2024-6-17 20:44:34 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
With the continuously accelerating speed of application development, integrating DevSecOps automation and security into the development lifecycle has become more crucial than ever. DevSecOps, a framework that embeds security practices within the DevOps process, aims to address security vulnerabilities early on, aligning seamlessly with Agile methodologies and continuous integration/continuous deployment (CI/CD) pipelines. By doing so, it significantly reduces the risk of security issues reaching production, ensuring a more secure and efficient development process.
The Importance of SCA in CI Pipeline Security Integration
But how do you catch vulnerabilities early on? Waiting for software composition analysis (SCA) scans late in the deployment process increases the cycle time for vulnerability remediation. That’s too late. However, asking every developer to not only run SCA scans on their code before changes are made but to also understand the intricacies of vulnerability analysis is going to alienate most of that team. That’s too early. Integrating automated security testing within your CI/CD pipeline can provide early detection without burdening developers. That’s just right.
If we could somehow get the benefits of early scanning and vulnerability identification (shift left) while removing the burden from the development team, everyone wins.
I hope that by spending a few minutes with me, you’ll learn the following:
- The importance of early identification of vulnerabilities in your build process
- How to generate SBOMs (Software Bill of Materials) in your CI/CD pipeline
- Reasons why using a next-generation SCA tool to achieve these goals can lead to organizational and developer success
- How Deepfactor helps you achieve these benefits
Understanding Gating (or Blocking) Builds in Continuous Integration Security Practices
Blocking or gating builds that occur in your CI pipeline is not a new idea; builds are almost always blocked if they don’t compile due to errors, or timeout due to the inability to reach required build infrastructure. Now you can also elect to block builds that introduce vulnerable dependencies. This CI/CD security checkpoint provides an immediate failure mode, so developers learn immediately what dependency they introduced that potentially could lead to exploits if left in their change requests.
Understanding SBOMs and Their Importance in CI/CD Pipeline Vulnerability Scanning
As a product of their scans, next-generation SCA tools know about everything used to build an application. This list of components is called an SBOM and contains information about what dependencies your development team relies on to build your product. SBOMs are becoming “table stakes;” many companies now require SBOMs to be produced for every piece of software they purchase. In fact, the U.S. government now requires SBOMs to be provided for any software procured.
The great thing about using a next-generation SCA tool is that SBOMs can generally be created at build time “for free.” Since an SBOM is just a text document, these can be stored alongside build artifacts or published as needed.
You can learn more in the whitepaper—SBOM Security: Top 5 Reasons to Build SBOMs Into Your Pipeline.
Benefits of Integrating Security into CI/CD Processes
By now, hopefully, you’re convinced that integrating security into your CI/CD pipeline offers numerous benefits:
- Early Detection of Vulnerabilities: Identify and address security issues early in the development cycle, reducing the risk of vulnerabilities reaching production.
- Improved Mean Time To Resolution (MTTR): Quicker detection leads to faster resolution, minimizing the impact of security incidents and downtime.
- Regulatory Compliance: Ensure adherence to business-specific regulations (e.g., HIPAA, GDPR) through automated inspections and compliance checks within the pipeline.
- Audit Readiness: Maintain audit trails and evidence of security checks, demonstrating compliance and security during audits.
Integrating security into DevOps best practices ensures continuous security improvement.
Using Deepfactor in Your CI Pipeline
Our next-generation platform offers a robust solution to simplify the implementation of DevSecOps. By integrating Deepfactor into your existing CI/CD toolchain, application security, and engineering teams can efficiently identify and remediate security vulnerabilities during development and testing.
Here, I’ll explain how to integrate Deepfactor into your CI/CD pipeline, using Jenkins as an example.
Deepfactor’s command line tool dfctl facilitates seamless integration into the most common CI/CD pipelines. Available as part of the Deepfactor runtime container image, dfctl can be used even on ephemeral CI nodes where permanent installation might not be feasible. By integrating Deepfactor, you can:
- Generate an SBOM for your container images or source code.
- Perform vulnerability scans on container images or source code.
- Gate builds and pull requests based on SCA and SBOM alert policies.
- Track vulnerability trends across builds in the release cycle.
