
2024-4-23 05:36:39 Author: securityboulevard.com(查看原文) 阅读量:0 收藏

Y Combinator's investments in cybersecurity, privacy, and trust startups came back to earth a bit in their latest Winter 2024 (W24) batch. At Demo Day earlier this month, six companies from the ecosystem were showcased — well below the peak of 19 companies in the W22 batch.
I pay close attention to Y Combinator and its cybersecurity-related companies because they're a tastemaker for the entire tech industry. Sure, we can debate industry-specific things like their level of specialization or track record of success, but you can't downplay or ignore their dominance as early stage investors across tech.
I've covered every YC batch since I started writing. This is now the sixth article in the series. Our list of companies to look at it is shorter this time, but there's still plenty to talk about.
Let's start by revisiting some longer-term investment trends across batches.
YC's cybersecurity, privacy, and trust investment trends
Y Combinator's number of investments per batch in the cybersecurity, privacy, and trust ecosystem had more than doubled since 2020…until now.¹
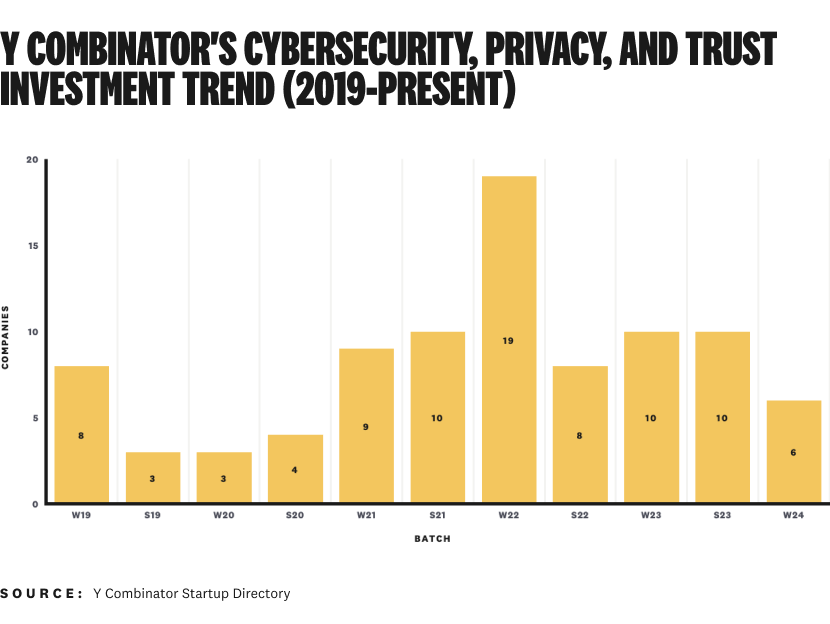
In YC's current era of smaller batch sizes (247, down from 402 in W22), six companies is still a healthy representation.
Garry Tan, YC's President and CEO, was also the group partner for two companies (PromptArmor and Tracecat) — a pretty disproportionate ratio for their leader.
I don't read too much into the reduction in investment this batch. They've invested in nearly 100 companies in the ecosystem over the past six years, and they have the resources to keep funding the best ones that come their way.
YC invests in a mind-bending amount of companies, though. Even though I'm saying their level of investment in cybersecurity companies is healthy, it's a low percentage of the overall batch size.
Here's what I mean:
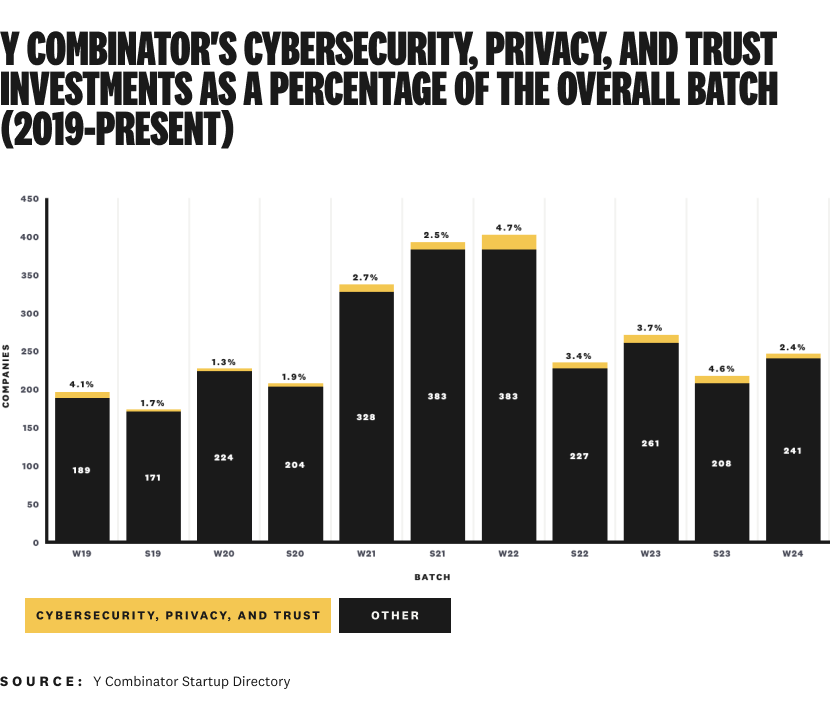
If we (hypothetically) took away all of YC's other investments, their ~15-20 investments per year (across two batches) in cybersecurity, privacy, and trust companies still makes them one of the most active early-stage investors in our industry.
