Recently, we held a talk at the Winterkongress1 of the Digitale Gesellschaft Schweiz in Winterthur, Switzerland, about our research project on breaking German parcel tracking sites. We could not name all the parcel services for which we identified vulnerabilities respecting disclosure timelines. Today, we describe our findings at GLS, another player in the German parcel market, and the disclosure process of corresponding vulnerabilities.
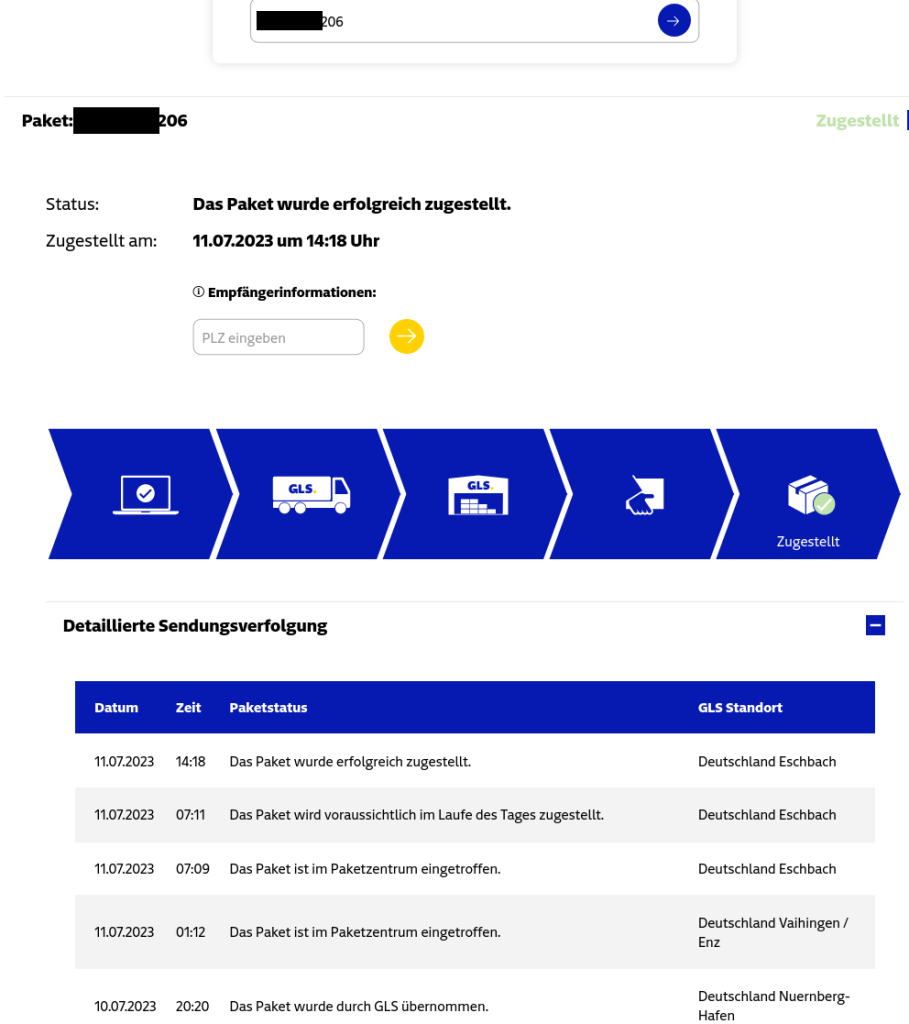
Similar to the vulnerabilities previously disclosed for DHL2 and DPD3, and UPS4, we identified that the GLS parcel tracking website discloses the recipient’s geographic area by showing the name of the destination parcel center. Furthermore, the recipient’s ZIP code was used to unlock personal information (including the exact coordinates of the address) and features that influence the parcel delivery process. The website did not implement rate-limiting or other techniques to prevent brute-forcing ZIP codes using the API.
