2024-6-4 01:8:2 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
The State of Healthcare Cybersecurity
While cybersecurity has always been a priority for healthcare organizations, the last few years have been different. Even as healthcare security teams make tremendous strides with their security capabilities and maturity, the industry is still greeted with daily headlines about ransomware attacks, unintentional exposure of protected health information (PHI), and other incidents that directly impact patient privacy and quality of care.
And increasingly, we’re seeing that the interconnected nature of modern healthcare, while beneficial in many ways, also creates the potential for cascading impacts throughout the industry when security incidents occur. There’s no better example of this than the February 2024 ransomware attack against UnitedHealth Group’s Change Healthcare unit, which disrupted the operations of pharmacies throughout the U.S. and caused ongoing fallout for months. In a May 2024 hearing before the U.S. House Energy and Commerce Committee, UnitedHealth Group CEO Andrew Witty estimated that this single incident will impact approximately one-third of all Americans.[1]
The February 2024 ransomware attack against Change Healthcare will impact an estimated one-third of Americans.
Cybersecurity Issues in Healthcare
There are many reasons that threat actors have been able to cause harm to healthcare organizations so regularly, but there is one major theme appears repeatedly: complexity.
Healthcare security teams must continually juggle:
- A patchwork of legacy security tools that don’t scale well or adapt to the needs of modern cloud architecture
- Resource constraints and issues like alert fatigue that can make it easy to fall into reactive mode
- Demanding compliance requirements that put additional strain on IT and security resources
- The need for security strategies that apply to both IT systems and the specialized OT devices used in the healthcare setting
- The complex challenge of securing healthcare-specific applications, which may have unique characteristics and/or run on legacy platforms that are difficult to secure
Healthcare Cybercrime: Threat Actors’ Motivates and Tactics
Another factor that adds complexity to healthcare security is the diverse set of threat actor profiles and tactics involved. For example, threats against healthcare organizations may originate from diverse sources such as:
- Cybercriminals, including malicious insiders in some instances, who are motivated by personal or financial gain
- Hacktivists seeking to destabilize the healthcare system to attract attention to or otherwise advance a particular cause
- Cyberterrorists or nation-state actors targeting critical healthcare facilities to cause harm to perceived adversaries
These threat actors have an ever-growing set of tools and tactics at their disposal, making attacks easier to execute than ever – and increasingly difficult to defend against.
Some of these are large-scale attack tools, such as botnets, that can be used to deliver ransomware or execute distributed denial of service (DDoS) attacks. And even relatively unsophisticated threat actors can access potentially devastating attack resources under arrangements such as ransomware-as-a-service or by buying or freely downloading turn-key tools from popular forums.
