
Last week, PinnacleOne examined the digital “great game” in the Middle East, as the convergence of 2024-6-3 22:31:34 Author: www.sentinelone.com(查看原文) 阅读量:19 收藏
Last week, PinnacleOne examined the digital “great game” in the Middle East, as the convergence of AI, nuclear energy, and geopolitical competition.
This week, we highlight how China’s strategy for evading semiconductor technology controls is driving an increased insider threat issue for leading western enterprises.
Please subscribe to read future issues — and forward this newsletter to interested colleagues.
Contact us directly with any comments or questions: [email protected]

Chips may be the new oil, but there is no petroleum intellectual property buried under the ground to steal. As nations see their economic and strategic futures increasingly dependent on securing digital supply chains, the semiconductor industry is now the front line for intense economic espionage activity and commercially motivated insider threat.
China’s Strategy for Evading Semiconductor Technology Controls
A CSIS report from last year described “China’s New Strategy for Waging the Microchip Tech War.” The report identified the ZTE crisis in April 2018 as a pivotal moment in China’s changing strategic thinking on semiconductors. The U.S. export controls imposed on the Chinese telecommunications giant served as a wake-up call, prompting China to elevate semiconductors from an economic priority to a national security imperative. This imperative has become only more intense as U.S. and allied technology controls tightened over the last two years, becoming now a de facto semiconductor blockade on China for leading edge technologies.
As Chinese intelligence agencies and national semiconductor champions explicitly target key industries through insider and cyber espionage to bolster its economic and military capabilities, semiconductor firms find themselves in the targeting bullseye.
In response, China has adopted a four-pronged strategy aimed at:
- Limiting its exposure to foreign pressure
- Deterring U.S. and allied actions
- Increasing international dependence on its semiconductor industry
- Harnessing the power of AI for economic and military advantages
This strategic shift has led to a more aggressive approach to acquiring foreign semiconductor technologies, with insider IP theft emerging as a key tactic. The blurred lines between state-sponsored espionage and commercial IP theft complicate the threat landscape – Huawei doesn’t need to be told by the MSS to steal valuable IP from its competitors, though it will take their support if offered.
As the Chip Four strengthen multilateral export control enforcement on China and slow AI chip exports to the middle east (seen as a backdoor for China), China will amp up the use of illicit and covert means to circumvent restrictions. This is exactly what we’ve seen.
Surge of Insider IP Theft Incidents
Against the backdrop of China’s shifting strategy, the semiconductor industry has witnessed a surge in insider IP theft incidents, many involving employees of Chinese descent allegedly stealing confidential data and trade secrets from their employers.
Just last week, an incident was reported at SK hynix where a former Chinese employee was arrested for allegedly stealing over 3,000 pages of confidential data on atomic layer deposition (ALD) equipment used in DRAM manufacturing processes. Hired in 2013, the employee worked in the department responsible for analyzing defects in semiconductor designs and was most recently involved in consultations with business-to-business clients in China. China has not yet been able to develop ALD equipment needed for precise and uniform deposition of advanced chips. The Chinese national returned to Korea in June 2022, and left to join Huawei the same month.
Other similar incidents over the past few years include:
- In March 2024, a former Google engineer named Linwei Ding, a Chinese national, was charged by the U.S. Department of Justice for allegedly stealing hundreds of Google’s classified AI files while secretly working for two Chinese companies, including an Ant Group affiliate called Beijing Rongshu Lianzhi Technology Company.
- In February 2024, an ex-Apple engineer was sentenced to prison for stealing self-driving car technology before attempting to flee to China.
- In June 2023, Haoyang Yu, a former engineer from Lexington, Massachusetts, was sentenced to six months in prison for possessing a stolen semiconductor trade secret from his former employer, Analog Devices, Inc. He was found guilty of using the stolen design to start his own microchip business.
- In February 2023, a court found seven former employees of Samsung guilty of illegally obtaining and transferring semiconductor-related technology to Chinese companies. The information related to semiconductor cleaning equipment and was classed as “national core technologies” protected by South Korean laws.
- In September 2021, a former employee of Applied Materials was convicted of possessing stolen trade secrets related to proprietary LCD chip technology, while two other employees were acquitted. Three other employees were initially charged with conspiracy to steal trade secrets under the allegation they planned to use them to launch a US/China-based competitor but were not convicted.
Developing a Comprehensive Insider Threat Program
As we described in an earlier ExecBrief, technology companies need to recognize and address the threat of malicious insiders. To effectively combat the rising tide of insider IP theft, semiconductor firms must develop and assess a comprehensive set of insider threat scenarios tailored to their unique threat model, technical controls, organizational design, and internal culture. The following example threat scenarios can guide insider trust program assessment.
