
Chained detections is a new threat hunting paradigm aligned with the strategy of chaining interesti 2024-5-31 00:19:56 Author: www.sentinelone.com(查看原文) 阅读量:13 收藏
Chained detections is a new threat hunting paradigm aligned with the strategy of chaining interesting events to identify behavior patterns and augment threat attribution. Much like SentinelOne’s Storyline technology, which connects events from various sources to create a narrative of an attack, human threat hunters harness these capabilities to comprehensively grasp the potential impact of a threat actor.
This new methodology, unique to SentinelOne’s WatchTower services, incorporates proactive and sophisticated ways of uncovering and responding to complex threats. This blog is the second installment in our series showcasing today’s threat hunting infrastructures and explores how to further leverage Chained Detections to enhance an organization’s security posture through adaptive threat hunting. Read part one of the series here.

Understanding Chained Detections
One of the biggest challenges in threat hunting is the fact it is operating primarily within the sphere of low and medium fidelity results. High fidelity detections can be easily converted into alerts, but others are subject to a mundane and time-consuming review, something only more senior analysts can do well. This can make threat hunting both a time consuming and cost prohibitive exercise for many organizations.
There have been many attempts to tackle this problem, including risk-based alerting, clustering, baselining, allowlisting and denylisting, data normalization, tokenization, and supporting the results with additional data enrichment strategies, but there is one more highly effective method out there. Chained detections execute a sequence of automated tasks triggered by an initial detection with the aim to triage and enrich telemetry data progressively.
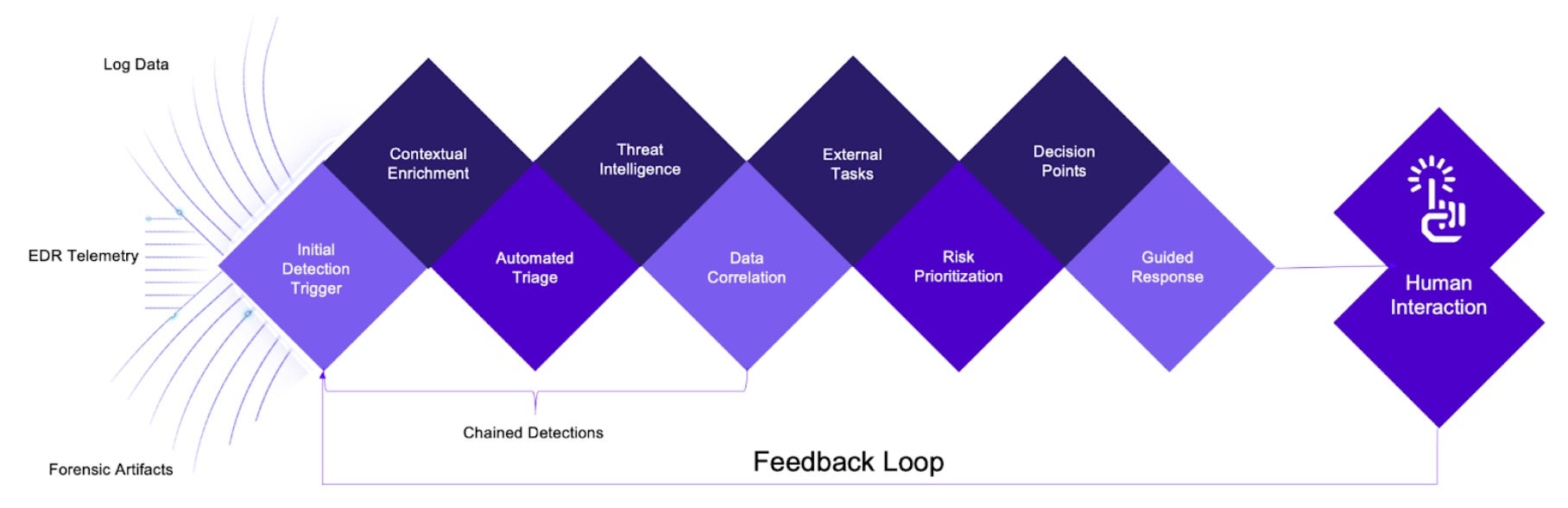
This approach helps to uncover and respond to complex threats without going down too many rabbit holes. Incorporating this new adaptive threat hunting methodology increases the effectiveness of any threat hunting program.
