
2024-6-13 21:57:32 Author: securityboulevard.com(查看原文) 阅读量:5 收藏
Many acronyms and security concepts come and go without much traction, but the term continuous threat exposure management (CTEM) seems to be taking hold for the foreseeable future. CTEM, a term originally coined by Gartner, offers a cyclical approach to finding and mitigating threat exposure—which is the accessibility and exploitability of digital and physical assets—in an ongoing, proactive, and prioritized way.
This iterative methodology equips security operations teams with the continuous coverage and actionable real-time insight needed to:
- Identify and correlate threats against the latest threat and vulnerability intelligence
- Prioritize risk and potential courses of action
- Pivot to predict and prevent exposure
- Accelerate detection and response
By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.
Gartner
Security spending is on the rise, but does your security posture reflect that? Our Skeptic’s Guide to Buying Security Tools is all about doing more with what you already have.
CTEM differs from other approaches in several ways. The most compelling of which is that many critical components of CTEM already exist within an organization’s security program, providing the potential for a cohesive approach that delivers the rare dual benefits of reducing risk while also reducing cost. CTEM also brings together multiple, individual security processes and capabilities in a way that allows enterprises to continually evaluate the accessibility and exploitability of their digital and physical assets.
This is particularly important now, as threat exposure is not only changing constantly, but faster than ever, driven by strategic business initiatives like mergers and acquisitions (M&A); remote and hybrid work; unpredictable world events; ongoing digitalization/cloud migration, and aI-powered cyber attacks.
The first blog in our CTEM series explored basic concepts about the program, including an overview of its phases, related technologies, and potential benefits.
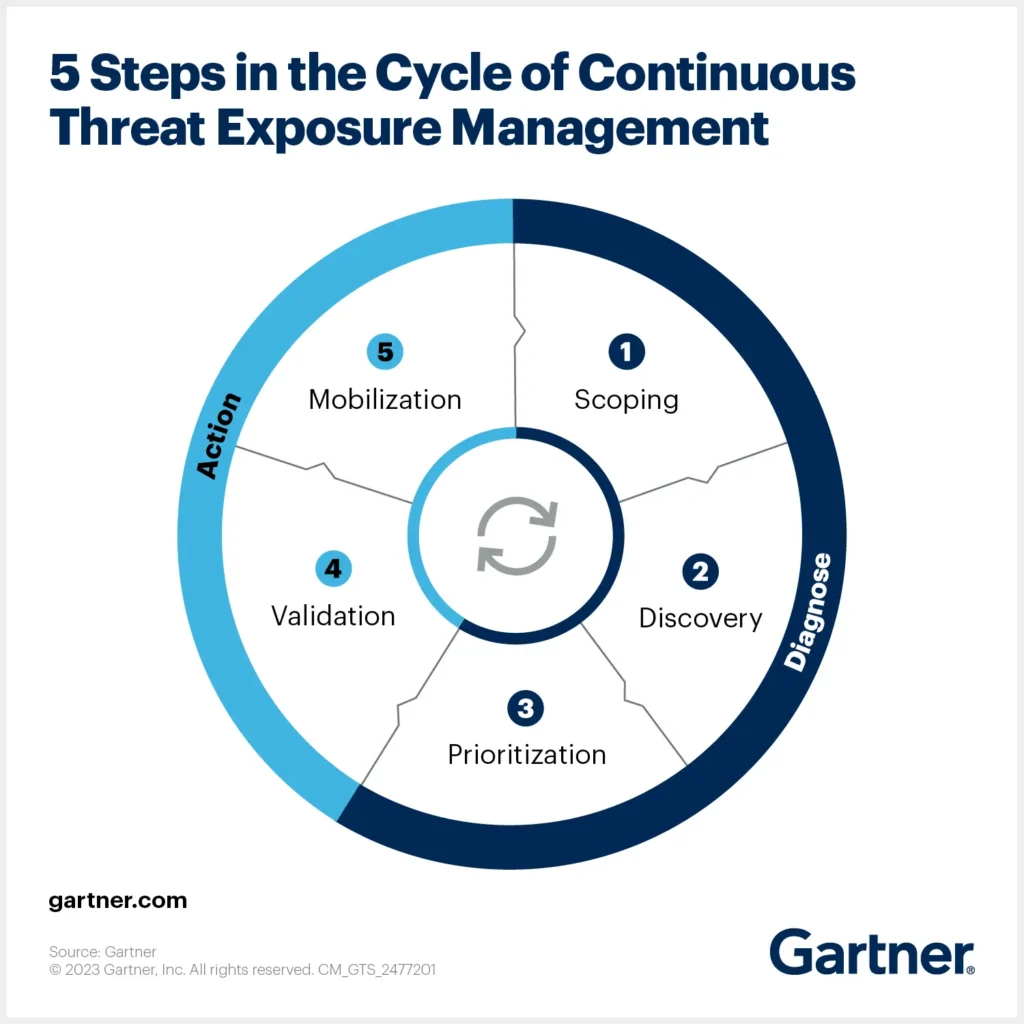
Here in blog two, we’ll take a closer look specifically at the validation phase of the process and discuss how breach and attack simulation (BAS) delivers the scalable, repeatable, automated, and continuous testing needed to keep the whole cycle flowing.
