2024-6-25 06:28:41 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Amazon Web Services (AWS) is the world’s largest cloud service provider. Unsurprisingly, they are committed to providing tools, solutions, and best practices that allow their customers to leverage Generative Artificial Intelligence (GenAI) workloads on AWS securely. Organizations are rapidly employing GenAI to bring increased productivity and creativity to businesses. In nearly all uses of GenAI, the AI models require access to data and that data can be nonpublic and private to the organization. Private and nonpublic data can include trade secrets, personal identifying information, and compliance data.
Thales and AWS have a strong partnership of working together to provide sovereign solutions for AWS customers. In 2022, Thales and AWS jointly unveiled external key management as a Hold Your Own Key (HYOK) strategy in AWS. AWS and Thales continue to jointly engineer and develop enhanced data protection capabilities, focusing on advanced encryption solutions and secure key management to support organizations working to secure their hybrid enterprises.
What Are GenAI Security Challenges?
GenAI is now being rapidly deployed across many verticals along a widely diverse set of use cases. Organizations, large and small, across many industries are looking to gain benefits from GenAI. A partial list of already identified benefits include:
- Improving customer experiences (chatbots and virtual assistants)
- Boosting employee productivity (employee assistants)
- Enhancing creativity & content creation (marketing)
- Accelerating process optimization (document processing)
- Transforming industries from responsive to proactive (healthcare)
A majority of GenAI options are powered by Large Language Models (LLMs) that are pre-trained with source input data to perform desired tasks such as content generation and code generation.
The AI lifecycle typically encompasses three phases:
- Sourcing (data and model)
- Training
- Inference
Each phase of the AI lifecycle is a potential exposure point for threat actors to engage in cyberattacks. Two methods to limit data exposure and mitigate the risk to cyberattacks for organizations training LLMs in GenAI include:
- Limiting the source data that will be used to train the AI models. Close monitoring is needed when dealing with nonpublic (organizational confidential) data sets.
- Ensuring that data is only used in an authorized manner and as needed.
Before organizations expose nonpublic data to an AI model, they should verify the sensitivity of the data that the GenAI can access is verified. Tools such as Thales Data Discovery and Classification ensure that only properly classified and identified data is available to the AI model and are integral to ensuring that sensitive data is not exposed to or being queried by the AI model.
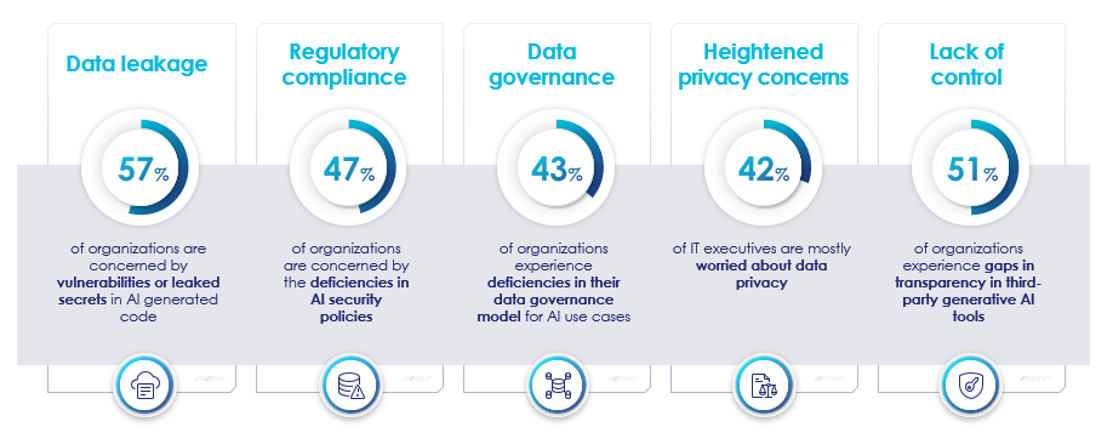
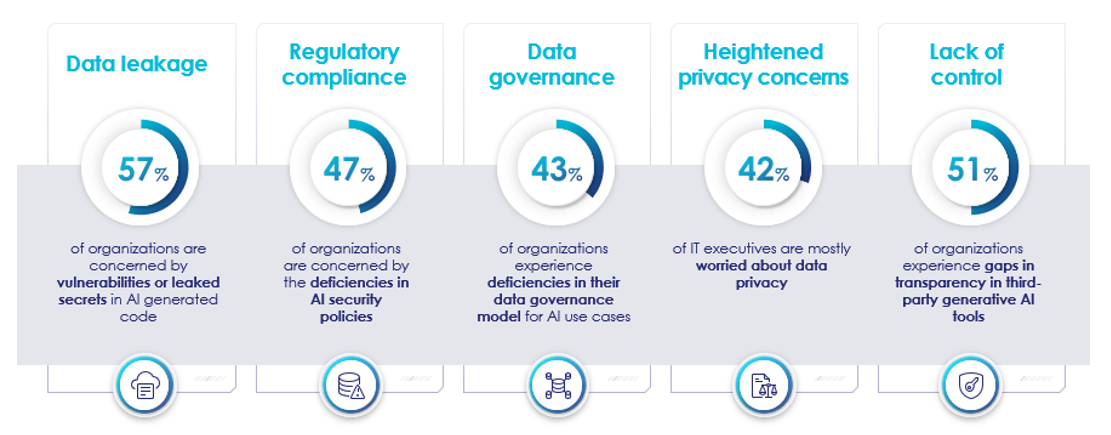
Each year Thales co-authors the Global Data Threat Report, where over 3,000 security professionals and executives around the world share their security concerns. In the 2023 study, a major concern highlighted was about data leakage regarding AI creating code, regulatory compliance, data privacy, and lack of control. The report found that 68% of the respondents expressed concerns that rapid changes in AI are challenging existing organizational plans.