Next, let's meet the companies in the W24 batch and think through their potential opportunities and challenges.
Opportunities and challenges for the Winter 2024 batch
Alarcity
What does the company do?
Alarcity is building an account takeover prevention platform. It's a combination of identity and fraud products and techniques specifically crafted for stopping account takeovers.
Where do they fit into the cybersecurity ecosystem?
They're somewhere between Authentication and Fraud and Transaction Security. The product isn't a full-on identity or fraud platform — it's an intentional blend of the two focused on a specific (and massive) problem within both domains.
What are their challenges?
Alarcity's launch article covered the current state of the problem perfectly:
Large tech companies invest in advanced fraud solutions such as passkeys and intelligent device/session management, etc. However, most companies do not have the bandwidth or expertise to do the same.
What most companies rely on today for ATOs is SMS 2FA. Yet, we are seeing ATOs grow despite the wide adoption of SMS 2FA because codes can be socially engineered, phished, or subject to SS7 attacks.
A skeptic could argue the solutions to ATO attacks are already out there, and it's just an implementation or adoption problem. Maybe true, but could an easier-to-adopt platform increase the adoption rate and win? There were payment processors before Stripe, too — but their early advantage was being ridiculously easier to adopt.
Another adjacent challenge is the difficulty of separating ATO prevention from a company's overall customer identity infrastructure. Companies with enough traction and maturity to have large-scale ATO problems have already invested loads of time, money, or both into their customer identity stack. They're unlikely to change the entire stack just to stop ATO attacks.
This means Alarcity may eventually need to integrate with existing customer identity platforms. Competing with the likes of Okta (Auth0), Ping Identity, FusionAuth, Descope, Passage, and dozens of other well-funded customer identity platforms is an exhausting road. Making friends with them could turn potential competitors into huge advocates.
Why could this be a big company?
Stolen credentials are the reigning champion of methods criminals use to cause breaches — and has been for many years running in Verizon's DBIR reports. Solutions aren't getting implemented quickly enough, and attacks are becoming more sophisticated and persistent.
Now, companies are starting to get sued for not doing enough (in the eyes of regulators, anyway) to stop these types of attacks on consumers. Historically, companies start to take action when legal or regulatory implications get bad enough.
Alarcity can be a big company if they make ATO prevention incredibly easy and effective to implement, alongside a boost in urgency from state and federal regulators to reduce the impact of this problem.
Delve
What does the company do?
Delve automates the process of becoming HIPAA compliant and monitoring compliance on an ongoing basis. It's not just a compliance product — they literally set up compliant infrastructure for HealthTech companies to build products on.
Where do they fit into the cybersecurity ecosystem?
I'd classify Delve as a "hybrid" company across infrastructure and Governance, Risk, and Compliance (GRC). They're solving security and compliance problems (HIPAA, at least to start) with infrastructure and compliance automation features.
What are their challenges?
I could be off base here, but Delve seems easier to implement for brand new companies (or products) than existing products already built on infrastructure created long before Delve was a company. This could make switching costs hard. Re-platforming an existing app is a big ask.
HIPAA compliance is a big-but-not-massive market at ~$3 billion annually.² It's a U.S. only regulation, and the existing market includes a lot of services spend. Delve (eventually) might need to repeat their model for other types of regulations as they scale, but that's a problem for later.
Why could this be a big company?
Trends for HealthTech industry investments look just about like cybersecurity — down from 2021 and early 2022 numbers, but still strong. This means there are still plenty of potential early-stage customers (including 24 in this YC batch alone) for Delve to grow with.
The idea of building and monitoring regulation-specific infrastructure is pretty novel. If Delve becomes the go-to approach for launching companies in regulated industries, they can be a big company.
Nuanced
What does the company do?
Nuanced is an API and web app for detecting AI-generated fraud, deepfakes, and misinformation. Their current specialty is detecting AI-generated images, which is useful for all kinds of services with high volumes of user generated content.
Where do they fit into the cybersecurity ecosystem?
They're a combination of AI/ML Security and Fraud and Transaction Security. The problem is fraud, and the reason is AI.
What are their challenges?
AI-generated fraud, deepfakes, and misinformation is still an emergent problem. Most people you know (definitely not your mom) have heard of this. It's still going to take a while for the long tail of companies to realize this problem exists, let alone adopt a solution for it.
