2024-4-5 16:0:28 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
Advancements in Internet of Things (IoT) technologies are paving the way for a smarter, more interconnected future. They’re taking down communication barriers among consumers and businesses across different industries.
According to Global Data, the global IoT market could be worth $1.1 trillion in 2024, potentially growing at a 13% compound annual growth rate (CAGR). Enterprise IoT comprised over 75% of the total revenue in 2020, potentially accounting for 73% of the overall market this year.

Businesses heavily rely on IoT systems for various operations. Although progressive and innovative, an overdependence on self-executing IoT systems poses several security risks. You might miss the obvious warning signs of cyberattacks.
The best approach is to assign IT specialists who will monitor your IoT systems. That way, they can identify and address potential security threats from the onset. Learn what the top IoT security challenges are and how to address them.
Read on.
Top IoT Security Challenges to be Aware of
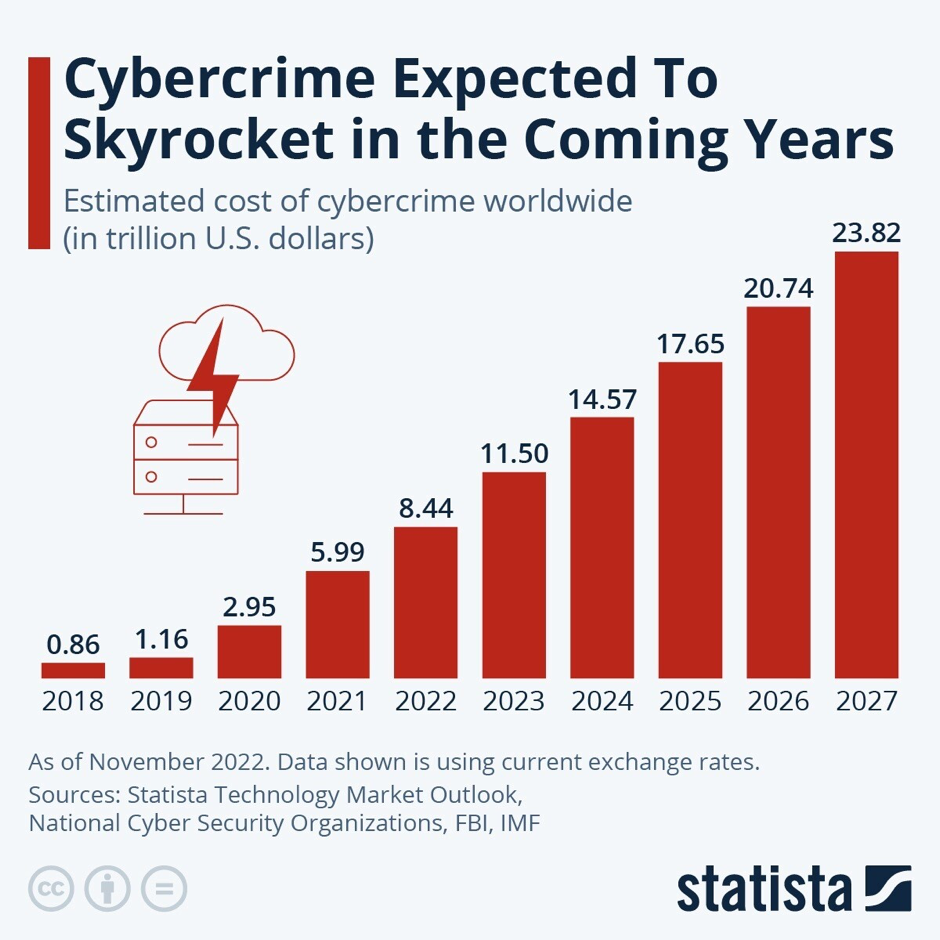
Companies and organizations should be wary of cyberattacks due to security vulnerabilities. The World Economic Forum cited 2023 as a big year for cybercrime, with the global cost forecasted to grow from $8.44 trillion in 2022 to $23.84 trillion by 2027.

