
Information theft and the number of data breaches rooted in identity-based risks are rising as atta 2024-3-27 22:28:14 Author: www.sentinelone.com(查看原文) 阅读量:22 收藏
Information theft and the number of data breaches rooted in identity-based risks are rising as attackers continue to exploit vulnerabilities and find ways to evade detection. This makes early detection one of the most critical pillars of defense across today’s attack surfaces. As identity-based threats continue to develop, organizations that focus on advanced detection and response can protect their data from skilled adversaries.
Advanced persistent threats (APTs) like Sandman, for example, have been observed using identity-based attacks to achieve initial access and lateral movement. These kinds of threat groups are not looking for ransom payments, meaning information theft is their most likely objective.
Increasing cases of information theft put organizations at risk of cyber espionage, financial loss, and brand damage. For organizations to counter such threats, early discovery is key. In this post, we pinpoint how robust identity security measures can help mitigate the tactics, techniques, and procedures (TTPs) used by threat groups like Sandman APT.

Case Study | Identity-Based TTPs Used by Sandman APT
In September 2023, SentinelLabs exposed a series of attacks targeting telecommunication providers in the Middle East, Western Europe, and South Asia. This was the work of a previously undiscovered threat actor they dubbed “Sandman”.
In their findings, SentinelLabs researchers noted that Sandman’s activities were characterized by strategic lateral movement to targeted workstations and minimal engagement. This suggests a deliberate approach aimed at achieving the set objectives while minimizing the risk of detection.
Sandman likely targeted major telcos for espionage purposes, using credential theft techniques and limiting engagement to evade detection. After infiltration, the threat group would wait before proceeding with their activities, suggesting a reliance on stealth for malicious purposes.
New Attack Tactics, Same Attack Cycle
Although the intrusions were detected and interrupted before the threat actor could progress the attacks, they illustrate how advanced intrusions still conform to a typical attack chain depicted below.
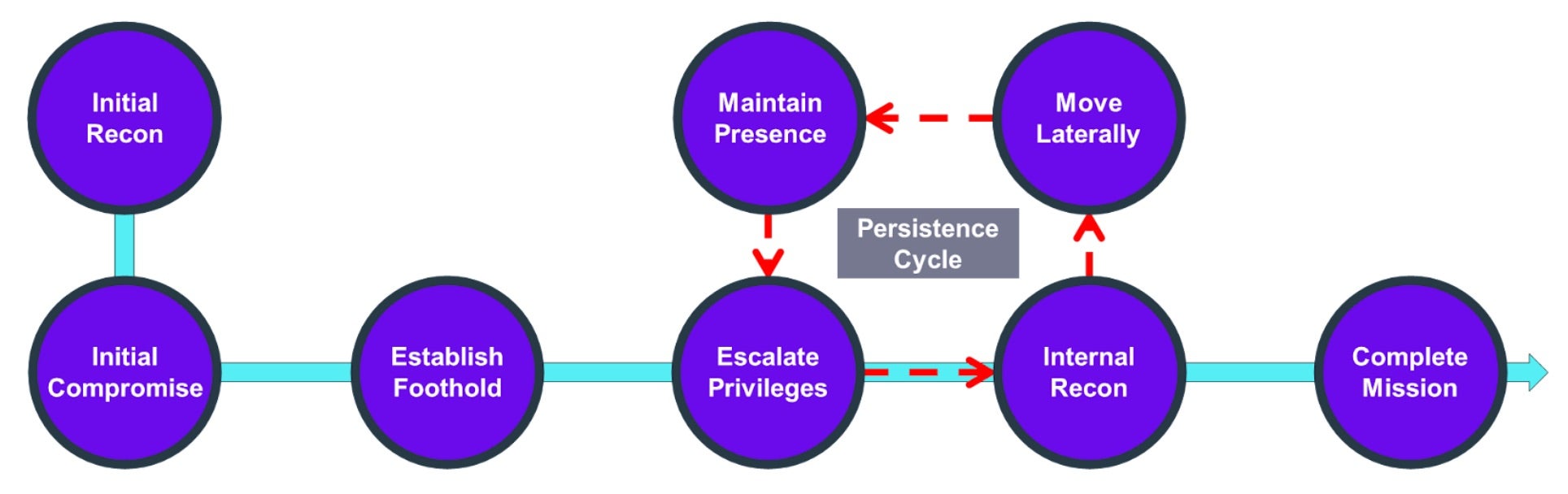
In this attack chain, threat actors will gather intelligence to identify the target and any exploitable entry methods. They will compromise an internal endpoint system to gain access and establish a foothold. Once in, they enter the persistence cycle of gathering information, identifying targets, moving laterally, and establishing backdoors while staying undetected. They will remain in this cycle until they finally execute their planned objectives and complete their mission.