The Role of Continuous Validation in CTEM
The key emphasis in the CTEM model is on the “continuous” aspect. And how do you continuously ensure that all your deployed threat detection and response processes are doing their job? By continuously validating them to:
- Track your security posture against consistent threat scenarios and help you identify drift, manage your exposure, and stay ahead of your adversary.
- Track the performance of deployed detection controls and processes to ensure that your defenders can rely on accurate data to perform the necessary remediation actions and protect the organization.
- Verify that any deployed mitigation/remediation does NOT affect the operations of the organization and was effective in driving down risk and improving overall security efficacy.
- Validate your security posture against previously known and newly discovered threats.
There are a number of security validation methods available today, but each has different use cases and functions. Find the optimal solution for your org with our guide: Six Methods to Test Your Organization’s Resilience.
The Advantages of BAS For Continuous Validation
Security leaders must increasingly justify and demonstrate the value of security investments to stakeholders. Only reliable, repeatable testing and validation can produce the meaningful before-and-after comparisons needed to quantify benefits and declare projects successful.
As the CTEM cycle revolves, BAS operates within the validation phase to uniquely deliver actionable insight around both the likelihood of attack and the ability of your security controls to block and shut down threats.
During a BAS exercise, an organization’s security experts emulate and execute attack cycles against the company’s own network employing the same tactics, techniques, and procedures (TTPs) threat actors use to target high-profile assets. Attacks might recreate specific threats and weaknesses—any combination of vulnerabilities, misconfigurations, and user behaviors that could put critical assets at risk—or particular types of attacks such as phishing, malware/ransomware campaigns, exploitation of known vulnerabilities, and data exfiltration.
BAS lets analysts measure and evaluate how well security controls and personnel perform as they detect, investigate, and mitigate attacks. Doing so illuminates areas that warrant further investment or need improvement. Simulations may extend to include ecosystem partners, vendors, and customers that play an active role in defending crown-jewel assets and integrated IT systems.
BAS tools offer several unique advantages over other security validation tools and manual approaches when it comes to continuous validation. With a BAS tool you can:
- Regularly and continuously challenge all your deployed security controls by validating their performance and effectiveness against known and newly discovered threats.
- Better prioritization of threats based on their overall impact to the organizational security posture.
- Effectively monitor, measure, and communicate organizational security posture to key technical and non-technical stakeholders, allowing them to make data-driven decisions about business and security spend.
- Ability to automate continuous testing against threats to ensure an optimal remediation process.
Continuous Validation Use Cases within CTEM
Continuous validation enables evidence- and risk-based decision-making, prioritization, and investment. An integral element of CTEM, BAS helps to assess risk and prepare for attacks ahead of time so you can:
Global online money transfer company PayPal partners with SafeBreach to make risk assessment decisions quickly and accurately to support the company’s robust M&A activity.