Cyberattacks are prevalent, ranging from phishing attacks like the Buybuy Baby closing sale scam to denial-of-service (DoS) attacks like the AWS attack in 2020.
As such, your IT department should watch for the most common IoT security challenges in 2024. Below are some:
1. Attack Surface Expansion
Expanding your IoT network with interconnected systems inadvertently creates multiple entry points for cybercriminals. Simply put, crooks can target you from various angles.
Worse, attack surface expansion makes monitoring more expensive—skimping on it only increases risks.
Some organisations, however, carelessly adopt systems they barely understand. This approach makes their security vulnerable.
Modernization only works if you’re equipped and trained for your new protocols. Otherwise, you’re merely creating unnecessary roadblocks and susceptibilities.
2. Evolving Regulations and Innovations
Since IoT tools are still evolving, the guidelines and protocols about them are constantly changing as well.
There’s no hard-and-fast rule on IoT implementation. As an organization, you have the discretion to set up IoT systems or use AI for contract review for your business operations. However, such a deployment requires robust A/B testing to avoid putting your security at risk.
As such, it’s highly encouraged for professionals to take test runs as a chance to perform extensive pen testing. Before rolling out new systems, test them on controlled groups with limited users and have them report bugs.
Your IT team can then use these reports during pen testing. The goal is to expose security issues during the testing phase so that they won’t cause problems down the road.
3. Widespread Botnets and DDoS attacks
Beware of botnets and DDoS attacks. Learn from Amazon’s AWS attack mentioned above.
Considering the interconnected systems and vast attack surface of an IoT system, crooks can quickly spread these types of malware. They just need to bypass one entry point.
Once they enter your system, they can flood other systems with malicious traffic, fake user requests, and infect files.
4. Lack of Governing Laws and Regulations
No single governing body regulates the IoT.
Although the International Telecommunication Union (ITU) and the International Organization for Standardization (ISO) set universal privacy guidelines, they don’t vet new technologies. Developers are ultimately responsible for the security of their products.
Most tech companies rush security testing during the beta and alpha phases. The IoT industry’s fast-paced developments pressure developers to release new systems quickly to keep up with the competition. They focus all their efforts on creating new features, leaving vulnerabilities undiscovered.
5. Limited Security Awareness among Users
Knowing how IoT systems work is one thing, but securing them against cyberattacks is another.
Unfortunately, you can’t expect all your employees to learn advanced cybersecurity. Processes like detecting system breaches, cross-platform patch management, and OS health monitoring require professional IT training.
As such, it’s imperative to bridge information gaps through frequent seminars. First, ask your IT team to explain IoT cybersecurity. Focus on teaching workers how to spot and report potential threats so IT professionals can address them faster.
Likewise, provide them with actual examples and real-life demonstrations. They should know what to watch out for on a daily basis.
6. Bad Cybersecurity Hygiene Practices
Don’t overlook your employees’ bad cybersecurity practices. Many companies suffer data breaches because of their workers.
Unfortunately, humans are the weakest link in their cybersecurity systems. Even with multiple programs to combat malware, you’ll still be susceptible to data breaches if your employees have poor digital hygiene.
Here are seemingly small yet critical mistakes that could cause massive damage:
- Using weak login credentials: A user’s login credentials serve as their first line of defence against hackers. If their password is a dictionary word with no special characters or numbers, crooks can quickly bypass it through brute-force attacks.
- Turning off 2FA: People often turn off multi-factor authentication for faster logins. Note that MFA creates extra security layers that’ll keep out hackers even after they get your username-password combinations.
- Joining public networks: Employees should never connect their work devices to unsafe public networks.
How To Resolve Security Challenges in IoT
Did you know that only 4% of companies feel confident about their security?
Less than 5% of all organizations believe their “users of connected devices and related technologies are protected against cyberattacks.” The problem, however, is that cyberattacks occur every 39 seconds.

Here are the key steps for addressing IoT security challenges:
1. Incorporate Custom Security Systems from the Onset
Stop recycling your cybersecurity process. Update your protocols when integrating tools or devices into your IoT network. Remember: Additional systems create extra liabilities.
Start by asking your team to list the initial vulnerabilities. Then, devise ways to mitigate the potential risks. Finally, execute your security measures and track your progress.
Note that your first patch updates would almost always end up buggy. Instead of striving for perfection in one go, prepare your team to solve issues that arise fast.
2. Observe Routine Monitoring and Patching
Include system monitoring and patching in your IT team’s daily routine. As your IoT system expands, it becomes harder to defend against cyberattacks.
Also, you’re more likely to overlook hacking warning signs. Just one successful attack could cost you hundreds of thousands, so be very careful.
C-level executives should invest in system specialists. Instead of dumping all your company’s cybersecurity needs on one department, each platform or tool should have an assigned manager.
Dedicated security personnel can manage day-to-day monitoring and reporting. Give them the time and resources to focus on cybersecurity—haphazard system tracking will only produce inaccurate results!
3. Use Encrypted Communication Protocols
Only use encrypted messaging platforms for team communication. Your employees should never send work files, add coworkers, or bring up confidential topics outside the approved channels. Otherwise, company data will be floating around platforms you can’t control.
C-level executives should create custom communication channels. Scaling enterprises should create a private, encrypted messaging system for their employees. It’s costly but worthwhile.
As your company grows and handles more sensitive information, the potential cost of a data breach exponentially spikes as well. It’s best to control how data moves around your workplace.
Strengthen the Cybersecurity of Your IoT Systems
We understand how exciting it feels to streamline day-to-day operations by replacing legacy systems with modern IoT systems.
Of course, you’re free to explore new digital tools and technologies. Just ensure you know their limitations and vulnerabilities—invest as much of your resources in cybersecurity as you would with tech research and implementation.
Likewise, look for reputable industry professionals, and don’t hesitate to hire third-party cybersecurity professionals if needed. This option is a cheaper, more cost-efficient alternative to building and maintaining an in-house IT team, especially for small and mid-sized enterprises (SMEs).
If your system heavily relies on Linux OS, consult TuxCare. Whether you need ongoing vulnerability patching or end-of-life Linux system support, they can help meet your cybersecurity needs.
The post Expert Insights on IoT Security Challenges in 2024 appeared first on TuxCare.
*** This is a Security Bloggers Network syndicated blog from TuxCare authored by TuxCare Team. Read the original post at: https://tuxcare.com/blog/expert-insights-on-iot-security-challenges-in-2024/
如有侵权请联系:admin#unsafe.sh