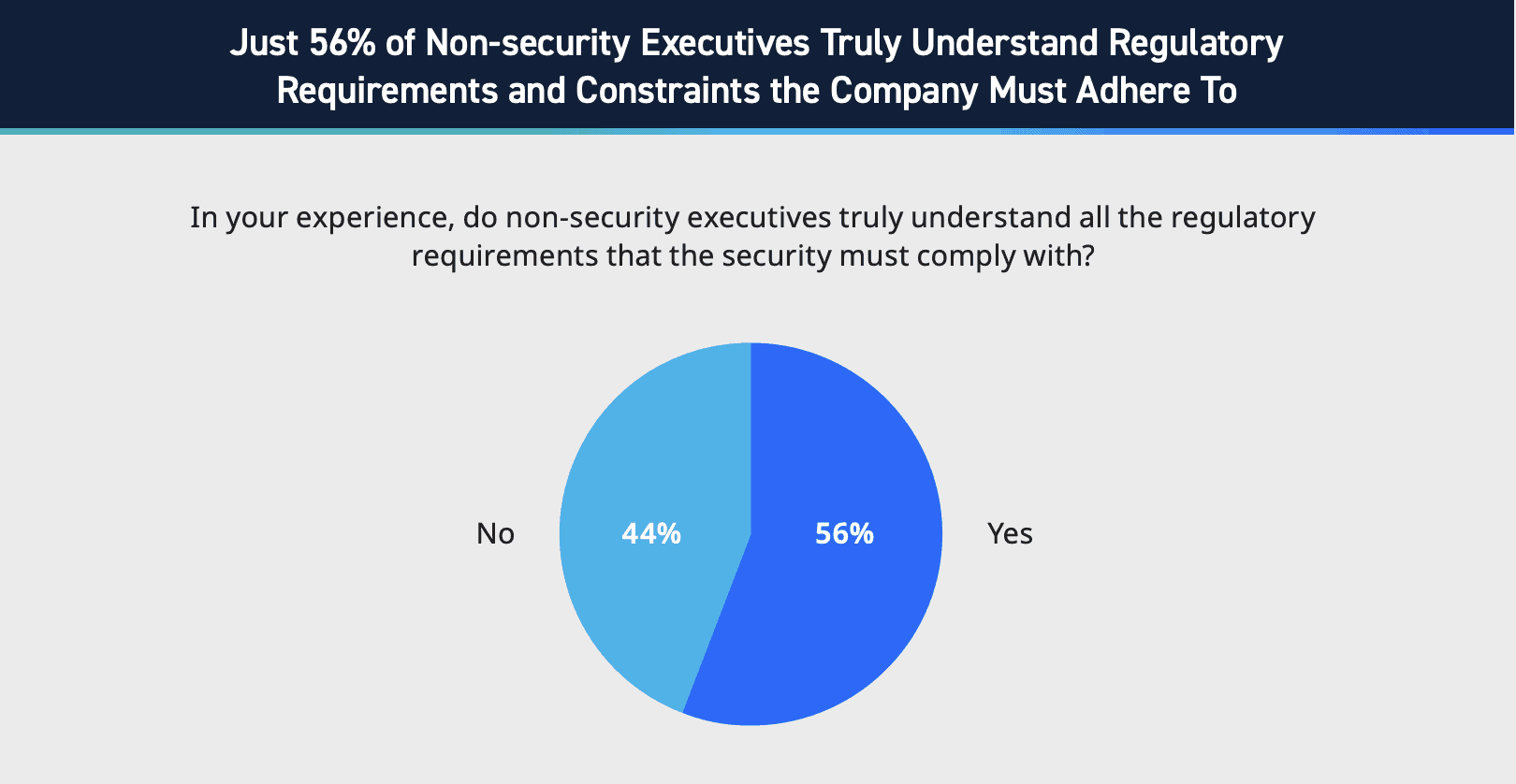
Figure 6: Statistics on non-security executives understanding regulatory requirements, LogRhythm’s State of the Security Team Research.
