
2024-3-18 23:27:24 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
Reading Time: 6 min

Guardio Labs came across a serious case of subdomain hijacking, affecting thousands of subdomains. They coined the term “SubdoMailing” to describe this chain of attacks that uses the threatened subdomains of reputed companies to send malicious emails. Investigations uncovered that the malicious campaign has been active since 2022.
SubdoMailing can be considered to be an evolved form of social engineering attack, that cashes in on the reliability of well-recognized subdomains. The attackers are operating this malicious campaign on a large scale, by sending millions of phishing emails from the hijacked subdomains.
Subdomain Hijacking Explained
In subdomain hijacking, attackers take charge of a subdomain associated with a legitimate root domain, which then becomes a breeding ground for various malicious activities. The hijacked subdomain can be used to launch phishing campaigns, circulate inappropriate content, sell illegal substances, or spread ransomware.
More often than not, inactive subdomains lie dormant for long periods of time. What’s even more dangerous, these subdomains have dangling DNS records that pave the way for subdomain hijacking. Once an attacker assumes control of these subdomains – they can get away with a lot!
When you are operating a domain name with several subdomains, it is easy to have your back turned and keep doors unlocked. Whether you are an enterprise or a small business, failing to secure your subdomains can lead to incidents like SubdoMailing or other forms of subdomain abuse.
How do SubdoMailing Attacks work?
An article by Guardio stated that the company discovered suspicious email traffic arising from thousands of apparently legitimate subdomains of reputed brands. This included big names like MSN, VMware, McAfee, The Economist, Cornell University, CBS, Marvel, eBay and many more!
These emails used a sense of urgency to manipulate users into clicking on compromising links. These redirected users down an avenue of harmful destinations. It ranged from invasive advertisements to more dangerous phishing websites that were aimed at stealing sensitive information.
SubdoMailing Example
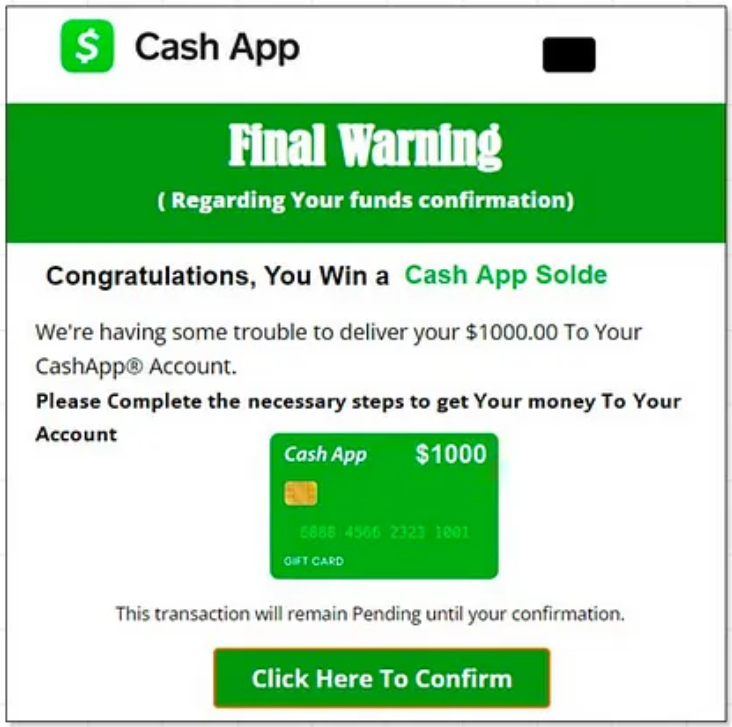
The example shown above is a classic case of SubdoMailing discovered by Guardio. Emails originating from a compromised Cash App subdomain were circulated among millions of users. This email displayed a warning message for the confirmation of pending funds to their Cash App accounts. The email contained several potentially malicious redirects.
Malicious email attachments and links that are carefully crafted are very hard to ignore. Especially when they come attached to a warning message that demands immediate attention. Naturally, in these situations, it is very likely that users will click on the links and fall victim to a cyberattack.
SubdoMailing Attack Attributes and Features
SubdoMailing attacks can be projected to have high success rates due to their unique characteristics. Guardio explains that SubdoMailing uses highly sophisticated tactics to manipulate legitimate subdomains of such popular brand names. These attacks were very hard to detect and required thorough investigation on the part of Guardio’s cybersecurity experts.
Why SubdoMailing Attacks May Have a High Success Rate
We see real potential in SubdoMailing attacks to seriously harm several unsuspecting users, due to the following characteristics:
- Impersonation of well-known brands with an established reputation
- Operating on a large scale by manipulating 8000+ domains and counting
- Bypassing spam filters
- Bypassing email content filters by curating credible image-based messages
- Attackers analyze your device type and location to launch more targeted attacks
- The malicious emails passed email authentication checks like SPF, DKIM, and DMARC
How do SubdoMailing Phishing Emails Bypass Email Authentication Checks?