Example How-To: Integrating Deepfactor With Jenkins
Before you start, you’ll need:
- Docker-enabled CI/CD agent: Most CI/CD pipelines provide this
- Bind docker.sock to the Deepfactor scan container: This allows scanning of local images, achievable with the -v option of the Docker CLI:
-v /var/run/docker.sock:/var/run/docker.sock
Note: If you are using Jenkins within a Docker container, make sure to attach a file path to the Jenkins home directory by launching Jenkins with the following option:
--volume /var/jenkins_home:/var/jenkins_home
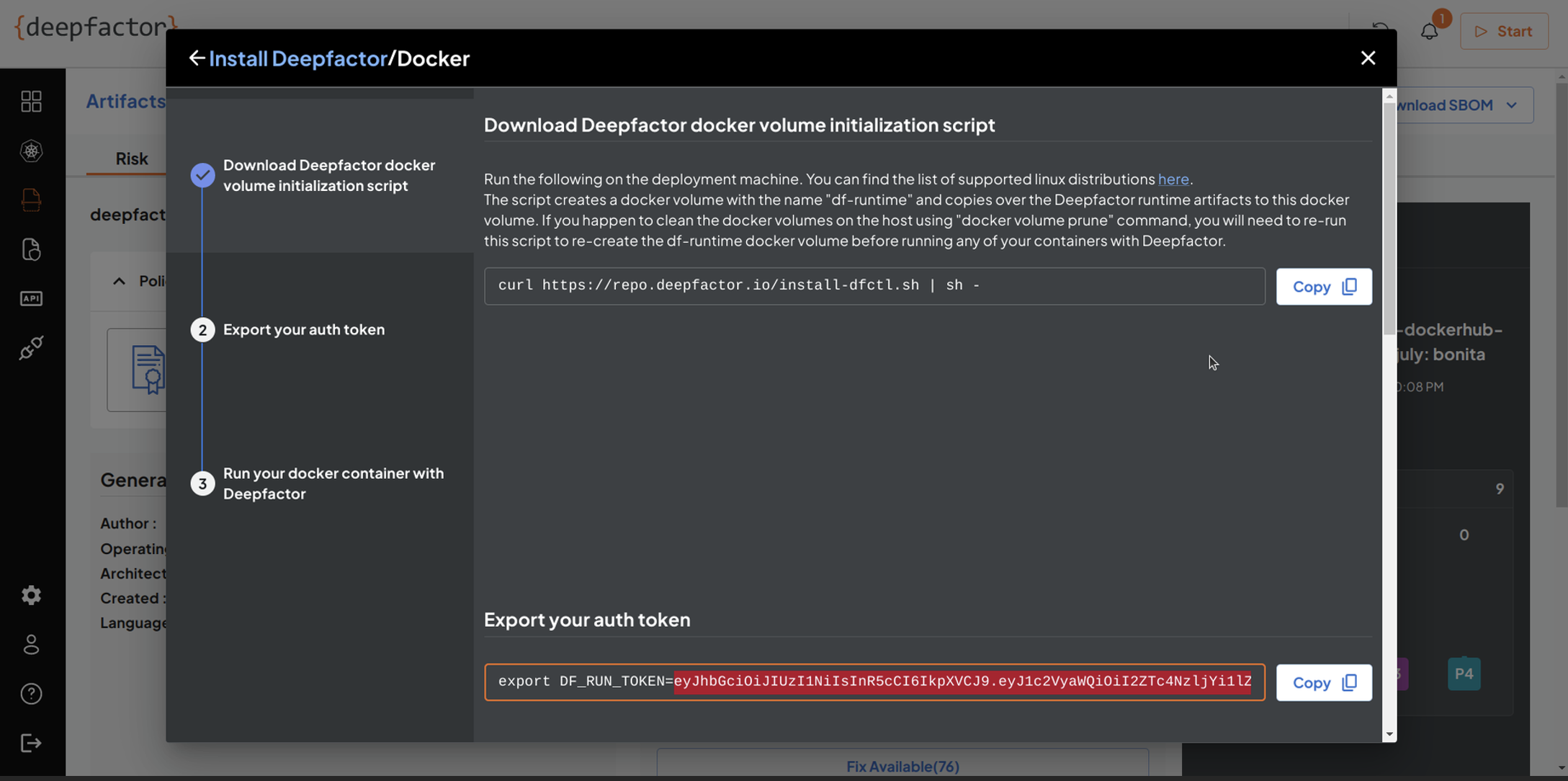
- Set up the Deepfactor portal and obtain the run token: Retrieve the Deepfactor run token from the portal UI and store it as a secret in your CI/CD tool.
