
read file error: read notes: is a directory 2024-5-21 20:59:20 Author: www.sentinelone.com(查看原文) 阅读量:19 收藏
Politically-motivated hacktivist groups are increasingly utilizing ransomware payloads both to disrupt targets and draw attention to their political causes. Notable among these hacktivist groups is Ikaruz Red Team, a threat actor that is currently leveraging leaked ransomware builders.
In attacks occurring over recent months, we have observed Ikaruz Red Team and aligned groups such as Turk Hack Team and Anka Underground (aka Anka Red Team) conduct attacks against Philippine targets and hijack branding and imagery belonging to the government’s Computer Emergency Response Program (CERT-PH).
In this post, we profile this hacktivist group and its recent actions, highlighting the threat actor’s methodology, social media activity and relevance within the wider geopolitical context.

Geopolitical Context & Affiliations
Ikaruz Red Team (IRT), under various identities, has targeted entities in the Philippines through defacements, small-scale DDoS attacks and now ransomware attacks. This behavior, between 2023 and present day (2024), is part of the larger wave of hacktivist groups targeting the region, as documented by Resecurity in April 2024. Resecurity ties these more recent observations to the greater geopolitical landscape, in the context of rising tensions with China, noting that the Philippines’ strategic significance in the Indo-Pacific makes it an attractive target for actors bent on civil disruption.
