Active Exploits target Check Point Security Gateway Zero-Day Information Disclosure flawCheck 2024-6-3 19:10:13 Author: lab.wallarm.com(查看原文) 阅读量:28 收藏
Active Exploits target Check Point Security Gateway Zero-Day Information Disclosure flaw
Check Point Cybersecurity has issued hotfixes to address a zero-day vulnerability in its VPNs that has been exploited to gain remote access to firewalls and potentially infiltrate corporate networks.
On 27.04.2024 (Monday), the company initially alerted customers to an increase in attacks targeting VPN devices, offering guidance on how administrators can safeguard their systems. Subsequently, the root cause was identified as a Zero-Day vulnerability, which attackers had leveraged against Check Point's clients.
Designated as CVE-2024-24919, this high-severity information disclosure flaw allows attackers to access specific information on internet-exposed Check Point Security Gateways that have remote Access VPN or Mobile Access Software Blades enabled.

The vulnerability could allow an attacker to read specific information on internet-connected gateways with remote access VPN or mobile access enabled.
The observed attempts, which had been previously reported on May 27, focused on remote access scenarios involving outdated local accounts with password-only authentication, which is not recommended.
Technical details of the vulnerability
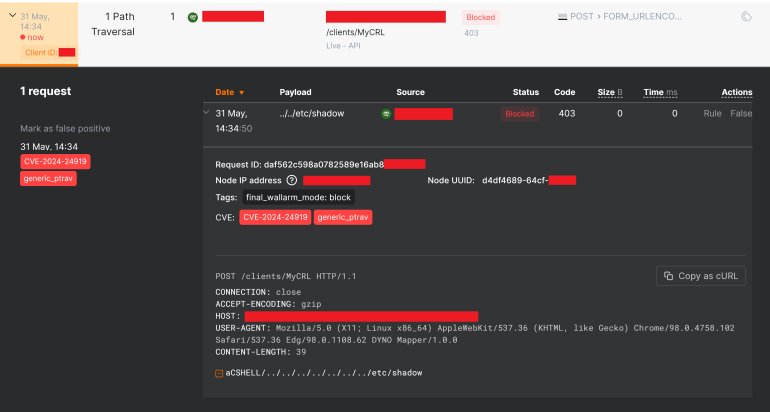
CVE-2024-24919 is a critical vulnerability in Check Point's CloudGuard Network Security appliance. It involves a path traversal flaw in the /clients/MyCRL endpoint, allowing unauthorized file access through a faulty implementation of the strstr function in the HTTP request handler.
The Faulty strstr Function
The strstr function, intended to validate user-supplied paths, is flawed in its implementation, allowing attackers to bypass controls by crafting paths with traversal sequences (e.g., ../). This improper matching lets malicious inputs like /clients/../../etc/shadow pass validation checks and access sensitive files. Attackers exploit this by sending specially crafted HTTP POST requests to the /clients/MyCRL endpoint, manipulating the path to traverse directories and read arbitrary files on the system, including system files, such as /etc/shadow and /etc/hosts.
Wallarm detects CVE-2024-24919 exposure in the wild
Wallarm WAAP platform proactively detects Path Traversal attacks, including CVE-2024-24919. Thus, we started detecting exploitation attempts in the wild immediately after the exploit was publicly disclosed. We detected and blocked over 13,000 attacks exploiting this vulnerability within the first two days after the exploit was publicly disclosed.

Affected software
CVE-2024-24929 affects:
- CloudGuard Network
- Quantum Maestro
- Quantum Scalable Chassis
- Quantum Security Gateways
- Quantum Spark Appliances
(Product versions R80.20.x, R80.20SP (EOL), R80.40 (EOL), R81, R81.10, R81.10.x, and R81.20)
Mitigation
Check Point advises updating affected systems with the provided hotfixes.
To apply the update (hotfixes) released by Check Point, navigate to the 1. Security Gateway portal, 2. Go to Software Updates, 3. Select Available Updates, 4. Click on Hotfix Updates, and 5.'Install.'
References
NVD NIST: https://nvd.nist.gov/vuln/detail/CVE-2024-24919
Vendor’s Advisory: https://support.checkpoint.com/results/sk/sk182336
Security Research: https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/
Exploit: https://github.com/LucasKatashi/CVE-2024-24919
Nuclei Template: https://github.com/projectdiscovery/nuclei-templates/blob/main/http/cves/2024/CVE-2024-24919.yaml
如有侵权请联系:admin#unsafe.sh