Initial Detection Trigger
The process begins with an initial detection, which could be based on various indicators such as anomalous behavior, known attack patterns, or suspicious activity in telemetry data. Due to the nature of the methodology, vague signals can be also utilized to execute the chain. For example, a file with a specific file name dropped anywhere on a system could act as a trigger.
Automated Triage
Once a detection is made, automated triage processes come into play. These processes aim to quickly assess the detection’s severity and relevance. Some basic steps in automated triage would include:
- Contextual Enrichment – Gathering additional data and context around the event, such as user accounts, device information, or network traffic patterns.
- Correlation – Determining if the event is part of a broader attack or a standalone incident by correlating it with events that may have triggered and are stored in a centralized logging backend.
- Prioritization – Assigning a priority level to the event based on its perceived risk and potential impact to the organization before collecting more information.
Chaining Tasks
Depending on the outcome of the initial triage, additional automated tasks are triggered in a chained manner. These tasks are designed to gather more information, validate the detection, and potentially take predefined actions. Examples of chained tasks include:
- Threat Intelligence Lookup – Querying threat intelligence feeds to check if the indicators associated with the event are known threats.
- Isolation and Remediation – Isolating the affected system or network segment to prevent lateral movement by the attacker and initiating remediation actions, such as applying patches or disabling compromised accounts.
Data Collection
Gathering detailed information about the affected system, such as running YARA rules and collecting memory dumps, process lists, or file system snapshots may be necessary.
Decision Points, Human Intervention & Feedback Loops
At each stage of the chained detection process, decision points are established based on the findings. These decision points guide whether to continue with additional tasks, escalate the incident, or conclude the investigation.
While much of this process is automated, there is still a role for human intervention. Security analysts may be brought into the loop when certain thresholds are met or when the automated processes cannot make conclusive determinations.
Chained detections also incorporate a feedback loop for continuous improvement. Information gathered during investigations, including false positives and false negatives, is used to refine and enhance detection and response processes.
The chained detections approach for threat hunting is highly effective for dealing with advanced and evolving threats. It enables organizations to respond rapidly and systematically to security incidents, minimizing the impact and reducing the time to remediation. It also leverages automation to handle repetitive tasks, allowing security analysts to focus on complex investigations and strategic decision-making.
Case Study | Real-World Threat Hunting with SentinelOne’s WatchTower Team
A malicious hacker reaches out to a client, claiming they’ve infiltrated their CCTV system and is asking for compensation. The SentinelOne WatchTower team receives the call to help uncover the culprits behind the extortion attempt, the precise actions taken, the systems involved, and the exact timing of it all. First, the team deploys instrumentation where there has been a cybersecurity blackout, a significant number of systems with no detection and response tools installed. This is a digital detective game and the main goal is to gain insight into every system level and user-based move.
SentinelOne followed the below steps to effectively threat hunt and mitigate the threat:
- Scanning for initial indicators, the SentinelOne response team identified an initial detection found in the EDR telemetry that malware payloads may potentially be present on an endpoint.
- Although there were no malicious processes and the files had been deleted, the team was able to locate some low frequency indicators. To build more context, enter metadata collection leveraging YARA rules.
- This revealed definite artifacts of files that were once on the system, specifically, payloads which may have included remote access tools (RATs) such as njRAT and StRaXxXD – likely downloaded from Telegram.
- After backtracking the user activities, various RDP brute forcing tools such as NLA.Ckecker and NLBrute were identified as having been downloaded onto other systems.
- This activity strongly indicated potential Initial Access Broker activity – not just an average attacker, but a sophisticated criminal organization.
Initial Detection on Target Compromised System
Threat Hunting Details:
endpoint.name: xxxserver1 timestamp: <<MM DD · 11:xx:46.811 am>> tgt.file.path: C:\Users\...\Downloads\nj-RAT.zip C:\Users\...\Downloads\Telegram Desktop\nj-RAT.zip tgt.file.sha1: ed4f80… src.process.user: xxxserver1\userA
The same user downloaded ddos.exe (alerted by SentinelOne upon agent installation on a different system):
timestamp: <<MM DD · 9:xx:27.123 pm>> tgt.file.path: C:\Users\...\Downloads\Telegram Desktop\ddos.exe tgt.file.sha1: fddece… src.process.user: xxxserver1\userA
Viewing event logs and correlating activity, the SentinelOne WatchTower team identified an active attempt to brute force login after finding numerous failed login attempts on xxxserver1. Upon checking the visible IP in the console, the team found it to be 10.x.x.x with an open RDP port 3389 accessible from the Internet. Subsequently, the team pinpointed the machine that was subjected to Remote Desktop Protocol (RDP) brute forcing and subsequently compromised to launch the attack.