Over the last year or so, the Philippines has experienced an increase in scattered hacktivist attack campaigns. Previously identified hacktivist groups such as Robin Cyber Hood, Philippine Exodus (aka PHEDS), Cyber Operations Alliance, and Philippine Hacking University have been claiming credit for a variety of ransomware attacks, misinformation campaigns and espionage. On April 8th, the Philippine’s National Privacy Commission (NPC) launched an investigation into a breach of critical government infrastructure through an attack on the Department of Science & Technology by a previously unknown hacktivist identifying itself as #opEDSA.
More widely, as we detail below, IRT shares close associations with Anka Red Team and Turk Hack Team, a pro-Hamas hacktivist collective that has gained increased notoriety since the onset of the Israel-Hamas war.
Ikaruz Red Team Ransomware Activity
Within this context, Ikaruz Red Team, previously known primarily for web defacements and nuisance attacks, appears to be engaged in launching small-scale ransomware attacks with leaked LockBit builders. The group has been actively distributing modified LockBit 3 ransomware payloads and advertising data leaks from a variety of organizations in the Philippines.
Ikaruz Red Team ransom notes use the original LockBit template almost entirely intact with the exception of the top line, where the LockBit ransomware name is replaced by ‘Ikaruz Red Team’. Modifying the config.json file prior to building the LockBit payloads allows for this simple modification within the ransom notes.
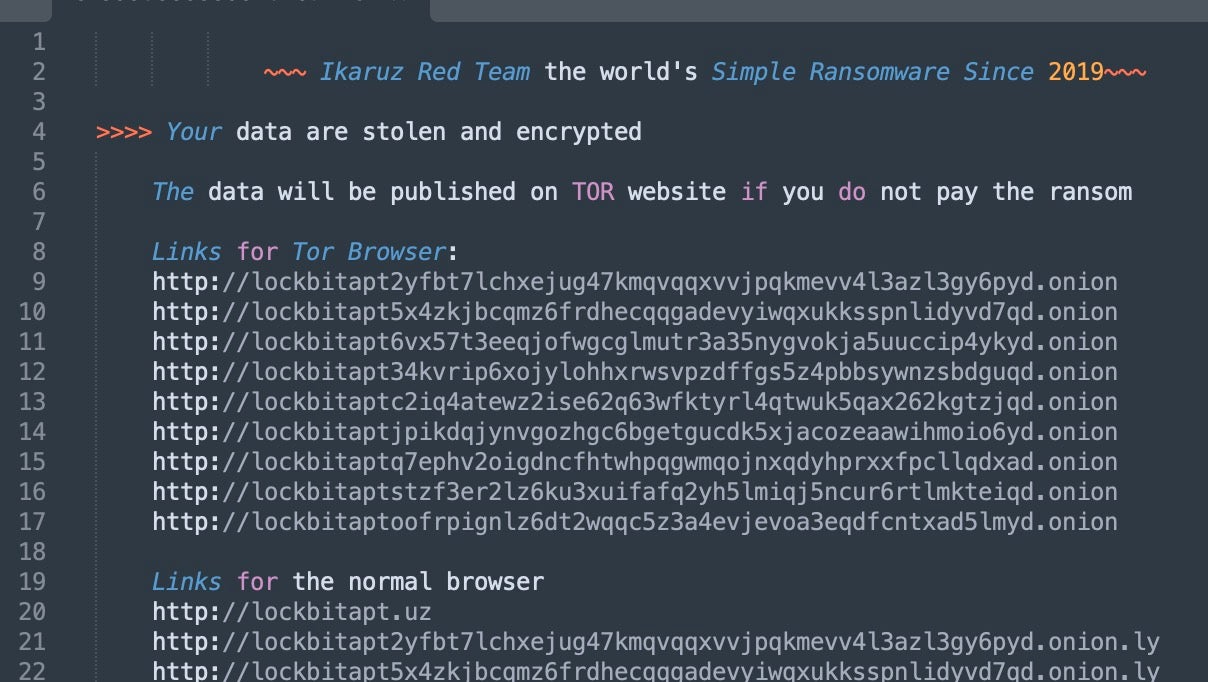