Let’s take the example of one of the use cases investigated by Guardio. Guardio found several phishing emails originating from a particular subdomain of msn.com.
On closer inspection of these malicious emails, Guardio found that they were sent from a server based in the Ukrainian city of Kyiv. Ideally, this would have been flagged as suspicious during an SPF check, unless the IP address of the server was authorized. On checking it was found that a subdomain of msn.com had authorized the suspicious IP address.
This could be due to either of the following reasons:
- It could be an insider threat where an MSN employee intentionally authorized the IP address to send phishing emails
- It could be a simple case of human error where the server was unintentionally authorized due to a typo
- It could be a more advanced form of DNS manipulation where the MSN subdomain was hijacked by an external threat to authorize the server
Further examination of the SPF record for the msn.com subdomain, took Guardio experts down a rabbit hole of 17826 nested IP addresses that are authorized to send emails on behalf of the domain. The sheer intricacy of the SPF record hinted at a highly suspicious yet carefully crafted approach toward manipulating authentication filters. More importantly, investigations revealed that this MSN subdomain was pointing to another domain via a CNAME DNS record. Hence, once the attacker bought the other domain, it enabled them to hijack the MSN subdomain.
So how did the attackers achieve this? Let’s find out:
Usage of Inactive/Abandoned Subdomains for SubdoMailing
Guardio used internet archives to dig deeper into understanding whether the msn.com subdomain was in fact claimed by MSN. Turns out, the subdomain was active 22 years ago. It had been lying abandoned for more than two decades – until recently!
So here’s what happened:
- A threat actor bought the domain that was linked to the subdomain. Since the link still existed 22 years later, they were able to hijack the domain.
- Now they were free to manipulate it in any way they liked! The attackers authorized their own servers in the subdomain’s SPF record, which allowed them to send authenticated phishing emails on behalf of the subdomain.
- They used this chance opportunity to send millions of fraudulent emails under the guise of msn.com, posing to be legitimate senders.
SPF Record Manipulation for SubdoMailing
In the case of SubdoMailing, the hijacked subdomain’s SPF record hosted several abandoned domains. These domains were further acquired to authorize attacker-owned SMTP servers. As per the nature of SPF policy, the subdomain ends up authorizing all of these attacker-controlled servers as legitimate email senders.
The very reason we use SPF is to authorize legitimate senders. This becomes very important when a company uses external email vendors to send their emails. This also eliminates the chances of fraudulent sources sending emails on behalf of a domain. In this classic case of SPF record manipulation, the advantage of using SPF to authenticate emails was abused to authorize malicious senders.
Preventing SubdoMailing Attacks: What Can Businesses Do?
An advanced form of subdomain hijacking attack like SubdoMailing requires a proactive prevention strategy. Here’s how you can start:
Preventing Dangling DNS Records
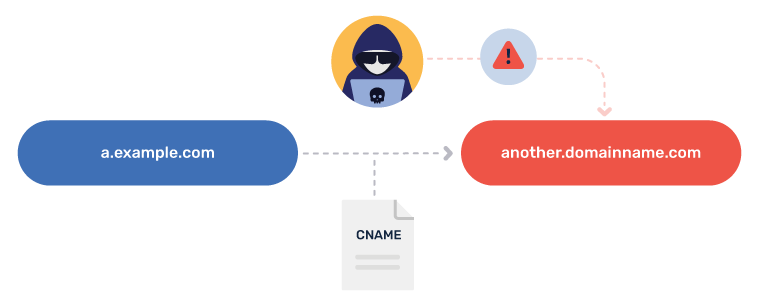
DNS entries pointing to domains that are deconfigured, or servers that are no longer in use, can lead to SubdoMailing. Make sure you are regularly updating your DNS records and are not authorizing outdated sources. Only active domains or servers that you are in control of should be pointed to in your DNS records. You should also ensure your email vendors are keeping their sending lists clean and removing servers that are no longer in use.
Monitoring Your Email Channels
Configuring DMARC reports is not enough, it should be accompanied by monitoring the reports. As a domain owner, you should be aware of your email sending practices at all times. With large email volumes, this is difficult to achieve even with a dedicated mailbox. This is why you need a third-party vendor like PowerDMARC. We help you monitor your sending sources and email activity on a cloud-based dashboard with advanced filtering capabilities. Subdomains are autodetected on our platform, helping you keep a close eye on them. This allows you to discover any suspicious activity instantly!
Take Control of Your Subdomains
This is a wake-up call for re-evaluating all your sending sources today. Get started by performing an SPF check with our free tool!
