This blog details how Obsidian detects and blocks the latest version of Tycoon, an adversary-in-the-middle (AiTM), Phishing-as-a-Service (PhaaS) platform that leverages a reverse proxy to intercept and replay credentials and MFA prompts.
This new version of Tycoon has recently received press from Forbes [1], Dark Reading [2], TechRadar [3], and others.
Background
Sekoia wrote a great article detailing how the Tycoon phishing kit has been updated with new obfuscation and anti-detection capabilities. This phishing kit uses a reverse proxy to intercept and replay credentials and MFA prompts, allowing them to defeat most MFA factors, including SMS, TOTP, Push, and Number Matching.
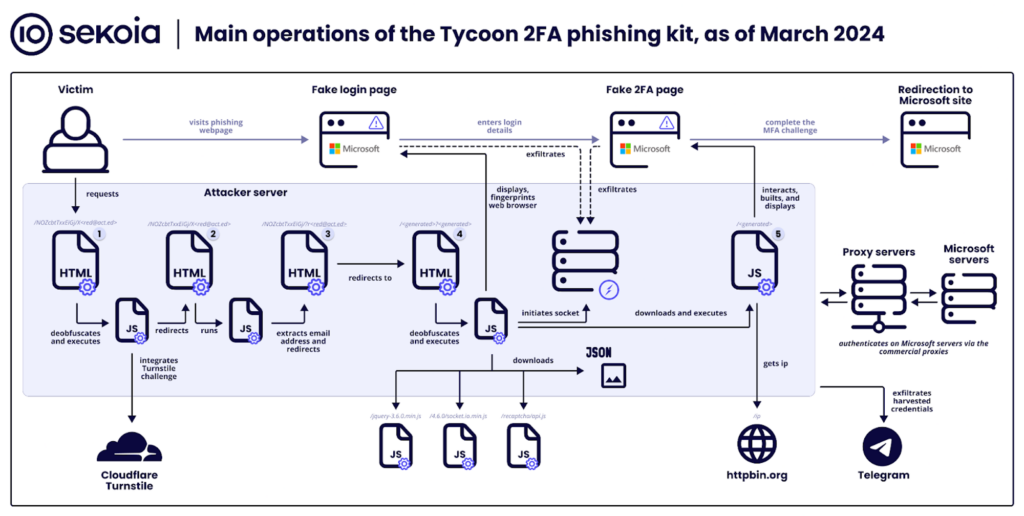
Phishing kits that leverage a reverse proxy are growing rapidly. Caffeine, EvilProxy, NakedPages, Dadsec, and Tycoon are documented kits, and open-source options include Muraena, Evilginx, and Modlishka.
Detecting & Blocking Tycoon’s latest version
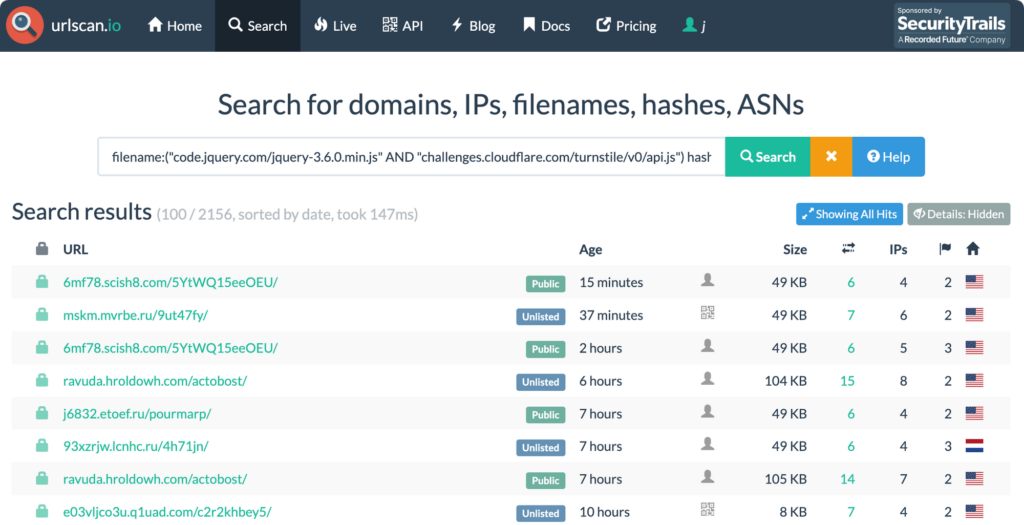
First, lets find some recent Tycoon phishing websites.
