
The Good | DoJ Indicts Cryptojacking Criminal and Botnet Operator Supporting Ransomware ActorsThe 2024-4-19 21:0:56 Author: www.sentinelone.com(查看原文) 阅读量:22 收藏
The Good | DoJ Indicts Cryptojacking Criminal and Botnet Operator Supporting Ransomware Actors
The DoJ doled out two indictments this week: the first announcing the arrest of Charles O. Parks III for his role in an elaborate cryptojacking scheme, the second, charging Alexander Lefterov, owner and operator of a major botnet.
Parks was charged with wire fraud, money laundering, and illegal transactions, tallying up to a maximum of 30 years in prison. According to the DoJ, the basis of Parks’ scheme was renting $3.5 million worth of cloud servers through a number of fake LLCs in order to mine nearly $1 million in cryptocurrency.
After tricking the cloud service providers (CSPs) into escalating his privileges, Parks was given access to services equipped with powerful graphics cards that were then used to mine Monero, Litecoin, and Ether. The mined funds were laundered through purchasing NFTs and converting them through traditional banks and various crypto exchanges to fund a lavish lifestyle.
Lefterov was indicted by a federal grand jury for aggravated identity theft, computer fraud, and conspiracy to commit wire fraud. Through the large-scale botnet he maintained, the Moldovan national and his associates have been linked to thousands of compromised computers across the U.S.
Using credentials harvested from the infected computers, Lefterov and his co-conspirators targeted victims’ financial accounts across banking, payment processing, and retail platforms to steal money. In tandem, Lefterov allegedly leased his botnet to other cybercriminals for ransomware distribution, later receiving a share of the profits from successful attacks.
Following both of these indictments, U.S. law enforcement reiterates their commitment to cyber defense, stating that the FBI and its partners will continue to investigate and pursue those involved in malicious activities both domestically and internationally.
The Bad | Researchers Link Russian-Based Sandworm APT to Attacks on Water Supply Systems
GRU-linked APT known as Sandworm has recently taken a behind-the-scenes approach, conducting covert attacks through various online personas and posing as hacktivist groups to mask their activities. In a new report, cybersecurity researchers identified Sandworm’s presence in at least three Telegram channels created to conduct disruptive operations and amplify pro-Russian narratives.
Sandworm has operated since 2009 under Unit 74455 of the Main Intelligence Directorate of the Russian Federation (GRU). Known to employ adaptive and diverse methods for initial access and exploit supply chain vulnerabilities, Sandworm is thought by researchers to be one of Russia’s foremost “cyber sabotage units” as well as a “formidable” threat globally.
Most recently, Sandworm has begun using online personas to execute disruptive operations and enhance the image of the GRU’s cyber capabilities. The report tracks the APT groups’ activity across three Telegram channels: XakNet Team, CyberArmyofRussia_Reborn, and Solntsepek. While most of the activity centers around targeting Ukrainian entities, one of the channels this week claimed attacks on critical water supply centers in the U.S. and Poland, and a hydroelectric facility in France. The posted videos showed fake images of attackers manipulating the controls of water suppliers in Texas.
🚨 Cyber Army of Russia claims to be targeting US water facilities🚨
The group announced the latest campaign against the US and have provided a video showing them allegedly manipulating settings at two water supply organisations in two cities of Texas – Abernathy and Muleshoe.… pic.twitter.com/wzixXdw3Sv
— CyberKnow (@Cyberknow20) January 19, 2024
While Sandworm’s focus has shifted towards espionage and influence operations, it continues to conduct disruptive attacks, targeting electoral systems, conducting intelligence gathering, stealing credentials, and retaliating against perceived adversaries. Cyber defenders continue to warn of potential interference in upcoming national elections and political events across the world, with Ukraine remaining a primary target amid ongoing conflict.
The Ugly | Suspected Nation-State Actors Exploit Zero-Day Flaw in Palo Alto Network Firewalls
Over the weekend, state-sponsored threat actors were suspected of exploiting a zero-day vulnerability in Palo Alto Networks’ PAN-OS firewall software. Though the vulnerability was quickly disclosed and patched by the Californian cybersecurity company, exploit code has since emerged this week and is already being used in attacks. Despite earlier mitigations provided during initial discovery, Palo Alto Networks is now urging users to upgrade their software immediately as the most reliable solution.
Tracked as CVE-2024-3400, the maximum severity flaw enables unauthenticated remote code execution (RCE) via command injection in low-complexity attacks that do not require user interaction. It affects PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewalls configured with GlobalProtect, both gateway or portal. Palo Alto Networks’ advisory confirms that Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability.