- Download the Deepfactor Command Line Tool (dfctl): Execute the following command to install dfctl on your Jenkins server:
curl https://repo.deepfactor.io/install-dfctl.sh | sh --
How to Execute a Deepfactor Scan in the Jenkins Pipeline
This next section details the steps for executing a dfctl scan from the Jenkins pipeline.
Step 1: Securely Store the Deepfactor run token as a secret in Jenkins.
Begin by storing the Deepfactor run token as a secret in Jenkins. This ensures that sensitive information is protected and can be securely referenced in your pipeline.
From your Jenkins server UI:
- Navigate to Manage Jenkins > Manage Credentials.
- Go to System > Global credentials and click on Add Credentials.
- Select Kind as “Secret text” and set the scope as preferred.
- Enter the ID as DF_RUN_TOKEN and input the token obtained from the Deepfactor portal UI.
- Click on Create. Now we will be. able to reference the DF_RUN_TOKEN secret in our pipeline.
Step 2: Execute a Deepfactor Scan
With the token securely stored, you can now configure the Jenkins pipeline to perform a Deepfactor scan. Depending on how your build is created, you might choose any of the following scan scenarios:
- Scan a container image
- Scan a locally built container image
- Scan a container image and generate CycloneDX SBOM
- Scan source code
- Scan image and gate build
As an example, here’s a sample pipeline script for scanning a container image and producing a list of vulnerabilities for all builds performed using the pipeline. In this example, I’m just assuming the build output is placed into a container image named “node:alpine” but you’d change that to the name of your container image.