Setting Yourself Up for Communication Success
To non-security stakeholders, technical jargon may as well be a foreign language — nothing you say will resonate if it’s not being understood. It’s imperative that your messaging aligns with your audience and the things that matter to them. Here are four best practices for effectively communicating with non-security stakeholders:
- Storytelling and finding a common language – Get creative and strategic with your use of analogies. In episode 3 of our State of the Security Team webinar series, Kevin Kirkwood gives an example of an analogy he used to help a group understand his explanation of honey files:
- Educate your executive leadership team and board on key concepts in cybersecurity – Just as you’d expect a board member to understand a basic financial report, they should be able to communicate about cybersecurity risk, at least in a high level. As a security company, many of LogRhythm’s executives already have a relationship with technology and our industry. But when our CEO, Chris O’Malley, joined, the team still held a few sessions where we could all discuss the SIEM space and our objectives at length. These sessions helped set a clear foundation for Chris and were useful for subsequent conversations.
- Develop a narrative around your reporting – We touched briefly on this earlier, but statistics are just numbers without a narrative and additional context on how they align to business objectives. As a security leader, it’s sometimes difficult to remember to share the wider context that’s in your head because you’re in the weeds of it all daily, but the additional context makes all the difference to your stakeholders.
- Have a feedback loop – There’s no single perfect way to communicate with stakeholders, as each person varies in their understanding of technology, and what’s important to the business or risk tolerance can fluctuate. It may take time or a few iterations to get to know your stakeholders and what’s most interesting to them. Listen to their feedback to understand what they pick up on and what’s not quite hitting the mark.
In the State of Security Team research report, we dive into additional best practices for effective communication including using real-time dashboards for giving a quick overview, more on simplifying technical language, and tips on collaborating widely across the organization to give context for interdepartmental conversations.
Check out episode 3 of our State of Security Team webinar series for more insight on bridging the communication gap in cybersecurity.
How Security Teams Can Confront Compliance and Resource Constraints
In our research, just 2% of respondents reported not doing anything to manage risk due to a lack of resources; all other respondents are finding ways to manage risk despite resource constraints.
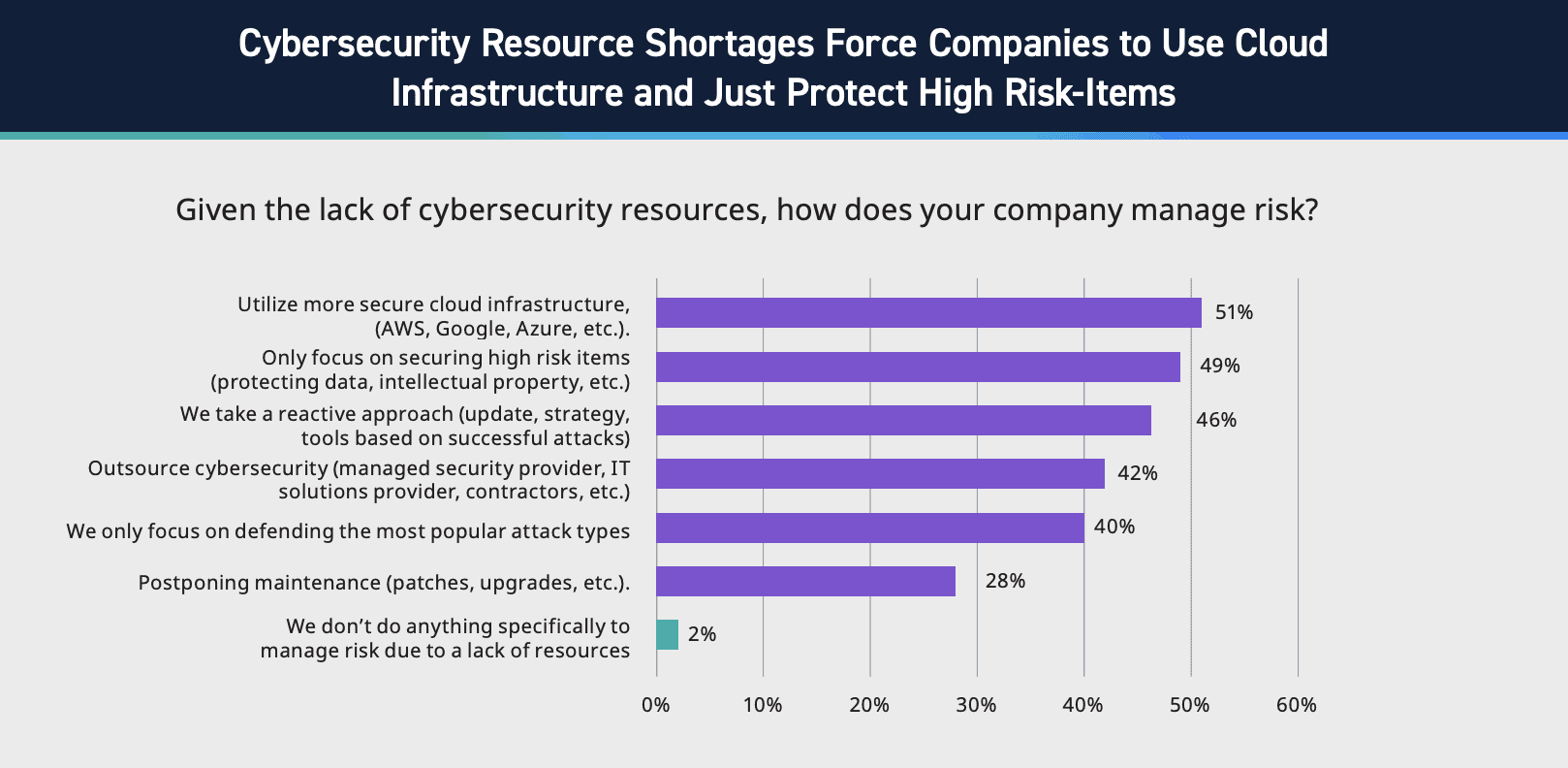
Figure 7: Statistics on managing risk with a lack of resources, LogRhythm’s State of the Security Team Research.
With thousands of vendors vying for the attention of security teams, it’s natural to want to myopically pursue more budget for the newest technology. But the reality is that many organizations are only using between 10-50% of the capabilities of the tools they already own. Cybersecurity is a journey, not a destination. Although the phrase may be cliché, it’s true; investing in the work needed to mature your security strategy over time, even with limited resources, will pay off long-term.