This may sound defeatist, but I also wonder if some companies are even going to try stopping AI-generated content. X (Xitter?!) is the wild west right now. Other out-of-band sites like forums, Discord channels, and Reddit just let a lot of this stuff go.
Why could this be a big company?
Some companies have to care about AI-generated content because trust and safety are important parts of their business. The scope of "have to care" is a lot wider than you'd think — everyone from dating sites to regulated industries like FinTech needs to avoid this type of behavior from malicious users.
If the problem itself multiplies exponentially (and it definitely could), companies will have to find a solution fast. What better way than a straightforward API like Nuanced? That's how they become a big company.
PromptArmor
What does the company do?
PromptArmor protects LLM applications from attacks. It's a full offering, including a product, services, and threat intelligence.
Where do they fit into the cybersecurity ecosystem?
They're an AI/ML Security company focused on securing LLMs.
What are their challenges?
Awareness of this problem space is going to take a minute. Most companies barely understand how or why to build LLM applications, let alone defend them from attacks.
Companies who are thinking about LLM security are often focused on the data loss/exfiltration part of the equation right now — things like preventing their own employees from sharing information they shouldn't. They haven't put much thought into how or why an attacker might exploit an LLM application.
Why could this be a big company?
This is an "all ships rise with the tide" situation. Generative AI sure looks like the next major technology platform, and those only come around a few times in your life.
Business and enterprise adoption of LLMs is moving faster than it has with some previous technology platforms. A majority of use cases, or at least a material share, are going to be business-focused.
A major security incident (and definitely a handful of incidents) involving LLM applications is going to get this problem on the radar of security leaders quickly. If PromptArmor can position itself as the go-to solution for securing an organization's LLM applications, it's going to be a big company.
Titan
What does the company do?
Titan helps companies manage access to data, starting with Snowflake. This includes authorization for any resource type in the data warehouse (users, roles, schemas, databases, etc.).
You could conceptually think of Titan like an Identity Governance and Administration (IGA) product but specifically for managing access to data, and implemented with infrastructure as code instead of an interface.
Where do they fit into the cybersecurity ecosystem?
It's an Authorization product built for Data Security.
What are their challenges?
It's easy to pick on access control for Snowflake as a niche market with a small TAM, but Snowflake has over 8,500 customers. Titan may (eventually) have to broaden support and add other data platforms in the future, but there's plenty of room to grow on Snowflake alone.
Managing access to data infrastructure is a complex problem, and implementing it with infrastructure as code requires sophisticated users. I'm sure the Titan team knows that and is building a product that works for them, at least for now. Someday, they might need to add an interface or other abstraction layers to make things easier for less sophisticated customers.
Why could this be a big company?
Snowflake has a $57 billion market cap and $2.8 billion of revenue growing 36% year-over-year. They're one of the ten best companies in all of tech. Building on top of them is a nice place to start.
And guess what? Managing security in Snowflake is a nightmare!
We're quickly moving past the days where access in data warehouses is a free-for-all. This is partly driven by plugging LLMs into them. Companies figured out how quickly LLMs give employees access to sensitive data if their underlying access to the data isn't tight.
Titan can be a big company if this problem rapidly increases the importance of access control in data infrastructure and they're the standard for solving it.
Tracecat
What does the company do?
Tracecat is an open source security automation platform. It's a nice one with modern features like no code, AI-assisted workflows, and local or cloud deployment options.
Where do they fit into the cybersecurity ecosystem?
They're a Security Orchestration, Automation, and Response (SOAR) product, which falls under Security Operations.
What are their challenges?
SOAR (or hyperautomation, if you want to use the fancy new term) is a busy market with lots of competition. The big security operations companies like Palo Alto Networks, CrowdStrike, Cisco (Splunk), and others all offer established SOAR products.
We've also seen a lot of M&A and financing activity lately, including Arctic Wolf's acquisition of Revelstoke, SentinelOne's acquisition of Stride, Torq's oversubscribed Series B, and so on.
Competing in this market is going to take an awesome product and then some — but the recent acquisitions and investments have made it clear the market is far from won.
Why could this be a big company?
We're entering a new era of SOAR/hyperautomation products, partly because the need for automation in security is still so acute. Who knows if or when AI is going to fully automate the SOC — probably not anytime soon. Until then, the combination of some AI and some automation is going to be what companies use to get by.
Tracecat can be a big company if they keep building an awesome product and their open source model (with a pretty reasonable entry price point) helps them find customers and grow with them.
Footnotes
¹Batch counts include companies as of Demo Day. Numbers may be off by a few because companies pivot in and out of the industry after launching.
²According to the mildly shady market research companies, anyway.
*** This is a Security Bloggers Network syndicated blog from Strategy of Security authored by Cole Grolmus. Read the original post at: https://strategyofsecurity.com/y-combinators-winter-2024-cybersecurity-privacy-and-trust-startups/
如有侵权请联系:admin#unsafe.sh