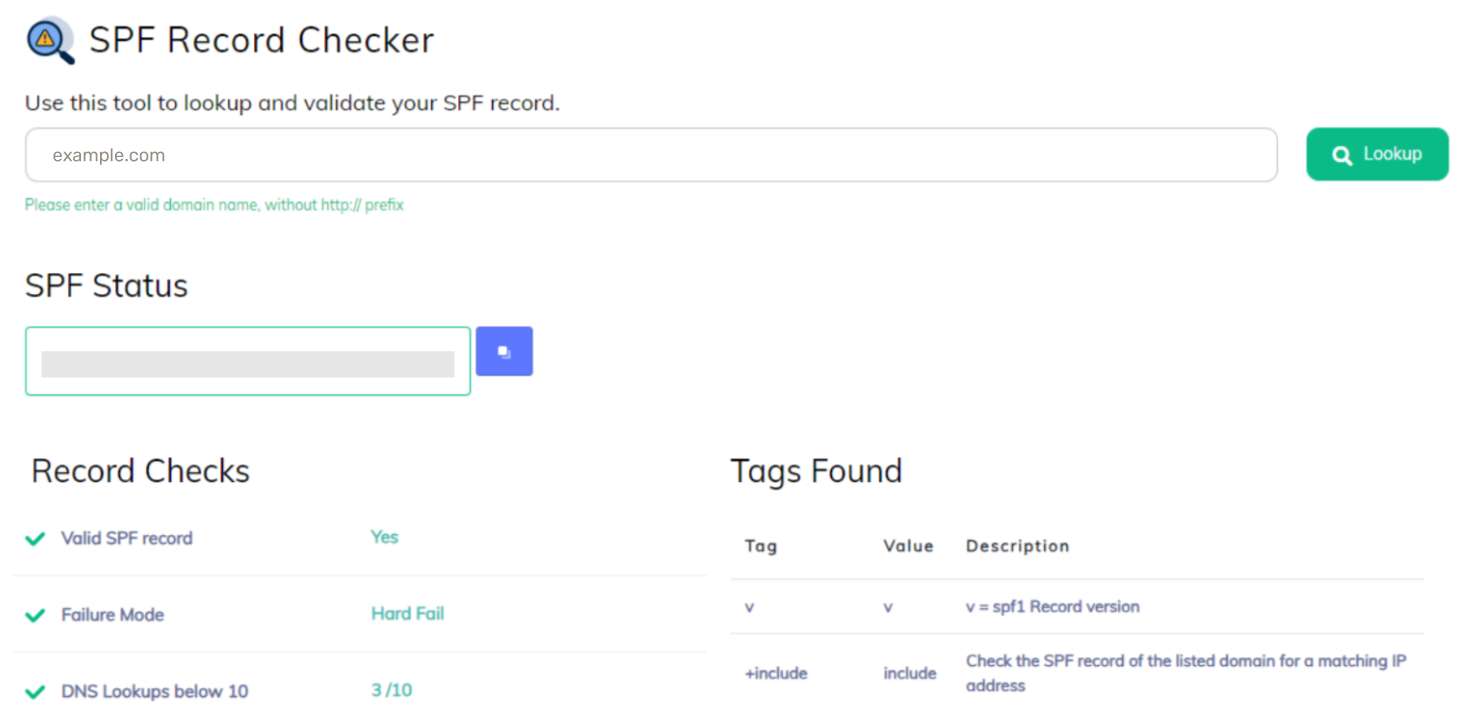
Evaluate the “include” mechanisms in your SPF status to check your included domains and subdomains. These domains are hosting SPF records, with IP addresses authorized to send emails on behalf of your root domain. If you find a subdomain you no longer use – it’s time to remove the “include” for it. You can head over to your DNS editing zone to make the required changes.
Additional Tips to Protect Against Cyber Attacks
- Ensure your CNAME records are always up to date, and disable or remove CNAME records that you no longer use
- Make sure the SPF mechanisms in your record are up to date too, remove any sending services that you no longer use
- Configure your legitimate sources to send DMARC compliant emails and set your DMARC policy to reject for your domains and subdomains.
- Protect your parked domains and subdomains
- Remove unused subdomains and DNS records
- Continuously review emails sent from your domains and subdomains by setting up reporting for all domains you own
Protecting Your Domains with PowerDMARC
PowerDMARC can help you secure your domain names! Our platform is designed to enable domain owners to take back control of their own domains through visibility and monitoring. We help you keep track of your sending sources, and email traffic by presenting granular details about the ins and outs of your email activity. This helps you detect unusual patterns in your domain activity, malicious IPs impersonating your domain, and even discover geo locations of the servers spoofing your brand name.
To start your domain security journey with us, contact us to speak to an expert today!

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Yunes Tarada. Read the original post at: https://powerdmarc.com/subdomailing-subdomain-hijacking-attack/
如有侵权请联系:admin#unsafe.sh