
2024-4-20 01:53:56 Author: securityboulevard.com(查看原文) 阅读量:2 收藏
The newest version of the European Union Network and Information Systems directive, or NIS2, came into force in January 2023. Member States have until October 2024 to transpose it into their national law. One of the most critical changes with NIS2 is the schedule for reporting a cybersecurity breach.
Unlike NIS, NIS2 requires that every cybersecurity breach incident be reported, whether or not the attack affected the entity’s operations. This is to help authorities improve monitoring and responses to potential threats. NIS2 maintains the requirement from NIS that every EU member state designates a central point of contact for compliance and a coordinating Computer Security Incident Response Team (CSIRT) for incident reporting or a competent authority.
The most significant change around incident reporting is how the NIS2 Directive details a mandatory multi-stage incident reporting process and the content that must be included.
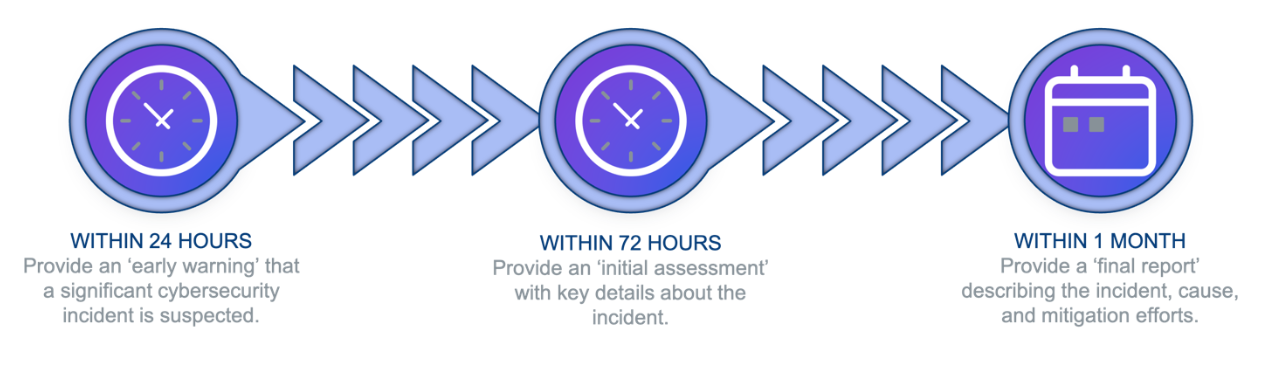
Initial notification: Within 24 hours.
An initial report must be submitted to the competent authority or the nationally relevant CISRT within 24 hours of a cybersecurity incident. The initial report should indicate whether an unlawful or malicious act caused the incident. This first notification is intended to limit the potential spread of a cyber threat.
Follow-up notification: Within 72 Hours.
A more detailed notification report must be communicated within 72 hours. It should contain an assessment of the incident, including its severity, impact, and indicators of compromise. The impacted entity should also report the incident to law enforcement authorities if it were criminal.
Final report: Within one month.
A final report must be submitted within one month after the initial notification or first report. This final report must include:
- A detailed description of the incident
- The severity and consequences
- The type of threat or cause likely to have led to the incident
- All applied and ongoing mitigation measures
Additionally, under the NIS2 Directive, entities must report any major cyber threat they identify that could result in a significant incident. A threat is considered significant if it results in:
- Material operational disruption or financial losses for the entity concerned
- It may affect natural or legal persons by causing significant material or immaterial damage.
NIS2 mandates that essential and important entities implement baseline security measures to address specific forms of likely cyber threats. Amongst these measures are risk assessments and security policies for information systems.
Enforcement Through Penalties: Failure to Comply
Failure to comply with the NIS2 Directive comes with stricter penalties than NIS. Under the NIS2 Directive, penalties for non-compliance differ for essential entities and important entities.
- For essential entities, administrative fines can be up to €10,000,000 or at least 2% of the total annual worldwide turnover in the previous fiscal year of the company to which the essential entity belongs, whichever amount is higher.
- For important entities, administrative fines can be up to €7,000,000 or at least 1.4% of the total annual worldwide turnover in the previous fiscal year of the company to which the critical entity belongs, whichever amount is higher.
