2024-6-28 17:15:58 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
The number of attacks targeting web applications and application programming interfaces (APIs) has increased significantly and shows no sign of slowing. According to Verizon’s latest Data Breach Investigations Report (DBIR), web applications were last year’s top attack vector, accounting for 80% of incidents and 60% of breaches. Let’s examine why so many applications remain vulnerable despite high-severity warnings and how to minimize the threat to your organization.
There are two main reasons why web applications are attractive targets for attackers. First, many carry vulnerabilities or configuration errors. Second, many contain extremely valuable information, such as personal and financial data – and a successful breach will give attackers direct access to that data. What’s particularly frustrating for security professionals is that this is not a new attack vector.
In 2023, 5.8 million attacks targeting Shellshock, a family of security bugs first reported 10 years ago, were the third most detected threat that hit Barracuda’s integrated Intrusion Detection Systems. The prevalence of these attacks signals that attackers are aware of numerous systems that remain vulnerable due to a lack of updates. They’re using Shellshock to orchestrate distributed denial of service (DDoS) attacks and exploit vulnerable interconnected systems through bots and botnets.
Shellshock encompasses six related CVE designations, each receiving the highest severity score of 10. These bugs reside in the Unix Bash shell, the standard command-line interface on Linux, Unix and Mac-based operating systems. Successful Shellshock exploitation allows attackers to force Bash to execute arbitrary commands, thereby gaining unauthorized access to many internet-facing services, including web servers that rely on Bash for processing requests.
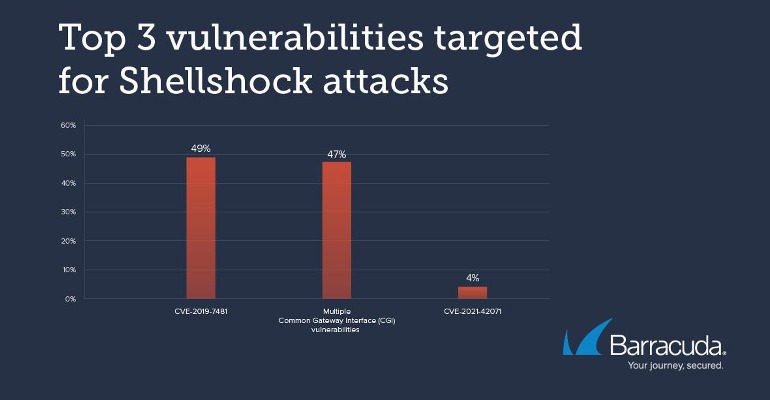
The chart below shows the top three vulnerabilities that Shellshock attacks target, underscoring the longevity of vulnerabilities that remain undetected in the software supply chain. Note that a device running the latest firmware version is still vulnerable if the software creators do not update their supply chain libraries.
CVE-2019-7481 is a 7.5-rated SQL injection vulnerability in a security service for which a patch exists. CVE-2021-42071 is a critical 9.8-rated vulnerability in a visual tool application that could allow an unauthenticated attacker to achieve remote command execution.
Attackers have been targeting CVE-2019-7481 since at least 2021 to install Mirai botnet variants. The Mirai botnet, consisting of many compromised connected (IoT) devices, primarily facilitates DDoS attacks. Since Mirai appeared in August 2016, researchers have identified multiple variants in the threat landscape, with Mirai mainly attacking IoT Linux-based devices. Most attacks initiate by downloading a shell script fetching several platform-specific malware binaries to execute them. Upon infection, the device joins the expanding botnet.
Our logs first recorded two Mirai variants targeting the LuCI web interface on OpenWRT-based routers. This management interface should not be internet-accessible, yet it frequently is, leaving it open for attackers to exploit.
Attackers deployed the first variant to run a shell script called “sorry.sh.” URLhaus reports have since led to the script’s removal, and their analysis confirms its role in a Mirai/Gafgyt infestation attempt despite its unavailability.
The second variant is still active. The attackers are using it to delete everything in the root directory and then download a shell script in /tmp. When executed, the shell script downloads several platform-specific binaries and executes them in order.
Cryptominer Infections Target Vulnerabilities
Our research found that besides Shellshock, attackers have also aimed at vulnerabilities to set up cryptominers. In 2022, cryptominers sought to exploit the newly discovered vulnerability in Atlassian Confluence. By February 2024, attackers leveraged older ThinkPHP vulnerabilities to install XMRig miners. Typically, they target older ThinkPHP vulnerabilities — remote code execution (RCE) vulnerabilities from 2018 and 2020, which should ideally be patched by now.
These attacks target specific vulnerabilities in concerted campaigns. About a decade ago, attackers predominantly sought out and exploited new vulnerabilities, like zero-days, to infiltrate networks. Now, they’re exploiting older, unpatched vulnerabilities to take advantage of the often incomplete security of software supply chains.
Addressing software supply chain security proves challenging. Even with the latest file transfer software deployed, it might internally rely on a vulnerable version of Log4J, leading to a false sense of security due to an underlying known vulnerability. Regular vulnerability scans are essential to uncover such issues, especially with critical libraries like Log4J. However, vulnerabilities in less-known libraries used by specific software can be harder to detect.
The strategy of defense-in-depth remains critical. Building a multilayered defense for your network and applications is vital to thwarting attacks before they compromise your application. This strategy protects against current threats and buys time to address new vulnerabilities as they emerge.
Defending against DDoS attacks is also essential. Attackers exploit years-old vulnerabilities to assemble botnets to launch new types of DDoS attacks, like HTTP/2 Rapid Reset. Implementing solutions capable of mitigating both traditional volumetric DDoS attacks and more sophisticated application-level DDoS attacks is crucial for maintaining business operations. The vulnerabilities discussed highlight the software supply chain as a critical vulnerability point in applications, necessitating substantial protective measures.
The steady volume of cyberthreats targeting web applications and APIs exploiting old and new vulnerabilities spotlights that the software supply chain is a weak link requiring a significant protective layer. APIs, bot attacks and client-side attacks are the latest ways hackers are working to breach applications.
Deploying bot protection, API gateways and software supply chain protection (scanning) will help thwart the attacks, but beware of the complexity of implementing point solutions. Taking a platform approach to application security protects against threats while being easy to use and manage. Unlike traditional, siloed security measures that focus on specific areas or layers of an application, a platform approach encompasses a comprehensive suite of security tools and practices designed to protect the entire application ecosystem.
如有侵权请联系:admin#unsafe.sh