In other cases, attacks may be more precisely tailored toward very specific goals and points of vulnerability in the healthcare setting. For example, threat actors often employ techniques such as social engineering or business email compromise to trick or coerce healthcare employees into taking specific unsafe or damaging actions.
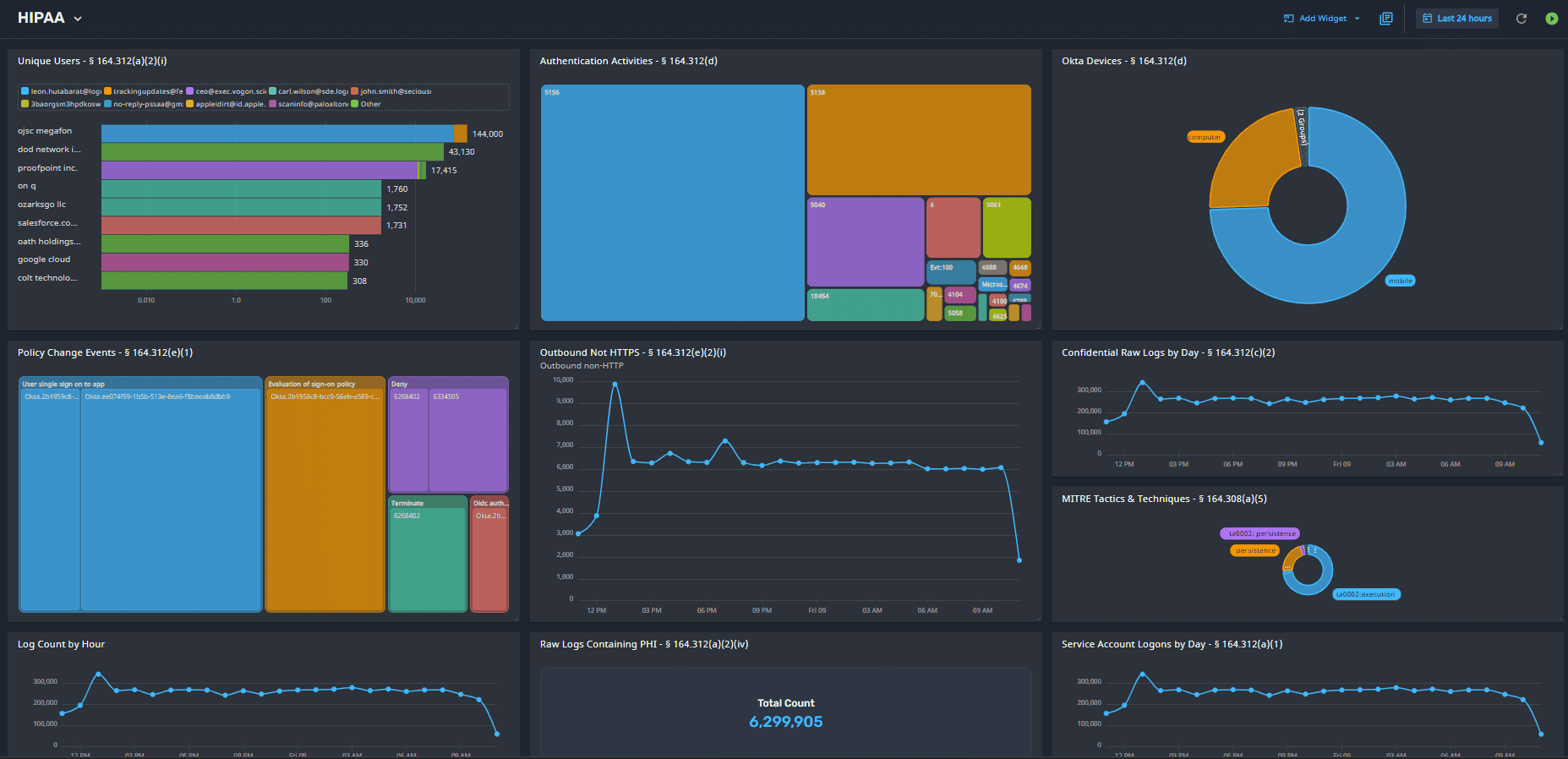
LogRhythm Axon Simplifies Healthcare Security
LogRhythm Axon, our cloud-native security information and event management SIEM platform, makes it easier for healthcare organizations to:
- Gain visibility into threats from across all environments and device types, including OT devices, specialized EHR and EMR applications, and legacy systems.
- Detect high-severity security threats quickly and accurately.
- Tap into actionable guidance and supporting information to streamline incident response, containment, and recovery
- Access rich analytics to drive continuous improvement and perform proactive threat hunting
LogRhythm Axon’s cloud-native approach, simple and easily customizable data integrations, and out-of-the-box detection content allow healthcare organizations to eliminate complexity and make an impact on risk quickly.
Custom or industry-specific data sources can be configured quickly and easily to address healthcare organizations’ unique risk factors.
The same is true for detection content. LogRhythm Axon gives healthcare teams a strong foundation of content and analytics mapped to frameworks like MITRE ATT&CK® and industry regulations like HIPAA. At the same time, security teams have the flexibility to create custom detection logic and analytic views catered to their unique needs.
Expanding Healthcare Security Visibility to Networks and Users
LogRhythm Axon’s stand-alone impact in healthcare environments can be further enhanced through optional LogRhythm capabilities like:
- Network traffic analytics that surface instances of unsanctioned application usage, unintentional PHI exposure, and signs of malicious activity
- User and entity behavior analytics that identifies possible account abuse, insider threats, and non-compliant system and application usage
The technologies feed threat details and supporting data directly into LogRhythm Axon, providing a unified framework to analyze and react to all of your activity information and threat signals.
Learn More About How LogRhythm Axon Helps Healthcare Organizations Simplify Security
Interested in learning more about how LogRhythm Axon can help your healthcare organization reduce complexity and risk? Read our solution brief, “Secure Your Healthcare Organization.”
It dives deeper into the topics covered in this post, including:
- Key factors that drive healthcare security complexity
- Trends in healthcare hacking and ransomware activity
- How LogRhythm Axon helps with specific healthcare security challenges
- The role of advanced techniques like network traffic analysis
- How to build momentum and continuously improve your approach
Download your copy today.
[1] Source: “Change Healthcare cyberattack fallout continues,” Health IT Security, May 2, 2024.
The post Meeting the Moment with Better Healthcare Security appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Kelsey Gast. Read the original post at: https://logrhythm.com/blog/meeting-the-moment-with-better-healthcare-security/
如有侵权请联系:admin#unsafe.sh