All contact details in the analyzed ransom notes are left to the default TOX IDs, Jabber IDs, and email addresses present in the LockBit builder. This is indicative of a threat actor with little interest or perhaps ability to engage in the kind of follow-up and victim negotiations typical of serious ransomware operators and affiliates, suggesting instead that the motivation is more to sow disruption and garner attention through social media postings.
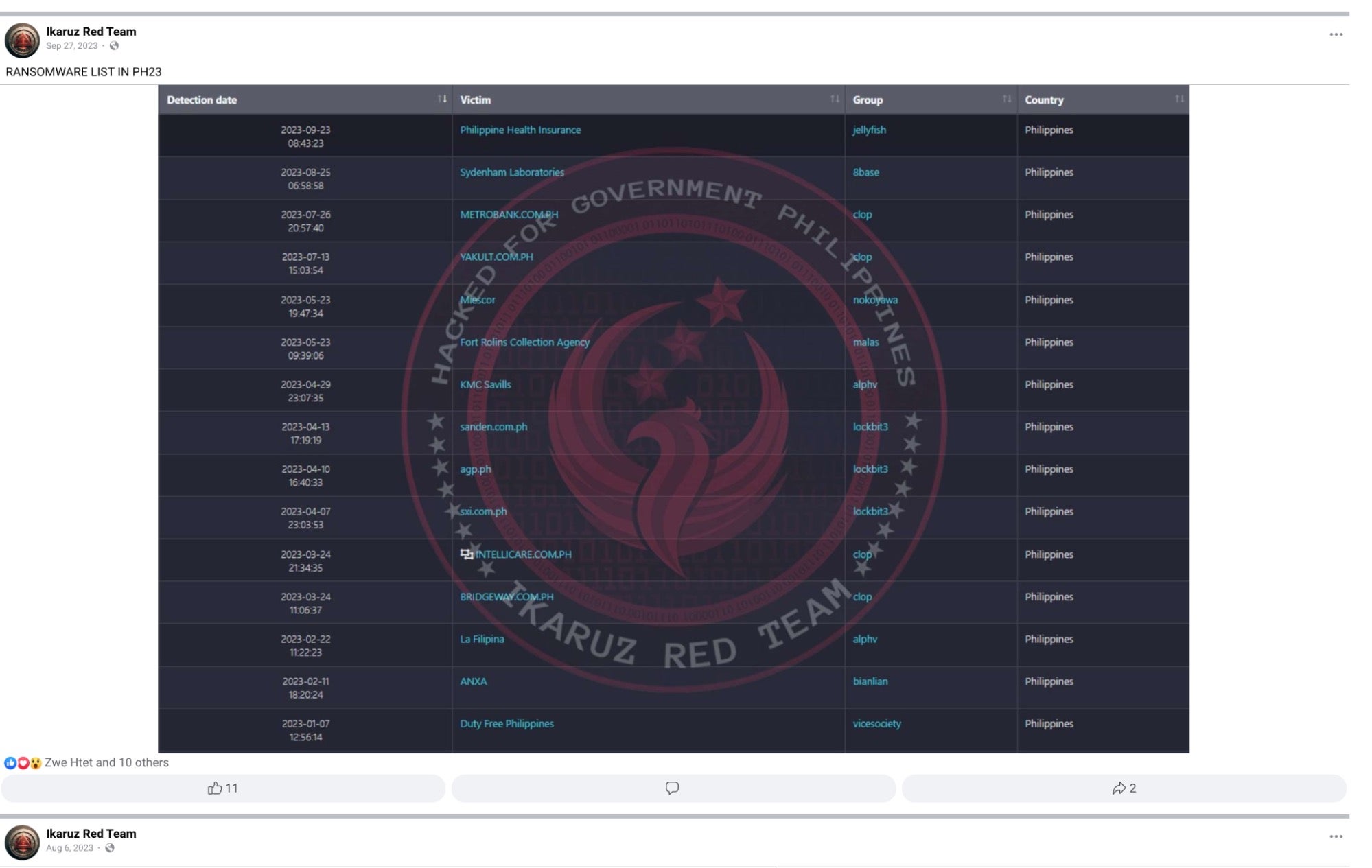
Between January and September of 2023, Ikaruz Red Team claimed responsibility for attacks on multiple Philippine entities. Besides LockBit, the group’s social media postings indicate the use of JellyFish (aka Medusa), Vice Society, ALPHV, BianLian, 8base, and Cl0p ransomware families.
Some of the reported attacks were publicly announced on IRT’s social media accounts, as well as being listed on the larger ransomware platforms’ respective data leak sites.
Observed payloads are standard LockBit 3.0 LBE.3 executables packaged as self-extracting RAR files with a custom IRT .ico file.

This bundled .ico file is meant to replace the stock LockBit icon resource on encrypted files. However there appears to be an error in referencing the resource, or the author omitted the inclusion of the required RED.png file.
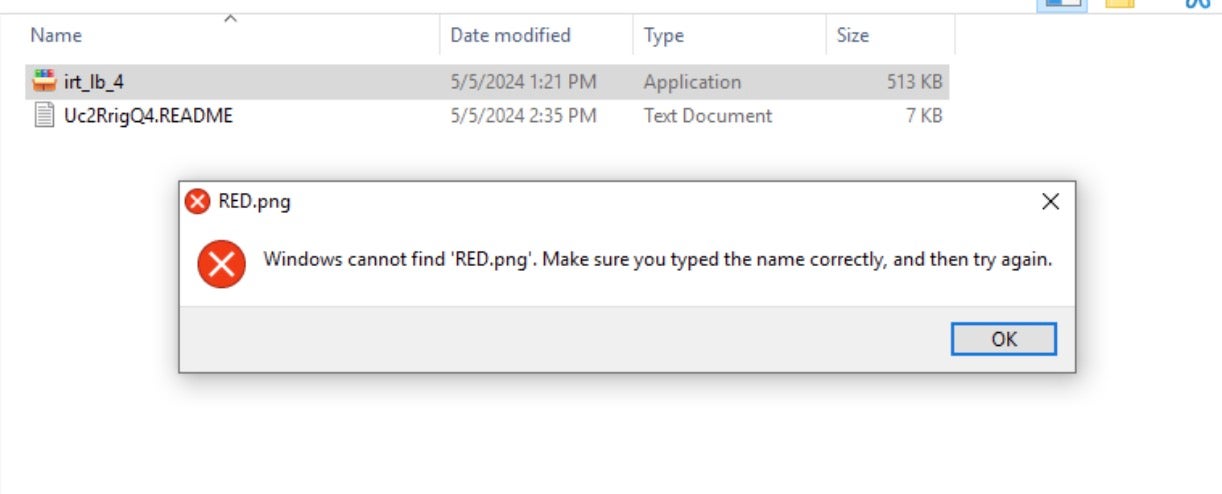
When executed under typical circumstances, the payload will extract the embedded LockBit payload (lb3.exe) and launch it. The ransomware will then rapidly traverse available local and mounted shared volumes, encrypting applicable files and data.
