2024-6-14 23:16:22 Author: cyble.com(查看原文) 阅读量:29 收藏
Overview
On May 7, 2024, Devcore Principal Security Researcher Orange Tsai discovered and reported a critical Remote Code Execution (RCE) vulnerability, CVE-2024-4577, to the PHP official team. This vulnerability stems from errors in character encoding conversions, particularly affecting the “Best Fit” feature on Windows operating systems.
Exploiting this flaw could potentially enable threat actors (TAs) to remotely execute arbitrary code, posing significant security risks to PHP installations across all versions running on Windows platforms. Recognizing the severity of the issue, the PHP development team promptly addressed CVE-2024-4577 by releasing an official patch on June 6, 2024.”
On June 8th, cybersecurity researchers at Imperva reported the first instance of TAs exploiting this vulnerability. The TAs utilized the vulnerability to deploy ransomware on systems vulnerable to this issue. This malicious activity was identified as part of the ‘TellYouThePass’ ransomware campaign.
Amidst these findings, Cyble Global Sensor Intelligence (CGSI) detected multiple scanning attempts related to CVE-2024-4577 originating from various locations. Notably, one such attempt from IP address 51[.]79[.]19[.]53 is associated with the Muhstik malware campaign recently identified by Aqua Nautilus. The exploitation attempt from the IP address suggests a potential connection to the TAs who previously exploited RocketMQ vulnerability and may now be attempting to exploit CVE-2024-4577 for payload delivery.
Muhstik is recognized as a prominent threat that specifically targets IoT devices and Linux-based servers. It is notorious for its capability to infect devices and employ them for activities such as cryptocurrency mining and launching Distributed Denial of Service (DDoS) attacks.
Cyble Global Sensor Intelligence (CGSI) findings
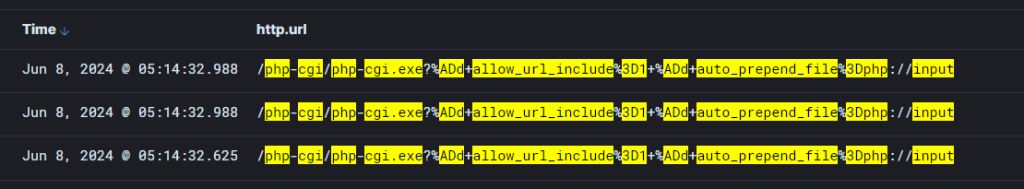
WatchTowr Labs published a proof-of-concept (PoC) exploit code for CVE-2024-4577 one day after the patch was released. On the subsequent day, Cyble Global Sensor Intelligence (CGSI) detected exploitation attempts targeting this vulnerability starting on June 8, 2024. The image below shows the attacks observed in CGSI.

Figure 1 – Exploitation attempt observed by CGSI network
Vulnerability Summary
Command injection vulnerability
CVE-2024-4577
CVSS:3.1:
9.8
Severity:
Critical
Vulnerable Versions:
The vulnerability impacts all PHP versions running in CGI (Common Gateway Interface) mode on the Windows operating system or exposing the PHP binary in the following versions:
- PHP 8.3 < 8.3.8
- PHP 8.2 < 8.2.20
- PHP 8.1 < 8.1.29
Description:
In PHP versions 8.1.* before 8.1.29, 8.2.* before 8.2.20, 8.3.* before 8.3.8, when using Apache and PHP-CGI on Windows, if the system is set up to use certain code pages, Windows may use “Best-Fit” behavior to replace characters in command line given to Win32 API functions. PHP CGI module may misinterpret those characters as PHP options, allowing a malicious user to pass options to the PHP binary being run and thus reveal the source code of scripts, running arbitrary PHP code on the server, etc.
Vulnerability Details
The vulnerability explicitly impacts PHP’s CGI mode, where the web server interprets HTTP requests and forwards them to a PHP script for processing. For instance, query strings are parsed and sent to the PHP interpreter via the command line, such as executing `php.exe cgi.php foo=bar` for a request like `http://host/cgi.php?foo=bar`.
If a character like a soft hyphen (0xAD) is used in a URL parameter, the CGI handler on Windows, following its Best Fit mapping, may interpret this character differently than intended.
Specifically, the soft hyphen, intended to be non-significant in many contexts, may be mapped to a regular hyphen (ASCII -).
PHP then interprets this as a regular hyphen in command-line arguments. This misinterpretation allows an attacker to execute arbitrary code on the vulnerable PHP server.
Below is the crafted HTTP POST request with 0xAD ‘soft hyphen’ instead of the usual hyphen:
- /cgi-bin/php-cgi.exe?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
- /php-cgi/php-cgi.exe?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
Conclusion
The exposure of potentially vulnerable PHP instances is alarmingly high, leading to an increased focus on this critical vulnerability. This heightened attention is evident from the TellYouThePass ransomware campaign, which swiftly exploited the vulnerability following the release of the PoC code.
In addition, CGSI detected exploitation attempts targeting CVE-2024-4577 associated with Muhstik malware, further underscoring the urgency and severity of this vulnerability. Organizations must prioritize immediate updates and mitigation strategies to protect their systems from these active and evolving exploit attempts.
Recommendations
- It is highly recommended to upgrade to the latest PHP versions: 8.3.8, 8.2.20, and 8.1.29.
- Regular Audits, Vulnerability, and Pentesting exercises are key in finding security loopholes that an attacker may exploit.
Indicators Of Compromise
| Indicators | Indicator Type | Description |
| 51[.]79[.]19[.]53 14[.]225[.]53[.]162 47[.]94[.]155[.]169 120[.]92[.]12[.]14 101[.]132[.]154[.]203 14[.]116[.]254[.]172 222[.]216[.]206[.]99 183[.]56[.]201[.]169 39[.]97[.]209[.]211 93[.]123[.]118[.]191 193[.]143[.]1[.]88 | IP | IP observed attempting to exploit CVE-2024-4577 |
References
https://nvd.nist.gov/vuln/detail/CVE-2024-4577https://devco.re/blog/2024/06/06/security-alert-cve-2024-4577-php-cgi-argument-injection-vulnerability-en/
https://www.imperva.com/blog/update-cve-2024-4577-quickly-weaponized-to-distribute-tellyouthepass-ransomware/
https://labs.watchtowr.com/no-way-php-strikes-again-cve-2024-4577
Related
如有侵权请联系:admin#unsafe.sh