2024-5-21 21:35:36 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Monitoring user activity on your critical endpoints is a vital part of an effective cybersecurity strategy. Organizations need to monitor both remote and local user sessions to ensure user accountability, manage cybersecurity risks, enable prompt incident response, and comply with relevant cybersecurity laws and regulations.
This is a step-by-step guide on how to monitor user activity in Linux and record remote SSH sessions on any endpoint with the Ekran System software agent installed. This article is also useful for organizations that want to explore Ekran System’s capabilities. Learn how to:
- Monitor, block, and record SSH sessions in Linux
- Receive alerts about suspicious user activity on Linux endpoints
- Export recorded Linux sessions for investigation purposes
- Generate reports on remote SSH connections to your endpoints
Why monitor SSH sessions?
SSH is a secure way to remotely access critical endpoints and servers. However, unauthorized users can still gain access through vulnerabilities or stolen credentials. By monitoring SSH sessions, your security officers can detect suspicious user activity, such as attempts to access unauthorized files or run malicious commands.
Benefits of monitoring and recording SSH sessions
Manage cybersecurity risks
Meet IT compliance requirements
Promptly respond to insider threats
Enhance visibility. By monitoring SSH sessions, you can gain a clear view of remote users’ activity. User activity monitoring software for Linux allows you to oversee who accesses critical systems and what they do, enabling you to detect anomalies and suspicious user behavior in real time. User session recordings also provide you with compelling evidence for incident investigation.
Manage cybersecurity risks. Better visibility can help you detect malicious user activity, such as unauthorized access attempts, data exfiltration, and system sabotage. Software for monitoring Linux SSH sessions allows you to detect cybersecurity threats and take measures to block them before they cause damage.
Meet IT compliance requirements. Many cybersecurity standards, laws, and regulations require organizations to audit access to sensitive systems. Recording SSH sessions and monitoring user activity in Linux provides an audit trail that can show when a critical workstation was accessed, who accessed it, and what activities they performed. These detailed audit logs can help demonstrate your organization’s compliance with industry regulations and internal security policies.
Promptly respond to insider threats. By monitoring user activity, your security team can quickly investigate incidents by analyzing logs. This gives them a better understanding of the scope and root cause of a breach, allowing for targeted decisions and a fast response time. Additionally, certain Linux user activity tracking software solutions can automatically detect and respond to threats before they become an issue.
For a detailed explanation of risks posed by remote users, refer to our articles on managing insider risks in hybrid and remote work environments.
Using Ekran System to monitor remote SSH sessions and local Linux sessions
Ekran System is a universal insider risk management platform that can help your organization deter, detect, and disrupt insider threats.

Ekran System enables you to monitor and record remote SSH sessions and user activity on local Linux endpoints, providing you with indexed recordings and the following searchable metadata:
- Session details, such as hostname, user name, IP address, and session duration
- User actions, such as keystroke input, including commands and parameters executed
- Commands carried out in executed scripts
- System function calls
- System responses from the terminal, such as command outputs
In addition to user activity monitoring, Ekran System provides access management capabilities, real-time alerts on user activity, incident response features, and comprehensive reporting to ensure a holistic approach to managing insider risks.
Ekran System is flexible, providing a variety of deployment options and supporting the following platforms:
Platforms supported by Ekran System
- Infrastructure servers
- Terminal servers
- Jump servers
- Physical and virtual desktops
- Windows
- Linux
- macOS
- UNIX
- X Window System
- Citrix
- VMware Horizon
- Microsoft Hyper-V
- Citrix
- Amazon WorkSpaces
- AWS (Amazon Web Services)
- Windows Virtual Desktops
Let’s see how to record local Linux sessions and monitor remote SSH sessions with Ekran System. If you prefer a presentation in a video format, you can watch our YouTube demonstration:
Note: Further instructions will only work for IT environments that have deployed Ekran System.
Monitoring, viewing, and blocking SSH sessions
By default, Ekran System monitors user activity on all endpoints with the Ekran System software agent installed. Whether users initiate Linux sessions remotely via SSH/telnet or start them locally, Ekran System records all user actions performed on the monitored workstation.
All sessions in Ekran System are displayed on the Monitoring Results page. Let’s suppose that a user starts an SSH session. Here’s how to check user activity logs in Linux:
First, filter the sessions by the operating system. Click the More Criteria button and select Operation System in the drop-down list.

Then, click the Operation System button that appears on the left and select the Linux OS.

You can then search for a session by an executed command. For example, let’s find Linux sessions in which some files were deleted.
Just type in the corresponding command in the search box on the right and press Enter. You can also search within sessions by other user actions such as typed keystrokes.
Once you’ve found the session you need, double-click it to open it.

In the opened Session Player, you can view the screen recording and metadata from the beginning of the session.