Fast-track strategic business initiatives
Mergers, acquisitions, and other organizational changes bring rapid, pronounced change to your digital attack surface—a beacon to opportunistic hackers. Ongoing CTEM validation lets IT predict how imminent changes may impact the availability of applications, security resilience, and cyber skills shortages. Good examples of CTEM use cases include allowing organizational changes and newsworthy attack techniques to trigger new cycles at any time (and any stage of the process).
Finish securing remote work
As organizations continue to declare remote work permanent, temporary exceptions also must become permanent changes to corporate access policies. BAS helps to define new security workflows by allowing analysts to simulate remote and cloud-based attacks on VPNs, public cloud services, authentication, and other resources exposed by hybrid work and shared access.
Keep time on defenders’ side
BAS exercises help improve two pivotal time-based security metrics: mean time to detect (MTTD) and mean time to respond (MTTR). Running simulated attacks on an automated or regular basis helps teams continually optimize monitoring and detection tool configurations and investigation workflows.
Mitigate third-party risk
Defenders’ responsibility for remediation now routinely extends beyond the security team’s traditional reach. As an example, increased integration with third parties creates serious gaps in visibility and exploitable blind spots between controls.
Along with vulnerabilities, shared attack surfaces include new vectors for exposure from social media platforms, open-source development code repositories, and shadow IT.
As the sheer volume of unpatched vulnerabilities grows, managing joint threat exposure requires more than applying software updates remotely, virtually, or automatically. BAS lets defenders model initial access and lateral movement involving many threat vectors and TTPs. BAS also promotes collaborating with other teams, cloud providers, and ecosystem partners to model attacks and lateral movement across mutual attack surfaces. The advanced automation and easy integrations enabled by BAS add tremendous value to collaborative efforts such as these.
Through 2026, non-patchable attack surfaces will grow from less than 10% to more than half of the enterprise’s total exposure, reducing the remediation practices.
– Gartner
Streamline Governance Risk & Compliance
A CTEM program aligns with your governance, risk and compliance (GRC) practice to inform shifts in long-term strategies. Ongoing validation using BAS helps GRC leaders demonstrate compliance and maintain clear audit trails, which in turn may positively impact cyber insurance premiums.
Validate controls
Frequent updates to software and systems lead to configuration drift that promotes errors and gaps in controls. Running regular BAS exercises to see that current security controls are—and stay—correctly configured helps ensure readiness to detect and block attacks.
Stop phishing and ransomware
Simulating phishing campaigns and other attacks on authentication helps IT professionals gauge whether employees can recognize and resist phishing scams. Testing also validates the effectiveness of investments in training programs and multi-factor authentication (MFA).
Automate validation
Gartner warns that mature organizations may have reached the limits of “automated remediation.” Machine learning (ML) promises to fully automate incident (IR)—someday. But right now, the best use of automation may be making analyst workflows smarter and your team’s job easier, rather than fully automate the job itself.
BAS helps to automate the validation of successful mobilization efforts–the final phase of the CTEM cycle–to demonstrate the value of automation tools and controls.
Through 2025, organizations that implement cross-team mobilization as part of their exposure management programs will gain 50% more security optimization than those only prioritizing automated remediation
– Gartner
The CTEM model offers tremendous benefits to any organization implementing it. However, given how new the model is, a practical implementation can be fraught with several challenges. Many of these challenges can be mitigated by selecting the right validation tools. Check back for our final blog in the series as we dive into the different tools and techniques that can support continuous validation, including BAS, penetration testing (pen testing), pen testing as a service (PTaaS), automated pen testing, red team exercises, and digital risk protection services (DRPS).
Ready to learn more about how BAS can play an important role in your CTEM program now? Check out our CTEM resource hub or connect with a SafeBreach cybersecurity expert today.
You Might Also Be Interested In
Get the latest
research and news
The post The Road to CTEM, Part 2: The Role of Continuous Validation appeared first on SafeBreach.
*** This is a Security Bloggers Network syndicated blog from SafeBreach authored by SafeBreach. Read the original post at: https://www.safebreach.com/blog/ctem-continuous-validation/
如有侵权请联系:admin#unsafe.sh