Using the latest technique suggested by Sekoia, we’ll search urlscan.io for the following:
filename:(“code.jquery.com/jquery-3.6.0.min.js” AND “challenges.cloudflare.com/turnstile/v0/api.js”)
hash:5feceb66ffc86f38d952786c6d696c79c2dbc239dd4e91b46729d73a27fb57e9
We receive some recent results:
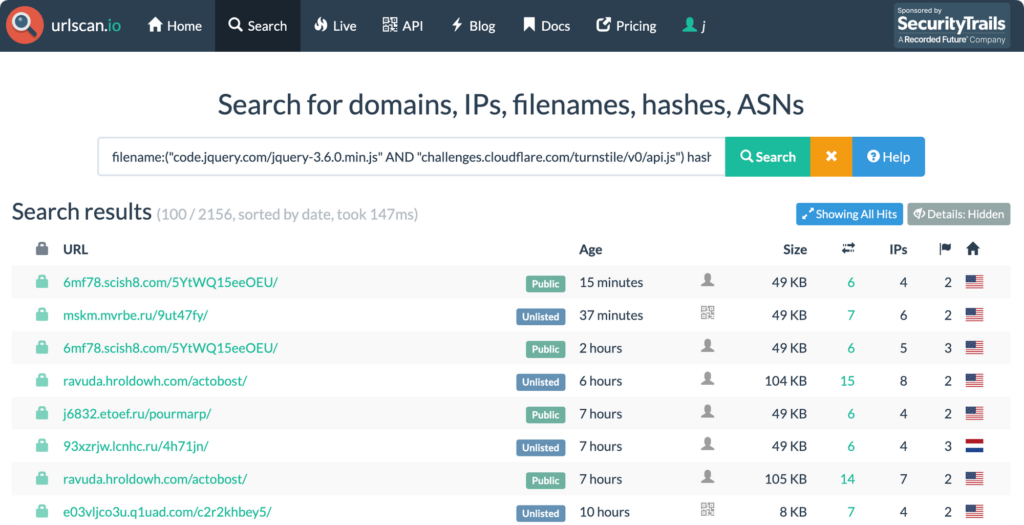
Investigating the first result, we can confirm that TycoonGroup has implemented Cloudflare’s captcha/turnstile to prevent security crawlers and email security products (like ESGs) from observing the website.

This isn’t a problem for Obsidian, as we inspect all content and network traffic for the entire browsing session, evading any countermeasures such as Cloudflare’s anti-bot/turnstile capability.
