
2024-6-6 22:50:53 Author: securityboulevard.com(查看原文) 阅读量:0 收藏
TL;DR: Using Ludus as the backend, and with the help of Erik at Bad Sector Labs, I present a fully customizable SCCM deployment you can integrate into your home lab. https://github.com/Synzack/ludus_sccm

Intro
The past couple of years have been an exciting time in Microsoft Endpoint Configuration Manager (formerly System Center Configuration Manager [SCCM]) tradecraft. I’ve read too many SCCM blogs to mention here and I have had the personal privilege to be coworkers with researchers such as Garrett Foster, Duane Michael, Chris Thompson, and Ryan Cobb and see their work firsthand.
As exciting as SCCM is, it was always a little intimidating to try to recreate the research being published. The first time I made an SCCM lab, it took hours of creating virtual machines (VMs) by hand, configuring the domain, reading SCCM configuration blogs, and several long calls with Garrett to understand why my pre-reqs were still failing.
Due to this barrier of entry, most of my SCCM hands-on training came on the job in actual production environments, with one of our researchers guiding the steps and testing scenarios in their research lab; assuming it had the same configuration. Speaking with other colleagues in the industry, they faced similar challenges. They would see SCCM on a real world engagement, but lacked the experience to confidently probe for vulnerabilities without fear of breaking something. In comes the need for a testing lab…but where?
During this time, there were limited resources for pre-built labs. There was a Snap Labs template by @an0n (https://twitter.com/an0n_r0/status/1687230842601451522) that was great, but I desired something that could be used in my local bare-metal lab.
Another option was Microsoft’s evaluation lab (https://learn.microsoft.com/en-us/mem/configmgr/core/get-started/set-up-your-lab), but it couldn’t be easily integrated into my existing lab and domain.
I began looking into ways to create my own lab. I tried migrating to Proxmox from ESXi (for the free API) and using tools like Packer, Ansible, and Terraform. This proved very time consuming and hard to scale as I am not a DevOps engineer. I had put the project on the back-burner until I came across a tweet that changed everything (https://twitter.com/badsectorlabs/status/1754909113090269474).
As of March 23, 2024, SCCM was added to the GOAD project (https://twitter.com/M4yFly/status/1771643303164891262). This looks like a fantastic resource, especially if you want a pre-configured lab, ready to go.
Ludus

Erik Hunstad, the founder of Bad Sector Labs, created Ludus and shared the same sentiments I did when it came to labs: advanced and easily deployable cyber ranges designed for testers and researchers alike. Ludus is built on top of Proxmox, has built-in networking, does all of the backend VM configuration for me, and uses easy to install templates for all the configuration. No longer did I need to worry about trying to create back end infrastructure; all I needed to do was focus on creating Ansible roles on my new pre-configured hosts.
And the best part? Ludus is FULLY customizable. I could recreate my home lab using my domain name, my usernames, and install any features I wanted à la carte. This is something I found wanting in other publicly available labs. They contained amazing content, but I always felt like I was using someone else’s lab and had to learn their naming conventions and structures.
The Lab
As soon as I found Ludus, I hit the ground running to build a fully customizable SCCM lab I could use for practice and research purposes. I had the pleasure of working with Erik directly as a resource to bounce ideas off of and improve my Ansible tradecraft. While there is still work to do and features to add, I wanted to provide this lab as a template for everyone in the field who is looking for the same features I was.
Check it out here: https://github.com/Synzack/ludus_sccm
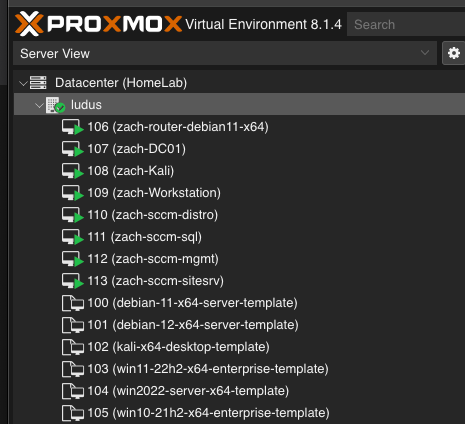
I would give you a network diagram, but since the network is whatever you want it to be, it’s up to your imagination!

