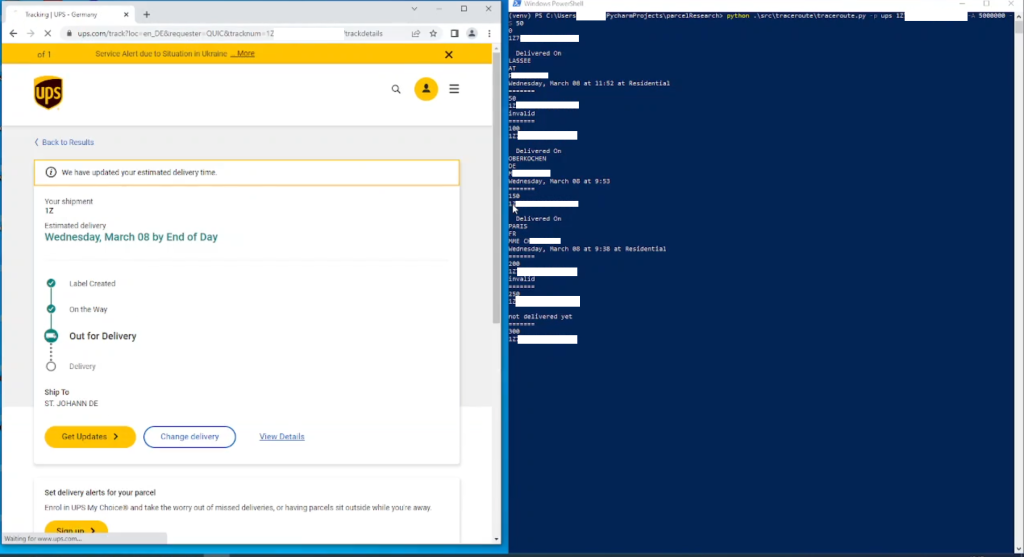
Today, we describe our findings at United Parcel Service of America, Inc. (UPS), another German parcel market player, and the corresponding vulnerabilities’ disclosure process.
Only a valid tracking number is needed to get the personal information of a parcel’s receiver, including the sender’s location, the recipient’s name, and the recipient’s location (city and country). It was possible to enumerate numerous tracking numbers during testing by iterating from known ones. Since the last digit of a tracking number is a checksum, it can be calculated. Also, certain businesses have a predefined prefix in their tracking numbers. This schema allows the enumeration of every parcel sent from a particular business.
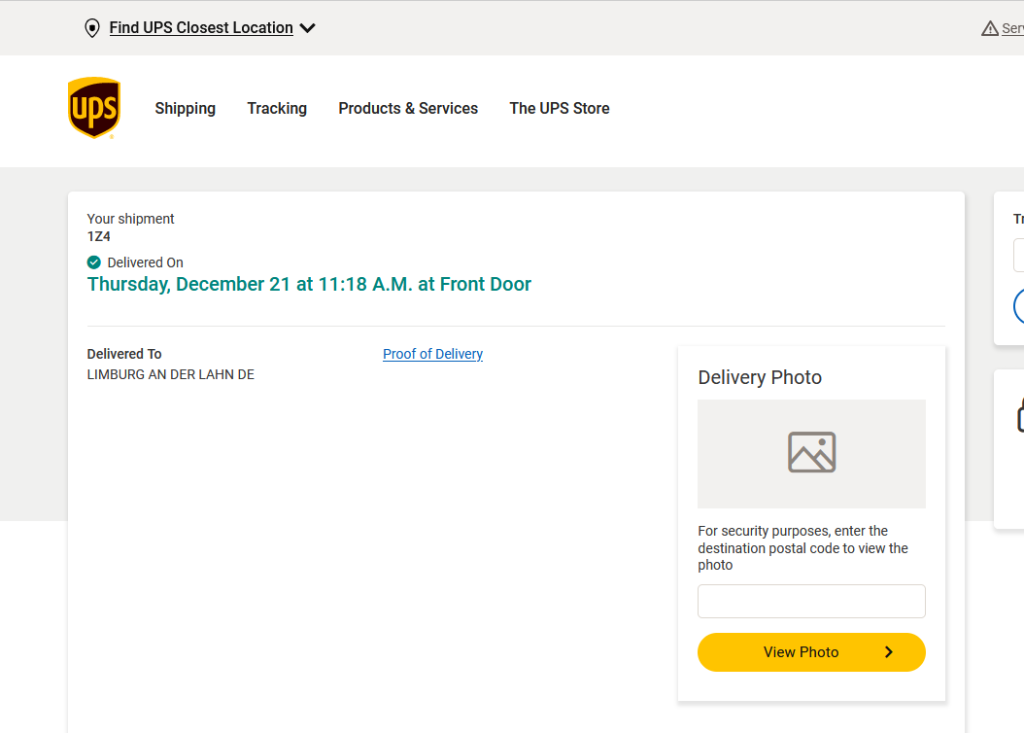
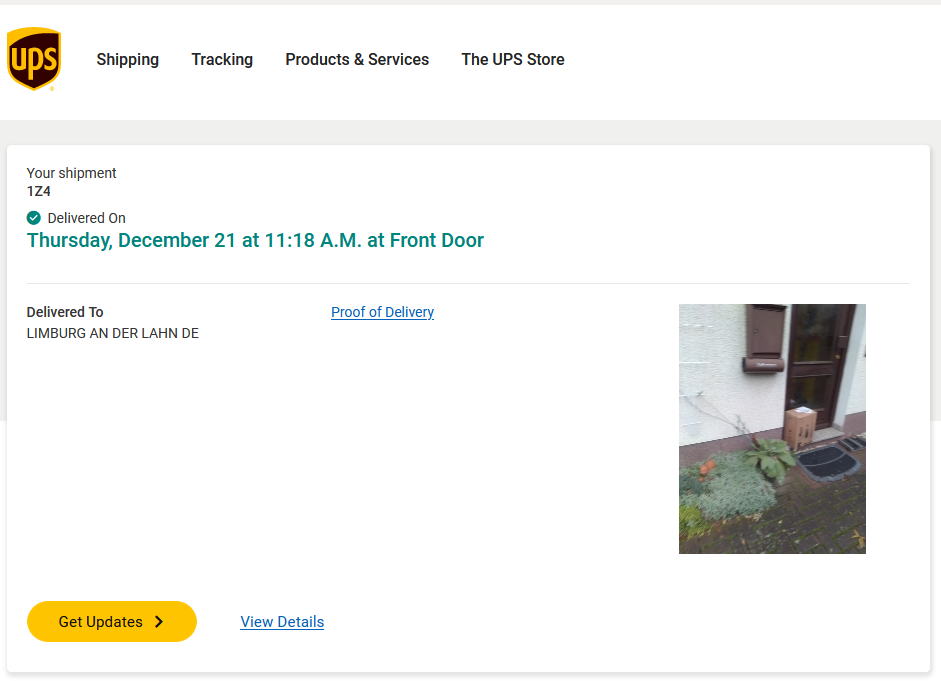
In some cases, the tracking also shows a delivery photo of the location where the parcel was left. This picture can be unlocked using the ZIP code of the destination address. In our test case, the site asking for the ZIP shows the city or village to which it was delivered. This makes it possible to guess the correct ZIP code in very few tries.
All in all, this allows an attacker to efficiently collect customers’ personal data, including their names, locations, shopping behavior, and, in some cases, even a photo of people’s houses. During testing, getting details of 15 parcels per minute was possible using a single session. The data collection process may be parallelized, drastically increasing this number. With standard COTS hardware, 20 sessions are trivially achievable. This would increase the speed to approximately 300 parcels per minute.