Encrypted files are given a .Uc2RrigQ extension with the specific Ikaruz Red Team LockBit payload we reviewed. The same .Uc2RrigQ string is appended to the names of the ransom notes (e.g., Uc2RrigQ4.README.txt). Per typical LockBit execution, the desktop wallpaper is also replaced with condensed instructions referencing the dropped ransom note.
Co-opting of Hack4Gov Imagery
As part of its attempts to draw attention, IRT has co-opted imagery and branding developed by the Philippine’s Department of Information and Communications Technology (DICT) and CERT-PH as part of a Hack4Gov challenge. HackForGov, started in 2023, is an annual government-sponsored CTF (Capture-the-Flag) competition hosted in Manila and aimed at building the country’s cybersecurity capacity.
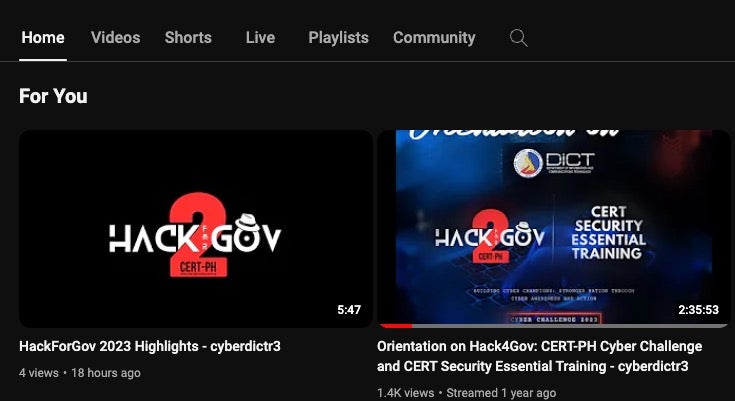
Ikaruz Red Team has co-opted much of this imagery and branding into their defacements and social media profiles. For example, an IRT Twitter/X profile under the name ‘Ikaruz Reginor’ heavily incorporates the same imagery, as does the group’s Zone-Xsec defacement entries, which claim affiliation to team “HACK4GOV.PH”.