pipeline { // agent any // or an agent node agent any environment { // fetch run token from credentials DF_RUN_TOKEN=credentials('DF_RUN_TOKEN') } stages { stage('Deepfactor static scan') { steps { sh('docker run --pull=always --rm -e DF_RUN_TOKEN=$DF_RUN_TOKEN --network host -v /var/run/docker.sock:/var/run/docker.sock public.ecr.aws/deepfactor/df/runtime:latest dfctl scan node:alpine') } } } }
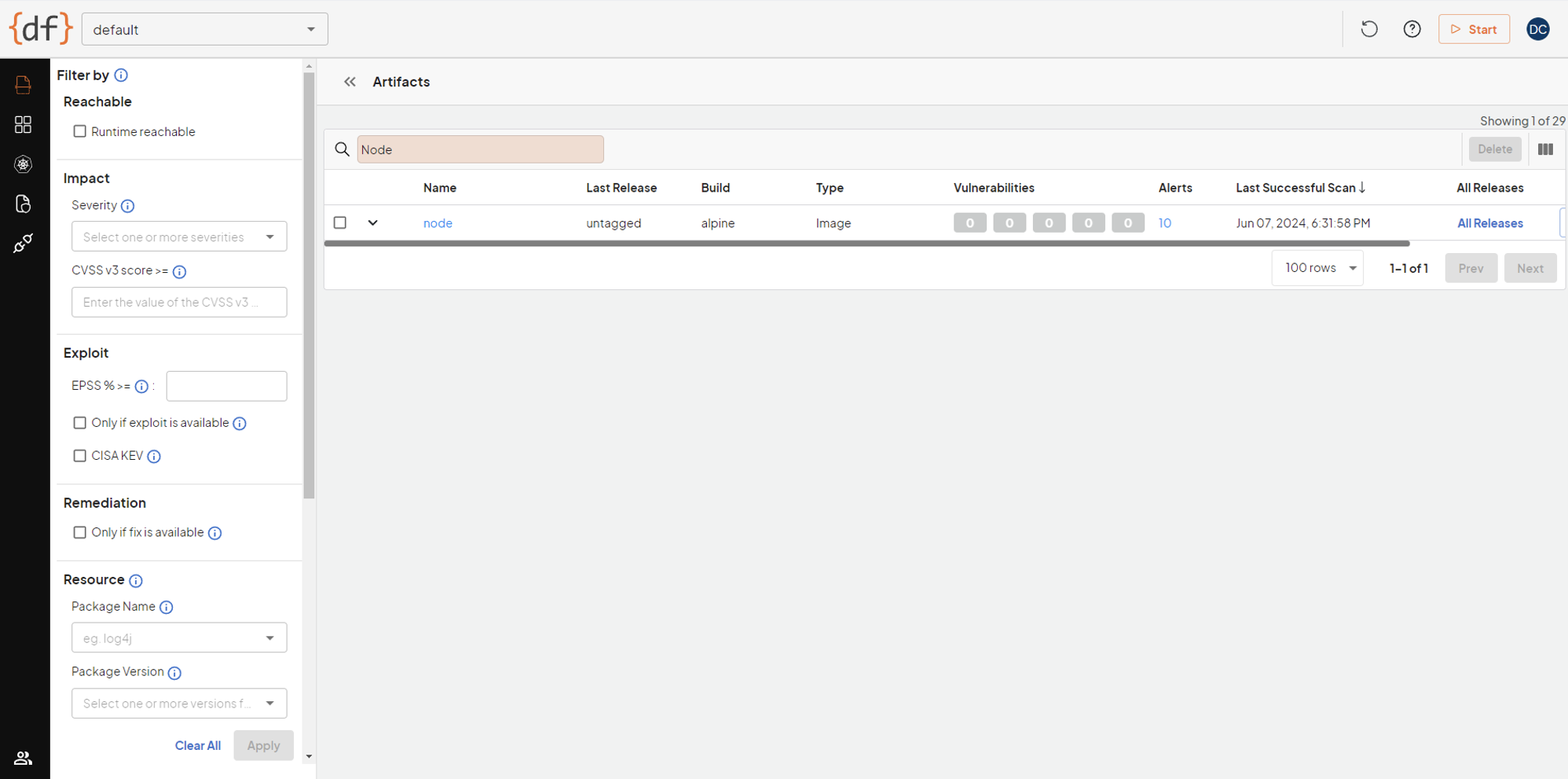
Ensure the Jenkins pipeline execution is successful and switch back to the Deepfactor portal UI to view the artifacts of your scan result.
For example, here we see the result of a build of the node:alpine container. We’re in good shape here, no vulnerabilities are reported (although 10 alerts have been produced; these may be related to end-of-life components or alerts that aren’t necessarily vulnerability-based).
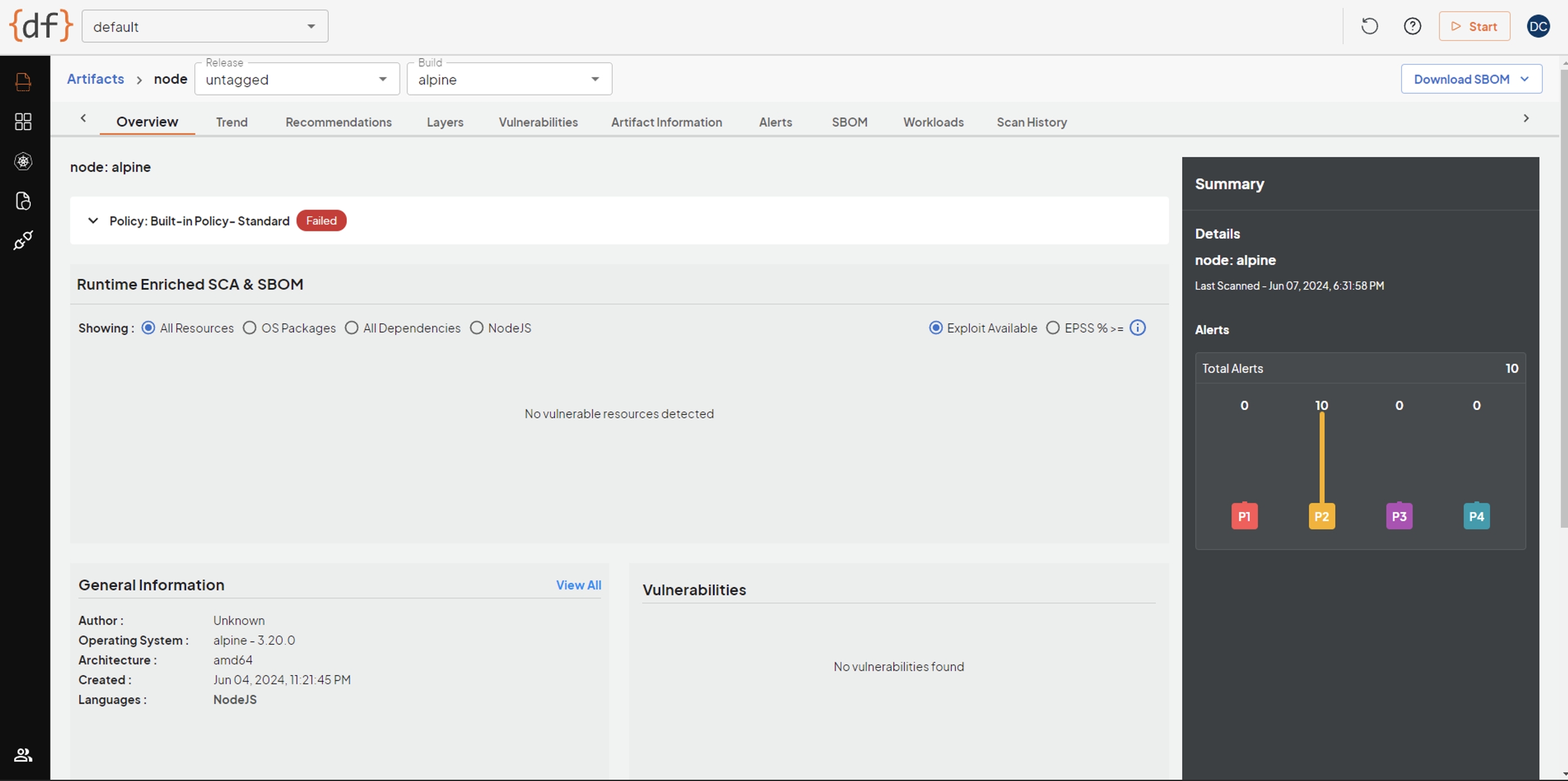
We can also drill down into the report to see more information about the scan results.
Ensuring Long-Term Successful Integration of SCA Tools
To ensure the long-term acceptance and benefits of tools like Deepfactor, I’d like to suggest some additional things you might consider:
- Educate and empower your team: Provide training and resources to help team members understand and implement Deepfactor effectively.
- Automate security checks: Use Deepfactor for automated vulnerability scanning, assessments, and compliance checks.
- Select appropriate KPIs: Define and track key performance indicators related to risk reduction, release velocity, and security culture.
- Establish a culture of security: Promote a security-first mindset across development and security teams.
- Monitor and improve: Continuously monitor your DevSecOps practices and adapt your approach based on feedback and evolving needs.
By following these guidelines, you can effectively integrate Deepfactor into your CI/CD pipeline, enhancing your application’s security posture and ensuring a more robust and secure development lifecycle. You should also check out the whitepaper—SCA 2.0: A Framework to Prioritize Risk, Reduce False Positives, and Eliminate SCA Alert Fatigue.
