fsmon is a FileSystem Monitor utility created by by Sergi Àlvarez at Nowsecure can run on Linux 2024-6-24 20:32:1 Author: www.mobile-hacker.com(查看原文) 阅读量:10 收藏
![]()
fsmon is a FileSystem Monitor utility created by by Sergi Àlvarez at Nowsecure can run on Linux, Android, iOS, FireFox OS, and OS X. It retrieves file system events from a specific directory and displays them in a colorful format or in JSON. You can filter the events happening from a specific program name directory or process ID (PID).
The primary benefit of fsmon is its ability to provide real-time monitoring of file system changes. This can be particularly useful in a variety of scenarios, such as:
- Security analysis: By monitoring filesystem events, you can detect potential security vulnerabilities, such as insecure storage.
- Malware analysis: Identify altered files, dropped payloads, created and removed files.
Quick benefits are summarized in the video below.
Using fsmon is possible by connecting a computer via ADB to non-rooted or rooted Android device and executing the binary. The result of file monitoring is then conveniently displayed on the computer’s screen. However, it can be run even without computer, by running it via any terminal application, such as Termux directly on the smartphone to monitor file system while on the go. I will show you few examples in the following sections. You can download compiled fsmon from GitHub or compile it yourself.
Non rooted Android
You can monitor file changes on external and shared storage using command:
fsmon /storage/emulated/0/
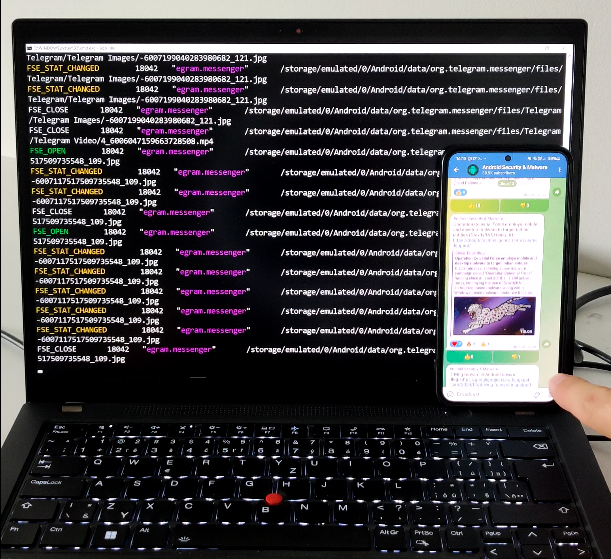
Using Termux app, you can in the background monitor file system directly on Android.

You can also monitor Android Wear file system on your smartwatches.

Rooted Android
With superuser rights, is file system monitoring is more useful since it allows to scan file changes for each app installed on device. This could be helpful for bug bounty hunters to identify access files by the app for insecure storage.
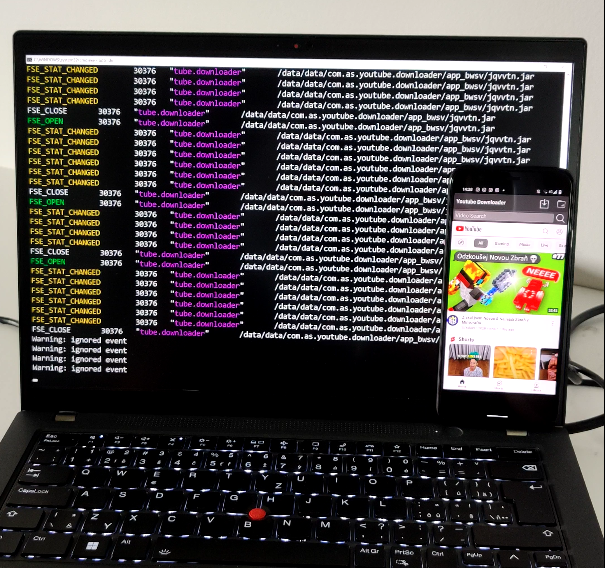
Malware researchers could identify dropped payloads, and files created or deleted by malware using
fsmon /data/data/com.as.youtube.downloader/ | egrep "\.dex|\.apk|\.jar|\.so"
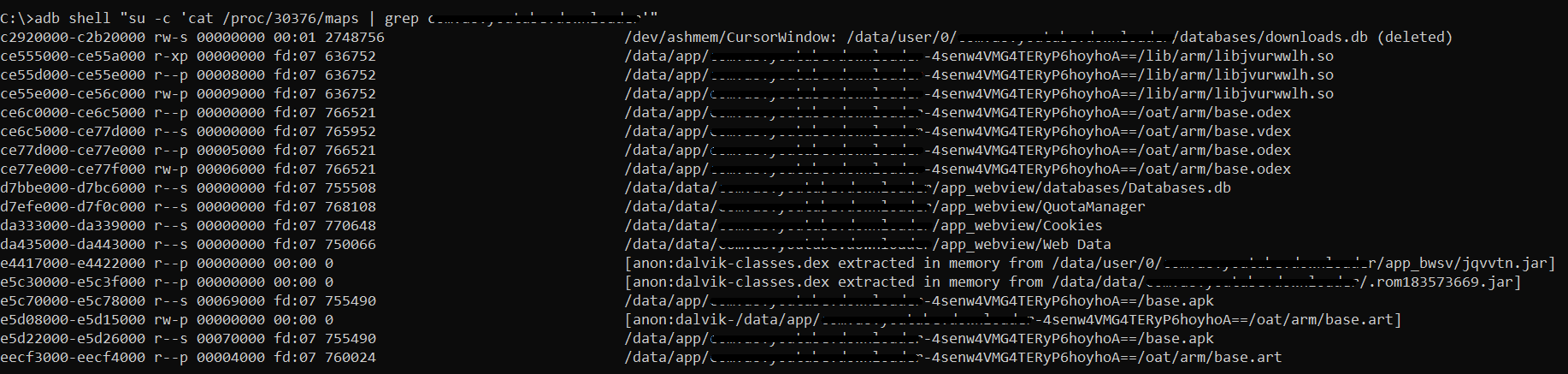
Benefit of fmon is that it can run on non-rooted Android system with real-time monitoring, however with obvious system defined limitations. The same result could be achieved using Frida toolkit, but only on rooted devices. If you are interested only in loaded binaries by specific Android app, it might be enough to just display process information, however you will lack information when each of loaded files were loaded and what operation was when executed, such as create, write, read or delete. Here is an example of a command to list loaded files by the process:
adb shell "su -c 'cat /proc/<PID>/maps | grep <package_name>'"
fsmon is a powerful tool for anyone interested in Android security. Its ability to monitor file system events in real-time can provide valuable insights into the workings of an application and help identify potential security vulnerabilities.
如有侵权请联系:admin#unsafe.sh