2024-4-23 19:4:30 Author: securityboulevard.com(查看原文) 阅读量:4 收藏
Applications are the workhorses of your business, but imagine the chaos if their communication channels, the APIs were compromised. Today, APIs (Application Programming Interfaces) are the hidden doorways through which 83% of web traffic flows. These vital connections power your apps, but a weak API is like a cracked foundation. It can bring your whole system down. When was the last time you scanned your APIs for security vulnerabilities? If the answer’s a shrug, it’s time to ditch the stress and embrace offensive security.
Did you know, 94% of organizations had security issues with their production APIs? Even worse, one in five suffered a data breach because of those gaps.
Don’t let these numbers keep you up at night. WeSecureApp’s API Penetration Testing Checklist is your step-by-step guide to identifying and fixing those API weaknesses before attackers exploit them.
One untested vulnerability is all it takes for a cyberattack to wreak havoc. Our checklist empowers you to take control and prevent a disaster.
Are You Making These API Penetration Testing Mistakes?
- Rushing to Market: Skipping through API Pentesting to meet deadlines can leave critical security gaps exposed.
- Focusing on Functionality Only: Just because your API works doesn’t mean it’s secure. Malicious actors can exploit even minor flaws.
- Failing to Test Error Handling: What happens when your API receives unexpected data? Unhandled errors can be a hacker’s playground.