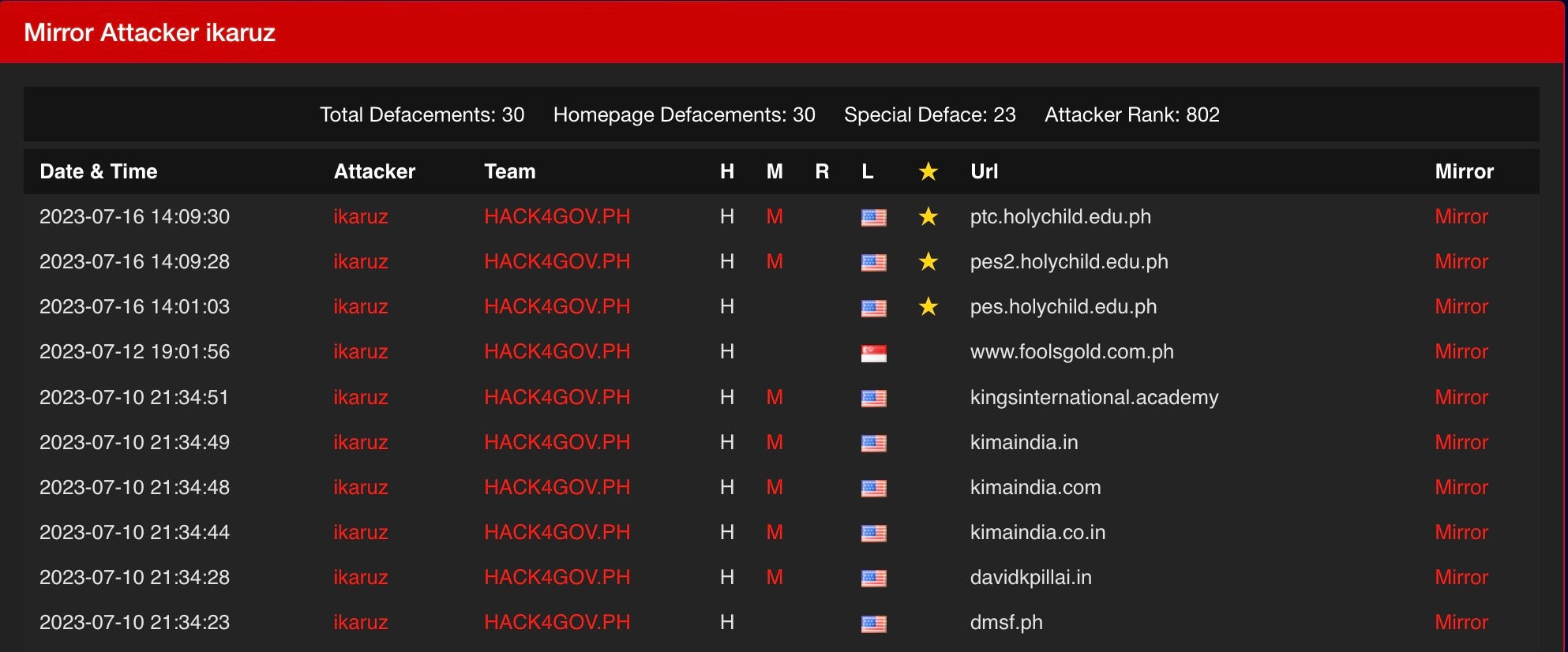
This threat actor is neither a participant in nor affiliated with the official HACK4GOV challenges in any way. We can only speculate as to the reasons behind co-opting official government images and branding, but perhaps two plausible theories would be as an attempt to mock the government’s efforts at improving cybersecurity resilience or an effort to cloak malicious activities behind official-looking iconography. These are, of course, neither mutually exclusive nor exhaustive possibilities.
Tracking Ikaruz Red Team Across Social Media
The threat actor utilizes various social media platforms and identities to engage with its audience and promote its political causes. The aliases “IkaruzRT” and “Ikaruz Reignor” are the most prevalent. This persona is active on popular forums including (the currently defunct) BreachForums and Zone-Xsec. Various public profiles also exist on GitHub, Facebook, Iris, X/Twitter, and Imgur.
The ‘ikaruzrt’ profile on BreachForums has actively posted regarding availability of data leaks from victims in the Philippines between August of 2023 and January of 2024.