Remote Desktop Protocol (RDP), developed by Microsoft, provides a convenient way to access IT systems remotely and is widely used across client environments. However, it also poses significant risks if not properly configured. Attackers often target exposed RDP clients, attempting brute force attacks on usernames and passwords. If successful, they can gain a foothold in the victim’s network.
Notable items detected by threat hunters:
…Downloads\StRaXxXD.zip 62a861056f35fd8cb754672080b0eeb8faae806d …Telegram Desktop\NLBrute (RDP brute forcing tool) …Telegram Desktop\IN_ip_ranges.txt, ip.txt (possible enumeration) …Telegram Desktop\سنگین بدبویTXT.txt …Telegram Desktop\@Delta_Package pentest network xxx.part3.rar …Telegram Desktop\2.rar …Telegram Desktop\ip.txt …Telegram Desktop\india test.txt …Telegram Desktop\dork for mahdi.txt …Telegram Desktop\@Delta_Package pentest network xxx.part6.rar …Telegram Desktop\Linux 1,2.rar …Telegram Desktop\Work With Dorks [DORKs Generator] By JohnDoe v.2.1.rar Targeting Domains with Google Dorks …Telegram Desktop\ep1.rar …Telegram Desktop\4.rar …Telegram Desktop\NLBrute (2).rar …Telegram Desktop\Cracker (1).exe 756280… …Telegram Desktop\NLA.Ckecker.zip dddbd… …Telegram Desktop\SQLi Dumper V10.3.zip f00d9… …Telegram Desktop\NLA.Ckecker (2).zip dddbd… …Telegram Desktop\ready.apk b78812…
Summary of Further Analysis
Swift action by the SentinelOne WatchTower team prompted the client to pull the plug on their server after receiving the details of the compromise. After a thorough investigation, the team advocated for the closure of unused RDP ports and security tools for threat detection and prevention be installed on every system. The team also recommended the implementation of multi-factor authentication (MFA) for every system accessible from the Internet as a best practice.
Conclusion
Threat hunting continues to face significant challenges, particularly in navigating the realm of low and medium fidelity results. This dilemma often translates into a cumbersome and time-consuming review process, reserved for seasoned analysts, making threat hunting both costly and impractical for many organizations. Chained detections represent a proactive and sophisticated methodology that revolutionizes threat hunting by streamlining the investigative process, avoiding unnecessary tangents, and focusing resources where they matter most. By incorporating automated triage, external tasks, and establishing decision points, organizations can swiftly uncover and respond to complex threats with precision and agility.
The chained detections approach supports a symbiotic relationship between automation and human intervention, harnessing the power of technology to handle repetitive tasks while empowering security analysts to tackle intricate investigations and strategic decision-making. The integration of a feedback loop ensures continuous improvement, refining detection and response processes based on real-world insights gathered during threat hunts and cyber investigations.
For organizations seeking to fortify their cybersecurity posture and elevate their threat hunting capabilities, embracing the chained detections methodology is not merely an option but a necessity in today’s threat landscape. By leveraging a combination of both automation, intelligence and human expertise, organizations can effectively combat advanced and evolving threats, minimizing the impact of security incidents, and accelerating the path to remediation.
Learn More About SentinelOne’s WatchTower
For enterprises looking for a threat hunting partner to help them implement a robust methodology and stand up to emergent threats, SentinelOne’s WatchTower provides threat hunting experts equipped with the latest threat intelligence powered by artificial intelligence (AI) and machine learning (ML) algorithms.
Today, customers can use WatchTower to achieve real-time and retroactive detections of anomalous activity across their enterprise to proactively address evolving threats and strengthen their security posture. Learn more about what WatchTower can do for your enterprise by requesting a demo.
如有侵权请联系:admin#unsafe.sh