- Inconsistent Testing: Ad-hoc Pentesting is unreliable. You need a structured approach to ensure comprehensive coverage.
Why is Robust API Penetration Testing Crucial?
Consider these scenarios:
- A malicious actor discovers an API endpoint that allows unauthorized access to customer data.
- A poorly coded API call leads to a denial-of-service attack, crippling your application’s functionality.
- An API doesn’t properly validate user input, opening the door to injection attacks.
These are just a few examples of the potential consequences of inadequate API Pentesting. By proactively identifying and addressing these vulnerabilities, you can:
- Safeguard sensitive data: Ensure customer information, financial data, and intellectual property remain secure.
- Maintain application uptime: Prevent disruptions caused by API exploits.
- Boost user confidence: Demonstrate your commitment to data security and build trust with your customer base.
- Mitigate regulatory risks: Comply with industry regulations and avoid hefty fines.
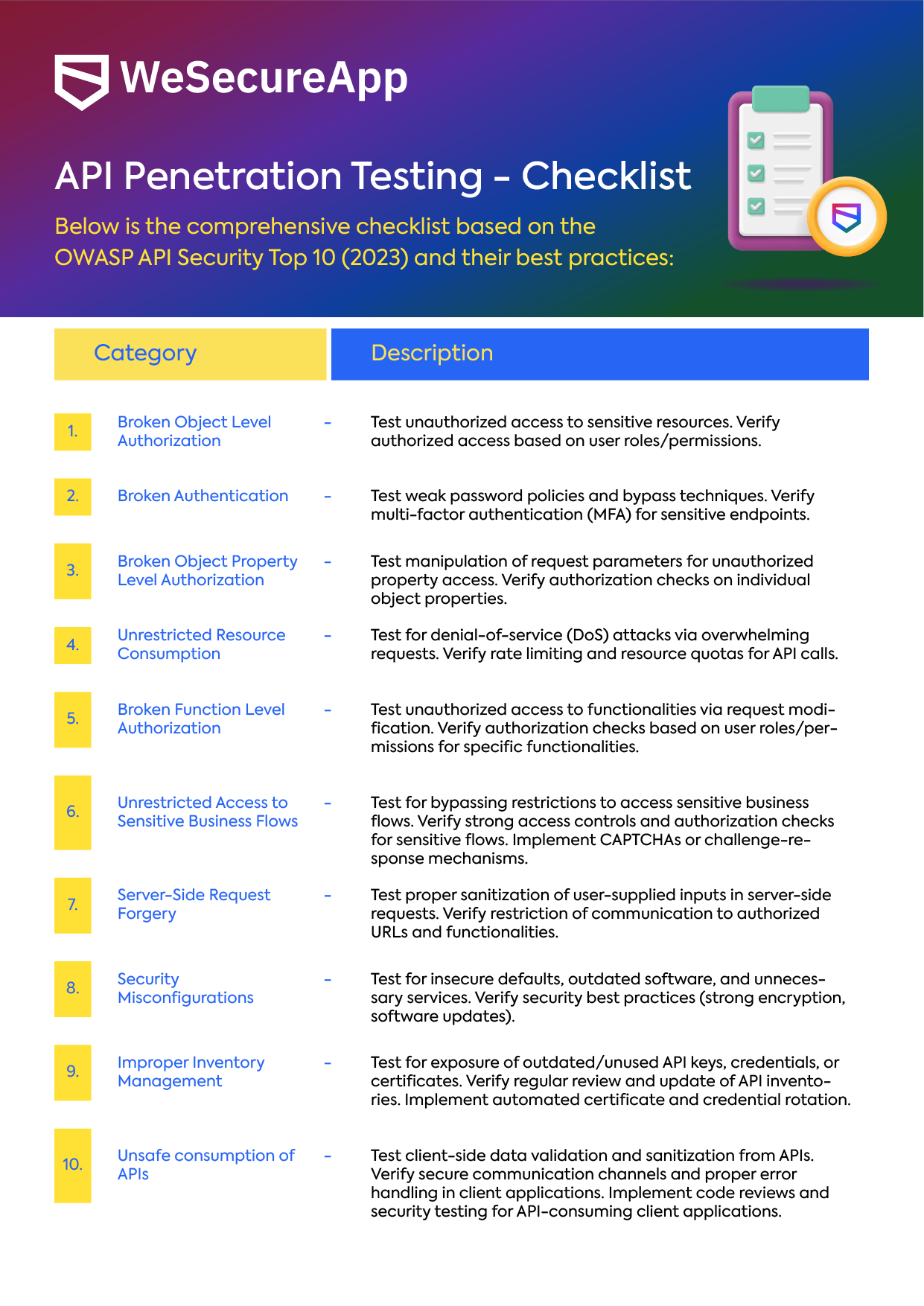
WeSecureApp’s API Penetration Testing Checklist
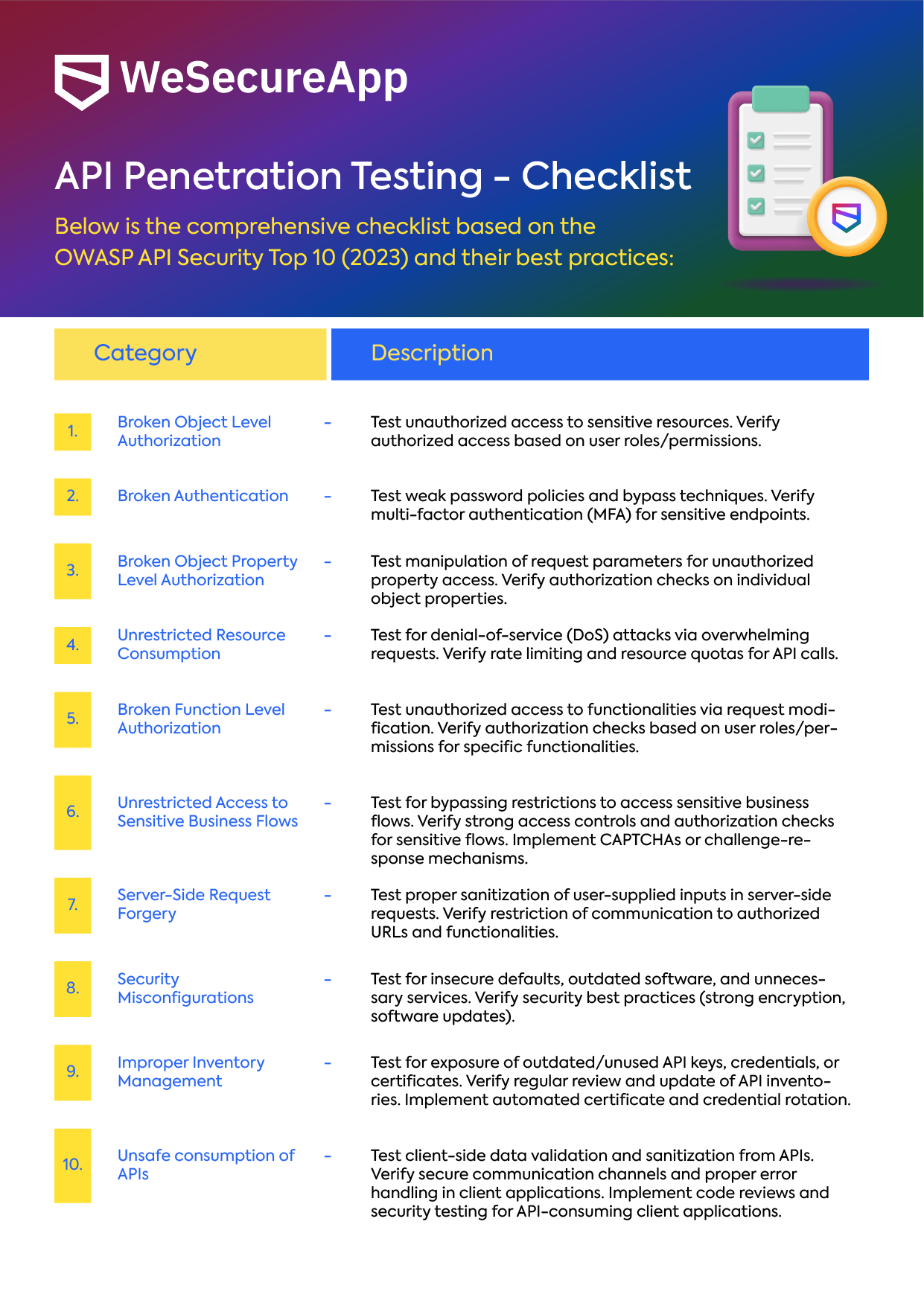
1. Broken Object Level Authorization (BOLA)
Broken Object Level Authorization (BOLA) is a critical vulnerability to check during API penetration testing. It occurs when an application fails to properly verify a user’s access rights for specific data objects. This can allow attackers to manipulate identifiers within requests and access unauthorized information or perform actions they shouldn’t be able to.