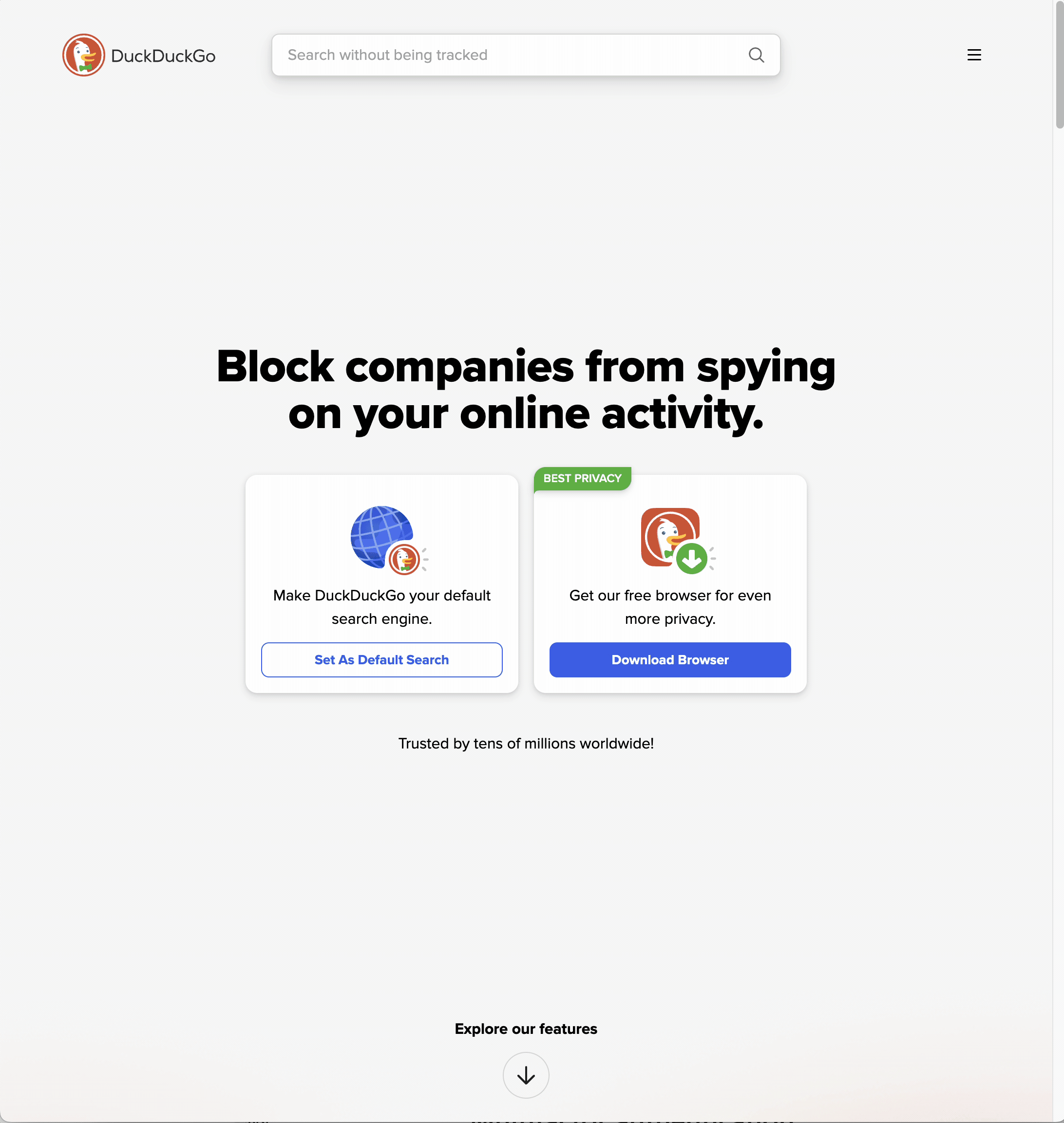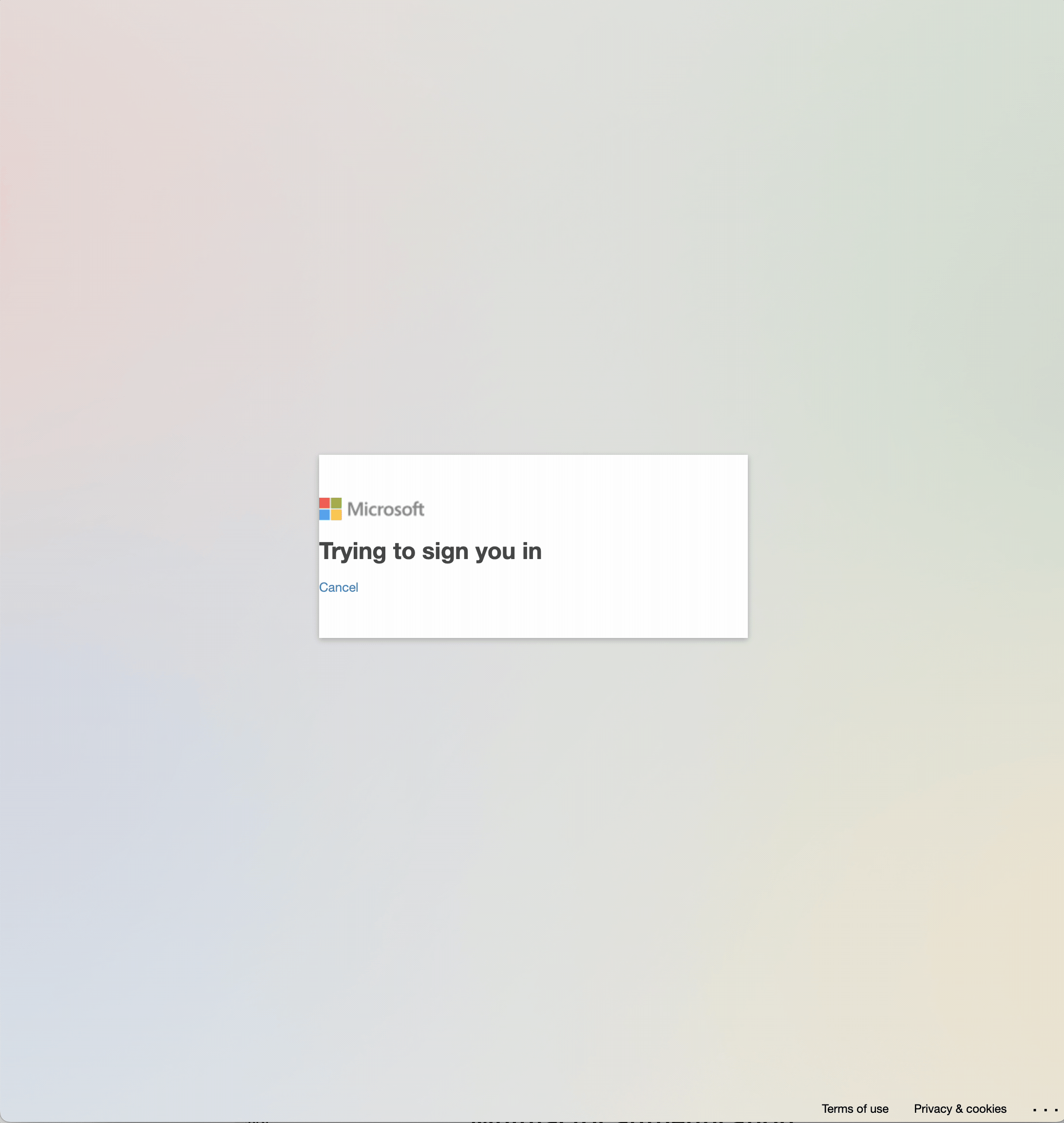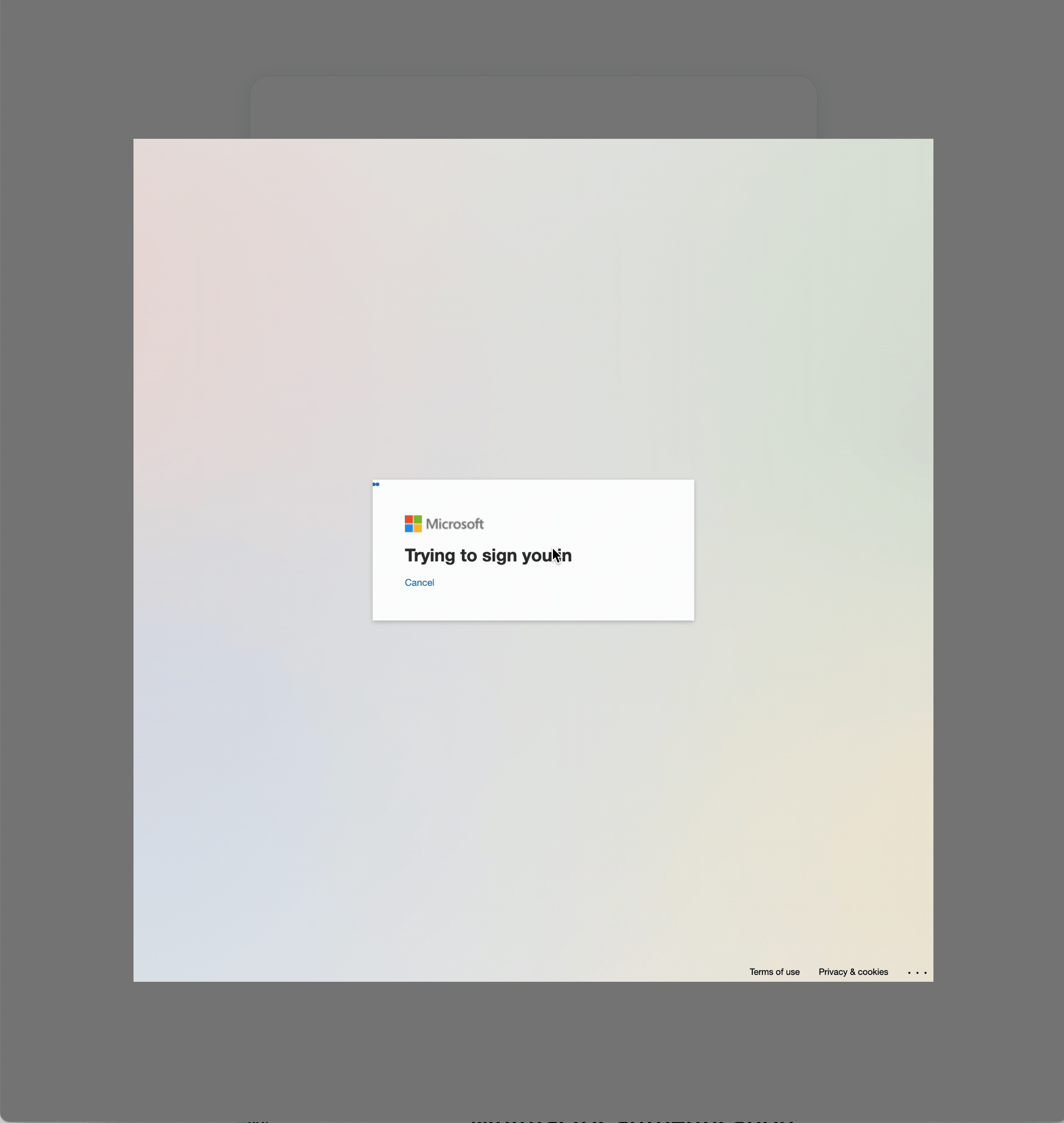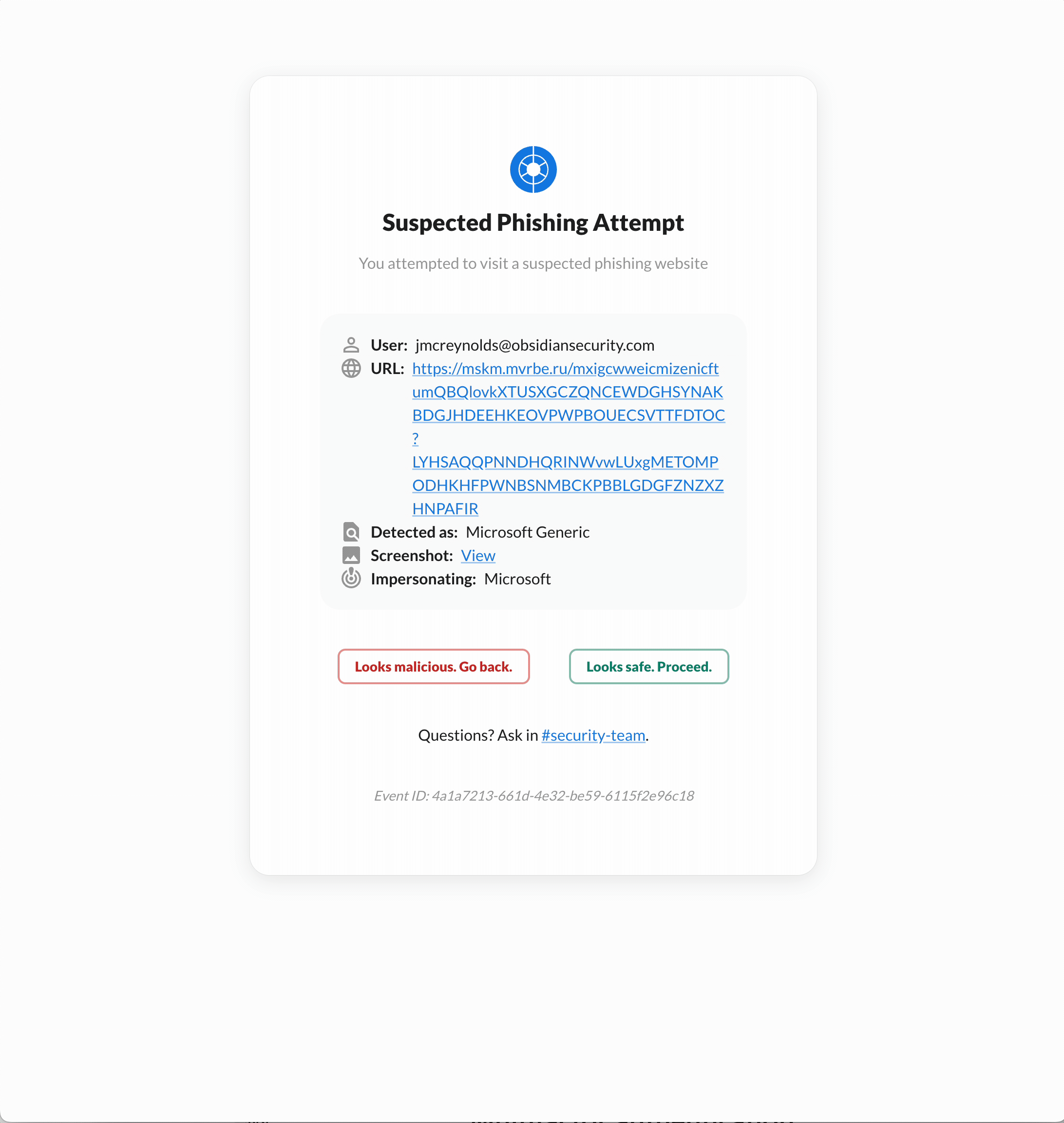
Once we observe the final landing page, which looks like a Microsoft login page, we detect these visual and structural similarities and block the user from submitting any credentials.
See it in action here:
Details:
- Once we observe the Microsoft-looking login page, we block the user. We look for visual and structural similarities. We are not dependent on ephemeral IOCs like IPs or domains or on heuristics like domain age and reputation; each can be easily changed or gamed.
