2024-6-25 18:46:26 Author: cyble.com(查看原文) 阅读量:33 收藏
Key Takeaways
- Cyble Research and Intelligence Labs (CRIL) recently came across a malware campaign involving a malicious lnk file associated with the UAC-0184 threat actor group.
- Previously, UAC-0184 targeted Ukrainian entities in Finland, utilizing the Remcos RAT in their operations.
- In their latest campaign, there are signs suggesting the group may be focusing on Ukraine, using disguised lure documents to distribute the XWorm RAT.
- When the LNK shortcut file is executed, it triggers a PowerShell script that downloads a ZIP file containing both legitimate and malicious Python components, including an encrypted payload.
- The current attack employs DLL sideloading and Shadowloader to execute the XWorm RAT as the final payload.
- Ultimately, the XWorm RAT malware attempts to connect to a Command-and-Control (C&C) server for remote access activities. At the time of analysis, the C&C server was inactive, resulting in no observed malicious activities.
Overview
CRIL recently observed a malware campaign targeting Ukraine using the Remote Access Trojan (RAT) known as XWorm. Upon investigation, it was found that this campaign is associated with the Threat Actor (TA) group UAC-0184. Previously, UAC-0184 has targeted Ukrainian entities in Finland, employing the Remcos RAT in their operations. They have utilized techniques such as steganographic image files and the IDAT Loader (SHADOWLADDER, GHOSTPULSE) to distribute malware payloads.
At the end of May, CRIL observed a campaign in which the TA is using Python-related files as part of its strategy to evade detection. The exact initial attack method is still unknown, but it may involve dissemination through phishing or spam emails with ZIP attachments.
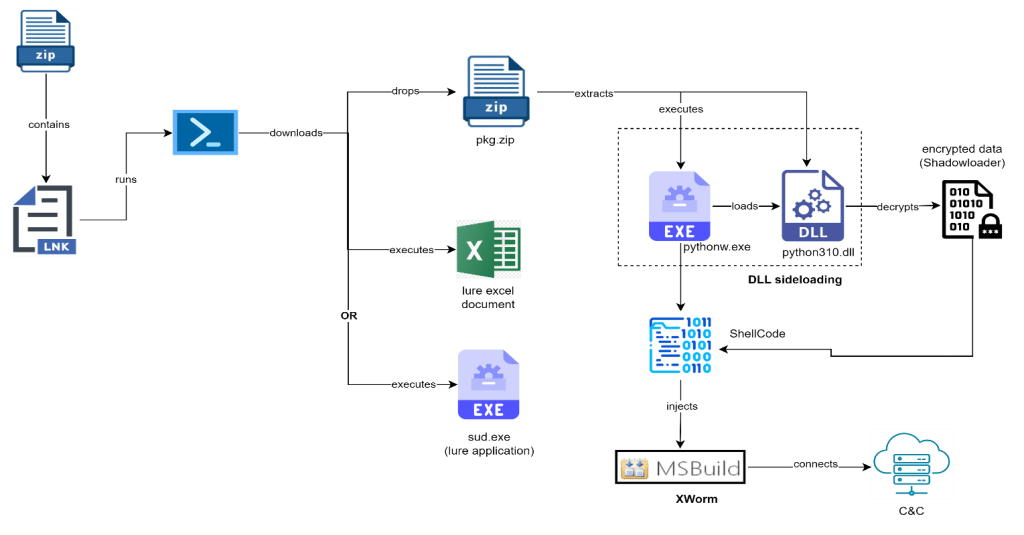
Our investigation commences with an analysis of the .lnk file found within the ZIP archive. Upon execution of the LNK shortcut, it initiates a PowerShell script that downloads an additional ZIP file and lure document. This ZIP file houses several items, including a genuine Python executable, a malicious Python DLL, and an encrypted payload binary. The infection technique employs DLL sideloading and Shadowloader to execute the final payload, identified as XWorm RAT.
The figure below depicts the infection chain of the UAC-0184 TA to deliver the XWorm payload.

Figure 1 – Infection chain
Technical Analysis
When extracting the contents of the ZIP file, revealing an LNK shortcut file named “NewCopy.xlsx.lnk.” If the user incorrectly assumes this LNK file is a real Excel worksheet and double-clicks on it, a deceptive Excel file will appear, as illustrated in the figure below.

Figure 2 – Lure Excel document
The content of the Excel worksheet does not reveal the victim of this campaign. When the lure document is displayed to the user, the LNK shortcut file executes in the background, launching the embedded PowerShell command from %appdata%, as shown in the figure below.

Figure 3 – Command-line of the LNK shortcut file
The PowerShell script is designed to download two files named pkg.zip and NewCopy.xlsx from the below URL to the current directory:
- hxxp://88.151.192[.]128/djfhu34u9983234s3fnvmxxzpkg.zip
- hxxp://88.151.192[.]128/djfhu34u9983234s3fnvmxxzcip/NewCopy.xlsx
Initially, the script downloads “pkg.zip,” extracts its contents, and creates a folder named “SecurityCheck” in %appdata%. It then saves the extracted files in the folder and proceeds to execute “pythonw.exe” using the start command.
Following this, the script downloads “NewCopy.xlsx” (a lure Excel document) and initiates its execution with the start command, as shown in the code snippet below. CRIL has noted that the TA UAC-0184 utilized a similar PowerShell script in a previous campaign, as mentioned by CERT-UA.