Here’s how to test for BOLA:
- Identify Object Identifiers: Analyze API requests and responses to pinpoint elements that uniquely identify data objects. These could be IDs in URLs, request parameters, or the response body itself.
- Tamper with Identifiers: Craft test cases where you modify the identified object identifiers in requests. Try incrementing sequential IDs, altering UUIDs, or even making educated guesses about valid identifiers.
- Verify Access Control: Observe the application’s response to these modified requests. If you gain unauthorized access to data or can perform unauthorized actions, it signifies a BOLA vulnerability.
Example:
Imagine an API endpoint that allows users to view their own account information using a unique user ID in the request URL. A BOLA test would involve modifying the user ID to see if you can access information belonging to other users.
2. Broken Authentication
Broken authentication is a critical vulnerability in APIs, allowing unauthorized access to sensitive data and functionality.
Here’s how to test for broken authentication:
A. Credential Strength and Rate Limiting:
- Test password complexity requirements:
- Can users create weak passwords (e.g., dictionary words, short lengths)?
- Does the API enforce password complexity policies?
- Check for brute-force protection:
- Is there a limit on login attempts within a timeframe?
- Does the API implement account lockouts after a certain number of failed attempts?
B. Session Management Flaws:
- Test session timeout:
- How long does a session remain active after login?
- Check for session hijacking:
- Can an attacker steal a valid session ID and gain access to the user’s account?
C. Authentication Mechanism Testing:
- Test for weak authentication methods:
- Does the API rely solely on basic authentication (username/password) without additional security layers (e.g., two-factor authentication)?
- Check for API key vulnerabilities:
- Are API keys easily guessable or stored insecurely?
- Can an attacker exploit weak key management practices?
D. Additional Tests:
- Test for forgotten password vulnerabilities:
- Can an attacker reset passwords without proper verification?
- Check for authorization bypasses:
- Can an attacker access unauthorized resources by manipulating authentication tokens or exploiting logic flaws?
Example:
Imagine an API that allows users to manage their finances. If this API only uses basic authentication with no password complexity requirements or rate limiting, an attacker could easily launch a brute-force attack to guess user credentials and gain access to sensitive financial data. By following these steps and identifying broken authentication vulnerabilities, you can significantly improve the security of your API.
3. Broken Object Property-Level Authorization
This vulnerability arises when applications grant access to specific data objects but fail to enforce granular permissions on individual properties within those objects. This allows attackers to manipulate or access sensitive information they shouldn’t be able to.
Here’s how to test for Broken Object Property-Level Authorization:
- Identify Data Objects: Analyze the API documentation and responses to understand the structure of data objects. Look for objects containing a mix of public and sensitive properties (e.g., user object with name, email, and admin flag).
- Test Property Access: Craft API requests that target individual properties. Try modifying properties you shouldn’t have access to (e.g., attempting to change another user’s email address).
- Analyze Response: Observe the application’s response. If unauthorized modifications succeed or sensitive information is revealed, the application might be vulnerable.
Example:
Imagine an e-commerce API allows users to update their profile information. A standard request might include name, address, and phone number. However, the API might also contain a hidden property for “account_type” (e.g., regular user or administrator). By testing modifications to this property, an attacker could potentially exploit a vulnerability and elevate their privileges.
