2024-3-17 08:36:54 Author: isc.sans.edu(查看原文) 阅读量:27 收藏
This PE file contains an obfuscated hexadecimal-encoded payload. When I analyze it with base64dump.py searching for all supported encodings, a very long payload is detected:
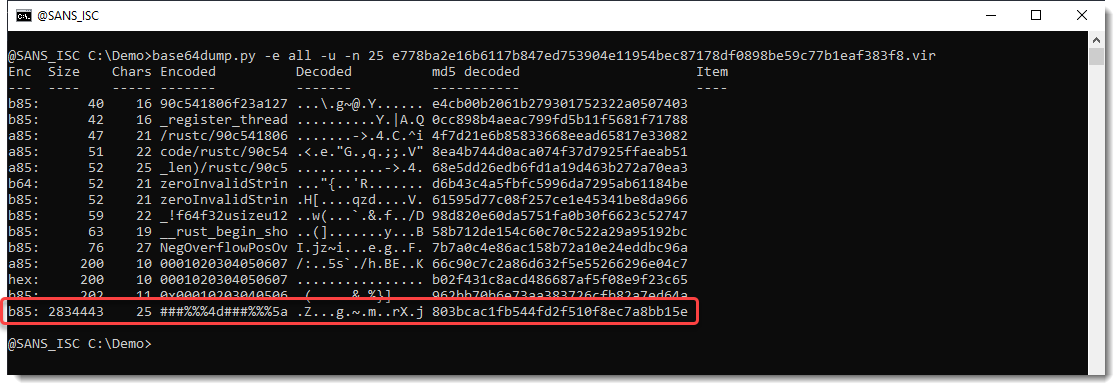
It's 2834443 characters long, and matches base85 encoding (b85), but this is likely a false positive, as base85 uses 85 unique characters (as its name suggests), but in this particular encoded content, only 23 unique characters are used (out of 85).
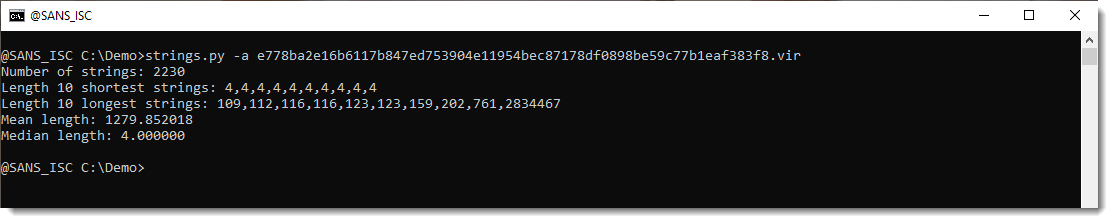
Analyzing the PE file with my strings.py tool (calculating statistics with option -a) reveals it does indeed contain one very long string:
Verbose mode (-V) gives statistics for the 10 longests strings. We see that 2 characters (# and %) appear very often in this string, more than 75% of this long string is made up of these 2 characters:
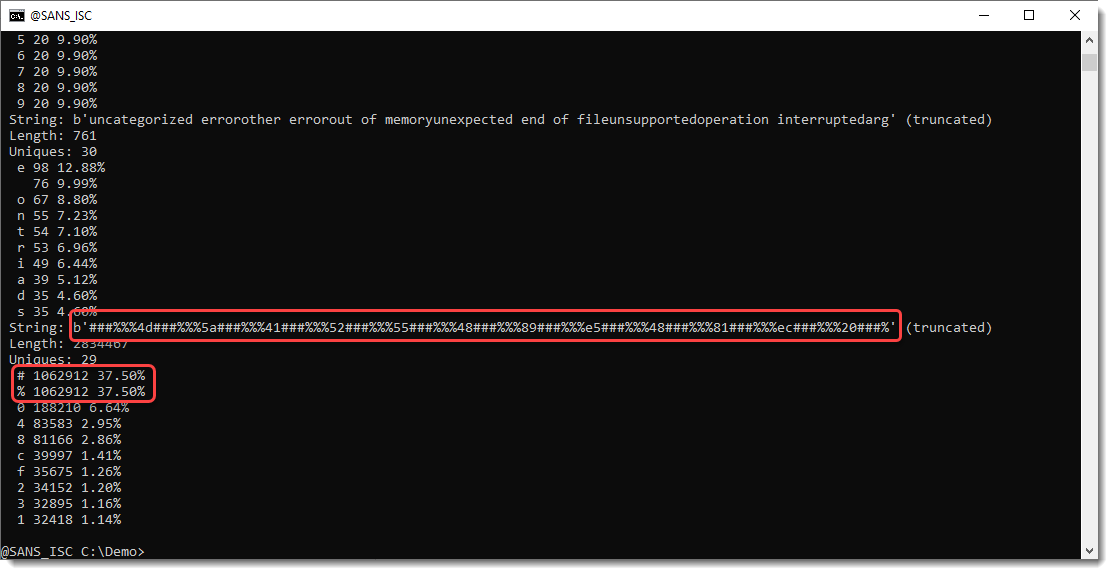
These 2 characters are likely inserted for obfuscation. Let's use base64dump.py and let it ignore these 2 characters (-i #%"):
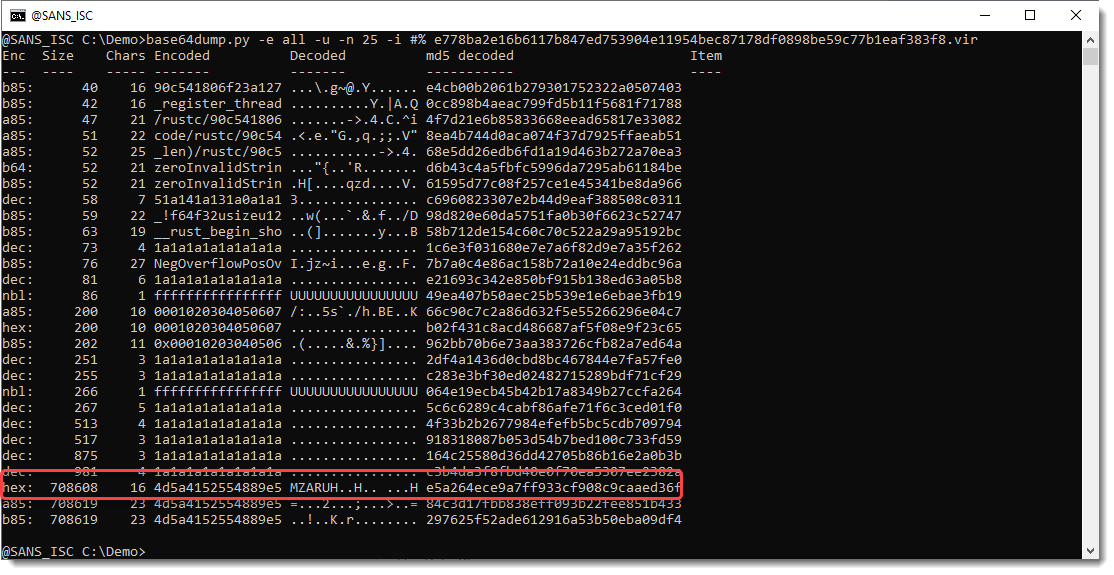
Now we have a hex encoded payload that decodes to a PE file (MZ), and most likely a Cobalt Strike beacon (MZARUH).
Didier Stevens
Senior handler
blog.DidierStevens.com
如有侵权请联系:admin#unsafe.sh