Cloud Infrastructure and Focusing on Critical Risk Items
51% of organizations are leveraging cloud infrastructure to manage risk. The cloud enables analysts and security engineers to focus solely on securing the business, eliminating the need for physical maintenance and upgrading. However, you’re ultimately still responsible for securing your use of the platform and implementing the appropriate controls. The cloud is only secure when you truly understand and adhere to the shared responsibility model and understand the vendor you engage with.
In Figure 7, we see that 49% of organizations focus solely on securing critical risk items. As cybersecurity is a continuous journey, prioritizing the highest risks first, then continuing down to lower risk areas makes business sense. However, on the flip side, focusing exclusively on high-risk items often leads to a reactive approach to those other threats. Neglecting lower-tier risks can lead to a reactive approach to cybersecurity, and incidents that are more costly than investing in protection upfront (e.g., updated toolsets, strategy, and new technology).
Outsourcing and Compliance
42% of organizations are using outsourcing to manage risk in a constrained resource environment. Outsourcing has also become a particularly popular solution for smaller organizations, where running a 24/7 SOC is too costly. While outsourcing can be beneficial, it’s important to note that you can’t outsource the responsibility for cybersecurity. Effective and successful outsourcing requires collaboration and clearly defined expectations between the organization and the service provider. For instance: do you expect a comprehensive report of security health at the end of each week or are you looking for a Level 1 analysis? To what extent do you expect the service provider to understand your threat landscape or business operations? These questions are essential for ensuring the outsourcing delivers maximum value.
Regular maintenance and upgrades are crucial for cybersecurity, yet 28% of organizations delay these actions, risking compliance issues and vulnerabilities from outdated software. A common misconception is that patches and upgrades can “break” systems, but this is rarely the case. Security solutions themselves can become part of your attack surface and trigger compliance repercussions if not properly maintained. For this very reason, at LogRhythm, we work to help our customers by offering a service specifically aligned to automatically upgrading our on-prem offering.
Ultimately, organizations must consider what can be done with the resources they do possess. Again, cybersecurity is a journey, and it’s only through continuous refinement and maturation of security strategies that organizations can reduce the risk of damaging data breaches over time.
To learn more on confronting resource constraints, check out episode 4 of our State of the Security Team webinar series.
For additional statistics on today’s security team resources, budget, breaches, and more, read the full 2024 State of the Security Team research report.
The post CISO Panel: How Security Teams Are Evolving Their Strategies in 2024 appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Delaney Adams. Read the original post at: https://logrhythm.com/blog/how-security-teams-are-evolving-their-strategies-in-2024/
如有侵权请联系:admin#unsafe.sh