The chart below summarizes additional organizational concerns about data leakage, privacy concerns, and lack of control over the rapid implementation of AI.
How is AWS Securing GenAI?
Amazon Q, Bedrock, and SageMaker are a few of the primary AWS offerings that allow AWS customers to quickly develop GenAI solutions, including the AWS AI–powered assistant. Amazon Q is aimed primarily at supporting business use cases and offers solutions that allow organizations the opportunity to integrate and leverage their internal data. Whether that data includes commercial intellectual property, trade secrets, supplier, or customer nonpublic data, organizations must understand how to limit the sensitive data visible to Amazon Q. It is imperative that precautions are taken to ensure no unauthorized apps, processes, or individuals, such as bots or threat actors, can access the nonpublic data.
AWS employs the Nitro System and Nitro Enclaves as their computing backbone, with unparalleled security and performance. AWS has announced extended support for Nitro Systems that will be optimized for GenAI and AI workloads, notably GPU intensive processes. AWS Nitro Enclaves offer an integrated solution with AWS Key Management System (KMS) that enables AWS customers to manage and encrypt sensitive data using encryption keys that the organization owns and controls. The ownership of the keys is managed using the Thales CipherTrust Manager which provides Enterprise Key Management and enables digital sovereignty for AWS customers. In a recent blog, AWS outlined their approach to securing data used for Generative AI.
How does AWS Nitro Enclaves Integrate with Key Management?
AWS has developed the Nitro System to fulfill the principles of Secure AI Infrastructure. The first principle isolates your AI data from AWS operators, ensuring its security. The second principle allows you to remove administrative access, enhancing control over your AI data. With Nitro Enclaves and AWS KMS, you can encrypt your sensitive AI data using your keys, store it securely, and transfer it to an isolated compute environment for inferencing. Throughout the process, your data remains encrypted and isolated from your users, software, and AWS operators.
How Can Thales Secure Generative AI Workloads on AWS?
AWS KMS External Key Store (XKS) is integrated with the Thales CipherTrust Cloud Key Management (CCKM) solution so that organizations can keep their encryption keys outside of AWS KMS. This approach is also called Hold Your Own Key (HYOK), which provides sovereign controls. When deploying GenAI solutions, AWS customers can manage the encryption of their nonpublic data using AWS XKS with Thales CCKM.
The XKS collaboration between Thales and AWS has led to the development of services that help organizations maintain control over their encryption keys and manage access to sensitive data securely. These technologies enable organizations to address challenges related to cloud migration, digital sovereignty, and the secure handling of sensitive information across various cloud platforms. Understanding when and how to employ AWS external key management with Thales is a crucial use case for organizations developing in-house AI capabilities and maintaining data security and compliance across different regulatory environments.
How Do Thales and AWS Ensure Sovereign Controls?
Developed with Thales since its inception, the AWS XKS combined with CCKM offers organizations looking to use critical workloads in AI a way to maintain sovereign control of sensitive data throughout their AI journey. Thales enables external key management and is an integral part of a digital sovereignty strategy for organizations that leverage AWS XKS to enhance data security.
