
On April 26, 2024, SentinelOne marked a significant milestone in security management with the launc 2024-5-14 21:0:16 Author: www.sentinelone.com(查看原文) 阅读量:11 收藏
On April 26, 2024, SentinelOne marked a significant milestone in security management with the launch of the Singularity Operations Center, the new unified security console. This major update to the Singularity Platform is now generally available (GA) to all cloud-native customers, representing a pivotal shift to a more integrated and efficient analyst experience for security teams.
This blog post introduces the many features of Operations Center and delves into how it centralizes security management with unified alerts, asset inventory management, a correlation engine, and our contextualized Singularity Graph to accelerate detection, triage, and investigation. Operations Center significantly boosts analyst productivity with enterprise-wide visibility and control, setting a high standard against other vendors with fragmented systems.

One Console, One Platform
Implementing disconnected tools for different attack surfaces and use cases has led to complex navigation, operational inefficiencies, and less visibility across security ecosystems. Using disparate tools has also generated data spread across multiple consoles, forcing analysts to continuously context switch and making it more difficult to understand their whole security landscape. Together, these pain points detract security teams from their ability to focus on everyday tasks while also creating slower, error-prone, and more manual triage and investigation processes. We built the Singularity Platform and Operations Center to help eliminate noise and workflow disruptions while providing best-in-class protection for organizations everywhere.
The Singularity Platform is an AI-powered cybersecurity platform with one console and one data lake for a truly unified experience. We worked closely with over 200 organizations to ensure the design of Operations Center prioritizes and empowers security analysts, threat hunters, security administrators, incident responders, and SOC managers, considering their everyday tasks through workflow-based navigation. Through our Design Partner