Figure 4 – Code snippet of the PowerShell script
The figure below illustrates the presence of the downloaded files “pkg.zip” and “NewCopy.xlsx,” along with the extracted files saved within the “% appdata%SecurityCheck” and “% appdata%ZY_Manage_testv4” directories.

Figure 5 – Downloaded files
Upon execution of “pythonw.exe,” it duplicates all files from that location and stores them in a new folder named “%appdata%\ZY_Manage_testv4\”. It then proceeds to execute “pythonw.exe” from this newly created directory, as shown in the below process tree figure.

Figure 6 – Process tree
DLL Sideloading
The “pythonw.exe” loads the malicious DLL named “python310.dll” through the DLL side-loading method, which in turn creates a cmd.exe process that initiates a suspended MSBuild process. Then, the loader decrypts the file named “daikon.tif” (which is Shadowladder) and injects the shellcode into the previously created “MSBuild.exe” using the Process Hollowing technique. The figure below illustrates the process in which pythonw.exe loads python310.dll and injects shellcode from daikon.tif.

Figure 7 – DLL sideloading method
XWorm
The injected content, identified as XWorm, then proceeds to perform malicious operations on infected systems. XWorm is categorized as commodity malware, designed to be easily accessible to threat actors, even those with limited technical expertise, who can purchase and use it for various cybercrimes. This versatile malware offers a wide range of capabilities, including data theft, DDoS attacks, cryptocurrency address manipulation, ransomware deployment, and downloading additional malware onto compromised systems. Cyble Research & Intelligence Labs (CRIL) has conducted a thorough analysis of XWorm and previously shared detailed insights about this malware on our blog.

Figure 8 – Presence of XWorm strings in the injected MSBuild exe
After execution, XWorm drops a VB Script file with a random name into the %temp% folder and runs it. This script then connects to the Command-and-Control (C&C) server, as shown below.

Figure 9 – C&C server
In mid-June, we came across other files in the campaign by the same threat actor, indicating a focus on Ukraine based on the lure. In this campaign, we have observed the LNK shortcut file exhibiting similar behavior as previously mentioned. However, unlike the earlier file that used an Excel worksheet as a lure document, this one uses a document viewer application as bait. The LNK shortcut file is named “Відомості про кредитора.dvs.”
When the user executes the LNK shortcut file, disguised as a .dvs file (possibly representing “document viewer software”), they will be confronted with a misleading GUI named “Державна виконавча служба: система документообігу,” which translates to State Executive Service: Document Management System, as shown below. The .dvs extension may be specific to the software employed by the State Executive Service for handling and displaying documents. We’ve noticed that the TA has employed a similar deceptive GUI in their past campaigns.

Figure 10 – Lure document viewer application
The following image displays another deceptive document from the campaign, which uses an electricity bill theme to target Ukrainians.

Figure 11 – Lure word document
The following figure displays a code snippet of a PowerShell script executed when launching the LNK shortcut file named “Відомості про кредитора.dvs.”