What Have We Learned?
A quick recap:
- Gating or blocking builds early if vulnerabilities are introduced is important
- Build time is a great time to create SBOMs if your organization is subject to compliance metrics
- Fostering a culture of security where checks are automated and easy to resolve is important (minimize work for developers)
- Deepfactor can help you achieve these goals with an easy-to-use command line tool that lets you seamlessly integrate into your CI pipeline.
FAQs
Q. How can Deepfactor be integrated into existing CI pipelines?
A. Deepfactor can be integrated into existing CI pipelines by using the dfctl command line tool, which facilitates seamless integration into most common CI/CD pipelines.
Q. What are the benefits of integrating security into CI/CD processes?
A. Integrating security into CI/CD processes offers early detection of vulnerabilities, improved mean time to resolution (MTTR), adherence to business-specific regulations, compliance auditing, and audit readiness with proof points.
Q: What steps should teams take to ensure successful integration of Deepfactor into their DevSecOps practices?
A. To ensure successful integration, teams should understand their current state, educate and empower team members, integrate security practices early, automate security checks, select appropriate KPIs, establish a culture of security, and continuously monitor and improve their DevSecOps practices.
The post Optimizing SCA Use in CI Pipelines for Advanced DevSecOps appeared first on Deepfactor.
*** This is a Security Bloggers Network syndicated blog from Deepfactor authored by Rajakumar Muthukumarasamy. Read the original post at: https://www.deepfactor.io/optimizing-sca-use-in-ci-pipelines-for-advanced-devsecops/
如有侵权请联系:admin#unsafe.sh