- Domain Controller
- Workstation
- Distribution Point
- Management Point
- Site Database
- Site Server
Installation
I won’t be covering the actual Ludus installation, as Erik already created fantastic documentation on https://ludus.cloud/. Installation is easy and only requires a few commands. After you have successfully installed Ludus and its server templates, you are ready to deploy your very own SCCM lab.
The actual roles and features can be installed directly from Ansible Galaxy with one command:
ludus ansible collection add synzack.ludus_sccm
That’s it!
After that, the entire configuration is handled in a single YAML file included in sccm-range-config.yml. Nearly everything in this file is configurable. Below is an example of a host configuration:
- vm_name: "{{ range_id }}-sccm-sitesrv"
hostname: "sccm-sitesrv"
template: win2022-server-x64-template
vlan: 10
ip_last_octet: 15
ram_gb: 8
cpus: 4
windows:
sysprep: true
domain:
fqdn: contoso.local
role: member
roles:
- synzack.ludus_sccm.enable_webdav
- synzack.ludus_sccm.ludus_sccm_siteserver
role_vars:
ludus_sccm_sitecode: 123
ludus_sccm_sitename: Primary Site
ludus_sccm_site_server_hostname: 'sccm-sitesrv'
ludus_sccm_distro_server_hostname: 'sccm-distro'
ludus_sccm_mgmt_server_hostname: 'sccm-mgmt'
ludus_sccm_sql_server_hostname: 'sccm-sql'
# --------------------------NAA Account-------------------------------------------------
ludus_sccm_configure_nna: true
ludus_sccm_nna_username: 'sccm_naa'
ludus_sccm_nna_password: 'Password123'
# --------------------------Client Push Account-----------------------------------------
ludus_sccm_configure_client_push: true
ludus_sccm_client_push_username: 'sccm_push'
ludus_sccm_client_push_password: 'Password123'
ludus_sccm_enable_automatic_client_push_installation: true
ludus_sccm_enable_system_type_configuration_manager: true
ludus_sccm_enable_system_type_server: true
ludus_sccm_enable_system_type_workstation: true
ludus_sccm_install_client_to_domain_controller: false
ludus_sccm_allow_NTLM_fallback: true
# ---------------------------Discovery Methods------------------------------------------
ludus_sccm_enable_active_directory_forest_discovery: true
ludus_sccm_enable_active_directory_boundary_creation: true
ludus_sccm_enable_subnet_boundary_creation: true
ludus_sccm_enable_active_directory_group_discovery: true
ludus_sccm_enable_active_directory_system_discovery: true
ludus_sccm_enable_active_directory_user_discovery: true
# ----------------------------------PXE-------------------------------------------------
ludus_sccm_enable_pxe: true
ludus_enable_pxe_password: yes
ludus_pxe_password: 'Password123'
ludus_domain_join_account: domainadmin
ludus_domain_join_password: 'password'
Once you have your lab configured to your liking, it is just two more commands to kick off the installation:
ludus range config set -f sccm-range-config.yml
ludus range deploy
Role Configuration Details
This lab, and Ludus in general, are built on top of Ansible roles, which are a way to organize tasks, variables, files, and other resources. They can be thought of as a specific set of instructions to configure each individual server role. This SCCM lab contains seven roles:
1) disable_firewall
Disable firewall is simply used to disable the Windows firewall on any host configured with the role. By default, all SCCM hosts will disable the firewall within their individual roles. In the default configuration, this role is only needed to be applied to the domain controller and workstation role.
Role variables: none
2) install_adcs
Install AD CS is for installing Active Directory Certificate Services (AD CS) and a Certificate Authority (CA) on the DC. Specifically, this is used to enable LDAPS on the DC.
Required Role variables: none
Misconfiguration Manager Prereq For:
- Takeover 8 — Hierarchy takeover via NTLM coercion and relay HTTP to LDAP on domain controller
3) enable_webdav
Enable WebDAV is for installing the WebClient service on the specified host. It also configured the installed service to run automatically.