Figure 12 – Code snippet of the PowerShell script
In this case, the TA deploys the XWorm payload by leveraging IObit Driver Booster files instead of Python-related files. Here, RttHlp.exe (the IObit Driver Booster executable) loads a malicious DLL named vcl120.bpl via DLL side-loading. This DLL then spawns a cmd.exe process, which subsequently initiates a suspended MSBuild process. Following this, the loader decrypts a file named “bacteriostat.flac” and injects shellcode into the running “MSBuild.exe” process using the Process Hollowing technique.
Conclusion
UAC-0184 is relentlessly carrying out a malware campaign against Ukraine, continually refining its techniques to better evade detection. Notably, it leverages Python-related files to avoid detection in this campaign. The deployment of the final payload XWorm RAT in this campaign indicates a primary objective of establishing remote access to compromised systems. UAC-0184’s operations demonstrate a sustained effort to infiltrate Ukrainian targets for strategic purposes.
Our Recommendations
- The initial breach may occur via spam emails. Therefore, it’s advisable to deploy strong email filtering systems to identify and prevent the dissemination of harmful attachments.
- When handling email attachments or links, particularly those from unknown senders, exercising caution is crucial. Verify the sender’s identity, particularly if an email seems suspicious.
- Consider disabling or limiting the execution of scripting languages on user workstations and servers if they are not essential for legitimate purposes.
- Implement application whitelisting to ensure only approved and trusted applications and DLLs can execute on your systems.
- Deploy strong antivirus and anti-malware solutions to detect and remove malicious executable files.
- Enhance system security by creating strong, distinct passwords for each account and, whenever feasible, activating two-factor authentication.
- Set up network-level monitoring to detect unusual activities or data exfiltration by malware. Block suspicious activities to prevent potential breaches.
- Regularly back up data to guarantee the ability to recover it in case of an infection and keep users informed about the most current phishing and social engineering methods cybercriminals employ.
MITRE ATT&CK® Techniques
| Tactic | Technique | Procedure |
| Execution (TA0002) |
Scripting (T1064) | Executes visual basic scripts |
| Execution (TA0002) |
PowerShell (T1059.001) | Powershell downloads PE & ZIP files |
| Persistence (TA0003) |
Registry Run Keys / Startup Folder (T1547.001) |
Creates a start menu entry (Start Menu\\Programs\\Startup) |
| Privilege Escalation (TA0004) |
DLL Side-Loading (T1574.002) | Adversaries may execute their own malicious payloads by side-loading DLLs. |
| Privilege Escalation (TA0004) |
Process Injection (T1055) |
Injects malicious content into MSBuild.exe process. |
| Defense Evasion (TA0005) |
Obfuscated Files or Information (T1027) |
.Net Binary include packed or crypted data. |
| Defense Evasion (TA0005) |
Deobfuscate/Decode Files or Information (T1140) | .NET source code contains calls to encryption/decryption functions |
| Discovery (TA0007) |
Process Discovery (T1057) | Queries a list of all running processes. |
| Discovery (TA0007) |
Security Software Discovery (T1518.001) |
May try to detect the virtual machine to hinder analysis |
| C&C (TA0011) |
Application Layer Protocol (T1071) |
Malware exe communicate to C&C server. |
| C&C (TA0011) |
Ingress Tool Transfer (T1105) |
Downloads files from webservers via HTTP |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type |
Description |
| bf5a2450f5287f775c2427590c29c27e28e3662c2f68296c64cdacdb639f3b97 | Sha256 | NewCopy.xlsx.lnk |
| hxxp://88.151.192[.]128/djfhu34u9983234s3fnvmxxzpkg[.]zip | URL | Malware download URL |
| 38dea3732044129bd99314de582ba3d58a649c8967fe12b98cd867ca6e349ffe | Sha256 | Pkg.zip |
| 06adb754096f5853999038c000d8cdafa69bb1696b1011e781ab18bbea6107ce | Sha256 | Python DLL |
| 40fd3597c44d10e201304b80c20dd8f2a1ad1ee1032f90d83d7917e037a1d130 | Sha256 | vmtcuv.vbs |
| 0d16de10ce708b990d1b0ae26ac12792c91864426c88a8c73a475f7f33db014b | Sha256 | XWorm |
| dea780f228acbd536b5cbb35efe1a41d18771f6ed987c9d19b175de44f1d566c 7860a6e7264839c59506d5d69e40311e0c1e6af11b2351ccffe8d9b09acde9a3 d815e32b7998d3927792e579d4ad8430792ca1043b3570f0ee73855529516d21 | Sha256 | ZIP files |
| 98fcabe279d4001b29949d980aa9ae8396b352ef7c4a90b9dbe07650a7d4b797 | Sha256 | Відомості про кредитора.dvs. lnk |
| hxxp://81.19.139[.]62/f8d79yuhjhlgdjlsjkf83da0pkg.zip hxxp://81.19.139[.]14/987yuhgzsd234dfwhjkaqppkg.zip hxxp://81.19.139[.]62/f8d79yuhjhlgdjlsjkf83da0sud/sud.exe hxxp://45.95.232[.]82/dfghujfdkg3fmsud/sud.exe |
URL | Malware download URL |
| 444986ba74685fde34afbbf6a6963c5f35f12a1a65a705e5184c545a18c080c6 | Sha256 | Pkg.zip |
| 7382cf09d04de58beeba4d71fec9777815924fe66849c89e4230b8f26bff2650 | Sha256 | VCL120.dll |
| b1355a4eef0c265a9d918cec16f7299f4acc51daf8e3d59ef445cb46914f48ff | Sha256 | sud.exe |
| dd8377e9c3620d0732bedecd0d219f77f7bcffbc49470a9b7ff22db33fe4a185 | Sha256 | XWorm |
| hxxp://185.216.68[.]142:9000/hooks/xxx?id=%computername% | URL | C&C |
| d938cb8accbc51046158350155f1af9248fc8459ef2b92be752b93dae77504a6 17dc38bd4e01496a91d82e6de763df6fd94c00eb1e90e0cccd7f07f84b549f43 e314b233b41a5688a4e43f876ccb10718351d3f396b4df623b4ebb0a093be7e0 |
Sha256 | LNK shortcut files |
References
- https://cyble.com/blog/evilcoder-project-selling-multiple-dangerous-tools-online/
- https://cert.gov.ua/article/6278521
- https://1275.ru/ioc/3249/uac-0184-apt-iocs/
- https://detect.fyi/messengers-and-dating-sites-new-methods-of-attacks-social-engineering-threats-c2db029e27ea
- https://blog.morphisec.com/unveiling-uac-0184-the-remcos-rat-steganography-saga
- https://www.rapid7.com/blog/post/2023/08/31/fake-update-utilizes-new-idat-loader-to-execute-stealc-and-lumma-infostealers/
如有侵权请联系:admin#unsafe.sh