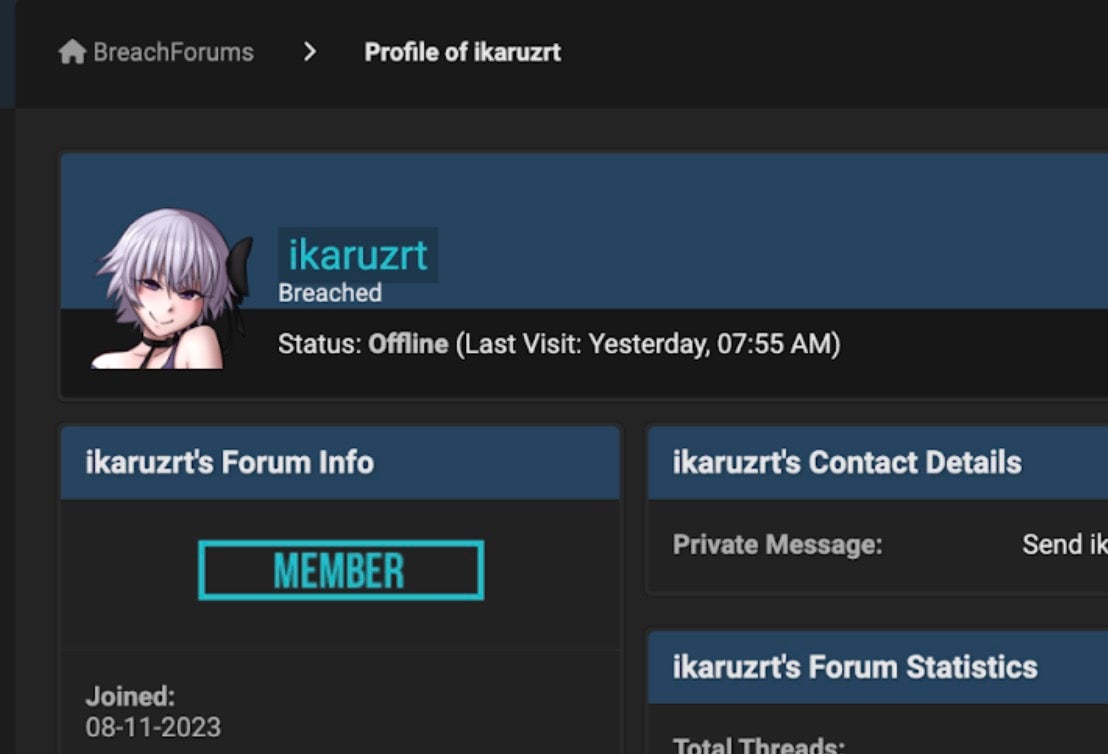
These postings on BreachForums include a September 2023 post advertising the breach of Yakult Philippines Incorporated. This appears to be a repost of data listed on Cl0ps data leak site in July 2023.
A related Ikaruz Red Team GitHub repository was created in mid-2023 and has historically contained code for webshells and defacement tools featuring 403/404 error code bypass features. Note that the co-opted Hack4Gov imagery extends to this platform also.

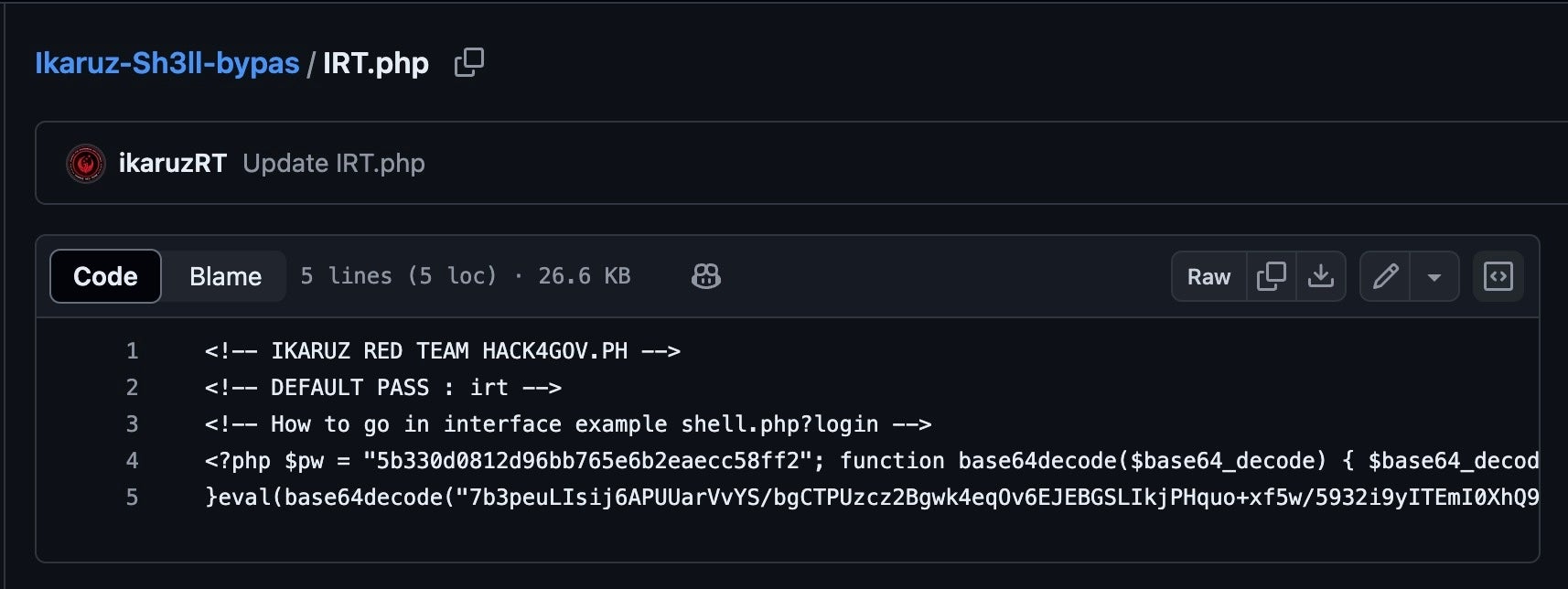
Across the group’s social media footprint, IRT claims affiliation or alignment with other hacktivist groups, in particular Anka Red Team, Anka Underground Team and Turk Hack Team.

Turk Hack Team, established in 2004, is a prolific, Turkish-aligned, hacktivist group known primarily for website defacements and DDoS attacks, including the mass-defacement of nearly 3000 Dutch websites in the “Netherlands Operation” and the notable DDoS attack against Crédit Agricole. Under the banner of “Anka Red Team”, this hacktivist collective has drawn more attention since the onset of the Israel-Hamas war through its support of Palestinian group Hamas.
Conclusion
Politically-motivated attacks targeting the Philippines have been on the rise, especially in the last year. Individual actors like Ikaruz Red Team aligning themselves with previously known groups such as Turk Hack Team and PHEDS are becoming increasingly destructive in their actions.
This destruction, ranging from government data breaches to small-scale ransomware attacks, is being facilitated by the open availability of leaked ransomware builders such as LockBit and ready-to-go scripts for DDoS attacks and web defacements.