- The end user is provided details about why they were blocked, including a screenshot of the offending page. In this illustration, “warning mode” is configured, allowing users to proceed if they believe it is safe. The logo and footer are customized to the company’s liking, keeping messaging on-brand and on-tone with company culture.
- If the user has questions or needs to contact the security team, they can use the details in the customized footer.
- Security is immediately notified when the page is blocked.
Conclusions
- The use of AiTM reverse-proxy phishing kits is growing
- These phishing kits successfully bypass the most common forms of 2FA/MFA, which include SMS, TOTP, Push, and Number Matching
- Existing security solutions, like email security gateways (ESGs), are struggling to handle these attacks due to countermeasures put in place, like anti-bot, captchas, and turnstiles. Additionally, attackers are starting to target Microsoft Teams, Slack, and personal email accounts, avoiding existing corporate email security measures.
- The most effective way to detect and block these attacks is to perform visual and structural analysis of the page throughout the lifetime of the user’s session.
Want to learn more and protect your organization from these attacks? Contact our team here.
The post Detecting & Blocking Tycoon’s latest AiTM Phishing Kit appeared first on Obsidian Security.
*** This is a Security Bloggers Network syndicated blog from Obsidian Security authored by Farah Iyer. Read the original post at: https://www.obsidiansecurity.com/blog/detecting-blocking-tycoons-latest-aitm-phishing-kit/