Program, our active users, ranging from advanced to early-career analysts across different industries, play a vital role in the product development process to ensure our improvements enhance the overall analyst function.
Gain End-to-End Visibility and Control
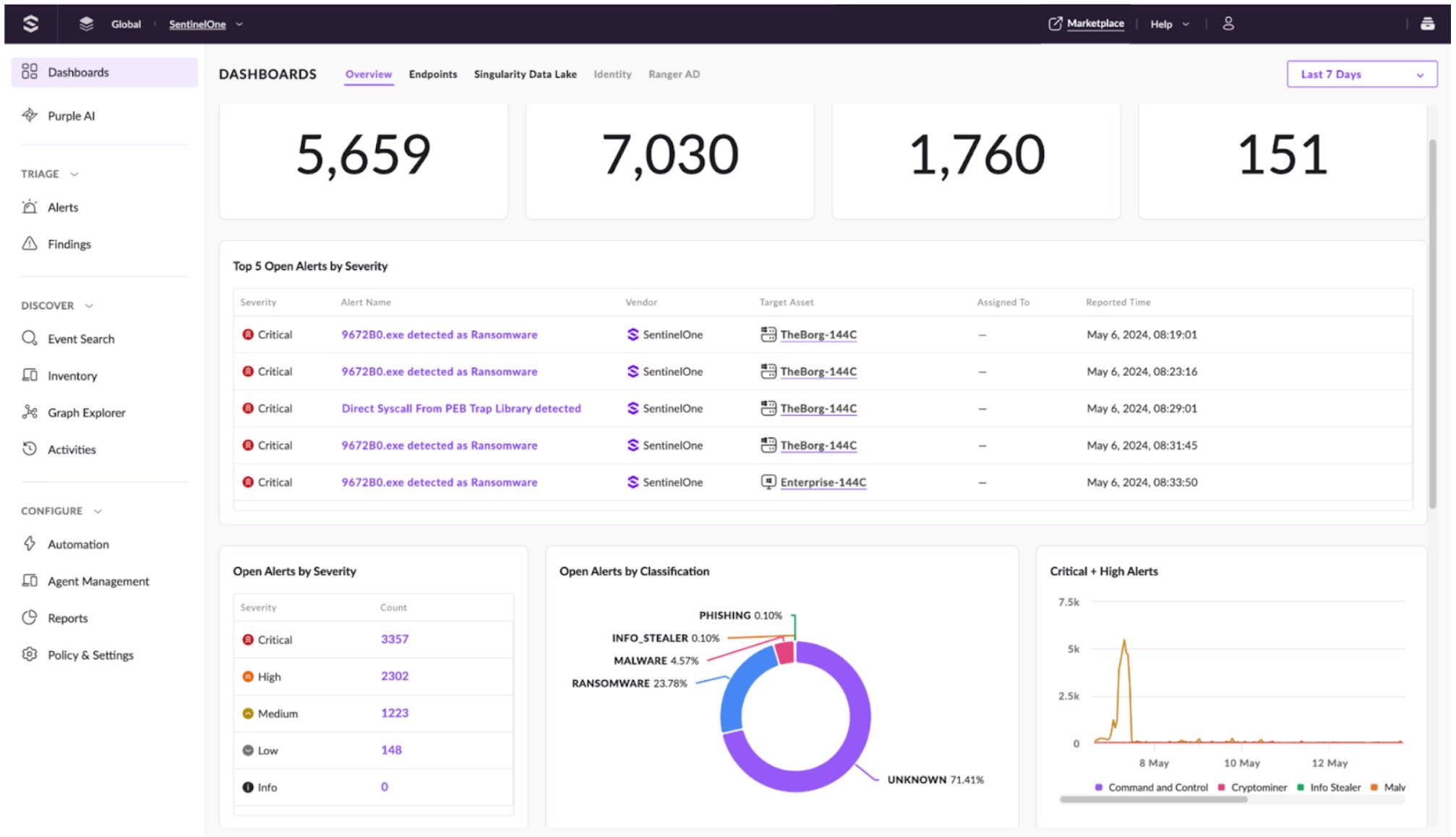
One of the core philosophies of Operations Center is centralization. Consolidating security operations through intuitive and integrated design provides a single view across the enterprise. The new unified alert management page enables security teams to conduct faster and more comprehensive investigations by managing and responding to security alerts in one location.
Without pivoting to multiple tabs and consoles, analysts benefit from a single queue comprised of alerts from SentinelOne native solutions in addition to ingested partner alerts. Customers can use Singularity Marketplace to ingest alerts from industry-leading partner solutions, such as Proofpoint TAP, ExtraHop Reveal(x), Microsoft Defender Suite, Palo Alto Firewall, and more. By understanding the full scope of an alert and its attributes, such as severity level, event indicators, origin, and more specific details, users can facilitate rapid response and surface holistic insights.