Sandman APT established a foothold within the target organization after stealing administrative credentials and gathering intelligence through internal reconnaissance. Then, the APT infiltrated specifically targeted workstations using the pass-the-hash (PtH) technique over the NTLM authentication protocol. These tactics can be counteracted by having robust identity security controls in place.
To protect against attacks like those perpetrated by Sandman, SentinelOne suggests looking at its Singularity Identity and Singularity Hologram cyber deception solutions for cyber risk mitigation.
Preventing Identity-Based Attacks with Singularity Identity
As part of the SentinelOne agent, Singularity Identity protects an organization’s digital identities and identity infrastructure by safeguarding credentials on the endpoints and Active Directory (AD) objects, including accounts, groups, domain controllers, and more.
Singularity Identity provides cyberattack prevention by protecting identities through concealment and misdirection. After attackers like Sandman establish a foothold on an endpoint, they conduct local and network reconnaissance for usable identity data (e.g., credentials, passwords, AD objects, etc.) because masquerading as legitimate users provides access to resources while minimizing detection. This activity also helps them identify high-value assets such as privileged or sensitive accounts, servers, and data for future attacks.
As they gather intelligence, Singularity Identity conceals the locally stored credentials from discovery, whether memory-resident or stored locally in applications and the operating system. It also identifies AD queries attempting to harvest data from the domain controller like members of privileged groups, domain controllers, or service principal names (SPNs), and conceals the results. It then creates an alert on the SentinelOne console while giving decoy identity data as lures and bait so the attackers do not suspect anything is wrong and continue their activities.
When performing PtH, attackers may capture valid password hashes for accounts using a credential access technique. Captured hashes are used with PtH to authenticate as that user. Once authenticated, PtH performs actions on local or remote systems. Singularity Identity detects and alerts on this and many other credential-based attacks.
Additionally, Singularity Identity supports deploying deceptive credentials across different storage locations, such as browsers, keychains, Windows Credential Manager, and password managers. Credentials taken from these locations will generate an alert and attackers are misdirected away from a production asset.
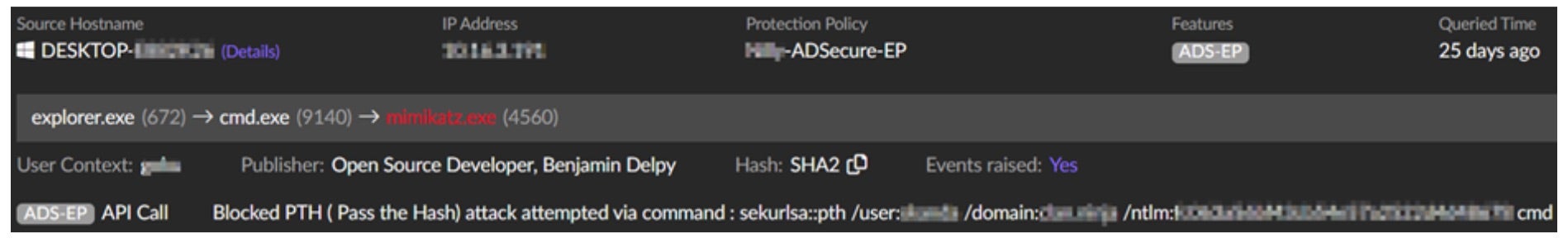
Preventing Identity-Based Attacks with Singularity Hologram
The cyber deception technology of Singularity Hologram takes protection one step further by supplying enterprise-wide decoys to engage the attackers. Hologram is capable of detecting attacks using alternate authentication mechanisms such as the PtH technique. The solution then alerts on attempts to use such methods to move laterally into decoys.
The decoy identity data can point to a black hole destination IP or system. However, having Hologram decoys in the network adds another layer of realism by providing a destination and service for the bait and lures. It also provides a way to engage with attackers like Sandman, who rely on minimal engagement to avoid detection.
Hologram learns the environment and can automatically create and deploy these decoys adjacent to production systems on the same network segments. These decoys match the production environment, mimicking systems and services throughout the network. They also allow defenders to collect data on the attack, as they record all attack activity that engages with them on the network, in memory, and on local storage.
Conclusion
Imagine being an attacker that breaks into a network with the goal of stealing enterprise credentials. After accessing the network resource the attacker is then kicked out because the defense mechanisms in place detected the attempted credential theft, misdirected the attack to a decoy, and recorded all the malicious activity. Such is the power of SentinelOne’s identity security and cyber deception solutions.
As more APTs go the route of leveraging stealthy, prolonged attacks through identity-based TTPs, focusing on early detection and vigilant monitoring allows organizations to stay steps ahead of even the most advanced threats.
SentinelOne’s Identity Suite delivers robust defenses to defend the infrastructure that houses business-critical digital identities. To learn more or request a demo, please visit https://www.sentinelone.com/lp/identity-suite-demo/.
Get a Demo of SentinelOne's Identity Suite
Bringing Identity to XDR. Ready to experience the market’s leading identity security suite?
如有侵权请联系:admin#unsafe.sh