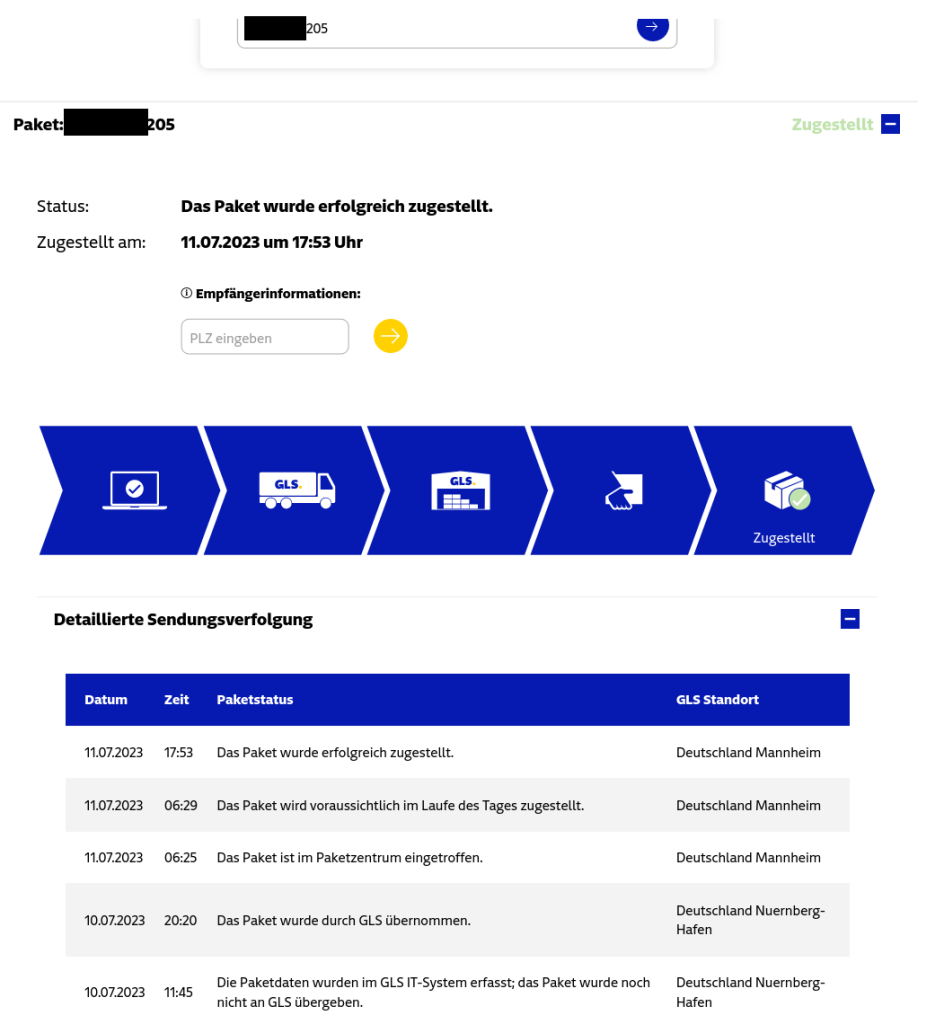
Because of the geographic hint, the number of ZIP codes could be limited to a small set of potentially valid ones, and due to missing measures preventing brute force, sending requests to the GLS API to find the valid ZIP code was possible. On average, a GLS parcel center covers 136 ZIP codes, while (again, on average) the 30 most populous ZIP codes are home to 50% of the population the parcel center serves. Our Python script sent six requests per second as proof of concept and identified many valid ZIP codes within 5 seconds (per tracking number) as the GLS tracking numbers are generated predictably.
Attackers with access to one valid tracking number, e.g., of a parcel sent by a web shop, can count upwards or downwards to find valid tracking numbers of parcels sent to other customers. Therefore, targeting customers of certain businesses is straightforward.
After providing the vulnerability information via the published security contact on their web page, GLS invested time in vulnerability analysis including approaches for fixes and mitigations, and a possible remediation timeline. This did not include only fixes for the communicated vulnerabilities but also included redesigning the interfaces and APIs for customers and subcontractors. ERNW extended the disclosure period to pay respect to Christmas time and corresponding loads in parcel shipping. Throughout the disclosure process starting in September 2023, until March 2024, GLS provided multiple status updates about the work on fixes in progress in monthly video conference meetings. We would like to thank GLS for the smooth disclosure process and the close cooperation.
- September 05, 2023: Initial contact to GLS, start of 90-day disclosure period.
- September 11, 2023: Initial response by GLS, ERNW provides detailed vulnerability information.
- November 01, 2023: Coordination of a first status meeting.
- November 14, 2023: Coordination Meeting: GLS presents a vulnerability analysis, approaches for fixes and mitigations, and a remediation timeline. ERNW extends the disclosure period.
- December 12, 2023: Coordination Meeting: Progress of mitigations and fixes.
- January 16, 2024: Coordination Meeting: Progress of mitigations and fixes.
- February 13, 2024: Coordination Meeting: Start of implementation and rollout of fixes by GLS.
- March 12, 2024: Coordination Meeting: Updates in implementation and rollout.
- April 16, 2024: Coordination Meeting: Coordination of disclosure.
- April 25, 2024: Public disclosure of findings by ERNW.
Cheers!
Dennis Kniel & Florian Bausch
For more insights into IT security and meeting awesome people from the field, don’t miss #TROOPERS24 conference in Heidelberg from June 24th to June 28th, 2024!
- Ich weiß, was du letzen Sommer bestellt hast. Online: https://winterkongress.ch/2024/talks/ich_wei_was_du_letzten_sommer_bestellt_hast/↩︎
- All your parcel are belong to us – Talk at Troopers 2023. Online: https://insinuator.net/2023/07/all-your-parcel-are-belong-to-us-talk-at-troopers-2023/↩︎
- Breaking DPD Parcel Tracking. Online: https://insinuator.net/2023/09/breaking-dpd-parcel-tracking/↩︎
- Breaking UPS Parcel Tracking. Online: https://insinuator.net/2024/04/breaking-ups-parcel-tracking/↩︎