Researchers that initially detected the flaw found that the threat actor was focused on exporting configuration data from compromised devices before leveraging them to move laterally into victim organizations. Noting the level of tradecraft and speed of the attacks, the report suggests that the threat actor is highly capable with a clear playbook – indications of a state-backed attack. Along with warnings to secure vulnerable devices, CISA has added the vulnerability to its Known Exploited Vulnerabilities catalog.
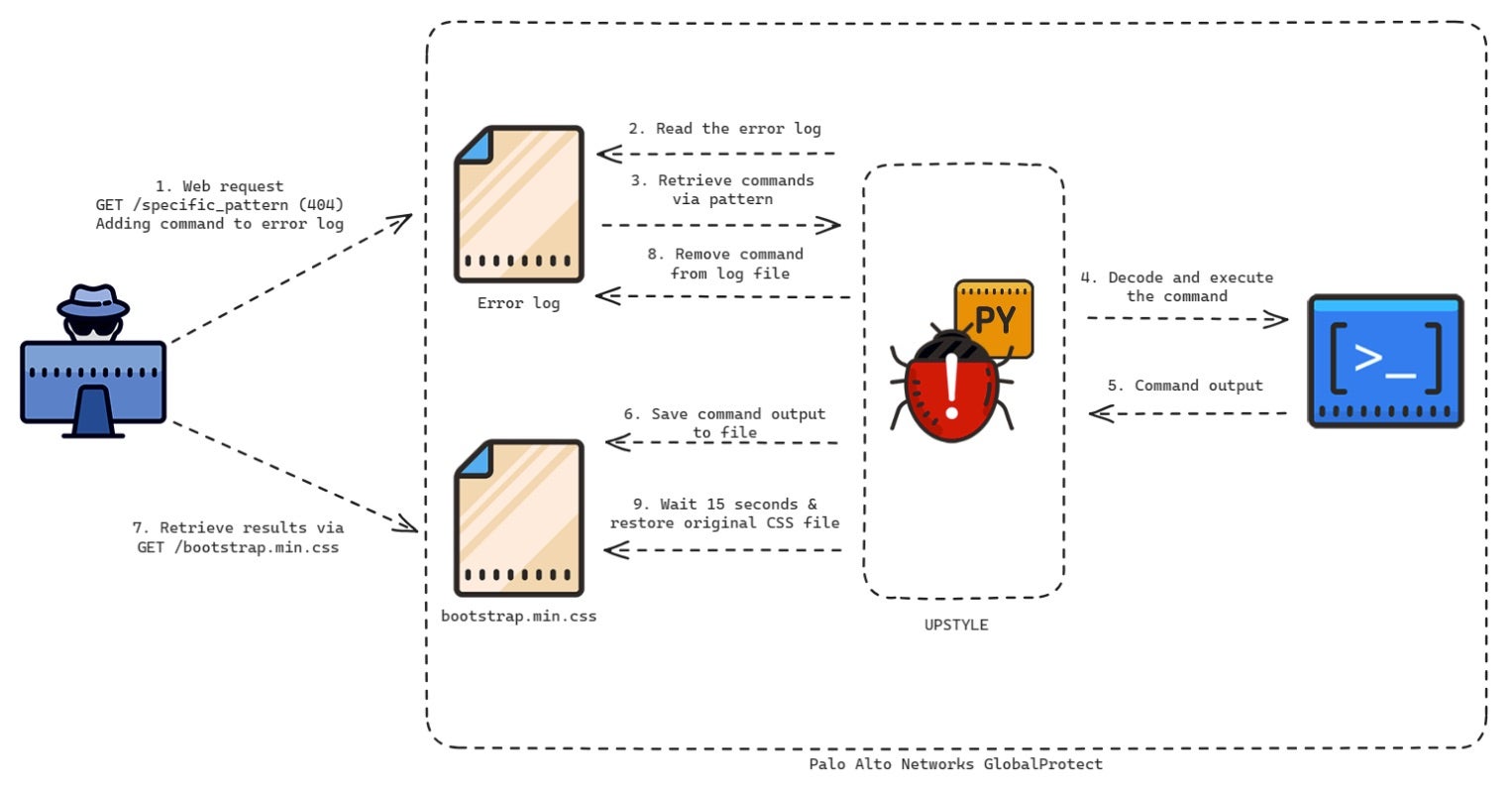
Internet-connected network devices are often running on outdated, unpatched firmware which makes them vulnerable to exploitation. This, along with the key role they play in network infrastructure, means such devices are considered low-hanging fruit to attackers looking for a way in. To mitigate risks, companies should prioritize regular patches, enforce robust access controls, and practice network segmentation to safeguard their networks against intrusion.
如有侵权请联系:admin#unsafe.sh