Until this post’s publication date, we have not received any reaction from UPS.
- May 11, 2023: Initial contact to UPS, start of 90-day disclosure period.
- June 01, 2023: New contact attempt.
- September 05, 2023: New contact attempt.
- September 07, 2023: First reaction by a UPS “fraud mitigation analyist” asking us to resend some attachments.
- September 08, 2023: All information is sent again to this contact person.
- September 14, 2023: New contact attempt because no follow-up reaction by UPS.
- September 26, 2023: New contact attempt.
- October 04, 2023: New contact attempt.
- October 31, 2023: New contact attempt.
- November 14, 2023: New contact attempt.
- November 20, 2023: New contact attempt.
- January 08, 2024: New contact attempt.
- February 02, 2024: ERNW decides to report the vulnerabilities to the Cybersecurity & Infrastructure Security Agency (CISA) which is part of the U.S. Department of Homeland Security. Handling software vulnerabilities is managed by Carnegie Mellon University’s CERT Coordination Center (CERT/CC).
- February 19, 2024: ERNW requests CERT/CC for coordination assistance and submits a detailed vulnerability report.
- February 26, 2024: The CERT decides not to handle the case.
- March 19, 2024: ERNW decides to fully disclose the vulnerabilities.
- April 10, 2024: Publication of this blog post.
Cheers!
Dennis Kniel & Florian Bausch
BTW, if you want to get more insight into IT security topics and meet awesome people from the field worldwide, mark your calendars and visit #TROOPERS24 conference from June 24 to June 28, 2024, in Heidelberg!