2024-6-26 23:51:16 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
Do you know the difference between internal pen tests, external pen tests, and wireless pen tests? It matters.
With the threat landscape expanding and criminals taking advantage of security gaps, organizations are turning to controls that can help them limit their exposure. Among other controls, penetration testing stands out because it simulates attackers’ malicious activities and tactics to identify security gaps in business systems or applications. A penetration test aims to understand what vulnerabilities are in business systems, how they could be exploited, and the potential impact if an attacker were successful. Because pen tests thoroughly investigate vulnerabilities, the scope of each pen test must be limited and may differ from test to test.
Pen tests take on different types of perspectives: internal, external, and wireless. In this blog, we will examine what each type of pen testing entails, who conducts these tests, and why they are all worth performing.

What is External Pen Testing?
External pen tests vet external infrastructure, or all public-facing assets—including the internet at large. Additionally, many organizational applications, like mail servers, websites, or even customer portals maintain a connection to these external networks and can also provide a doorway from which a threat actor can pivot.
External penetration tests are typically what people think of when they hear about pen testing. These tests use the same techniques as adversaries to attempt to exploit weaknesses in an organization’s front facing perimeter or attempt to bypass them altogether with strategies like a phishing campaign or other social engineering methods.
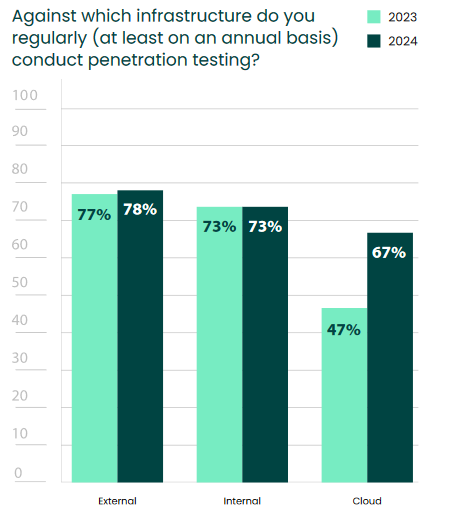
The 2024 Pen Testing Report revealed that 78% of security professionals pen test their external infrastructure. When defending against today’s adversaries, organizations understandably need to know how their first line of defense will hold up.
What is Internal Pen Testing?
Internal pen testing proves internal architecture against adversaries who have already gained a foothold in the organization. Since such attacks start with internal access, they may attempt to achieve more high-value objectives including acquiring high-level privileges, compromising the Domain, or accessing other valuable assets and/or information.
Internal attacks can originate from:
- Malicious insiders
- Compromised users
- Careless employees
- Insecure third-party vendors
- Clients
- Customers
And more. Internal threats can be anything from bad hygiene habits, like weak passwords and poor access controls, to system and app misconfigurations and insecure endpoints. When it comes to malicious insiders, the Verizon 2024 Data Breach Investigations Report notes that “Privilege Misuse,” (the new bespoke category), accounted for 897 incidents, 854 with confirmed data disclosure. Considering there were 10,626 total incidents of data disclosure (breaches), that figure amounts to nearly ten percent.
What is Wireless Pen Testing?
Wireless network pen testing is neither internal nor external but falls under its own category. It involves probing wireless access points and plumbing for vulnerabilities and configuration weaknesses that could allow unauthorized access.
In a wireless pen test, teams will check for vulnerabilities in your corporate Wi-Fi deployment, such as:
- Rogue access points | An access point installed on the network without the network owner’s permission. These could be something as simple as a personal employee router connected to the network for work purposes, but they increase the attack surface and increase risk as they typically do not have the same security configurations as the rest of the network.
- Cracked WPA pre-shared keys (PSKs) | A PSK is a shared secret (used previously) to establish a secure connection between a client device (mobile, laptop) and a wireless access point. It is used to encrypt all communication between them, but when that PSK gets stolen or cracked, it could allow unauthorized users onto the network.
- Spoofed MAC addresses | Changing the MAC address of a device on the network could make it seem like another device, funneling all communication to the malicious agent (with the spoofed MAC address) instead.
And other malicious tactics. The wireless penetration testing review process consists of:
- Discovering approved and rogue access points such as Wi-Fi networks, Bluetooth devices, wireless printers, RFID, general IoT, and more.
- Proving existing protection methods including, SSID, cloaking, MAC address filters, WEP, and WPA.
- Analyzing the current configuration of wireless access points.
- Assessing the footprint of the wireless signal to determine how easy it would be for rogue clients to access the network.
While most organizations honor wired pen tests, wireless penetration tests often get overlooked. However, these types of attacks are significantly easier to launch (and get away with) as it is improbable to block someone from being in the immediate physical vicinity of your Wi-Fi network. Fortra’s wireless pen testing assessment of your wireless protocols identifies vulnerabilities and suggests ways to close those gaps.
Who Should Be Conducting These Pen Tests?
Though it’s easy to think that in-house teams would handle all internal tests and external/third party teams would handle external tests, this is not the case. Both teams can conduct internal, external, and wireless pen tests.
Utilizing both types of teams provides the capability to conduct more tests and allows you to get fresh eyes on the problem. Internal teams can mix it up by pen testing wireless assets and go in without bias. External teams could pen test internal systems and help prevent internal teams from getting too used to the environment. And third-party services can also be pulled in to provide a fresh perspective and differing skill sets, helping to simulate the kind of diversity your team will be facing in a real-world scenario against unknown attackers.
Creating a Holistic Pen Testing Strategy
Though organizations must make tough choices when deciding which tests they have the time and resources to run, one of the most important criteria to consider is whether you’re balancing internal and external tests. Several things are true:
- Only testing externally overlooks vulnerabilities that can be exploited by a malicious insider or a compromised account. And with strategies like phishing more popular than ever, it’s critical to remember how easily network access can be attained.
- However, only testing internally can prevent organizations from inadvertently leaving a door wide open, allowing an attacker to get in without much difficulty.
- Wireless assets warrant their own attention and play by their own security rules, just like internal and external systems. They must be tested for Wi-Fi deployment weaknesses that internal and external tests leave behind.
All three are needed to honestly say that you’ve fully pen tested your environment – your entire environment. And you almost have to test all three to make each one worth it. Imagine locking your front and back doors, but always leaving the side one open. Attackers don’t care how they breach an organization – they will try every door until they get in! How much security would those two locked doors be with a third one constantly unlocked?
Today’s cybercriminals aren’t picking and choosing one method alone, and neither should we. It is our job as defenders to be where the bad guys are, and when it comes to attacks, we need to be ensuring our systems from the inside, out.
如有侵权请联系:admin#unsafe.sh