2024-4-3 01:42:3 Author: securityaffairs.com(查看原文) 阅读量:11 收藏
Binarly released the free online scanner to detect the CVE-2024-3094 Backdoor

Researchers from the firmware security firm Binarly released a free online scanner to detect the CVE-2024-3094 Backdoor
Last week, Microsoft engineer Andres Freund discovered a backdoor issue in the latest versions of the “xz” tools and libraries. The vulnerability was tracked as CVE-2024-3094 and received a CVSS score of 10.
Red Hat urges users to immediately stop using systems running Fedora development and experimental versions because of a backdoor.
XZ is a popular data compression format implemented in almost all Linux distributions, including both community-driven and commercial variants.
The malicious discovered by the researchers is obscured and is present only in the download package. The Git distribution doesn’t include the malicious code due to the lack of the M4 macro necessary for triggering the build of the malicious code.
The malicious build interferes with the authentication in sshd through systemd. Under certain conditions, an attacker can compromise sshd authentication and gain unauthorized remote access to the entire system.
CISA also published an advisory urging to downgrade to an uncompromised XZ version (i.e., 5.4.6 Stable) and to hunt for any malicious.
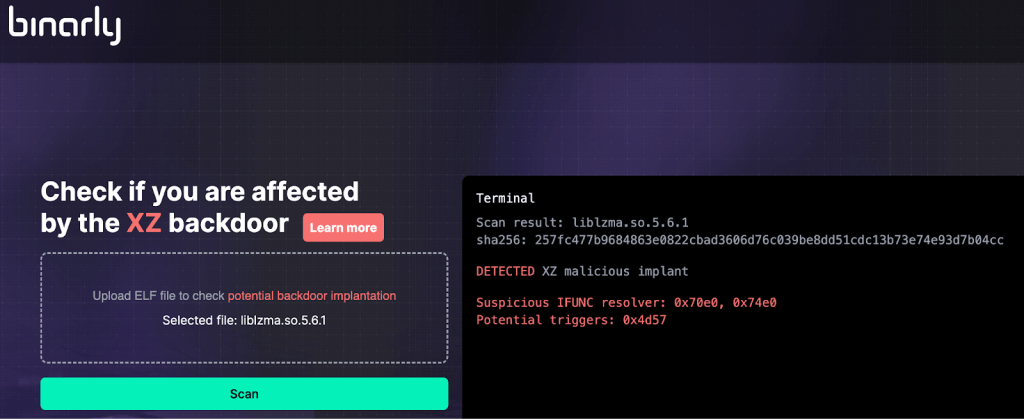
Binarly has created a free scanning tool to help the industry mitigate the threat, the company pointed out that the detection method they use has close to zero false positive rates.
The company states that most of tools that were developed by other experts are focused on simple version checks, hash-based detection of the backdoored component, or YARA rules of the hardcoded unique string constants. These approaches for backdoor detection could lead to false positives.
“To generically detect such implantation, we decided to focus on ifunc transition behavioral analysis with our Binary Intelligence technology. The detection method is completely based on static analysis, where we are detecting generically the tampering of control flow graph transitions” reads the advisory published by the company. “Such detection methods could expose potential control flow tampering during the implantation of malicious ifunc resolvers. This technique works generically and will be able to detect invariants or reuse of the payloads in other software supply chain attacks.”
The XZ backdoor scanner is available for free at XZ.fail, users can upload their binary files to check potential backdoor implantation.

Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, CVE-2024-3094)
如有侵权请联系:admin#unsafe.sh