The digital era is constantly evolving, and businesses are rapidly migrating towards cloud-based solutions to leverage the agility, scalability, and cost-effectiveness they offer. However, this transition also introduces new security challenges. As more sensitive data and applications reside in the cloud, ensuring their security becomes paramount. This is where Cloud Penetration Testing (Cloud Pentesting) steps in as a way to secure your data.
What is Cloud Penetration Testing?
Cloud Pentesting is a comprehensive approach designed to identify and exploit security vulnerabilities in cloud-based applications and infrastructure. It essentially simulates real-world cyber attacks to assess the security posture of your cloud environment. This exposes potential flaws before hackers can leverage them.
Similar to traditional penetration testing, Cloud Pentesting employs various techniques to analyze your cloud defenses. Ethical hackers, also known as white-hat hackers, work within a defined scope and authorization to discover and exploit vulnerabilities. This testing process helps identify:
Security Misconfigurations: Improper cloud misconfigurations of cloud resources can create security gaps that attackers can exploit.
Weak Access Controls: Inadequate access controls can grant unauthorized access to sensitive data and applications.
Software Vulnerabilities: Cloud-based applications, like any software, can harbor vulnerabilities that attackers can use to gain a foothold in your system.
Data Leakage: Cloud Pentesting can uncover potential pathways for sensitive data to leak from your cloud environment.
Why Cloud Security Demands Proactive Measures?
Cyberattacks are a growing concern, with statistics revealing a cyberattack occurring every 44 seconds. India faces a critical challenge with cybercrime, averaging over 7,000 daily complaints reported in 2024 (as of May 23rd). These attacks target vulnerabilities in systems and applications to gain unauthorized access to sensitive data. Cloud environments are no exception, and the number of cloud-based security incidents has risen significantly in recent years.
While Cloud Service Providers (CSPs) implement baseline security measures, the obligation of securing data and applications within the cloud falls on the shoulders of the organizations themselves. This shared responsibility model necessitates a proactive approach to cloud security, and Cloud Penetration Testing emerges as an important way in this strategy.
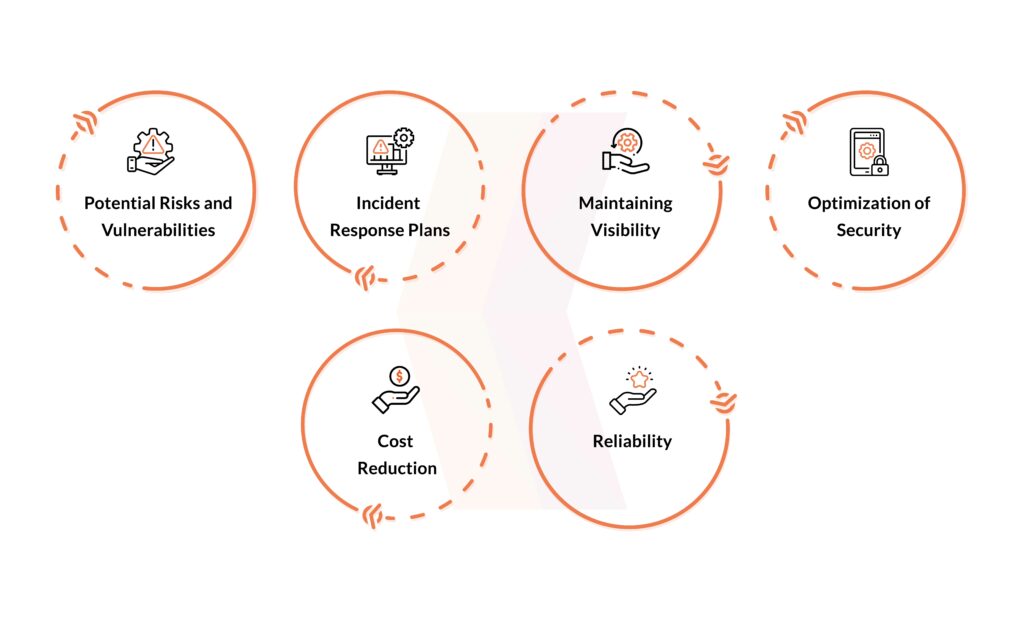
Importance of Cloud Penetration Testing
Book a Free Consultation with our Cyber Security Experts

Integrating Cloud Penetration Testing into your security strategy offers a multitude of benefits. These have been listed below:
Proactive Threat Detection: By simulating real-world attacks, Cloud Pentesting helps identify vulnerabilities before they can be exploited by malicious actors.
Enhanced Security Posture: Addressing the identified vulnerabilities can significantly strengthen your cloud security posture and minimize the attack surface.
Improved Resilience: Cloud Pentesting helps identify flaws in your incident response plan, allowing you to refine your procedures and improve your ability to respond effectively to security incidents.
Compliance Adherence: Many industries have strict data security regulations. Cloud Pentesting can help ensure your cloud environment adheres to these compliance requirements.
Boosted Customer Trust: Demonstrating a commitment to cloud security through regular Cloud Pentesting builds trust with your customers, who are increasingly concerned about data privacy.
What is the Process of Cloud Penetration Testing?
The process of cloud security testing involves a systematic approach to assess the security of cloud-based systems and services. Here is a general outline of the key steps involved:
- Planning and scoping: Define the scope of the cloud security testing engagement. Identify the specific cloud services, applications, or infrastructure components to be tested. Determine the goals, objectives, and constraints of the testing process.