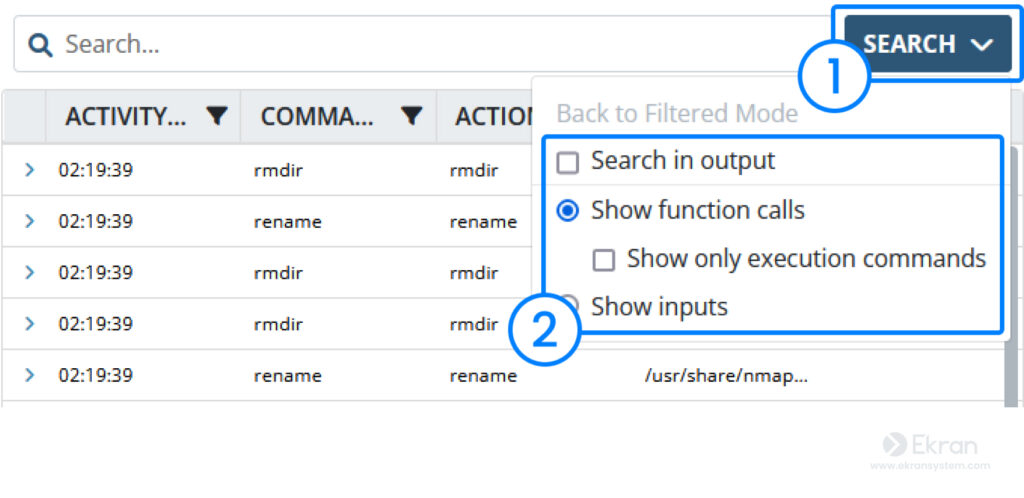
You can configure the video player to display only executed commands and search for a command in a Linux command output in a specific session or the entire database. To do this, choose your settings in the dropdown menu by clicking the Search button.

If a session is still in progress, you can view what the user is doing in real time by clicking the Live button. The Block User button in the upper right allows you to block the user if they pose a threat.

Configuring alerts on suspicious user activity
When dealing with a critical endpoint, you can configure real-time alerts to get instantly notified whenever suspicious user activity occurs. To set this up, open the Alert Management page.
As an example, we’ll set up an alert for detecting a user getting root privileges on Linux. This alert is one of the pre-defined alerts available in Ekran System.
You can search for an alert by inputting its name in the search box. Once you find an alert, click on the Edit icon to configure it.

The alert rules are already predefined, so you only need to assign the Client and specify the additional actions that will be performed if the alert is triggered.
In the Assigned Clients section, click Add and then select the endpoints you want to enable this alert for.

In the Actions section, specify who will be notified via email if the alert is triggered.
You can also decide which response action Ekran System will automatically take upon triggering an alert. Possible response actions include:
- Display a warning message to a user
- Block the user
- Kill a process
Once you’ve configured the alert, click Finish.

Now a designated person will receive an email if the user on the specified endpoint attempts to get root privileges.
With Ekran System, you can create your own custom alerts or enable predefined ones. For instance, you can receive alerts when users try to upload files to the cloud, install an application, or type a specific word.
To view the list of all triggered alert events, open the Alerts tab on the Monitoring Results page. You can open a suspicious session by clicking the Play icon — session playback starts with a selected alert event.

Exporting a recorded session for forensic investigation
With Ekran System, you can export an entire user session or part of one for use as evidence during forensic investigation. The exported session can be viewed on any computer, even without access to Ekran System’s interface. The exported file is encrypted and protected from modification.
To export a session, open it and click the Tool icon in the Session Player. Then select Forensic Export in the drop-down list.

In the pop-up window that appears, define your preferred settings and click Export.

Once the export finishes, you can download the resulting file on the Forensic Export History tab on the Monitoring Results page.

Note: You will need to download the Ekran Forensic Player to view the exported session.
Generating reports on remote SSH connections to your endpoints
Ekran System can regularly notify you about remote connections to your Linux endpoint in a summary report generated ad-hoc or emailed to you on schedule.
To generate a report, open the Reports page and select the Session Grid Report in the Report Type drop-down list. In the Date Filters section, select the period you want the data to be displayed for.

Descriptions and samples of the reports are located in the right part of the interface.
In the Clients section, click Add and select the Linux endpoints you want to generate a report for. You can do this by inserting the names of endpoints in the search box.

Define the report options and click the Generate Report button. Your report will be available to download on the Generated Reports tab of the Reports page.

You can also receive regularly scheduled reports by opening the Scheduled Report tab and clicking Add.
On the Add Rule page that opens, select the Enable scheduled report generation option, enter a name for the rule, and click Next.

Then set the report parameters and enter the email address to which the report will be sent. Click Finish.
Ekran System will automatically create the report and send it to your email address per the defined frequency.
Case study
A US-based Financial Services Company Effectively Monitors and Audits Privileged Users with Ekran System

Conclusion
Monitoring user activity in remote SSH and local Linux sessions can help your organization enhance visibility in your IT infrastructure, promptly detect and respond to security threats, and meet certain IT compliance requirements. By recording user sessions, you’re able to hold users accountable for their actions and provide forensic investigators with informative evidence of security incidents if they occur.
By leveraging Ekran System’s user activity monitoring, privileged access management, and incident response capabilities, you can significantly boost your CISO’s insider risk management efforts and enhance overall organizational cybersecurity.
Want to try Ekran
System? Request access
to the online demo!
See why clients from 70+ countries already use Ekran System.

*** This is a Security Bloggers Network syndicated blog from Ekran System authored by Vlad Yakushkin. Read the original post at: https://www.ekransystem.com/en/blog/linux-session-monitoring
如有侵权请联系:admin#unsafe.sh