2024-6-4 01:36:9 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
The Cybersecurity Maturity Model Certification program gives the Defense Department a mechanism to verify the readiness of defense contractors both large and small to handle controlled unclassified information and federal contract information in accordance with federal regulations. The CMMC 2.0 program is currently in the final rulemaking phase with implementation expected in 2025. Large defense contractors with multi-location or region business operations should conduct a CMMC readiness assessment to get ahead of the eventual implementation deadline and better understand how to best implement a compliance solution.
stackArmor’s security and compliance experts have over two decades of experience implementing strong security and compliance guardrails based on NIST and DOD controls. They have developed an efficient Cybersecurity Maturity Model Certification (CMMC) Readiness Assessment solution. Defense contractors should accelerate their readiness efforts by:
- Determining the CMMC scope and boundary definition
- Performing a discovery of CUI data that may include but not limited to
- Word processing
- File and Document sharing
- Collaboration & Communication
- Enterprise Systems
- Review of compliance policies, procedures, and data access plans
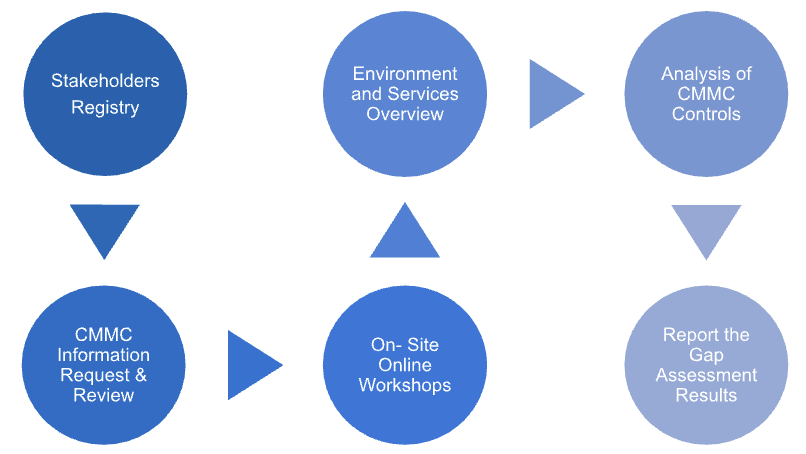
Methodology and Scope for CMMC 2.0 Readiness Assessment
Audit preparation for any NIST based cyber security framework traditionally begins with a discovery of the environment and a gap assessment of the compliance controls.
A series of interview workshops are conducted to understand the impact of the CMMC requirements that the defense contractor will be subject to, with regards to the potential national security information and implementation of cybersecurity standards at progressively advanced levels. This assessment is performed to understand the type and sensitivity of the information. The workshops should also seek to outline the process for information flow down to subcontractors or business partners.
The assessment should be executed across the organization and should include:
- Current Compliance Program Discussion
- Organizational Chart
- Security Management Positions and Resources
- Current Configurations
- Dataflow for CUI, FCI and CTI
- Accreditation Boundary
- Documentation Request List (DRL)
- CMMC Security Control Questions
- Identify Critical CMMC Showstoppers
- Follow-Up Interviews
- Analysis and Reporting
Conducting Personnel Interview Workshops
Conducting structured and systematic interviews with critical stakeholders, information owners, and control owners should ideally follow best practices prescribed by NIST. stackArmor’s CMMC readiness assessment uses steps from the NIST 800-55 Rev1 Information Security Measurement Process to evaluate systems and include a combination of assessor actions and including examine, interview, and test as outlined in NIST 800-171A, which include:
- The examine method is the process of reviewing, inspecting, observing, studying, or analyzing one or more assessment objects (i.e., specifications, mechanisms, or activities). The purpose of the examine method is to facilitate assessor understanding, achieve clarification, or obtain evidence.
- The interview method is the process of holding discussions with individuals or groups of individuals within an organization to once again, facilitate assessor understanding, achieve clarification, or obtain evidence.
These discussions with individuals or groups facilitate understanding, achieve clarification, or lead to the location of evidence; the results of which are used to support the determination of security control effectiveness over time. stackArmor holds discussions with individuals or groups of individuals to facilitate our understanding of current and planned controls.
Interviews can be conducted in person, or by conference calls as mutually agreed upon. Depending on the size and organizational structure, these interviews can be conducted by asset owners (firewalls, servers, networking) or by control family owners (facility managers, Human Resources (HR) directors, Network Operations Center (NOC), etc.).
The CMMC 2.0 Readiness Assessment is an important first step that provides management with data to make budgetary and technology decisions on the right way to proceed with their implementation plan.
stackArmor CMMC Services
CMMC is a United States Department of Defense program that provides a standardized approach to assessing, authorizing, and monitoring commercial cloud services for use by federal entities. As part of the CMMC certification process, companies must be evaluated by an independent Certified Third-Party Assessment Organization known as a C3PAO. Due to the rigor of the CMMC experience, stackArmor has developed diverse services for CSPs. These services, including the CMMC Gap Assessment, have been found beneficial in their pursuit of CMMC compliance.
Key Services Include:
- Defining the CMMC scope definition
- Review and provide guidance on current initiatives
- Planning for the organizations upcoming CMMC process
- Advise on general network CMMC Level 3 requirements
- Input for new policies and procedures or other documents
- Review of the IT Environment to determine level of scope related to CMMC standards
Contact us with any more questions.
*** This is a Security Bloggers Network syndicated blog from Blog Archives - stackArmor authored by stackArmor. Read the original post at: https://stackarmor.com/conducting-a-cmmc-2-0-readiness-assessment/
如有侵权请联系:admin#unsafe.sh