- Reconnaissance: Gather information about the target cloud environment. Identify the cloud provider, understand the architecture, and enumerate cloud-based assets and services. This step helps in understanding the scope and potential attack vectors.
- Threat Modeling: Analyze the cloud environment from an attacker’s perspective. Identify potential vulnerabilities, weak points, and areas of concern. Prioritize testing efforts based on the criticality of assets and potential impact.
- Vulnerability Scanning: Conduct automated scans to identify common vulnerabilities and misconfigurations in the cloud infrastructure. This includes scanning for weak access controls, unpatched systems, insecure network configurations, and other known vulnerabilities.
- Manual Testing: Perform manual testing techniques to explore and validate vulnerabilities identified in the previous step. This may involve attempting to exploit vulnerabilities, leveraging weak security controls, or analyzing the effectiveness of encryption and access controls.
- Privilege Escalation: If initial access is achieved during testing, attempt to escalate privileges within the cloud environment. This step helps assess the impact of compromised credentials or privileges and identifies any weaknesses in access controls.
- Data Exfiltration: Simulate attacks aimed at extracting sensitive data from the cloud environment. This helps identify weaknesses in data protection mechanisms, encryption practices, or data leakage prevention controls.
- Reporting and Remediation: Document the findings, including identified vulnerabilities, potential impacts, and recommended remediation steps. Provide a comprehensive report to the organization, along with actionable recommendations to mitigate the identified risks.
Note that conducting cloud security testing requires proper authorization from a premium cloud service provider and the organization that owns the cloud infrastructure.
Unauthorized pentesting can lead to legal consequences and service disruptions. Regularly performing cloud security testing helps organizations identify and address security flaws, reduce the risk of data breaches, unauthorized access, and service interruptions, and ensure the overall security of their cloud-based systems and services.
Benefits of Cloud Security Testing
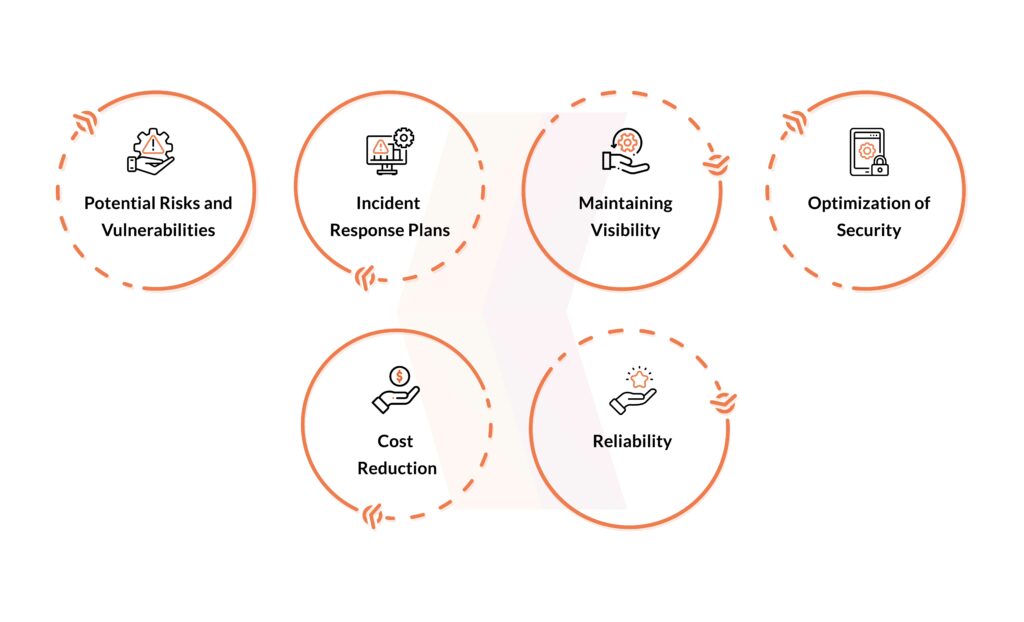
Through proactive prevention of avoidable breaches, cloud penetration testing helps organizations increase the security of their cloud systems. It provides insightful information for strengthening security programs by highlighting vulnerabilities, risks, and gaps in security procedures.
Cloud Penetration Testing plays a crucial role in:
- Enhancing an organization’s understanding of business risk
- Identifying vulnerabilities
- Illustrating the potential consequences of exploitation
- Offering remediation advice for effectively mitigating risks
Conclusion
Businesses have to ensure robust cloud security; it is no longer an option. The perpetually present threat of hacking is the catch, though. As this blog pointed out, cloud security testing is a crucial step in securing your cloud architecture against potential flaws and data breaches. With proven expertise in securing cloud data for over 450+ businesses of all sizes across various industries, Kratikal, being a CERT-In empanelled organization is your trusted cybersecurity company.
The fact is that security issues are dynamic and ever-changing. Your current security measures might not be sufficient to keep up with increasingly sophisticated cyber threats. The cloud offers immense potential, but are you equipped to handle hidden security threats? Don’t wait – proactively secure your cloud environment with Cloud Penetration Testing.
The post What is Cloud Penetration Testing? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Riddika Grover. Read the original post at: https://kratikal.com/blog/what-is-cloud-penetration-testing/
如有侵权请联系:admin#unsafe.sh