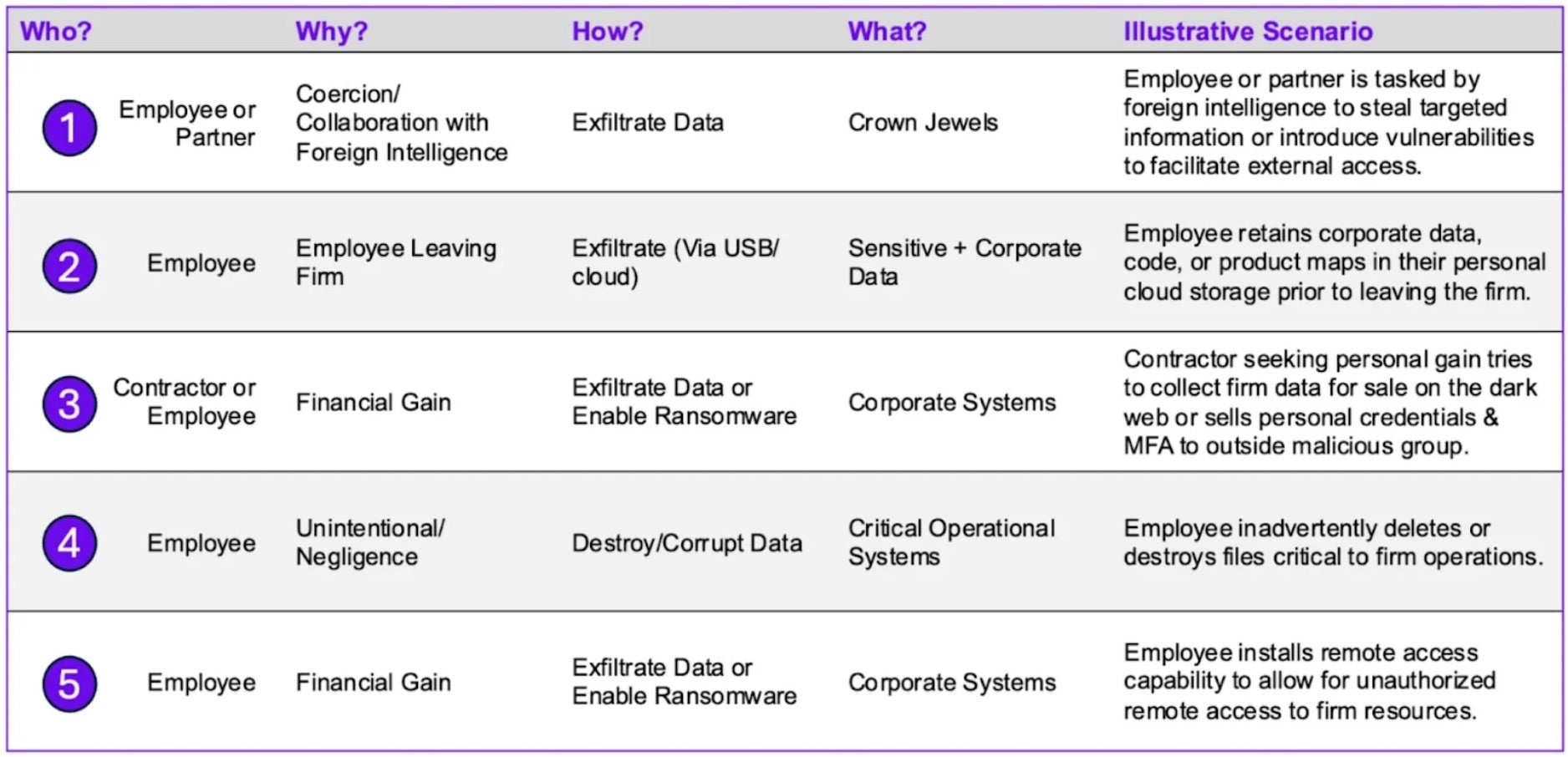
In particular, firms can follow the following approach to build a robust insider threat program:
- Define a tailored set of insider threat scenarios:
- Consider both nation-state actors and lone-wolf/commercial threat actors, identifying plausible targets and objectives specific to the firm’s critical assets and IP.
- Map out potential attack paths and exploitation methods used by insiders, such as exfiltration via USB/cloud storage, installing remote access tools, or destroying critical data.
- Develop a comprehensive set of scenarios that reflect the firm’s unique threat model and risk profile.
- Assess current security controls against these scenarios:
- Evaluate the effectiveness of existing technical controls, such as data loss prevention, access monitoring, and endpoint security, in detecting and preventing insider actions described in the scenarios.
- Identify gaps in visibility, detection capabilities, and response procedures.
- Evaluate organizational design and internal culture:
- Analyze how the firm’s structure, processes, and culture may enable or mitigate insider threats, assessing factors such as employee screening, segregation of duties, access management, and security awareness.
- Identify potential weaknesses or inconsistencies that insiders could exploit.
- Develop a roadmap for improvements:
- Prioritize areas for enhancing insider threat defenses based on the gaps identified in the assessment phase.
- Define clear action items across people, process, and technology domains, such as deploying additional monitoring tools, refining incident response playbooks, improving access controls, and providing targeted security training.
- Set timelines and assign accountability for implementation.
- Implement program enhancements and conduct ongoing validation:
- Execute the improvement roadmap in a phased manner, continuously testing and validating security controls against updated insider threat scenarios.
- Engage third-party experts as needed to assess program maturity and identify further opportunities for improvement.
- Foster a culture of insider threat awareness:
- Regularly communicate the importance of insider threat prevention to all employees, encouraging the reporting of suspicious activities through clear and safe channels.
- Provide role-specific training on identifying and responding to potential insider incidents, and recognize and reward employees who demonstrate strong security practices.
By following these steps and tailoring them to their specific context, semiconductor firms can develop a robust insider threat program that addresses the full spectrum of risks posed by malicious, negligent, or compromised employees. Regular scenario-based testing and iterative improvement will ensure the program remains effective as the threat landscape evolves.
Going Forward
The semiconductor industry stands at a critical juncture, facing an onslaught of state-directed and commercially motivated IP theft that threatens a geostrategic industry. As geopolitical competition intensifies and the boundaries between economic development and national security blur, semiconductor companies must adapt to this new reality and take decisive action to safeguard their invaluable assets and personnel.
如有侵权请联系:admin#unsafe.sh