Required Role variables: none
Misconfiguration Manager Prereq For:
- Takeover 8 — Hierarchy takeover via NTLM coercion and relay HTTP to LDAP on domain controller
4 ) ludus_sccm_distro
This role is for configuring the SCCM Distribution Point Role. It will automatically install all Windows features needed for its role in SCCM, disable the firewall, and add the Site Server machine account as a local admin.
Required Role variables:
- ludus_sccm_site_server_hostname
5) ludus_sccm_mgmt
This role is for configuring the SCCM Management Point Role. It will automatically install all Windows features needed for its role in SCCM, disable the firewall, and add the Site Server machine account as a local admin.
Required Role variables:
- ludus_sccm_site_server_hostname
6 ) ludus_sccm_sql
This role is for configuring the SCCM Site Database Role. It will automatically install all Windows features needed for its role in SCCM, disable the firewall, and add the Site Server machine account as a local admin. Additionally, it will create your designated SQL service account within Active Directory, configure it as an SQL administrator account, and install SQL Server 2022.
Role variables:
- ludus_sccm_site_server_hostname
- ludus_sccm_sql_server_hostname
- ludus_sccm_sql_svc_account_username
- ludus_sccm_sql_svc_account_password
7) ludus_sccm_siteserver
This is the most important and complicated role within this lab. This role installs the SCCM Site Server. It will automatically install all Windows features needed for its role in SCCM, disable the firewall, and configure the actual SCCM service.
Required Role Variables:
- ludus_sccm_sitecode
- ludus_sccm_sitename
- ludus_sccm_site_server_hostname
- ludus_sccm_distro_server_hostname
- ludus_sccm_mgmt_server_hostname
- ludus_sccm_sql_server_hostname
In addition to the required variables, there are also optional variables that can be configured to enable features within SCCM. Please see the next section for more details.
Site Server Configuration Details
NAA Accounts
To configure network access accounts (NAAs), there are three role variables under the synzack.ludus_sccm.ludus_sccm_siteserver role.
Variables:
- ludus_sccm_configure_naa
- ludus_sccm_naa_username
- ludus_sccm_naa_password
To enable an NAA account within your lab, simply set “ludus_sccm_configure_nna” to “true” and provide a username and password for your account. This account will automatically be created within the Active Directory domain and added to your SCCM installation as a user with the NAA role.
Misconfiguration Manager features enabled by this configuration:
- Cred 2 — Request computer policy and deobfuscate secrets
- Cred 3 — Dump currently deployed secrets via WMI
- Cred 4 — Retrieve legacy secrets from the CIM repository
- Cred 5 — Dump credentials from the site database
Client Push Account
To enable client push accounts within your lab, set “ludus_sccm_configure_client_push” to “true” and define your client push account username and password. Similar to the NAA implementation, the account will automatically be created within Active Directory and added to your SCCM installation. The latter variables will allow you granular control over the client push installation settings themselves. This role will automatically install SCCM on your domain hosts if you configure it to.
