2024-7-2 15:36:21 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
TL;DR
- In early June 2024, Snowflake Inc. reported it was investigating a wide-scale cyber breach. So far, more than 165 customers, including companies such as LendingTree and Live Nation, have been notified that their confidential data has been compromised.
- Under new cybersecurity regulations, if an SEC-registered victim of Snowflake’s data breach experiences materially significant consequences, they are obligated to disclose it on Form 8-K, Line 1.05.
- However, due to the ambiguous definition of “material,” there have been reporting inconsistencies among known victims. For instance, while no organization has disclosed it as a “material” event, only two have even publically divulged the incident in a different line item.
- The noticeable inconsistencies may alert shareholders, who, like the public, are already aware of the various corporations that have been targets of the Snowflake attack. This situation could potentially lead to intense scrutiny of reporting decisions or the lack thereof.
- While applicable to all organizations, those that are Snowflake customers in particular need to develop a robust and defensible materiality determination framework to justify reporting decisions (or lack thereof), maintain investor confidence, and ensure compliance.
- Quantified loss benchmarks are one of the most straightforward means of developing such a framework. They offer data-driven information that streamlines the materiality determination process.
- Kovrr’s Cyber Materiality Analysis feature calculates a multitude of loss thresholds on demand, providing stakeholders with the data necessary to efficiently determine materiality for SEC disclosures and more effectively manage material cyber risks.
Leveraging Compromised Credentials as an Initial Attack Vector
After unearthing evidence as early as May 2024, cloud computing–company Snowflake released an official statement on June 2, reporting that they were investigating a series of targeted cyber events. A week later, Google’s Mandiant, who, alongside Crowdstrike, is aiding Snowflake in this investigation, concluded that clients had been attacked after malicious actors had gotten access to compromised credentials.
With roughly 165 of their customers so far notified of the likelihood of their sensitive data being exposed, the attack is beginning to emerge as one of the largest third-party service provider data breaches ever, potentially causing unprecedented market damage. Some of the organizations known to have been affected to date include LendingTree, Live Nation Entertainment, Advanced Auto Parts, and Standander.
Informed Decision-Making With Inconsistent Cyber Loss Information
Although these 165-plus corporations are undoubtedly focused on determining whether they’ve been infiltrated and, if so, executing incident response plans, many of them also have to dedicate resources to other matters. Indeed, the previously mentioned companies, along with Snowflake Inc. itself, are publicly traded on the US stock exchange, making them subject to the Security and Exchange Commission’s (SEC) cybersecurity laws.
The latest cyber rulings mandate that SEC-registered companies report materially impactful events. However, the parameters that define material thresholds are highly ambiguous, allowing for extreme disclosure inconsistencies. It’s entirely plausible that two organizations with similar characteristics may suffer the same amount of damage, but only one determines this loss to be material.
As the consequences of this massive third-party service provider event continue to unfold, some of the hacked companies will inevitably classify it as a material event. At the same time, some may not even report it at all. Sooner or later, this significant room for interpretation will lead to greater criticism of the SEC’s already difficult-to-comply-with regulations, especially among stakeholders who are attempting to make informed investment decisions.
The SEC’s Material Cyber Event Disclosure Intentions vs. Reality
Resolved to rectify disparate reporting practices and ensure stock prices accurately reflect the increasingly costly cyber risk landscape, the US SEC issued stricter cybersecurity directives in July last year. Among other upgrades, these laws introduced Item 1.05 on Form 8-K. The novel line item created a specific space for registrants to disclose “any cybersecurity incident they determine to be material” within four days of said determination.
Defined by its “substantial likelihood that a reasonable shareholder would consider it important,” materiality is plainly a fluid concept. On the one hand, this fluidity is entirely appropriate, as a loss that an investor may consider important in one context may not hold in another. Conversely, these nuances render it nearly impossible for the SEC to achieve its intended goal of providing market shareholders with consistent information.
Indeed, the Form 8-Ks submitted regarding material cyber events thus far have been wildly divergent, providing very little detail into how such a determination was made. Ironically, the majority of these disclosures have also reported events that are not material. While the misuse of the line item was addressed explicitly in May 2024, the lack of a concrete materiality definition will no doubt continue to pose a challenge to market transparency and stability.
The Ensuing “Material” Fall Out of the Snowflake Incident
As of June 2023, only two of the known Snowflake customers who are publicly registered with the SEC have filed Form 8-Ks. Nevertheless, neither has reported the incident to have yet been determined material; other known victims have remained silent.
Live Nation Entertainment, Form 8-K Submitted, Non-Material
The first of the two known SEC-registered Snowflake victims to file an incident disclosure was Live Nation Entertainment, on behalf of its subsidiary, Ticketmaster. Adhering to SEC Director, Division of Corporation Finance Erik Gerding’s advice from May, the company voluntarily disclosed the attack under Line Item 8.01 after identifying unauthorized activity and the subsequent sale of confidential customer information.