How a Data-Centric Security Solution Can Help
Proactive and Preventative Security Measures
Organizations must recognize and address incidents more efficiently to meet NIS2’s reporting demands. A unified approach to managing sensitive data, discovering and classifying the data, assessing vulnerabilities, and taking advantage of risk analytics helps meet these higher demands. All these measures provide real-time reporting for greater visibility and risk analytics.
Leverage AI/ML Early Warning System
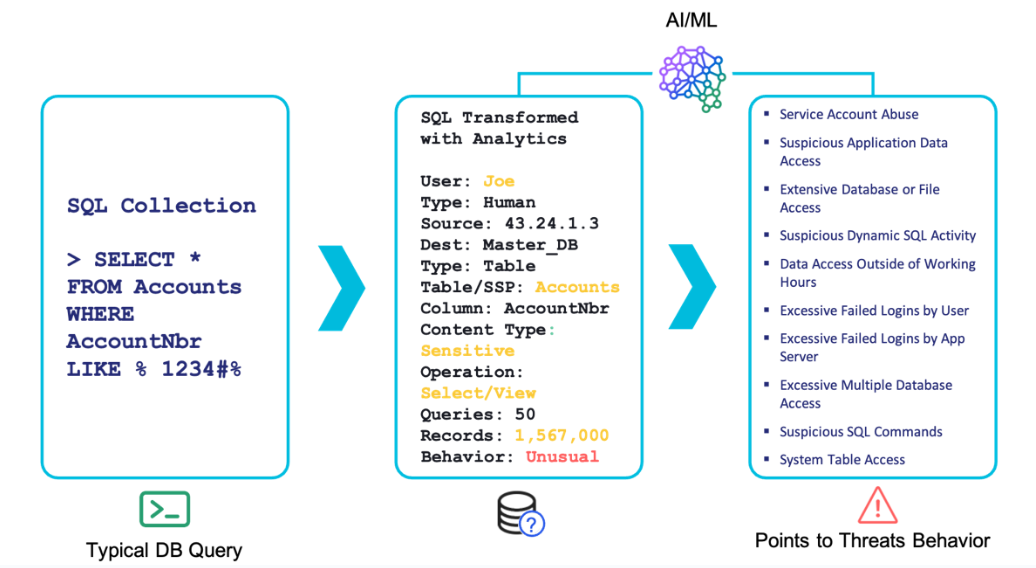
A reporting engine reduces reporting time by delivering critical data within twenty-four hours of the first sign of an attack. The graphic below shows how Imperva Data Security Fabric (DSF) identifies abnormal behavior based on a seemingly ordinary database query. Using artificial intelligence and machine learning behavior analytics, Imperva DSF identifies and reports threat behavior associated with several potential business-impacting issues by:
-
- Anticipating an impending attack by identifying event sequences that align with recognized attack patterns.
- Seamlessly translating database languages into plain English for effortless usage.
- Translating Structured Query Language (SQL) to actionable security events for the Security Operations Center.
Implement Automatic and Ad-hoc Reporting
Implementing a data security solution with a robust reporting engine enables you to produce pre-defined or user-defined reports based on accumulated data. Reports should be able to be generated either automatically, on the fly, or scheduled to run at regular intervals and then distributed as required. These reports accumulate a wealth of data that provide transparency regarding various aspects of your data, databases, file servers, and users in your network. This information can be used to report on activities to assist in maintaining compliance with various regulatory bodies, distribute reports on critical data risk posture assessments, generate regular reports that chronicle data access activity, data repositories status, and alert activity, and much more.
Conclusion
NIS2 has increased its focus on the time you are required to report a cybersecurity incident. Failing to do so can result in substantial fines. To maintain compliance and avoid penalties, organizations must consider implementing a data-centric security solution that uses a reporting engine to speed the reporting process.
To learn more about how Imperva Data Security Fabric aligns with NIS2, download the Solution Brief.
The post Taking Time to Understand NIS2 Reporting Requirements appeared first on Blog.
*** This is a Security Bloggers Network syndicated blog from Blog authored by Brian Robertson. Read the original post at: https://www.imperva.com/blog/taking-time-to-understand-nis2-reporting-requirements/
如有侵权请联系:admin#unsafe.sh