ludus_sccm_enable_automatic_client_push_installation
- This variable sets whether client push will automatically install the SCCM client on discovered computers
ludus_sccm_enable_system_type_configuration_manager
- This variable sets whether client push will automatically install the SCCM client on SCCM site system roles
ludus_sccm_enable_system_type_server
- This variable sets whether client push will automatically install the SCCM client on discovered hosts of type “server”
ludus_sccm_enable_system_type_workstation
- This variable sets whether client push will automatically install the SCCM client on discovered hosts of type “workstation”
ludus_sccm_install_client_to_domain_controller
- This variable sets whether client push will automatically install the SCCM client on discovered hosts of type “domain controller”
ludus_sccm_allow_NTLM_fallback
- If this variable is set to “true” and the site can’t use Kerberos to authenticate the client, it uses NTLM to retry the connection
- This enables NTLM relay attack opportunities
Discovery Methods
To configure the discovery methods your SCCM installation implemented, you can modify the following variables:
ludus_sccm_enable_active_directory_forest_discovery
- If set to “true”, SCCM will discover security groups, including local, global, and universal groups from specified locations in Active Directory Domain Services (AD DS)
ludus_sccm_enable_active_directory_boundary_creation
- If set to “true”, SCCM will create Active Directory boundaries from AD DS discovery information
ludus_sccm_enable_subnet_boundary_creation
- If set to “true”, SCCM will create IP address range boundaries from AD DS discovery information
ludus_sccm_enable_active_directory_group_discovery
- If set to “true”, SCCM will discover additional information, including the computer organizational unit (OU) and group membership, about previously discovered computers from specified locations in AD DS
ludus_sccm_enable_active_directory_system_discovery
- If set to “true”, SCCM will discover computers from specified locations in AD DS
ludus_sccm_enable_active_directory_user_discovery
- If set to “true”, SCCM will discover users from specified locations in AD DS
PXE
To configure the Preboot Execution Environment (PXE), you can modify the following variables:
ludus_sccm_enable_pxe
- If set to “true”, PXE will be enabled
ludus_enable_pxe_password
- If set to “true” PXE will require a password
ludus_pxe_password
- Sets what the password will be if enabled
ludus_domain_join_account
- Specifies which domain account will be used to join devices to the domain in PXE. This account must already exist
ludus_domain_join_password
- Specifies the password of the domain join account
Misconfiguration Manager features enabled by this configuration:
- Cred 1 — Retrieve secrets from PXE boot media
Complete List of Misconfiguration Manager Features Included
Recon
- Recon 1 — Enumerate SCCM Site Information via LDAP
- Recon 2 — Enumerate SCCM roles via SMB
- Recon 3 — Enumerate SCCM roles via HTTP
- Recon 4 — Query client devices via CMPivot
- Recon 5 — Locate users via SMS Provider
Cred
- Cred 1 — Retrieve secrets from PXE boot media
- Cred 2 — Request computer policy and deobfuscate secrets
- Cred 3 — Dump currently deployed secrets via WMI
- Cred 4 — Retrieve legacy secrets from the CIM repository
- Cred 5 — Dump credentials from the site database
Elevate
- Elevate 1 — NTLM relay site server to SMB on site systems
- Elevate 2 — NTLM relay via automatic client push installation
Exec
Takeover
- Takeover 1 — Hierarchy takeover via NTLM coercion and relay to MSSQL on remote site database
- Takeover 2 — Hierarchy takeover via NTLM coercion and relay to SMB on remote site database
- Takeover 8 — Hierarchy takeover via NTLM coercion and relay HTTP to LDAP on domain controller
Configurable Features
Using the available Ludus AD CS roles, you can integrate AD CS into your lab to perform:
- Takeover 3 — Relay to AD CS
Closing Thoughts and Future Goals
There are more features to SCCM than are represented in this current lab, but I hope that it can be a starting point for those looking for a lab solution type like I was. I plan on adding more features as it progresses (such as standalone SMS roles and other Misconfiguration Manager attack techniques) and I invite anyone to make updates and add additional features if you feel inclined. I believe that home labs are one of the best tools we can use as researchers and testers alike.
Be sure to check out Ludus and give a follow to Bad Sector Labs on X. Erik is truly passionate about this project and he has many more roles on GitHub you can integrate into your lab.
Also, be sure to read the corresponding Misconfiguration Manager blog: Misconfiguration Manager: Overlooked and Overprivileged by Duane Michael, Garrett Foster, and Chris Thompson. The entire repository can be found at https://misconfigurationmanager.com.
And a special thanks to Ryan Cobb for inspiration to make this lab and showing me some ansible techniques.
Please reach out to me on X or BloodHound Slack with any questions or feedback!
Zach Stein — X, GitHub, @Zach Stein on BloodHound Slack
Automating SCCM with Ludus: A Configuration Manager for Your Configuration Manager was originally published in Posts By SpecterOps Team Members on Medium, where people are continuing the conversation by highlighting and responding to this story.
*** This is a Security Bloggers Network syndicated blog from Posts By SpecterOps Team Members - Medium authored by Zach Stein. Read the original post at: https://posts.specterops.io/automating-sccm-with-ludus-a-configuration-manager-for-your-configuration-manager-c8f4d8e40473?source=rss----f05f8696e3cc---4
如有侵权请联系:admin#unsafe.sh