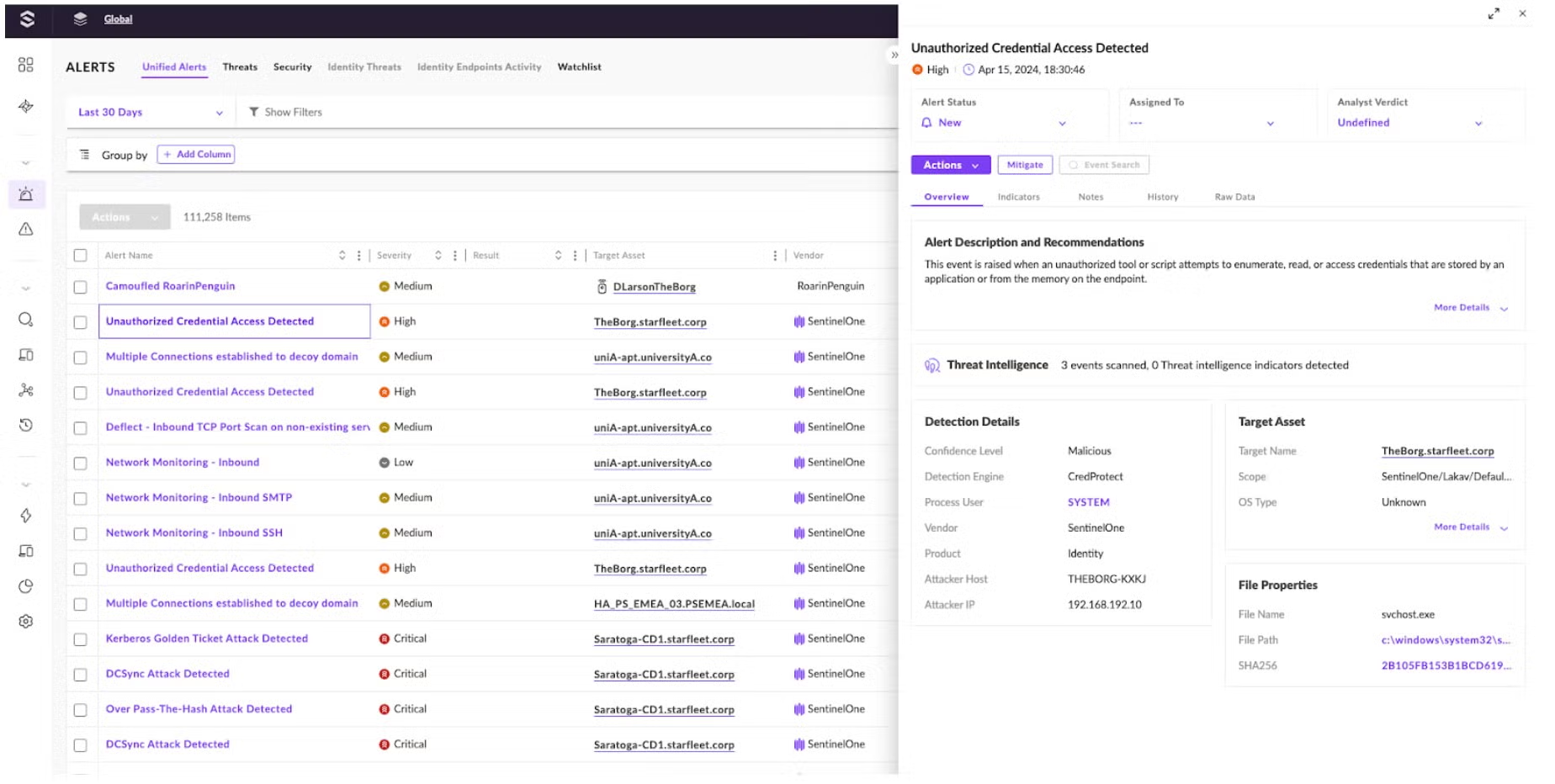
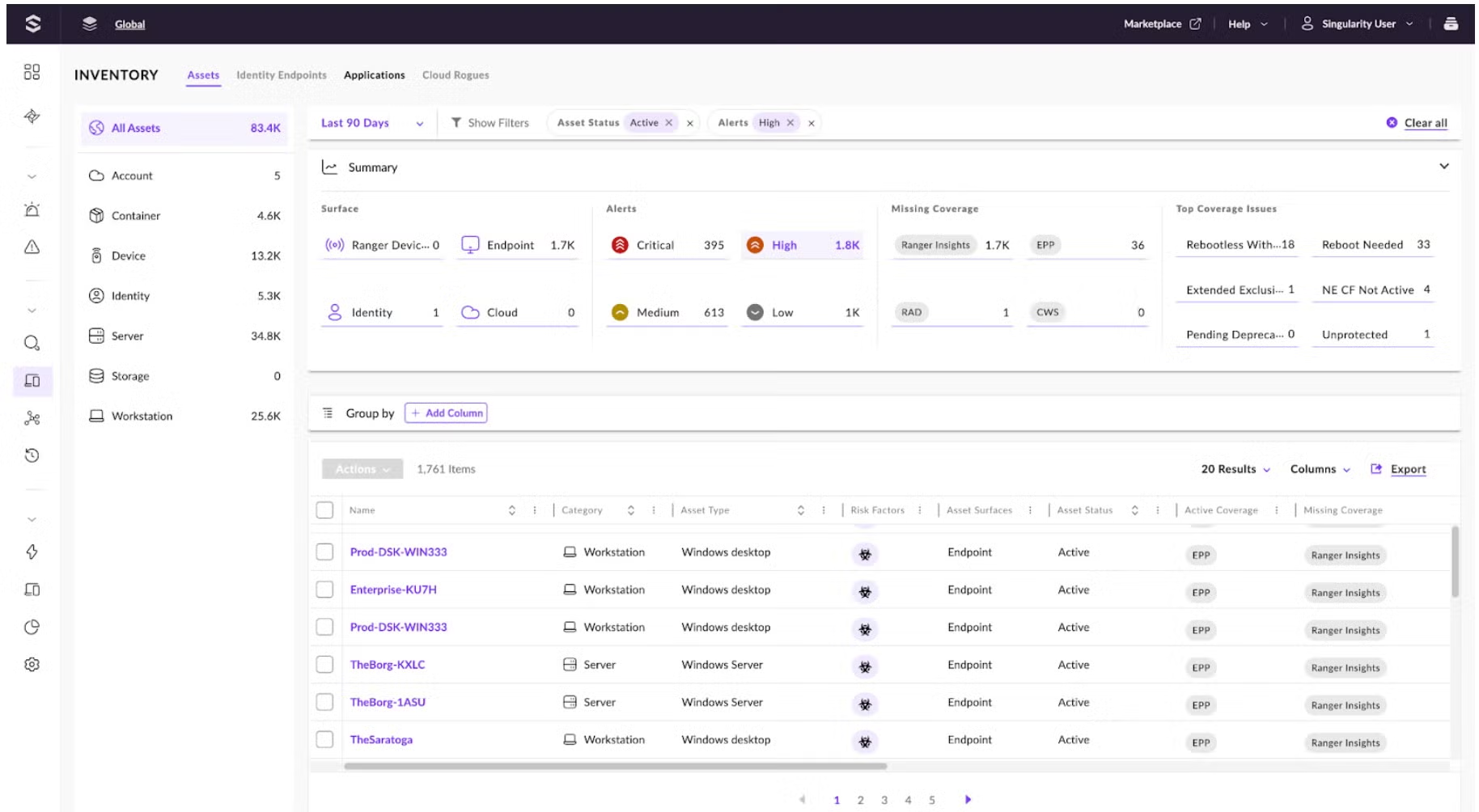
Organizations also require deep insight into all the assets in their environment to fully understand their attack surface, identify coverage gaps, and reduce potential risks. In the Operations Center, security teams can now centrally oversee and manage all assets in a unified inventory, which includes managed endpoints, cloud resources, identity assets, and network-discovered devices. To accelerate triage and investigation, analysts have access to an up-to-date inventory page that contains essential asset properties for easy review, criticality assignment, organizational tagging, and direct actions, such as initiating security scans.
Accelerate Detection, Triage, and Investigation
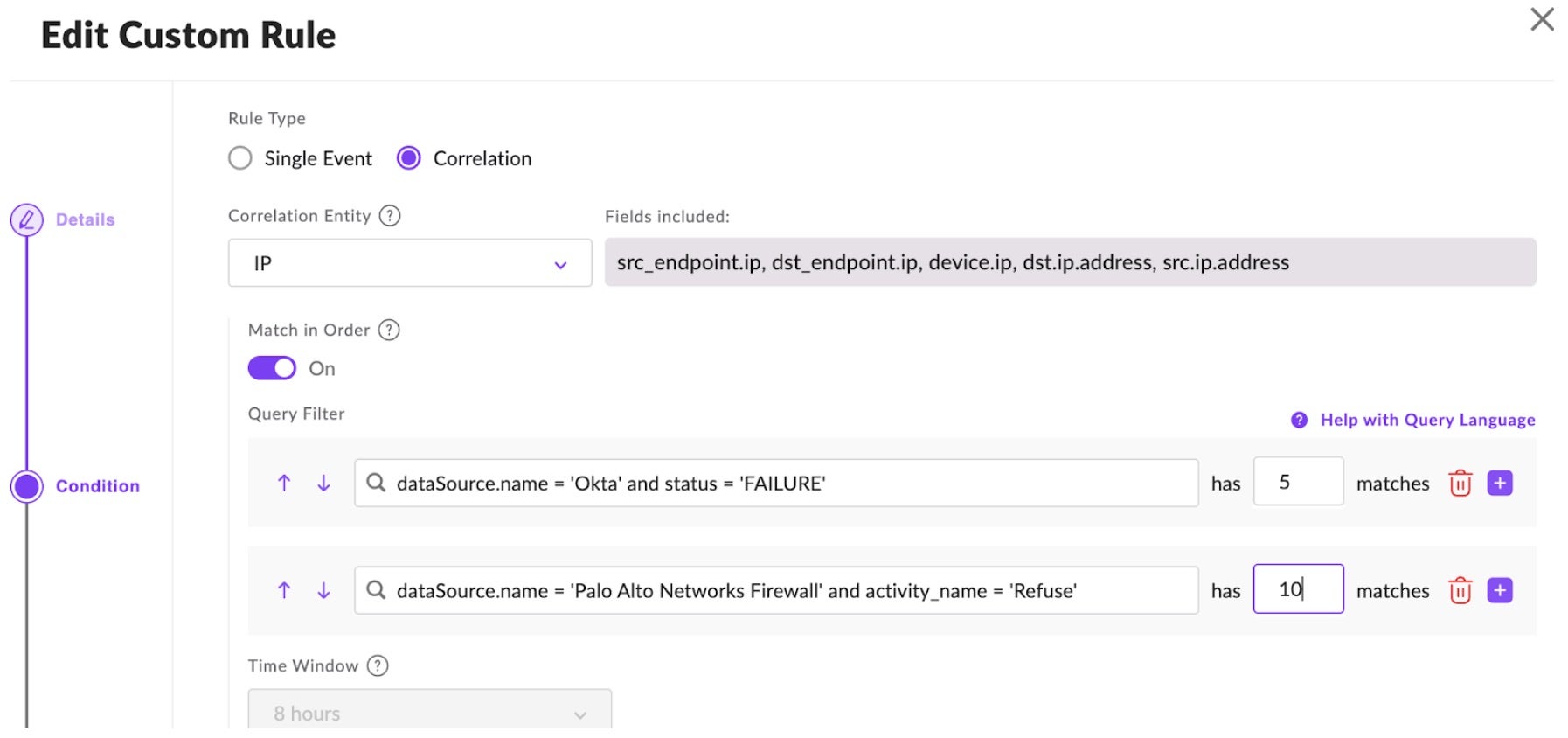
SentinelOne’s goal with Operations Center is to optimize efficiency at every stage of the analyst experience, from preparation and detection to recovery. We are introducing our new correlation engine to help detect complex cyber threats earlier and in real time, preventing breaches and minimizing damage. It correlates activities from multiple data sources and events and identifies patterns that indicate malicious intent to generate a more detailed and reliable alert. The correlation engine saves time and accelerates triage and investigation for analysts, eliminating the need to manually search through thousands of logs to validate specific criteria.
When investigating a potential threat, users now benefit from our Singularity Graph, an interactive graph that correlates and contextualizes security alerts and assets. Analysts can write their own queries or leverage the graph library for out-of-the-box queries to conduct faster investigations. The visual graphs enable the discovery of deeper contextual insights with a visual representation of the relationship between threats and their connections to assets currently in the organization. Users can easily click on any asset or alert for more detailed information and quickly take action to mitigate threats.