4. Unrestricted Resource Consumption
An API, like any application, consumes resources like CPU, memory, and network bandwidth when processing requests. Unrestricted resource consumption occurs when an API lacks mechanisms to limit or control these resources efficiently. This can be exploited by attackers to launch Denial-of-Service (DoS) attacks, significantly impacting performance and potentially causing outages.
Testing for Unrestricted Resource Consumption:
- Request Volume: Send a large number of concurrent requests to an endpoint and monitor server response times. Look for significant delays or timeouts indicating potential resource exhaustion.
- Request Complexity: Craft requests with complex payloads or parameters requiring extensive processing. Analyze server response times and resource usage to identify if complex requests overwhelm the system.
- Data Exfiltration: Test endpoints that return large datasets. If no limits are in place, attackers could potentially download massive amounts of data, consuming bandwidth and storage resources.
- Brute-forcing: If authentication endpoints lack rate limiting, send a high volume of login attempts with various credentials. This can overload login processes and consume unnecessary resources.
Example:
An e-commerce API allows customers to search for products. The search functionality takes a user-defined search term as input. An attacker could exploit this by sending requests with extremely long or complex search strings. Processing such requests might require significantly more resources than intended, potentially impacting the performance of other API functionalities.
5. Broken Function Level Authorization
Applications with APIs (Application Programming Interfaces) often rely on a system that grants access based on user roles or permissions. Broken Function Level Authorization (BFLA) occurs when this system is flawed, allowing unauthorized access to specific functionalities within the API.
What to Look For:
- Inconsistent Permission Checks: Verify if authorization checks are applied consistently across all API endpo3
- fbv+ints. Inconsistent checks might allow unauthorized users to access functionalities meant for administrators by manipulating requests.
- Predictable Endpoints: Analyze API endpoint URLs or parameters for predictable patterns. Attackers might exploit these patterns to access unauthorized functions by slightly modifying their requests.
- HTTP Method Tampering: Test if changing the HTTP method (e.g., from GET to DELETE) in an API request bypasses authorization checks and allows unauthorized actions.
Example:
An e-commerce API allows registered users to view their order details (GET request to /orders/<order_id>). However, deleting orders is restricted to administrators. If the authorization check only considers user role for modifying order details, an attacker could potentially exploit this vulnerability:
- The attacker sends a GET request to view order details (authorized action).
- They observe the format of the URL, noticing it includes the order ID.
- The attacker modifies the request, changing the HTTP method to DELETE and keeping the same URL structure with a specific order ID.
If the API lacks proper authorization checks for the DELETE method, the attacker might be able to delete an order despite not having administrator privileges.
6. Unrestricted Access to Sensitive Business Flows
During an API penetration test, scrutinize how the API handles critical business processes. These processes could involve financial transactions, inventory management, or user data manipulation. The goal is to identify situations where an attacker could exploit weak access controls and manipulate these flows for malicious gain.
Here’s how to test for this vulnerability:0
1. Identify Sensitive Endpoints: Look for API endpoints that manage critical business functions like adding to carts, processing payments, or modifying user data.
2. Test Authentication: Verify that strong authentication mechanisms are in place to restrict access to these endpoints. This could involve multi-factor authentication or API keys with granular permissions.
3. Examine Rate Limiting: Ensure rate limits are implemented to prevent excessive calls to sensitive endpoints. This can thwart attempts to automate attacks like the shopping cart example.
Example:
Let’s consider an e-commerce API. An attacker might discover an endpoint that allows adding unlimited items to a shopping cart without proper authentication or rate limiting. By exploiting this vulnerability, the attacker could programmatically add all available items to their cart, essentially taking them off the market and potentially disrupting sales.
7. Server-Side Request Forgery (SSRF)
SSRF vulnerabilities can be exploited by attackers to trick a web application’s server into making unintended requests. These requests can target internal resources or even external systems.
Here’s how an SSRF attack might unfold:
- Exploitable Feature: The application has a feature that fetches data from user-supplied URLs. This could be for fetching weather information, retrieving images, or updating product details based on a URL.
- Malicious Input: An attacker injects a crafted URL into the user input field. This URL could point to an internal server or even a malicious external site.
- Server Makes Request: The application, unaware of the manipulation, uses the server to fetch data from the attacker-provided URL.
- Attacker Gains Access: Depending on the target URL, the attacker might be able to:
- Internal Server Access: Reach internal systems that are typically hidden behind firewalls. This could expose sensitive data or allow further attacks within the network.
- External System Attack: Launch attacks against external systems that the application server can access.
Example:
An e-commerce application allows users to submit product image URLs. An attacker uploads a URL that points to a file on the server itself (e.g., http://localhost/internal/config.txt). If the application has an SSRF vulnerability, the server might fetch the file, potentially exposing sensitive configuration details to the attacker.