As of the filing date, May 31, 2024, Live Nation does not believe that the breach had nor will likely cause a “material impact on overall business operations…financial conditions…or results of operations,” explaining its usage of Item 8.01 as opposed to 1.05. The organization, achieving a 2023 annual revenue of $22.7 billion, reported no other details regarding the ensuing damages or fallout.
In the past month, Live Nation’s stock price has decreased by 0.56%, although it’s slowly started to increase, reaching its nadir on June 14.
Advance Auto Parts, Form 8-K Submitted, Non-Material
The second, only other known victim of the Snowflake attack to have filed a Form 8-K, Advance Auto Parts, disclosed on June 14. Like Live Nation Entertainment, the corporation utilized Item 8.01 to report a breach and later confidential data trafficking while explicitly stating that there had been “no materiality interruption to…business operations” due to said event.
Unlike the entertainment company, Advance Auto Parts included more details about the cyber event’s impact, anticipating financial consequences of roughly $3 million. This additional monetary data is particularly helpful to shareholders, which, after all, is the purpose of these disclosures. For an organization whose revenue for 2023 was $11.27 billion, a loss of $3 million, or 0.027%, is, indeed, most likely not material enough for Line 1.05.
In the past month, Advance Auto Parts’ stock price has decreased more significantly than Live Nation’s at 5.27%. Although prices are beginning to rise, they are doing so slowly.
No Form 8-K Disclosure From Snowflake Inc.
Form 8-K is conspicuously absent from any of Snowflake’s recent SEC filing dockets (only Forms 144 and 4 have been submitted post-event announcement). While it’s highly plausible that the company has not experienced what has been determined to be material damages due to the cyber event, shareholders undoubtedly would find the already-known consequences interesting enough, even if only disclosed in Line Item 8.01.
As the extent of the damage surfaces, customer trust is most likely to erode, and Snowflake’s reputation will decline, undoubtedly impacting its market value. In the past months, the company’s stock price has fallen by a whopping 17.32%, and there is little sign of recovery in the near future. Although the expansive news coverage is currently keeping reasonable investors informed, they have unpromisingly received little detail directly from the organization itself.
The Need for a Robust, Defensible Materiality Determination Framework
The glaringly inconsistent disclosure practices amongst those companies whose data is known to have been exfiltrated in the Snowflake incident may consequently lead to allegations of non-compliance. Questions of why some companies are taking proactive measures to be transparent with shareholders and why others have decided not to alert the SEC naturally arise.
Moreover, with relatively little information offered regarding why certain events were deemed to be materially impactful or not, organizations must, at the very least, be internally prepared to face legal scrutiny regarding their Form 8-K disclosure decisions. Only by having a standardized, well-documented approach to the determination process can companies strongly defend their choices and maintain investor trust.
Leveraging Quantification to Establish Preliminary Material Benchmarks