How to Leverage External Key Management
By leveraging the Thales external key manager with AWS XKS to manage cryptographic keys securely, organizations have complete confidence that data encryption keys are handled and stored securely, can be backed up and managed external to the Cloud Provider, and use of policy prevents unauthorized access to encrypted data. By managing keys external to the Cloud Provider KMS, organizations can selectively apply encryption based on organizational policy and enterprise key lifecycle management. This organizational enterprise external key management allows organizations to isolate data protection, including the option to store the encryption keys external to the Cloud Provider. This isolation is a key risk mitigation strategy. Using Thales for external key management in AWS supported platforms, organizations who may be concerned about data loss or leakage can disable access to the cryptographic keys, providing an additional layer of security and assurance. With the wrapping keys being inaccessible, organizations ensure that encrypted data remains encrypted even if other online defenses are compromised.
How To Comply with Auditing and Monitoring Requirements
Thales external key manager implements robust auditing and monitoring capabilities. Monitoring is crucial for detecting unauthorized access or anomalies in data usage, which is often an early or first indicator of a security breach or detection of anomalous behavior. Thales CipherTrust Manager provides audit logging that enables organizations to track how and when data is accessed and by whom.
As a cybersecurity aligned solution, Thales increases the protection of organizational data that is an essential foundational building block to AI research and models. Thales and AWS work together to provide a robust framework for securing sensitive data used by AI systems, ensuring compliance with data protection regulations, and maintaining the integrity and confidentiality of the data.
How To Protect Hybrid Workloads
For organizations looking to secure their confidential data, whether on-prem, in a cloud provider or in the hybrid enterprise, Thales offers CipherTrust Transparent Encryption (CTE). CTE facilitates Bring Your Own Encryption (BYOE) for organizations by maintaining nonpublic data in an encrypted state until the time of use by an authorized service or entity. The Thales transparent data encryption solution automatically encrypts and decrypts data as it is read and written to storage, operating invisibly to applications and business processes. Thales CTE enables organizations to protect their data without altering existing workflows.
Cybersecurity best practices dictate that organizations employ enterprise key lifecycle management including issuing, rotating, and backing up the encryption keys used to protect nonpublic data. The Thales CTE solution along with CipherTrust Manager allows organizations to own, instantiate, and use their keys, which they manage and store independently, crucial for maintaining control in BYOE scenarios. Thales transparent encryption provides granular access controls, enhancing security by ensuring data cannot be decrypted without appropriate permissions. The Thales BYOE solution provides comprehensive auditing capabilities that support regulatory compliance by monitoring encrypted data access and key usage. With support for various environments, including cloud, hybrid, and on-premises, Thales CTE ensures organizations can apply BYOE consistently across all supported platforms and locations.
How to Audit the Authorization for the AI Service to Access Nonpublic Data
Managing how the GenAI can access nonpublic data is essential. Organizations need to ensure only authorized processes can access and monitor the processes that are accessing or attempting to access the nonpublic data. A best practice and risk mitigation approach is to use dynamic credential rotation to ensure human or machine credentials cannot be obtained and improperly used. Advantages to organizations using dynamic credential rotation include:
- Enhanced Security: By frequently changing credentials, dynamic rotation minimizes the damage if an attacker manages to steal a credential, making stolen credentials less valuable to attackers.
- Reduced Attack Surface: Dynamic credentials limit the window of vulnerability. Since they are only valid for a brief time, there is less chance of them being exposed through leaks or misconfiguration.
- Automated Management: Dynamic credential rotation can be automated, eliminating the need for manual intervention and reducing the risk of human error.
- Improved Auditing and Compliance: Because dynamic credentials are generated on demand, easy tracking of who has accessed, can be helpful for auditing purposes, and can also help organizations meet compliance requirements.
- Scalability: Dynamic credential management systems manage a large set of credentials with complex rule sets more efficiently than manual systems. This makes them a viable choice for organizations with complex IT environments.
Thales CipherTrust Secrets Management provides a solution to support automated dynamic credential management. Employing just-in-time or dynamic credential rotation can significantly improve an organization’s security posture and improve the overall security of an AI initiative by making it more difficult for attackers to exploit stolen credentials. It also results in improved audit results to ensure only authorized services are accessing nonpublic data.
Do Not Let Security Concerns Stop Your AI Transformation
We understand that GenAI is important to our customers. Where security and compliance are concerned, Thales and AWS are here for your journey. Thales has over 50 corporate AI related initiatives and we follow a secure AI development methodology to ensure we are benefiting from AI without jeopardizing data integrity or privacy.
Thales encryption and key management solutions are used to protect organizational data as the organization commences on internal AI development efforts. Thales offers a wide range of security solutions. The broad range of Thales security solutions include those offered by Imperva that enables enterprises protect their applications and APIs anywhere at scale.
Thales data security solutions provide granular protection of applications and credentials — protecting both human and machine identities, and data at rest, in use, and in motion.
Learn More About Sovereign Controls with Thales and AWS
如有侵权请联系:admin#unsafe.sh