For hacktivists, ransomware serves an entirely different purpose from that of financial gain, aiding instead their desire to cause disruption and make political statements against those they consider enemies or those who are deemed to be supporters of these perceived enemies.
Within the hacktivist landscape, Ikaruz Red Team fits into a larger movement of threat actors committing unsophisticated yet damaging attacks targeting the Philippines region. There is indication that a broader cluster of these behaviors may be part of rising regional tensions with China and a desire to destabilize Philippine critical infrastructure.
Indicators of Compromise
| SHA1 | Description |
| 133388ea2bd362993198bba461c7273a2a3af1ec | ransom note |
| 2454820aef7c6289af85758df89976718013a5a4 | ransom note |
| 267ed8df557c41cd322d4ed5dd1764018c74f611 | ransom note |
| 41b2e3f0ddb3ceef2cddb09ca9edf4334461720c | webshell (github) |
| 57cc1ef9f762b1db9999772356cd8e6a70cb9964 | ransom note |
| 5b830b5d5577ad8186e9ba4f7fdeee0b32c535e3 | test.php |
| 8596a6bb124e56f6d545b77e74c3b23f6f578f55 | RED.ico |
| 8bc4fadf5a929103b0c25c5f2f02da9c9ca67a1f | ransom note |
| a379e55be365ece1ca2b8f72b6c54bb8b5bfe4e9 | lb3.exe |
| b65183cc886185a8c34860f68d3289d8e9dd84e3 | LockBit 3.0 (Ikaruz Red Team) |
Singularity™ Platform
Singularity™ enables unfettered visibility, industry-leading detection, and autonomous response. Discover the power of AI-powered, enterprise-wide cybersecurity.
如有侵权请联系:admin#unsafe.sh