Because an event’s materiality comprises several factors, stakeholders would do well to harness quantitative loss benchmarks as a starting point for the determination process. These values are relatively easy to calculate and provide a clear roadmap for organizations that must assess impact without unreasonable delay. In fact, many businesses worldwide already utilize quantified thresholds for incident evaluation, cyber or otherwise.
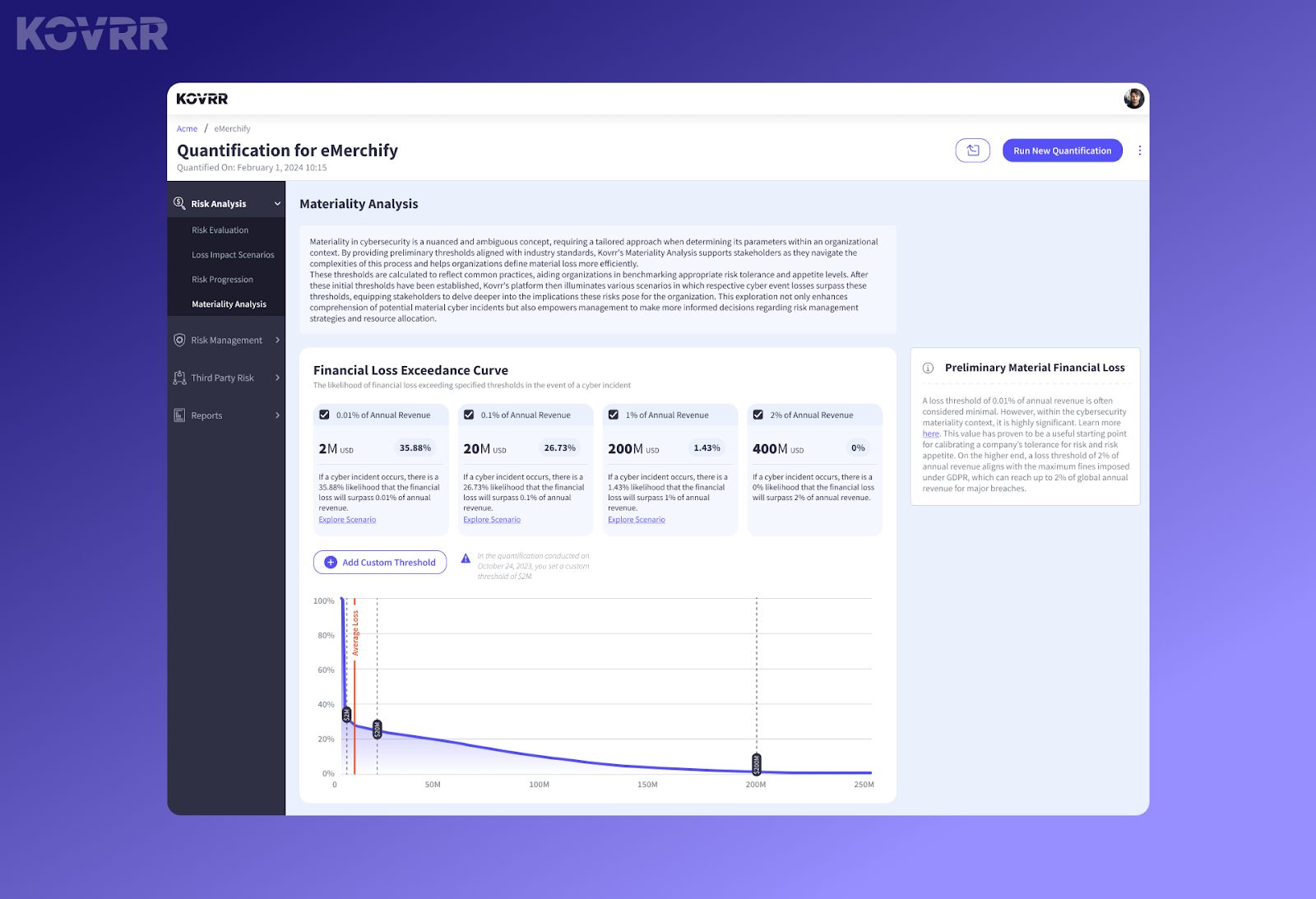
After conducting extensive research and evaluating various impact levels of detrimental business events, cyber risk management experts found that a 0.01% financial loss to revenue threshold is a highly logical starting point for determining the material significance of an event. While there is yet to be a universally accepted standard for material loss, this basis point of revenue nevertheless offers structure to an otherwise overwhelming process.
Once equipped with this preliminary threshold, organizations are then free to explore the other components that contribute to a material impact, using all of the information in the aggregate to make the final disclosure decision. It’s important to note that there may be times when a material event did not surpass the benchmark (or vice versa). Rather than using the single basis point of revenue loss as a strict rule, it should be considered more of a guidance indicator.
Kovrr’s On-Demand Cyber Materiality Analysis
Recognizing the challenges organizations face when creating a standardized materiality framework, Kovrr created the Cyber Materiality Analysis feature. This feature not only calculates an organization’s specific 0.01% revenue loss threshold but also quantifies the likelihood of experiencing a loss of that amount in case of an incident. It likewise offers this information according to other financial benchmarks, including 0.1%, 1%, and 2% loss of annual revenue.

The novel cyber risk management feature similarly provides loss thresholds for the number of data records compromised and outage hours. For example, stakeholders may decide that, instead of focusing on finances, a more appropriate quantitative value to use to initially measure materiality is the loss of a specific percentage of data records. Kovrr’s platform provides these figures, along with a myriad of other insights that facilitate the material determination process.
Read Materiality Analysis Offers Risk Managers Data-Driven Loss Thresholds to learn more about this innovative feature, or schedule a free feature demo today.
Staying Compliant With Cyber Risk Quantification (CRQ)
Given the SEC’s interpretative nature of what constitutes a material event, registrants must establish a data-driven approach to their determination processes that can withstand scrutiny. By leveraging a cyber risk quantification platform such as Kovrr’s to calculate preliminary loss thresholds, stakeholders ensure they are well-equipped in case their reporting decisions are questioned.
Quantified benchmarks provide a defensible roadmap that organizations can use to streamline this otherwise gargantuan task. Handling the consequences of a cyber event is stressful enough, which is why having this data-driven framework is crucial not only for regulatory compliance and consistent disclosures but also for making sure resources are devoted to the tasks that matter most.
Contact one of Kovrr’s cyber risk management experts today to discover how our CRQ platform harnesses broader business metrics to aid compliance efforts. Stay aware. Stay prepared.
如有侵权请联系:admin#unsafe.sh