8. Security Misconfigurations
Security misconfigurations are a common vulnerability in APIs. They arise from mistakes or oversights during setup, deployment, or ongoing maintenance. These errors can expose sensitive data, grant unauthorized access, or disrupt API functionality.
Here’s what to look for during penetration testing:
- Unnecessary Services: Are there services running that the API doesn’t require? These can create a larger attack surface for malicious actors.
- Outdated Software: Unpatched vulnerabilities in the API server, libraries, or supporting systems can be exploited. Ensure all software is updated regularly.
- Improper Permissions: Are user permissions correctly configured? Weak permissions can allow unauthorized users to access or manipulate data.
- Missing or Weak Encryption: Is communication between the API and clients encrypted with strong protocols like TLS? Weak encryption can expose data in transit.
- Insecure Error Messages: Do error messages reveal sensitive information like stack traces or internal system details? This can provide attackers with valuable clues for further exploitation.
- Misconfigured CORS Policy: A poorly configured Cross-Origin Resource Sharing (CORS) policy might allow unauthorized domains to access the API.
By identifying and addressing these misconfigurations, you can significantly improve the security posture of your API.
Example:
During testing, the penetration tester discovers an API endpoint running a debug mode that exposes internal system details. This misconfiguration could allow an attacker to understand the underlying architecture and identify potential vulnerabilities for exploitation.
9. Improper Asset Management
A complete and accurate list of all APIs within an organization is crucial for effective security. Improper inventory management can leave hidden vulnerabilities exposed. Here’s how to test for this issue:
Checklist:
- Discover Unlisted APIs: Utilize tools like web scanners and fuzzing techniques to identify undocumented endpoints.
- Verify Documentation Accuracy: Compare documented functionalities to actual behavior of the API. Look for discrepancies or missing information.
- Test for Deprecated Versions: Attempt to access and interact with older API versions that may still be functional but not officially supported.
- Identify Shadow APIs: Look for internal APIs used by specific applications that might not be listed in the central inventory.
Example:
A company uses a shopping cart API documented to accept only product IDs and quantities. During testing, a pentester discovers an undocumented parameter that allows adding arbitrary data to customer orders. This could be a vulnerability if the additional data isn’t properly sanitized and validated.
10. Unsafe Consumption of APIs
Many applications rely on external APIs to function. However, if these APIs are not consumed securely, it can introduce vulnerabilities into your application. This checklist point focuses on identifying weaknesses in your application’s interaction with external APIs.
Here’s what to consider:
- Improper Input Validation: Are you properly validating all data sent to external APIs? Malicious actors can inject code or manipulate data to exploit weaknesses in the API. Ensure your application validates and sanitizes all user input before passing it on.
- Weak Authentication and Authorization: How does your application authenticate with external APIs? Are strong passwords or tokens used? Does your application only request the minimum permissions necessary? Weak authentication or authorization can allow attackers to gain unauthorized access to sensitive data or functionality through the API.
- Insecure Communication Channels: Is communication with the external API encrypted (HTTPS)? Unencrypted communication can allow attackers to intercept data, including sensitive information like passwords or credit card details.
- Outdated Dependencies: Are you using the latest versions of any external libraries or frameworks that interact with APIs? Outdated software may contain known vulnerabilities that attackers can exploit.
Example:
An e-commerce application integrates with a payment processing API to handle customer transactions. The application fails to validate the amount field before sending it to the payment API. An attacker could exploit this by injecting a negative value, resulting in the application crediting their account instead of processing the payment.
WeSecureApp: Your Partner in Building Secure Applications
API penetration testing is an essential step in shoring up your organization’s API security posture. By following a comprehensive API Penetration Testing Checklist, you can identify and address vulnerabilities before they’re exploited by attackers.
WeSecureApp’s team of Pentesters can help you conduct a thorough penetration test and ensure your APIs are locked down tight. We’ll not only identify vulnerabilities but also provide actionable remediation steps to get your APIs battle-ready.
Why wait? Don’t let a single untested weakness become the open door to disaster. Contact WeSecureApp for a free consultation!
Recommended Reading
How to Intercept Traffic from Proxy Unaware Application Using DNSChef
Penetration Testing Across Industries: Requirements and Assessment Scope
Security and Penetration Testing for Banking & Finance Companies
The post The Only API Penetration Testing Checklist You Need appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Shubham Jha. Read the original post at: https://wesecureapp.com/blog/the-only-api-penetration-testing-checklist-you-need/
如有侵权请联系:admin#unsafe.sh