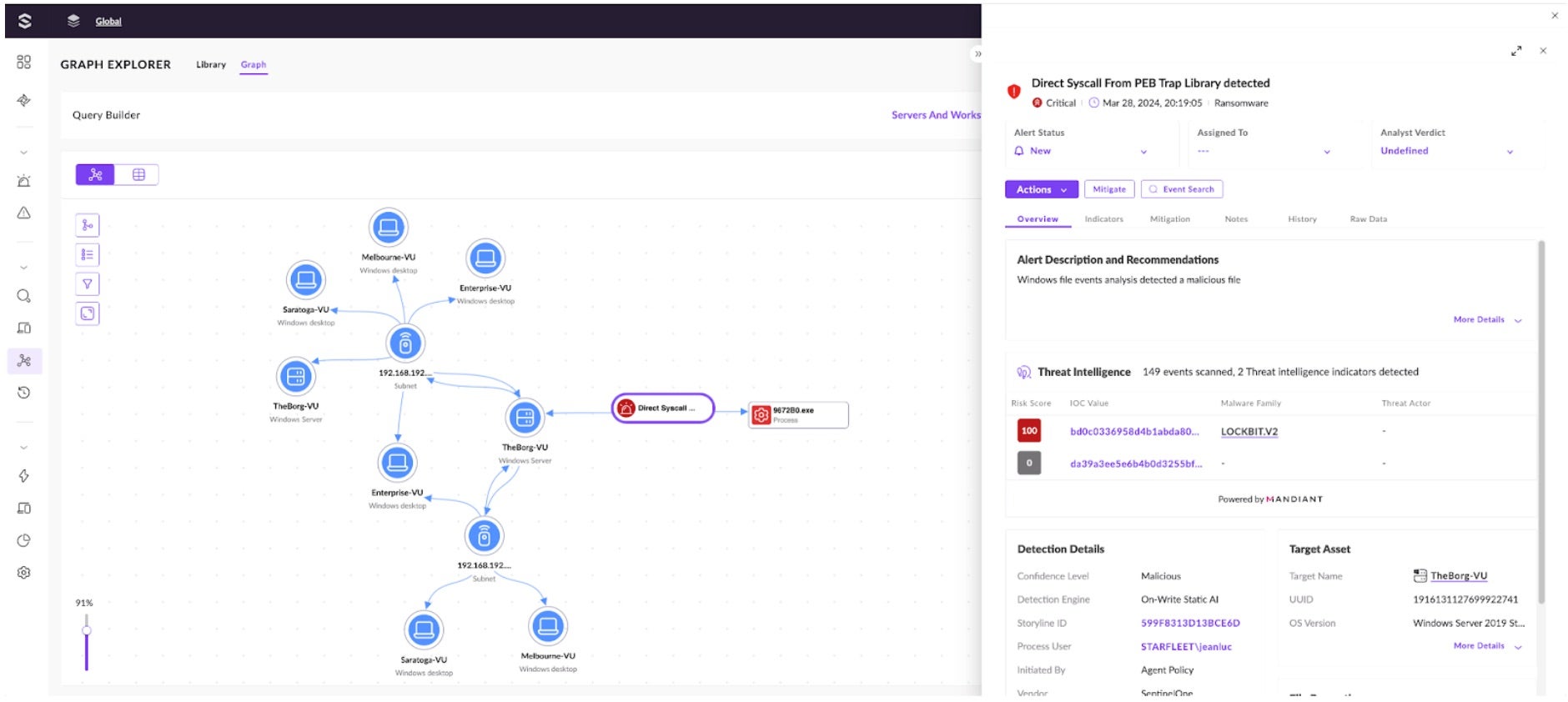
Singularity Operations Center is a testament to our commitment to delivering the most advanced AI-powered security platform:
- Consolidate Security Operations – Centralize workflows through integrated and intuitive design for complete visibility and control across the enterprise, including workplace and cloud environments.
- Streamline Incident Response – Accelerate detection, triage, and investigation with contextual insights for rapid response and risk reduction.
- Simplify Configuration Management – Improve productivity and save time by efficiently managing configuration, settings, and policies from one location.
Enable Now to Elevate Security Operations
The Singularity Operations Center is Generally Available to current cloud-native customers as an opt-in toggle. Existing customers can visit the Customer Portal to learn how to enable the new console and navigation.
Learn More
Not a customer, but want to see more? Meet our team for a demo to see how you can get started with the Singularity Platform, or visit our self-guided product tours.
Singularity Platform
Singularity™ enables unfettered visibility, industry-leading detection, and autonomous response. Discover the power of AI-powered, enterprise-wide cybersecurity.
如有侵权请联系:admin#unsafe.sh